
Insider Threat Matrix™
@ITMFramework
The Insider Threat Matrix™ - an open framework from @Forscie for mapping, investigating, and responding to insider threats.
The strength of insider threat programs grows when practitioners learn from each other. The Insider Threat Matrix™ @ITMFramework remains the only public, operational framework for insider risk and investigation, strengthened by the insights professionals continue to share.…
The joiner phase is the strongest point to detect conflict-of-interest risk. MT021 shows how undisclosed incentives can follow a new hire into their role and surface only when decisions matter. 🔗 insiderthreatmatrix.org/articles/AR1/s… Forscie®. Inside Matters
insiderthreatmatrix.org
Conflicts of Interest | Motive
A subject may be motivated by personal, financial, or professional interests that dir...
Trust in an insider threat investigation comes from one thing: defensibility. PLAN: Proportionate, Lawful, Accountable, Necessary - provides that standard. Forscie’s latest Knowledge Center article shows how PLAN reinforces organizational trust and ensures investigative findings…
Insider risk is changing, fast. James Weston joins David Loader to explore the convergence of online and offline behaviour, and why most enterprise programs still can’t see what’s coming next. 🎧 youtube.com/watch?v=6OCnOr… Forscie®. Inside Matters.
youtube.com
YouTube
Combatting Insider Threat: Beyond Firewalls and Point Solutions
The Insider Threat Matrix™ just advanced. v2.0.0 is live, now featuring MITRE ATT&CK® mapping and full integration support for custom use cases. Open, expert-driven & Investigator-built. Explore the ITM on GitHub: github.com/Forscie/Inside… Forscie®. Inside Matters.
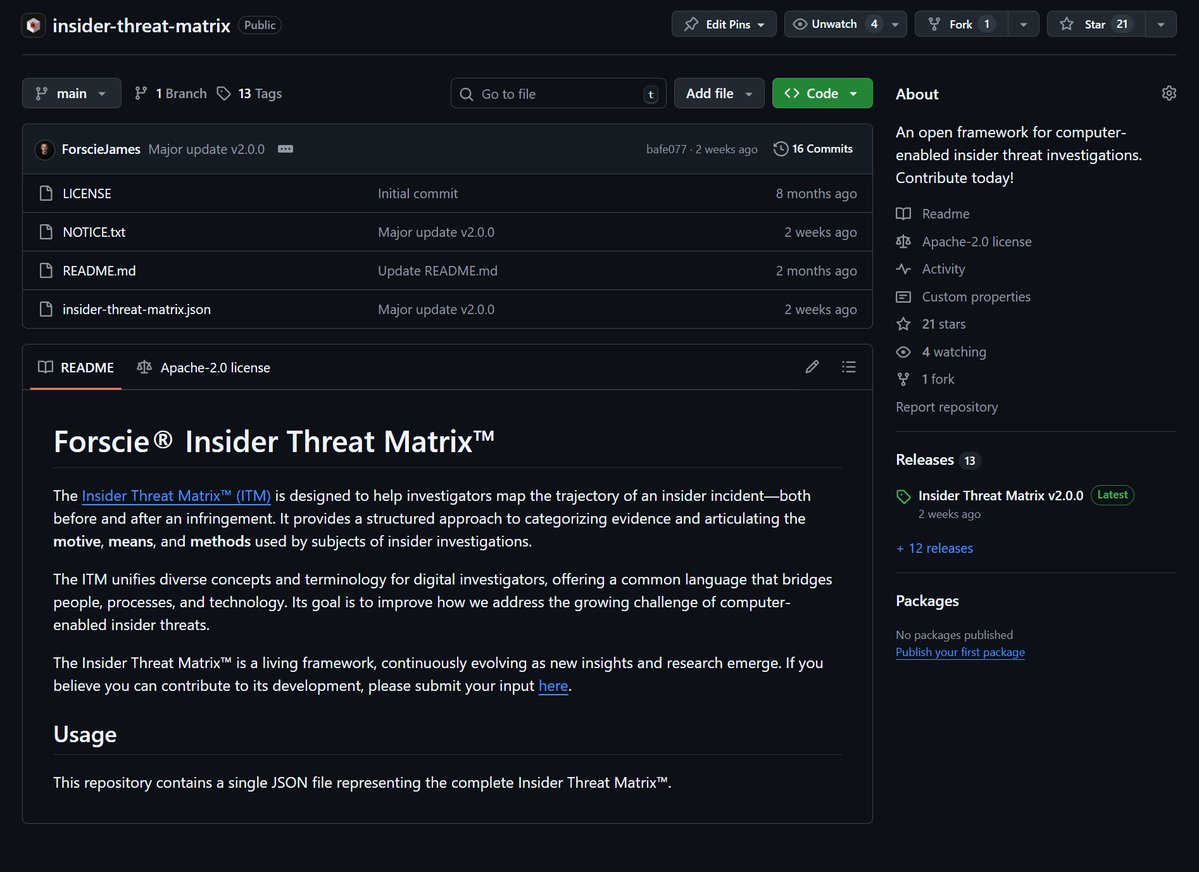
Access defines accountability. Our Knowledge Center article explores how Microsoft Purview’s role-based permissions, alerts, and just-in-time access enable defensible insider threat investigations. Read more: knowledge.forscie.com/article/Managi… Forscie®. Inside Matters.
