JFrog Security
@JFrogSecurity
The JFrog Security Research Team empowers developers and companies to excel by identifying, prioritizing, and mitigating software risks.
قد يعجبك
📣 #CyberSecurityAwareness Mini-Series: "Hunting Malicious ML Models" Part 5, THE FINALE asks... 🫨 Can "Safe" ML Models be Weaponized?⚡️ ✨ Let’s start by defining what a “Safe” Models is: Safe models were created to reduce this malicious code execution risk we discussed in…

📣 #CyberSecurityAwareness Mini-Series: "Hunting Malicious ML Models" Part 4 is all about... 🏃🏻 Library Mitigations and How They Can be Bypassed 🏃🏻 Scanners cannot take full responsibility for protecting against malicious models. This has pushed #ML Python libraries to add…

📣 #CyberSecurityAwareness Mini-Series: "Hunting Malicious ML Models" Part 3 poses the question... How do scanners work and why do they generate False Positives (FPs) + False Negatives (FNs)? 🤔 ❎ False Positives (FPs) ❎ Looking at the numbers, other scanners on Hugging Face…

📣 #CyberSecurityAwareness Mini-Series: "Hunting Malicious ML Models" Part 2 talks about the 3 most common model threats 👇🏼 🔹 PyTorch-Malcode (1,263 files detected) #PyTorch models’ default save and load functionalities rely on Pickle serialization and deserialization.…

Too many #security tools are creating more problems than they solve. This #CyberSecurityAwarenessMonth, JFrog Field CISO, Paul Davis, breaks down why a fragmented defense can leads to higher costs, slower remediation, and a weaker security posture. Learn how to move from silos…

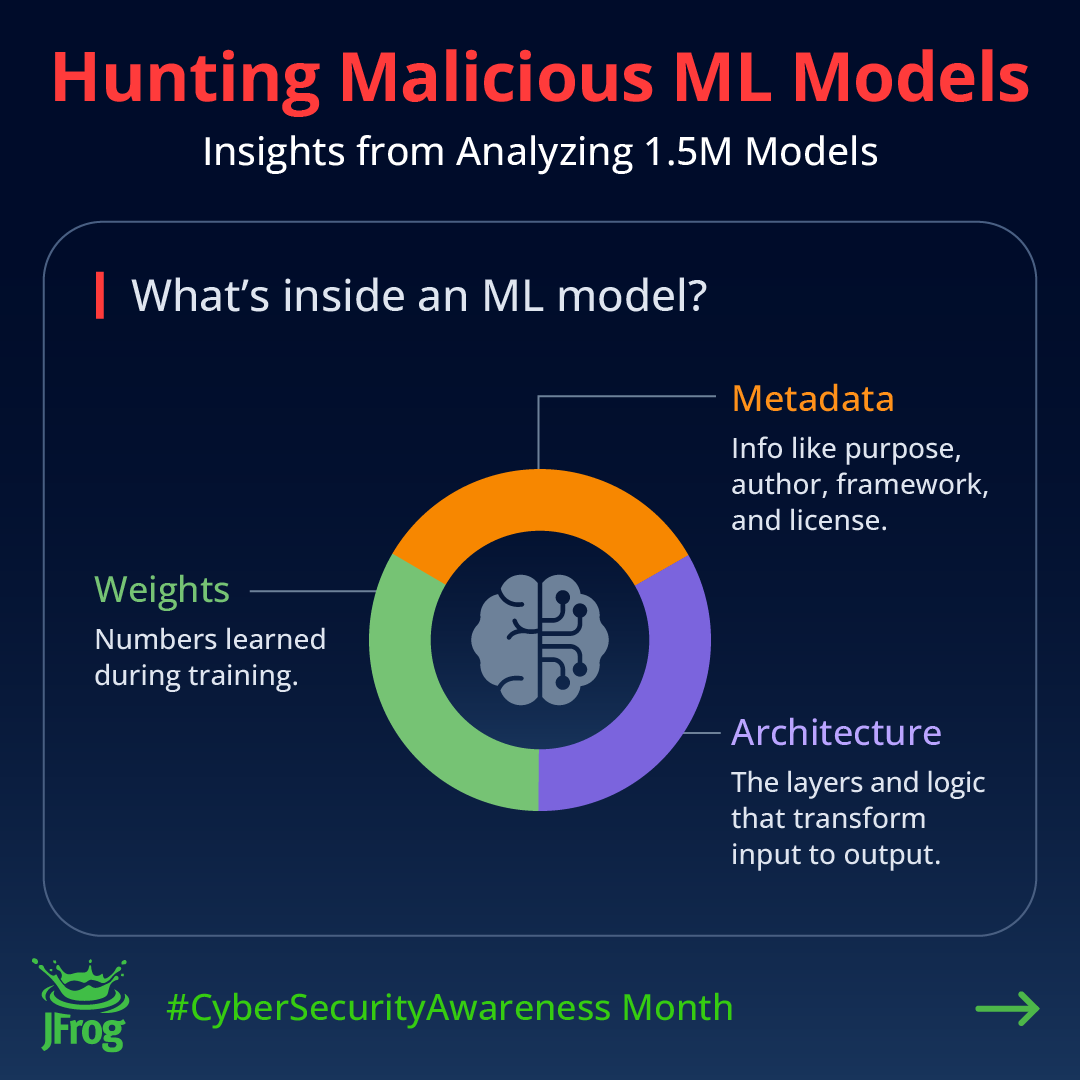
🔐 October marks #CybersecurityAwarenessMonth! We kicked it off yesterday with our first miniseries: “Hunting Malicious ML Models – Insights from Analyzing 1.5M Models.” And all month long, we'll be sharing new research, blogs, & webinars as your go-to resources for uncovering…

