Ivan Macalintal
@IMNetSpyder
Connecting the Dots, Tweeting and Hooting through the kaleidoscope of life. Tweets, Hoots and Opinions are my own and do not represent that of my employer.
قد يعجبك
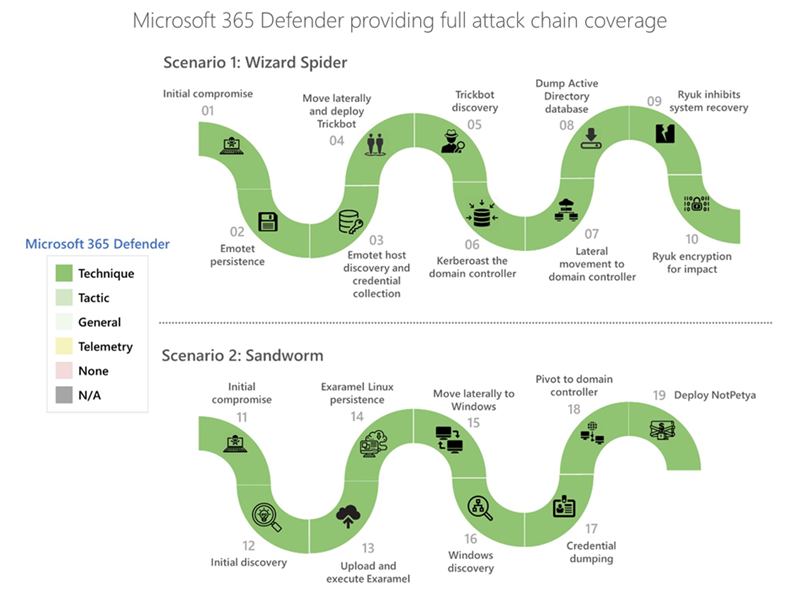
This year’s MITRE Engenuity ATT&CK® Evaluations concentrated on Wizard Spider and Sandworm. Microsoft 365 Defender once again demonstrated industry-leading protection, highlighting the need for an XDR-based approach for attack detection and prevention. microsoft.com/security/blog/…
We updated our blog on the CVE-2021-44228 Log4j 2 vulnerability with details about ransomware attacks on non-Microsoft hosted Minecraft servers, as well as additional product guidance, including Threat and Vulnerability Management msft.it/6015ZzTUV
microsoft.com
[Updated 01/19/2022] Guidance for preventing, detecting, and hunting for exploitation of the Log4j...
Microsoft is tracking threats taking advantage of the remote code execution (RCE) vulnerability in Apache Log4j 2. Get technical info and guidance for using Microsoft security solutions to protect...
Microsoft is tracking threats taking advantage of the CVE-2021-44228 remote code execution (RCE) vulnerability in Apache Log4j 2 ("Log4Shell"). Get technical info and guidance for preventing, detecting, and hunting for related attacks: msft.it/6019ZENIW
MSRC has just published a blog post for Microsoft's response to CVE-2021-44228 Apache Log4j 2 msrc-blog.microsoft.com/2021/12/11/mic…
This is so cool! Nasdaq recognizes Asians at Microsoft and the Asian-American and Pacific Islander Heritage Month! Proud and thankful to have the support of our Microsoft family and Nasdaq ! #AsianPacificAmericanHeritageMonth #diversityandinclusion #microsoft #microsoftlife


The @MITREattack evaluation results are in and Microsoft Defender for Endpoint has successfully demonstrated industry-leading defense capabilities. Read the results: msft.it/6014V5Nss
Our team is still expanding! This time around, it will be in Vancouver. For any interest, let me know or you can go directly to our Careers link below. Cheers. lnkd.in/gWW7d4Y
Microsoft took action against the Trickbot botnet, disrupting one of the world’s most persistent malware operations. In this blog, we detail the evolution of Trickbot, associated tactics, recent campaigns, and dive into the anatomy of a specific attack. msft.it/6019TIb4l
We’re seeing more activity leveraging the CVE-2020-1472 exploit (ZeroLogon). A new campaign shrewdly poses as software updates that connect to known CHIMBORAZO (TA505) C2 infrastructure. The fake updates lead to UAC bypass and use of wscript.exe to run malicious scripts.
Microsoft is actively tracking threat actor activity using exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon. We have observed attacks where public exploits have been incorporated into attacker playbooks.