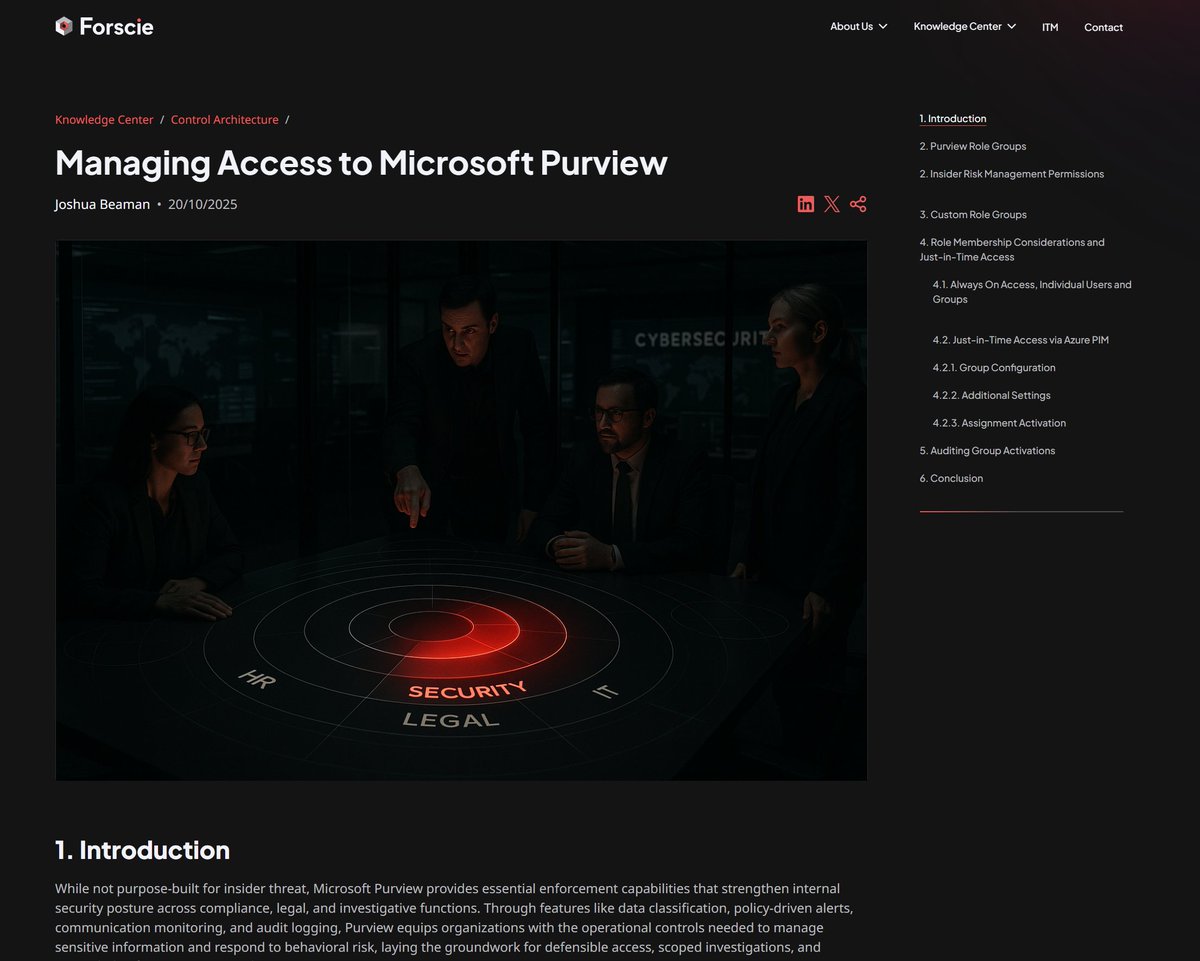
When coercion extends beyond the screen. The ITM adds a new motive sub-section: Threats of Violence or Physical Harm, addressing cases where cybercrime and organised crime collide to coerce insiders through fear. Trust isn’t just digital. It’s human. insiderthreatmatrix.org/articles/AR1/s…
Ransomware isn’t always external. The Insider Threat Matrix™ classifies ransomware deployment under IF027.002, often tied to MT012 (Coercion) or MT006 (Personal Gain). Not every breach begins outside. Some begin with trust. Forscie®. Inside Matters. insiderthreatmatrix.org/articles/AR4/s…
insiderthreatmatrix.org
Insider Threat Matrix™ | Unified Framework For Investigators
ITM™ is an open framework for digital investigators and the cyber security community, to better address the challenges of computer-enabled insider threats.
