Nextron Systems
@nextronsystems
Managed Compromise Assessments #YARA #IOCs #DFIR #APT #Sigma - the home of @thor_scanner, ASGARD and the Aurora Agent
내가 좋아할 만한 콘텐츠
✨ Exciting News! ⚡️ We've launched our official Nextron Community Discord Server! A hub for tech talks, support, and exclusive updates. 🔗 Join us now to connect, learn, and shape the future of products (THOR, THOR Lite, THOR Cloud, Aurora, etc.): discord.gg/r6BTgbDvRt

Beyond availability - toward verified recovery Backups should do more than bring systems back online - they should bring them back clean. Together with @Veeam, we’ve built an integration that adds forensic assurance to backup workflows. THOR extends Veeam’s trusted recovery…

🔒 NetScaler CVE-2025-7775 under attack! Patching is not enough. Appliances may have already been compromised. Use THOR to scan via SSHFS & uncover web shells, backdoors + artifacts. Details in our blog: eu1.hubs.ly/H0mVbP60

Even with the best defenses, attackers still find a way. Recent UK breaches show that policies & EDRs miss hidden threats like renamed binaries, web shells & malware-less persistence. 🛡️ Compromise Assessments with THOR uncover what others overlook. 👉 eu1.hubs.ly/H0mGtPy0

New Partnership: Nextron Systems x Arctic Wolf 🐺 Together, we’re strengthening SOC defenses with Nextron’s curated Sigma rule feed for sharper detection and broader coverage. Read more: eu1.hubs.ly/H0mGxhM0 #CyberSecurity #ThreatDetection #Sigma

We’ve partnered with Arctic Wolf 🐺 @AWNetworks - They extend their detection coverage with Nextron’s curated Sigma rule feed: 700+ high-quality rules - Most of our rules are generic, technique-focused, and designed to detect unknown threats - not just IOCs - We get structured…

𝗛𝗮𝘃𝗲 𝗮𝘁𝘁𝗮𝗰𝗸𝗲𝗿𝘀 𝗯𝗲𝗲𝗻 𝗶𝗻𝘀𝗶𝗱𝗲 𝘆𝗼𝘂𝗿 𝘀𝘆𝘀𝘁𝗲𝗺 𝗯𝗲𝗳𝗼𝗿𝗲 𝘁𝗵𝗲 𝗽𝗮𝘁𝗰𝗵? ToolShell exploits gave unauthenticated access. Web shells, stolen keys, persistence. 🕵️ Learn more in our blog post: eu1.hubs.ly/H0mxXnJ0

⏱️ Instant Timelines with THOR - No manual tagging. No log wrangling. DFIR expert Maurice Fielenbach shows how to map persistence in minutes: ✔️ Registry Run Keys ✔️ Startup folder implants ✔️ LOLBin payloads 👉 Step-by-step guide & tool usage here: eu1.hubs.ly/H0mvr2d0