More #malcro mayhem
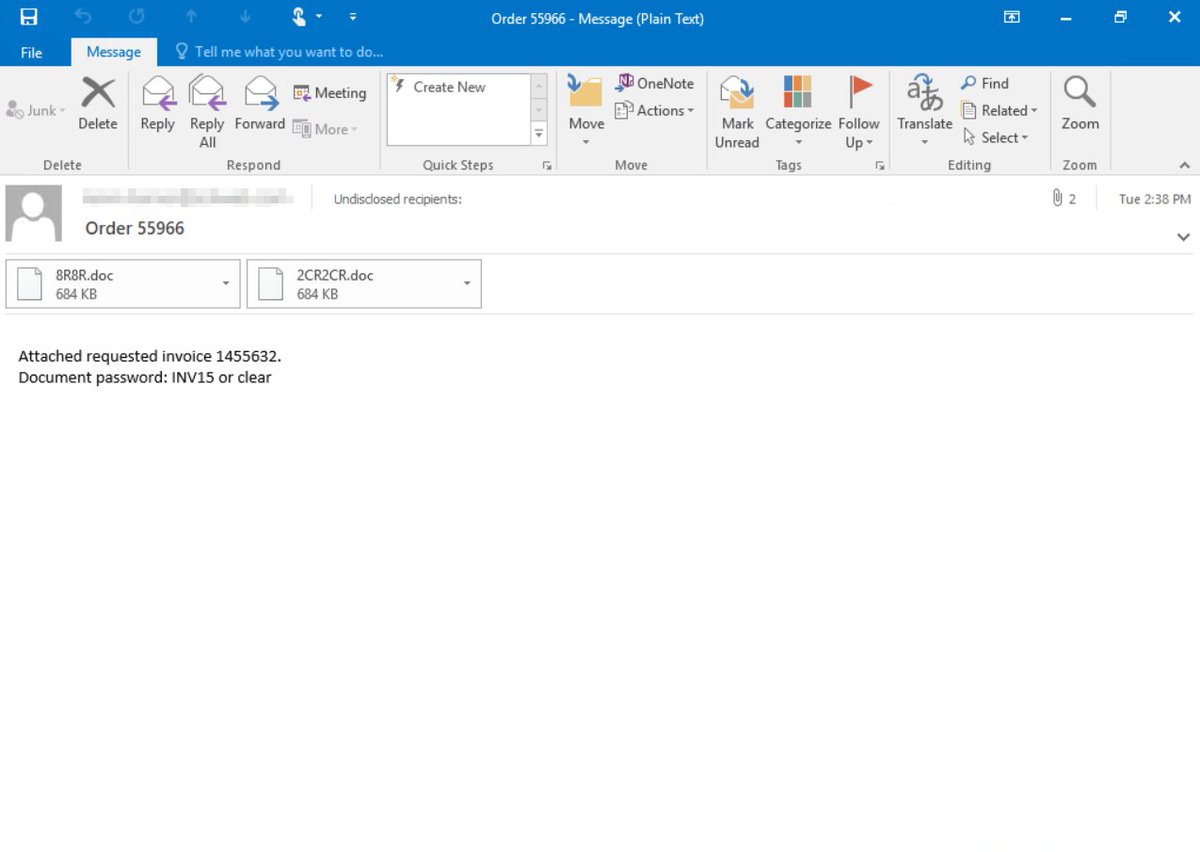
Earlier this week we started seeing a spike in the use of password-protected documents in multiple malware campaigns, including Trickbot. These documents are attached to emails that use varying social engineering lures like the typical "order", "invoice", "documents".
MITRE Engenuity’s Center for Threat-Informed Defense published a FIN6 adversary emulation plan, a collection of threat intelligence, MITRE ATT&CK data, supporting scripts, utilities. Microsoft is proud to be part this industry-wide collaborative project. msft.it/6015TtfB3
Dudear campaigns, associated with the threat actor CHIMBORAZO (aka TA505), are a staple in the threat landscape, with regular runs since resurfacing in January. This month’s campaign, active as of today, uses the same techniques including polymorphism & detection evasion tactics.

Since reemerging on July 17, Emotet has sustained its activities with daily spam runs spewing more than 500K emails every day (except weekends) starting at around 2:00 AM Pacific Time (UTC -7). This week, the malicious attachments used were observed mostly in Europe.