Our security team uncovered a malicious PyPI package called SoopSocks, which disguises itself as a SOCKS5 proxy but behaves like a backdoor. Our research revealed that it installs persistence via Windows services and scheduled tasks, modifies firewall rules, silently executes…

JFrog is getting a jumpstart on #CyberSecurityAwareness Month! 🚨 We're kicking it off with our 1st miniseries: "Hunting Malicious ML Models - Insights from Analyzing 1.5M Models" 👇🏼 Here's what you need to know👇🏼 1. HUGE growth in malicious ML models published on Hugging Face…


🚨 NEW APP SECURITY ALERT: 🚨 Shai-Hulud npm supply chain attack – 164 new compromised packages detected by JFrog Security Researchers. Following the recent compromise of the nx packages and another wave targeting popular packages, the npm registry was hit by a third…
United States الاتجاهات
- 1. Cowboys 67.3K posts
- 2. Fred Warner 7,403 posts
- 3. Panthers 68.1K posts
- 4. Ravens 62.2K posts
- 5. Zac Taylor 1,801 posts
- 6. Browns 60.7K posts
- 7. Dolphins 44.6K posts
- 8. #KeepPounding 7,168 posts
- 9. Eberflus 9,163 posts
- 10. Colts 54.3K posts
- 11. #FTTB 3,122 posts
- 12. Steelers 63.1K posts
- 13. Rico Dowdle 9,432 posts
- 14. Penn State 66.4K posts
- 15. Drake Maye 20.6K posts
- 16. Cam Ward 1,625 posts
- 17. James Franklin 49K posts
- 18. Chargers 52K posts
- 19. Herbert 15.5K posts
- 20. Pickens 16.8K posts
قد يعجبك
-
 Department of Education and Youth
Department of Education and Youth
@Education_Ire -
 Soufiane
Soufiane
@S0ufi4n3 -
 PT SWARM
PT SWARM
@ptswarm -
 urlscan.io
urlscan.io
@urlscanio -
 GetApp
GetApp
@GetApp -
 Jake | JCyberSec_
Jake | JCyberSec_
@JCyberSec_ -
 Andy Robbins
Andy Robbins
@_wald0 -
 Future of Privacy Forum
Future of Privacy Forum
@futureofprivacy -
 Joe Roosen
Joe Roosen
@JRoosen -
 Ido Naor 🇮🇱
Ido Naor 🇮🇱
@IdoNaor1 -
 IoT Security Foundation
IoT Security Foundation
@IoT_SF -
 KENNEDY M. 🍒
KENNEDY M. 🍒
@tastelikekanndy -
 名古屋生まれの投資家
名古屋生まれの投資家
@nagoyajorge117 -
 Pinny Hikind
Pinny Hikind
@HikindPinny -
 Anika Torruella
Anika Torruella
@DefenceBird
Something went wrong.
Something went wrong.