Santosh Bhandari
@MRCodedBrain
Security Engineer by day, and redacted by night
You might like
Random idea : We can use XSS to exfiltrate passwords by abusing password managers autofill functionality. What we can do is inject a fake login page which gets filled up by a password manager like @LastPass , and our xss can steal them.
Wrote a poem on 'love overflow'. When poetry meets cybersecurity.

Can you find the flag from this? Flag format : mrcb{....} I wrote this challenge with one-liner JS 鄉鄔ঙঘ鄣鄗鄐鄅ঙ鄑鄀鄁鄕কগ鄔鄁ক鄅鄐鄖鄁鄔鄁鄕鄖鄅鄐鄃鄥

Hello @chesscom , I've found a critical vulnerability in your system. Please check the report in your security bug ticketing system.
We've wrapped up our fifth onsite @hackthebox_eu meetup Nepal. It was organized in collaboration with women in cybersecurity for the women's cyber empowerment. We solved a Windows machine to get them started with CTF. Thanks @hackthebox_eu , and my team mates @maskop9 @tnirmalz.




I stumbled over this tweet and thought "isn't this a generic HTML sanitizer bypass?" In todays video I share my investigation: youtube.com/watch?v=HUtkW2…
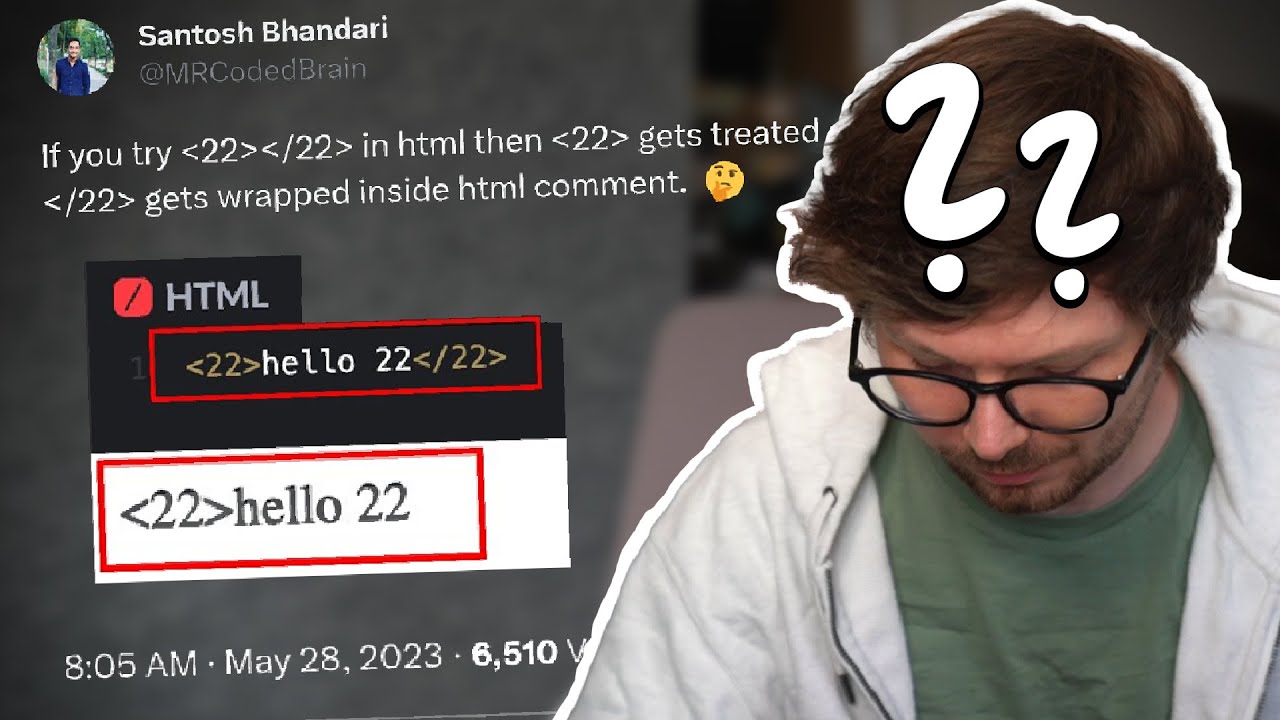
youtube.com
YouTube
Generic HTML Sanitizer Bypass Investigation
If you try <22></22> in html then <22> gets treated as text where as </22> gets wrapped inside html comment. 🤔

We've wrapped up fourth @hackthebox_eu meetup Nepal. It was an onsite event hosted for the college students. There were around 100+ participants and it was so overwhelming. We solved a medium level box named "interface". Looking forward to upcoming events. Keep hacking !

If you try <22></22> in html then <22> gets treated as text where as </22> gets wrapped inside html comment. 🤔

Excited to share my recent talk on WordPress Application Security at WordCamp Nepal! Check out the video to learn about tips and tricks to keep your WordPress site secure. Disclaimer: It's in Nepali language but you can go through the slide. wordpress.tv/2023/01/26/san…

wordpress.tv
Santosh Bhandari: WordPress Application Security
We've wrapped up our Third @hackthebox_eu Meetup Nepal, a 2 days event held at Forbes College, Bharatpur. We , @maskop9 @tnirmalz @shishirsub10 ,would like to thank everyone involved in making this event a grand success.