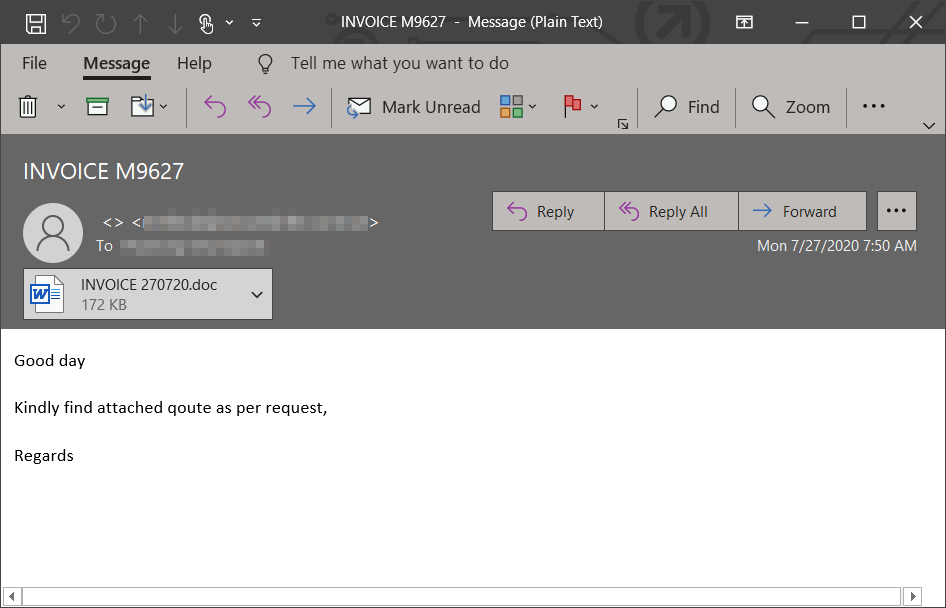

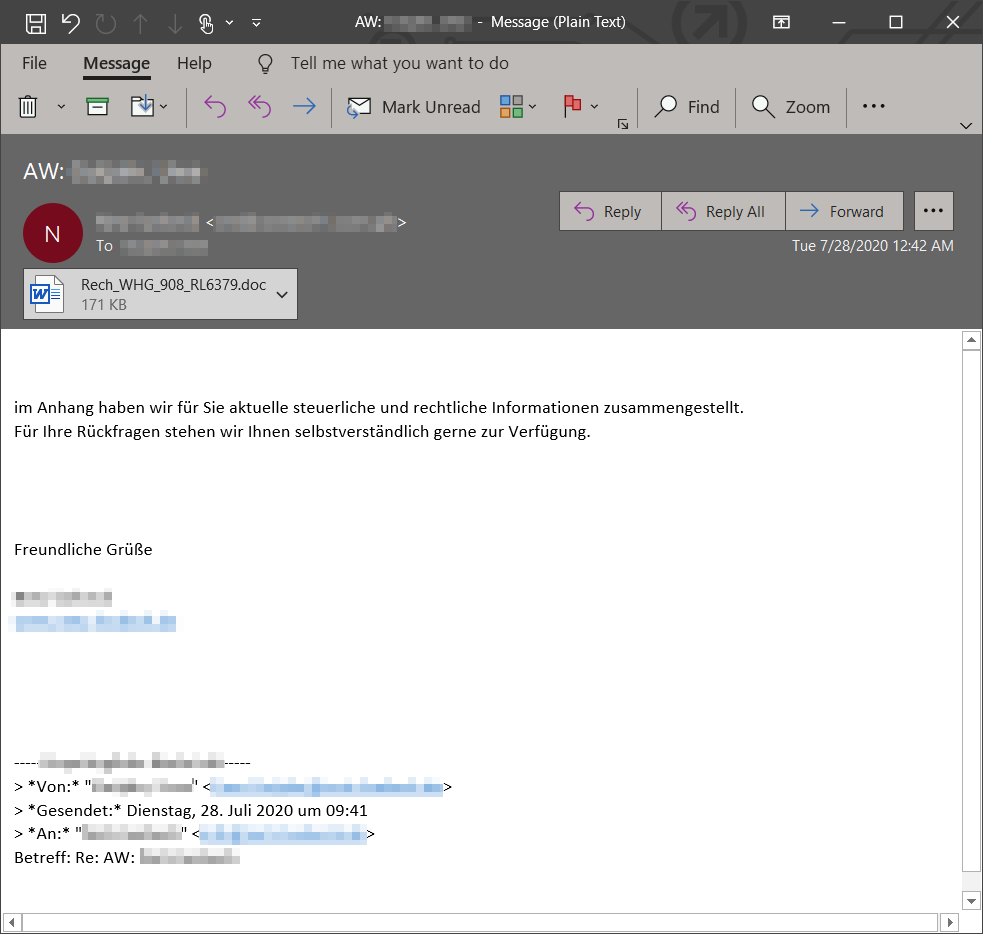
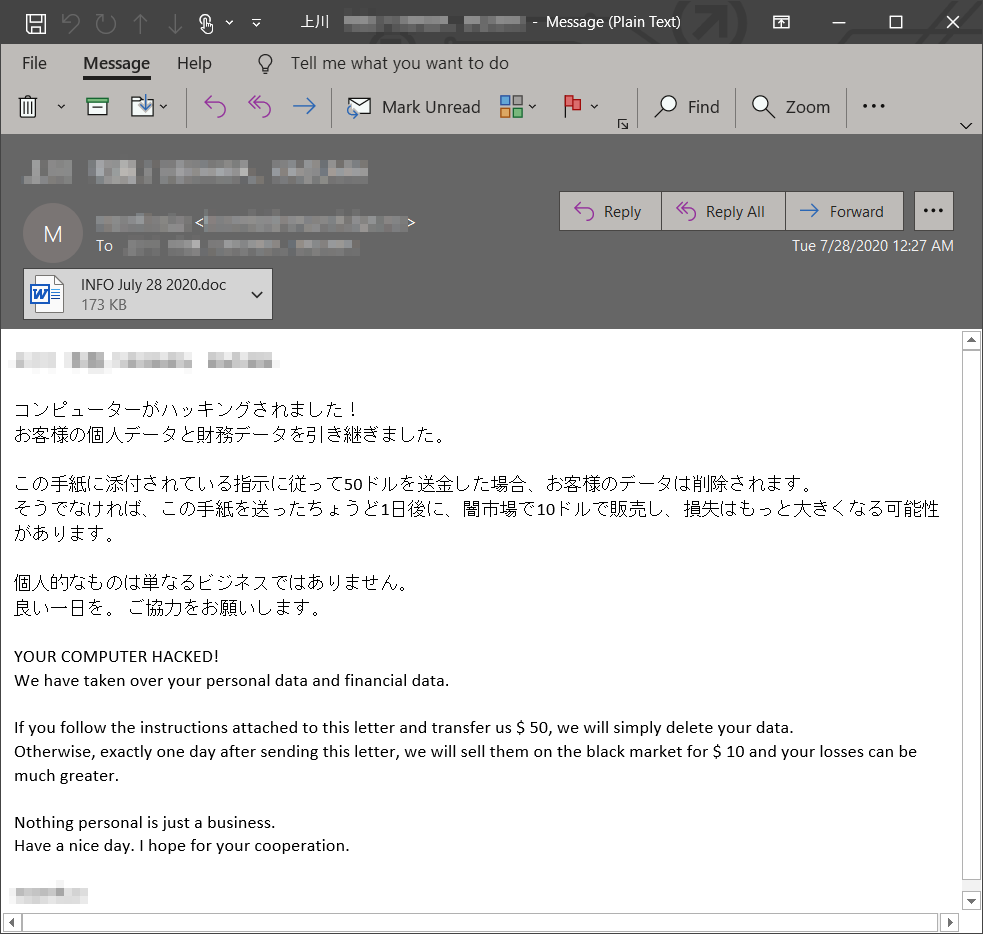
Emotet resurfaced in a massive campaign today after being quiet for several months. The new campaign sports longtime Emotet tactics: emails carrying links or documents w/ highly obfuscated malicious macros that run a PowerShell script to download the payload from 5 download links


Since day one, our mission has been to protect customers with the best endpoint security solution that they will absolutely love. 🥰 We are proud that @SCMagazine awarded us a perfect 5-star rating in their latest review. techcommunity.microsoft.com/t5/microsoft-d…

We started observing these campaigns in early June, but we saw them surge this week. The emails contain either a link to a redirector site (typically a compromised website) or an HTML attachment with a malicious URL in iframe. Both methods lead to the website with CAPTCHA.