New in ASGARD Analysis Cockpit v4.3: ✔️ Case Intelligence (suggested cases from intel) ✔️ THOR Cloud integration ✔️ Redesigned UI for smoother analysis A significant leap for forensic analysts. ➡️ eu1.hubs.ly/H0mtcNd0 #DFIR #ThreatIntel #ThreatHunting #ASGARD #THORCloud
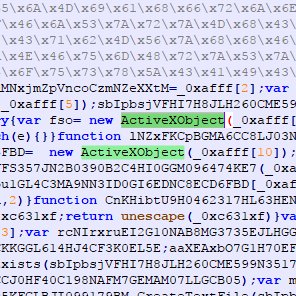
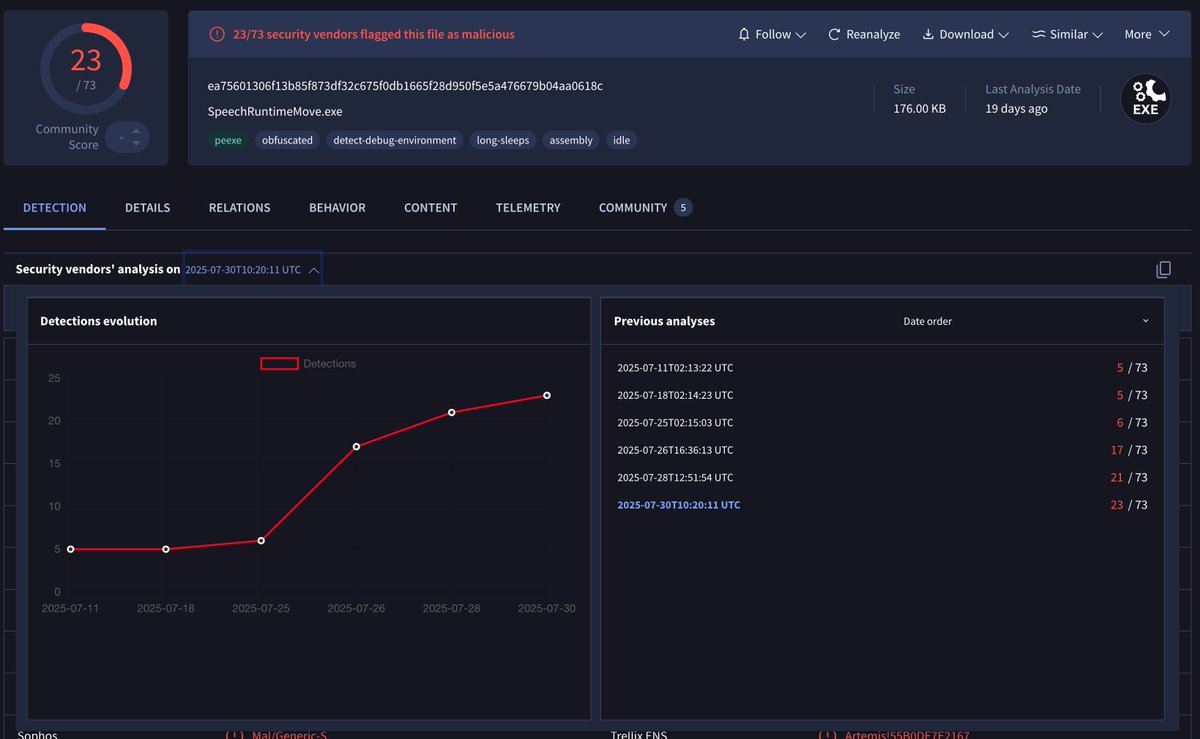
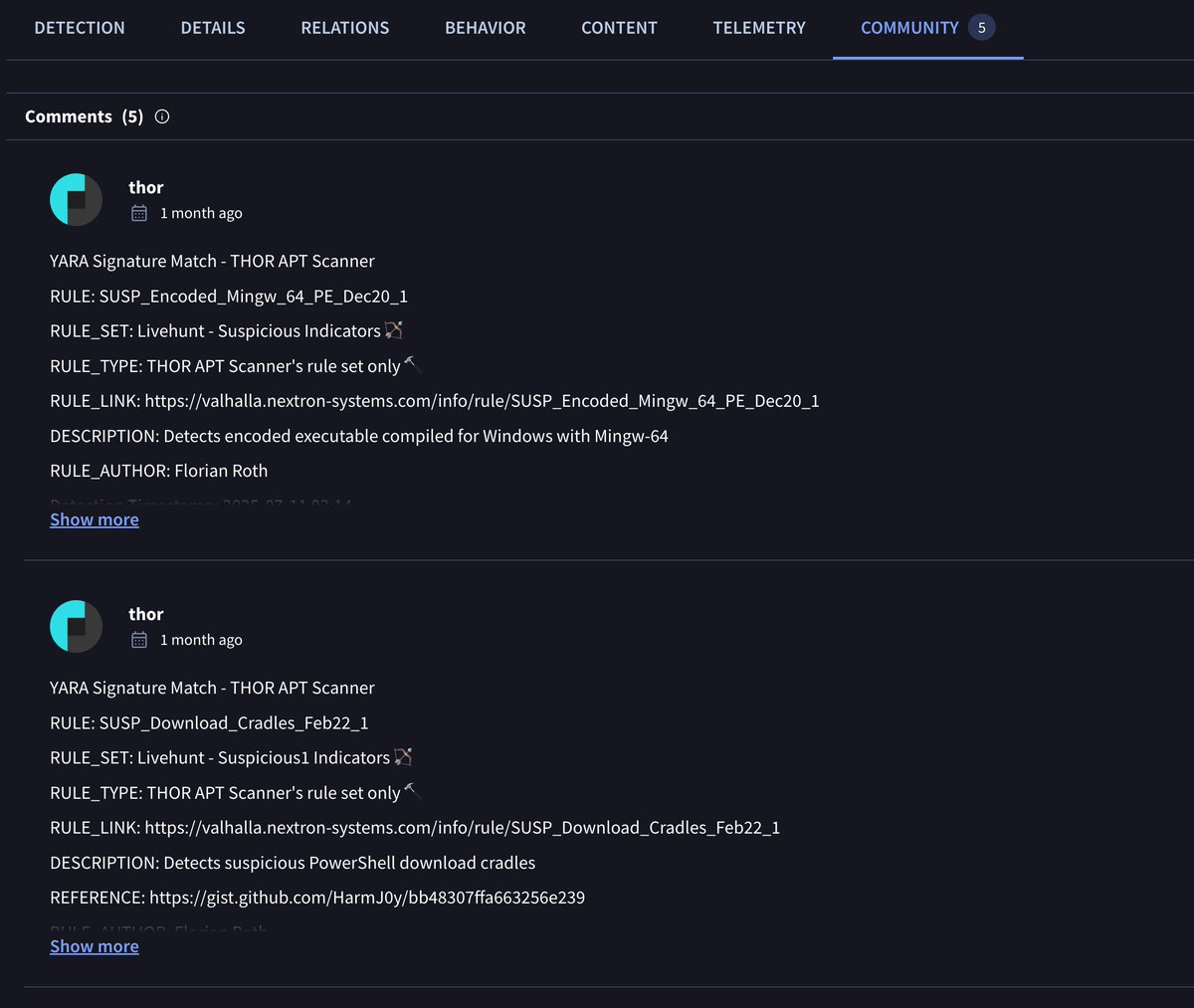
A new lateral movement PoC was published on GitHub: SpeechRuntimeMove (COM Hijacking via SpeechRuntime DCOM) We added the repo to our stack to build, test, and analyze The sample uploaded to VirusTotal is already covered by at least 5 of our generic rules (VT only shows up to 5…