Insider risk demands its own vocabulary, one built on investigation, not combat. Forscie is rewriting how the field speaks. Forscie®. Inside Matters. knowledge.forscie.com/article/perime…
Insiders don’t need exploits to pivot through your internal network. They can simply make requests. Firewall rules. Jump hosts. Change tickets. Each step approved. This isn’t lateral movement. It’s institutional bypass. 🔗 insiderthreatmatrix.org/articles/AR3/s…
insiderthreatmatrix.org
Insider Threat Matrix™ | Unified Framework For Investigators
ITM™ is an open framework for digital investigators and the cyber security community, to better address the challenges of computer-enabled insider threats.
External compromise is costly. So organised crime is turning inward. Criminal gangs and Organised Crime Groups (OCGs) are recruiting insiders, buying access instead of breaching it. 🔗 knowledge.forscie.com/article/approa…
Live today: Ryan Bellows & Kasey Olbrych on using the Insider Threat Matrix™ to advance your insider risk program. Hosted by @Proofpoint. 🕒 10 AM PT / 1 PM ET / 5 PM GMT 🔗proofpoint.com/us/resources/w…
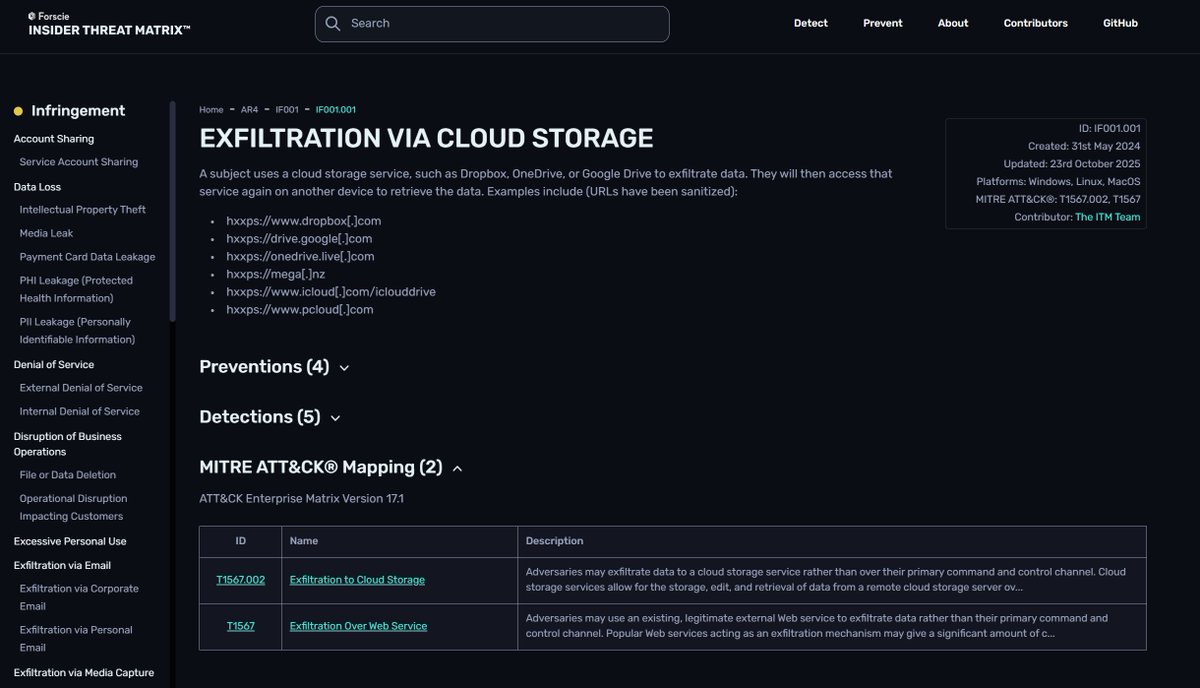
The Insider Threat Matrix now includes MITRE ATT&CK mapping. Internal behaviors and external techniques—unified in one view. For detection engineers: faster correlation, clearer context, operational precision. See it now: insiderthreatmatrix.org
Repeated “personal use” isn’t harmless. It’s drift. In the Insider Threat Matrix, it’s IF017 – Excessive Personal Use: where tolerated habits become culture, and culture becomes risk. Intent isn’t always malicious. Sometimes it’s just normalized. 🔗 insiderthreatmatrix.org/articles/AR4/s…
insiderthreatmatrix.org
Excessive Personal Use | Infringement
A subject uses organizational resources, such as internet access, email, or work devi...