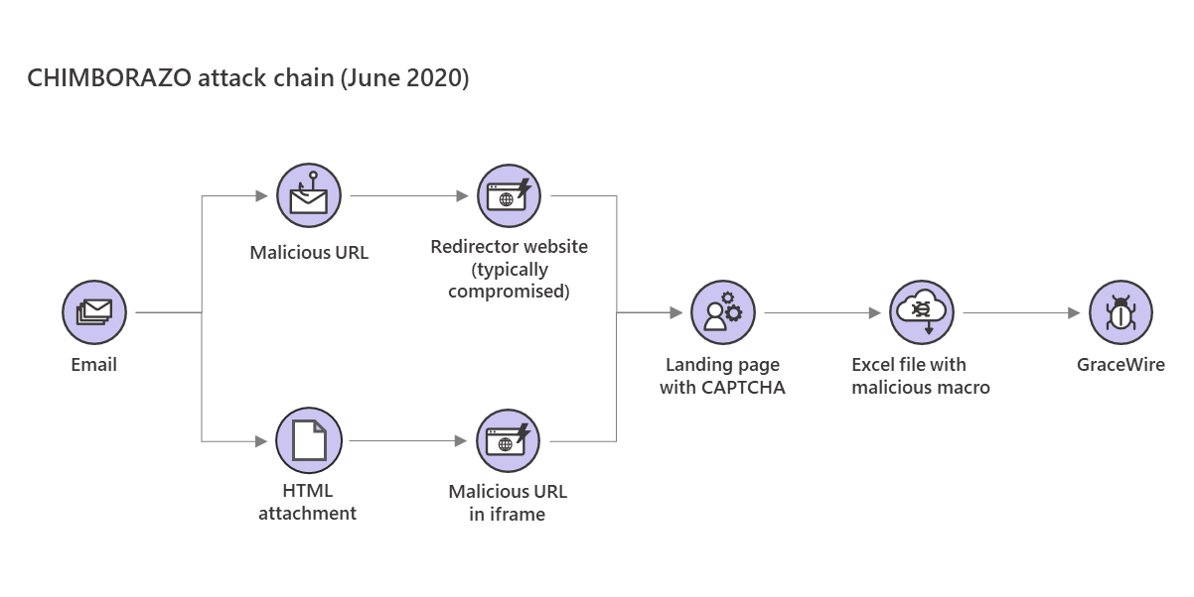
CHIMBORAZO, the group behind Dudear campaigns that deploy the info-stealing Trojan GraceWire, evolved their methods once again in constant pursuit of detection evasion. The group is now using websites with CAPTCHA to avoid automated analysis.
Attackers have shifted their focus as a result of COVID-19 to take advantage of device misconfigurations in remote work scenarios. We've introduced new assessments and tagging to help you harden your systems against these threats. 💪 #mdatp #tvm #COVID19 techcommunity.microsoft.com/t5/microsoft-d…

United States الاتجاهات
- 1. Knicks 13.1K posts
- 2. Landry Shamet 1,278 posts
- 3. #AEWDynamite 21.5K posts
- 4. #Survivor49 3,860 posts
- 5. Brandon Williams 1,017 posts
- 6. #CMAawards 5,460 posts
- 7. #AEWCollision 8,726 posts
- 8. Derik Queen 4,077 posts
- 9. Vooch 1,122 posts
- 10. Vucevic 5,882 posts
- 11. Labaron Philon 1,092 posts
- 12. #mnwild N/A
- 13. FEMA 65.9K posts
- 14. Vucci Mane N/A
- 15. Blazers 4,158 posts
- 16. NO CAP 14.5K posts
- 17. Coby White 1,042 posts
- 18. Dubon 3,768 posts
- 19. Naji Marshall N/A
- 20. Josh Hart 2,751 posts
Something went wrong.
Something went wrong.

























































































![certbr's profile picture. Centro de Estudos, Resposta e Tratamento de Incidentes de Segurança no Brasil - NIC.br / CGI.br. Notificações e dúvidas enviar para cert [arroba] cert.br](https://pbs.twimg.com/profile_images/892396873830608896/oS7Tc7Ha.jpg)