I keep seeing reports of attackers going after #ESX hosts – exporting VMs, cloning domain controllers, grabbing NTDIS files. Not really surprising. ESX often ends up being the quiet corner of the network where no one’s looking. Thing is: we’ve had some solid ways to deal with…

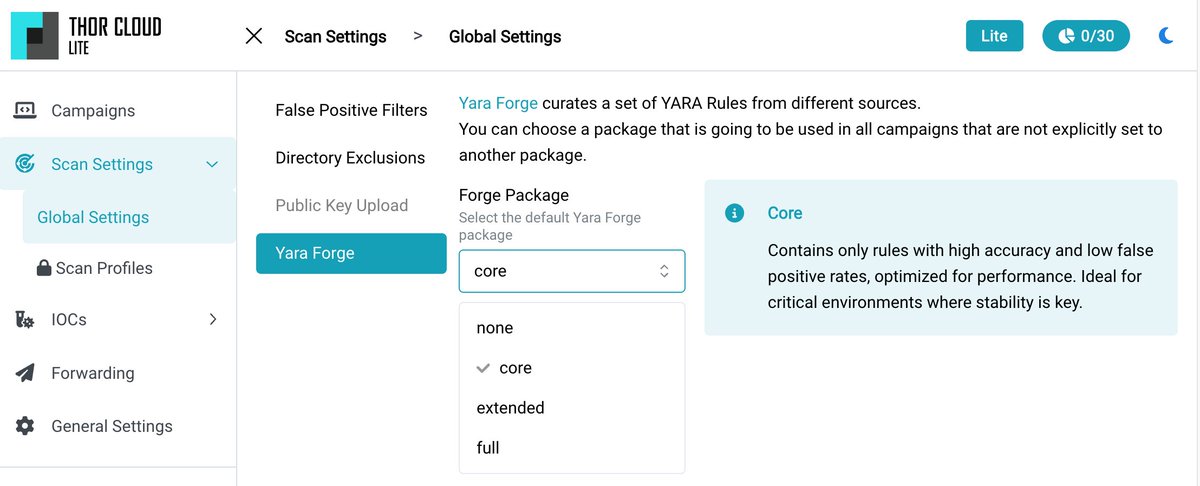
New in THOR Lite 📦 Archive scanning with YARA - previously exclusive to the full version 🧠 Curated rulesets from YARA Forge Two powerful features, now unlocked nextron-systems.com/2025/08/13/new…