It starts as a download. A movie. A tool. A shortcut. In the Insider Threat Matrix, that act has a name: IF007 — Unlawful Access to Copyrighted Material. It’s not about content. It’s about culture. Every tolerated breach entrenches what’s allowed. 🔗 insiderthreatmatrix.org/articles/AR4/s…
insiderthreatmatrix.org
Unlawfully Accessing Copyrighted Material | Infringement
A subject unlawfully accesses copyrighted material, such as pirated media or illegiti...
When threat actors recruit from within, the first signs probably won't appear in a SIEM. They are more likely visible to HR. PV054: HR Collaboration and Advisory Integration - defines how early engagement prevents compromise. Inside Matters. 🔗 insiderthreatmatrix.org/preventions/PV…
insiderthreatmatrix.org
Human Resources Collaboration for Early Threat Detection | Prevention
Implement a process whereby HR data and observations, including those from managers a...
Some insiders are not motivated by personal gain. They act out of fear. Extortion is leverage weaponized, instilling fear to gain access, and convert access into profit. Sometimes the right question isn’t why they did it. It’s who coerced them. 🔗 insiderthreatmatrix.org/articles/AR1/s…
insiderthreatmatrix.org
Non-Violent Threats and Intimidation | Motive
The subject acts under coercion stemming from threats that target reputation, profess...
On October 15, 2025, join @F0R5C13 and @KnownDivide as they walk through how the The Insider Threat Matrix™ helps insider risk teams replace uncertainty with clarity. Hosted by @Proofpoint. 📅 Wednesday, October 15, 2025 at 10 AM PT / 1 PM ET / 6 PM BST proofpoint.com/us/resources/w…
Sign-up now: proofpoint.com/us/resources/w…
The Insider Threat Matrix™ is an open framework for investigators and insider risk practitioners. On October 15, 2025, @Proofpoint hosts @KnownDivide and @F0R5C13 to show why it was created and how teams can adopt it. 📅 October 15, 10 AM PT / 1 PM ET / 6 PM BST…
Pirated media on endpoints isn’t just an annoyingly common AUP infringement. For insider threat investigators, patterns of behavior such as pirated media infringements can also help identify more serious drift before it escalates. knowledge.forscie.com/article/identi…
United States 트렌드
- 1. Josh Allen 39.6K posts
- 2. Texans 59.7K posts
- 3. Bills 148K posts
- 4. Joe Brady 5,288 posts
- 5. #MissUniverse 462K posts
- 6. #MissUniverse 462K posts
- 7. Anderson 27.7K posts
- 8. McDermott 4,684 posts
- 9. #StrayKids_DO_IT_OutNow 53K posts
- 10. Technotainment 19.2K posts
- 11. Troy 12.1K posts
- 12. joon 12.2K posts
- 13. Beane 2,870 posts
- 14. #Ashes2025 23.3K posts
- 15. Maxey 14.6K posts
- 16. #criticalrolespoilers 2,349 posts
- 17. GM CT 22.7K posts
- 18. Al Michaels N/A
- 19. Fátima 200K posts
- 20. FINAL DRAFT FINAL LOVE 1.27M posts
Something went wrong.
Something went wrong.













