Persistence without malware? Here's how attackers abuse T1547.001 using only built-in Windows tools - and how to catch them. 🕵️ 🔍 eu1.hubs.ly/H0mk5Tf0

THOR Cloud now supports webhooks ⚡️ Want to get alerted the moment a scan detects something on one of your systems? You can One webhook. One alert. No polling. Works even in the free THOR Cloud Lite Blog Post nextron-systems.com/2025/08/07/web…

Hidden Autostarts: An eye-opening tour of Run key variants you’ve probably overlooked Learn how attackers abuse T1547.001 not just with reg.exe, but also via PowerShell, VBScript, regini.exe, and even mshta.exe. eu1.hubs.ly/H0m6Xn-0

Plague: The PAM Backdoor That Slipped Past Every Scanner A stealthy Linux implant, undetected by all AV engines, hijacks PAM for silent SSH access. Learn how to uncover it and why YARA + behavior-based hunting matters. 🔗 eu1.hubs.ly/H0m7DT30 #Linux #ThreatHunting #YARA

What’s the most abused MITRE persistence technique? 🕵️ T1547.001 – Registry Run Keys / Startup Folder is #1, used by 54 threat groups. DFIR expert Maurice Fielenbach crunched the ATT&CK data. Read the key findings + detection tips 👉 eu1.hubs.ly/H0m3q2B0

Persistence is noisy - if you know what to listen for. We analyzed attacker telemetry and cut through the ATT&CK noise to dissect the most abused persistence method in the wild: registry run keys. Learn how to hunt it properly. nextron-systems.com/2025/07/29/det… by Maurice Fielenbach
⚡️ We’ve partnered with @Threatray to combine deep code analysis and generic YARA-based detection - Soon THOR Thunderstorm matches enrich Threatray’s platform - Our analysts gain insights from Threatray’s Binary Intelligence Platform - Detection meets classification…

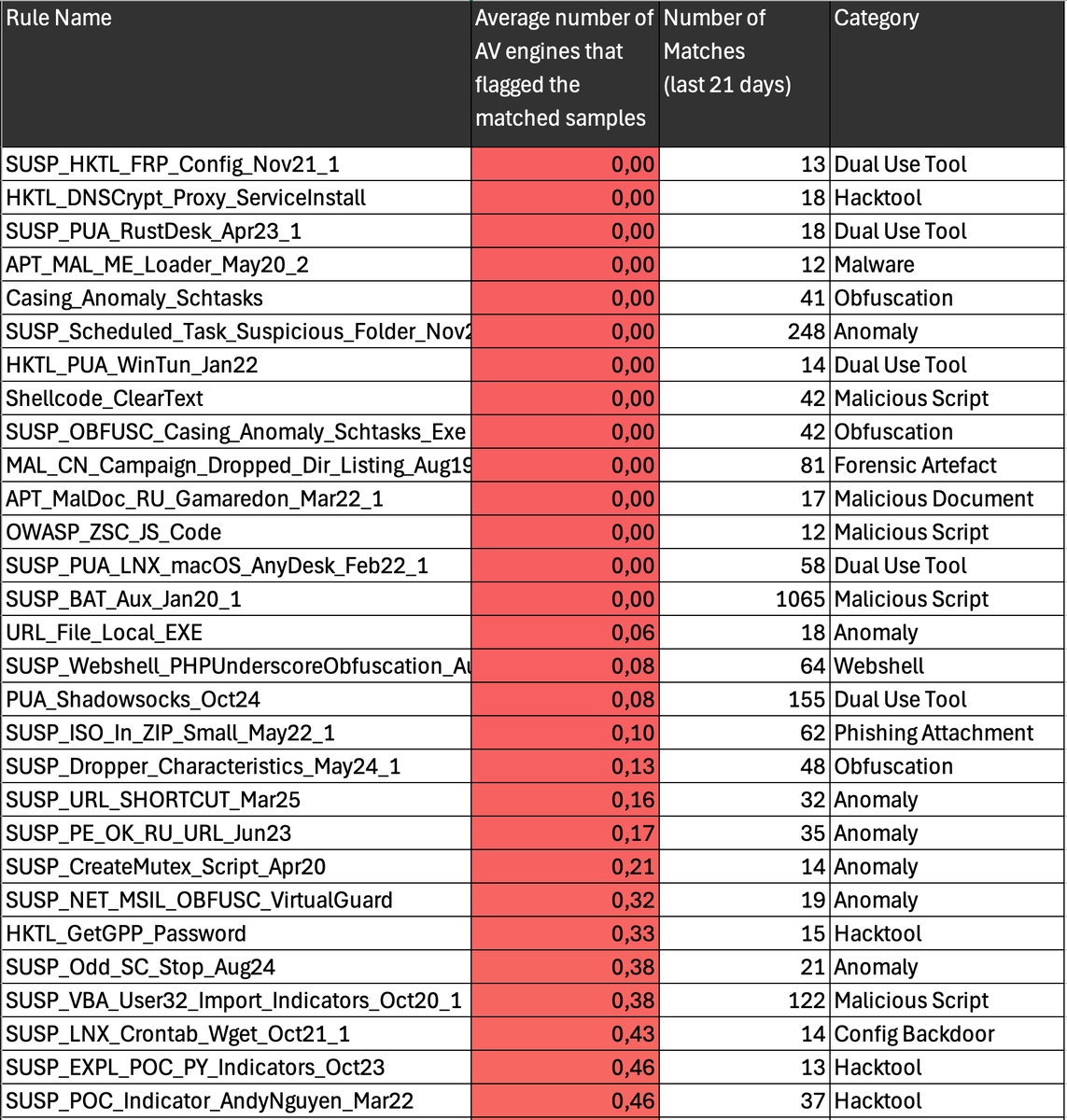
We analyzed the top 500 most successful THOR rules – “successful” meaning: they detected samples that were either ignored or missed by nearly all AV engines on VirusTotal. Some rules detect clear malware. Others reveal dual-use tools, renamed hacktools, misused admin binaries,…


This isn’t malware – it’s a controlled test case. But it shows something most YARA scanners simply can’t do. THOR performs in-memory matching with full segment awareness. In this case, the rule hits two regions in the same process: - One string in the memory of the loaded binary…

United States 트렌드
- 1. Good Sunday 66.1K posts
- 2. #sundayvibes 4,639 posts
- 3. Zirkzee 18.2K posts
- 4. #MUFC 16.5K posts
- 5. #CRYMUN 7,994 posts
- 6. Amorim 39.6K posts
- 7. WILLIAMEST AT EMQUARTIER 255K posts
- 8. Crystal Palace 29.4K posts
- 9. #EMAnniversaryxWilliamEst 260K posts
- 10. Stockton 31K posts
- 11. Mason Mount 5,776 posts
- 12. Licha 2,415 posts
- 13. Mateta 10.1K posts
- 14. Yoro 8,023 posts
- 15. Gakpo 6,080 posts
- 16. Duke 33.8K posts
- 17. Dalot 5,823 posts
- 18. Casemiro 6,897 posts
- 19. #BNewEraBirthdayConcert 1.39M posts
- 20. Muhammad Qasim 16.8K posts
내가 좋아할 만한 콘텐츠
-
 ATT&CK
ATT&CK
@MITREattack -
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Unit 42
Unit 42
@Unit42_Intel -
 RedDrip Team
RedDrip Team
@RedDrip7 -
 The DFIR Report
The DFIR Report
@TheDFIRReport -
 abuse.ch
abuse.ch
@abuse_ch -
 Arkbird
Arkbird
@Arkbird_SOLG -
 blackorbird
blackorbird
@blackorbird -
 Volexity
Volexity
@Volexity -
 Roberto Rodriguez 🇵🇪
Roberto Rodriguez 🇵🇪
@Cyb3rWard0g -
 volatility
volatility
@volatility -
 Red Canary, a Zscaler company
Red Canary, a Zscaler company
@redcanary -
 Karsten Hahn
Karsten Hahn
@struppigel -
 sigma
sigma
@sigma_hq -
 ANY.RUN
ANY.RUN
@anyrun_app
Something went wrong.
Something went wrong.