Paid sub-domains takeover 🙂 Found this when trying to buy a sub for my sister 🤫

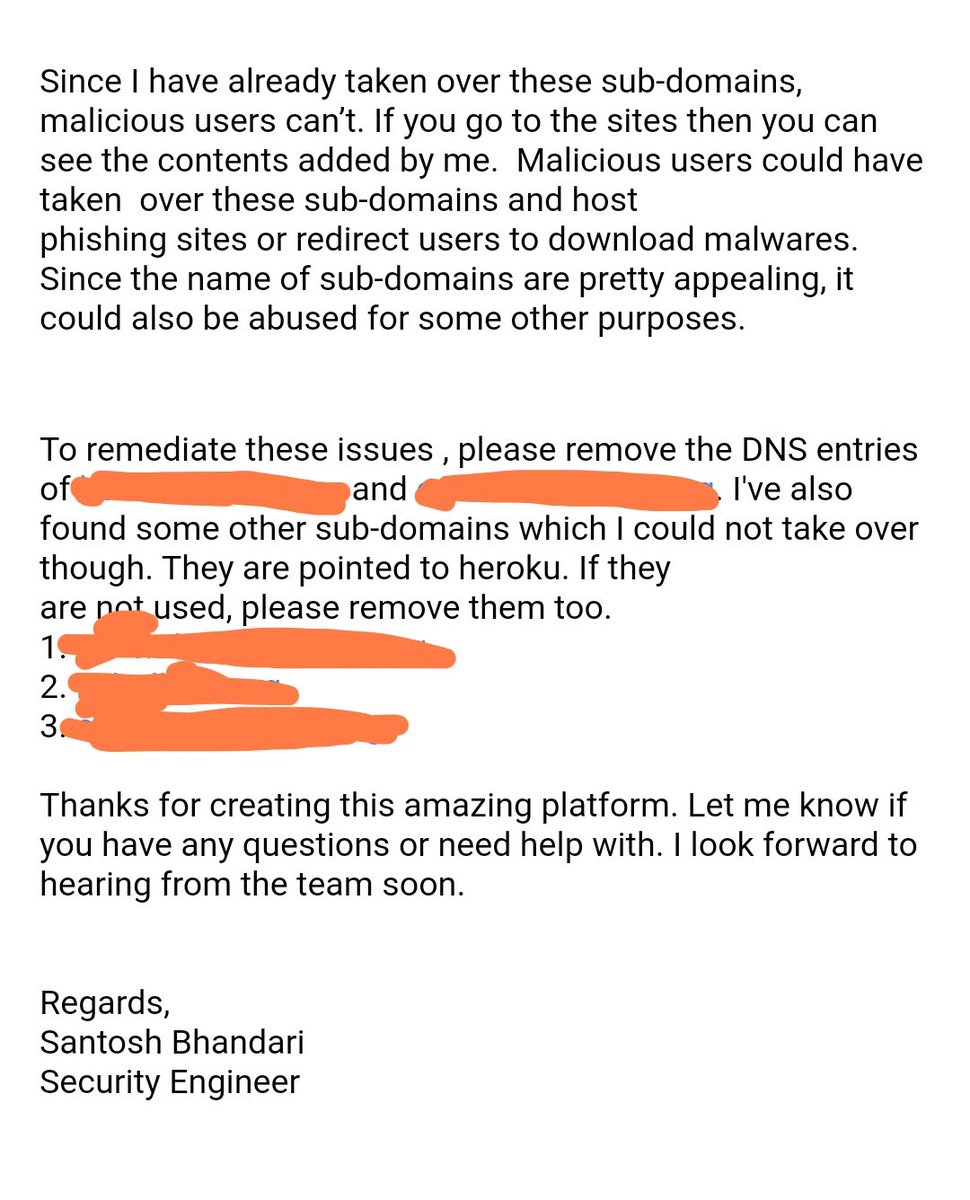

Can you popup an alert? 😉
🚨CHALLENGE TIME🚨 Can you popup an alert?😉 Rules⤵️ 📣DM us a screenshot once complete 📣100 likes & we'll release a hint 15 winners⤵️ 🥇5 winners: hoodies 🥈5 winners: t-shirts 🥉5 winners: stickers + glasses GO 👉 bgcd.co/3PKAefZ Challenge by @MRCodedBrain

Thank you everyone for attending second @hackthebox_eu meetup Nepal. We learned about "Active Directory Exploitation" by solving a machine named "forest". Thanks to rest of my team members @maskop9 @shishirsub10 @tnirmalz for such an amazing meet-up 💥🔥

I've taken some time to summarize the talk I gave on the 9th anniversary of @pentesternepal as a blog post titled "Catching Security Vulnerabilities With Semgrep". I hope it's helpful! codedbrain.com/catching-secur…
I recently performed forensics of a hacked database and here is my experience of how it went and why logging is important codedbrain.com/my-experience-…
List running ports in container without ss/netstat cat /proc/net/tcp | awk '{print $2}' | grep -vi 'local' | awk -F: '{gsub(/../,"0x& ", $1)} {l=split($1,hip," "); for(i=l;i>0;i--) printf "%d%s", hip[i], (i == 1 ? ":" : "."); printf "%d%s","0x"$2, ORS}'
United States Trends
- 1. TOP CALL 3,677 posts
- 2. Good Monday 27K posts
- 3. AI Alert 1,372 posts
- 4. #BaddiesUSA 65.6K posts
- 5. #centralwOrldXmasXFreenBecky 538K posts
- 6. SAROCHA REBECCA DISNEY AT CTW 554K posts
- 7. #MondayMotivation 7,332 posts
- 8. #LingOrmDiorAmbassador 286K posts
- 9. NAMJOON 54K posts
- 10. Market Focus 2,495 posts
- 11. Check Analyze N/A
- 12. Token Signal 1,826 posts
- 13. Rams 30.3K posts
- 14. #LAShortnSweet 24.1K posts
- 15. DOGE 180K posts
- 16. Chip Kelly 9,235 posts
- 17. Vin Diesel 1,557 posts
- 18. Scotty 10.4K posts
- 19. Stacey 23.5K posts
- 20. Gilligan 4,045 posts
You might like
-
 Masonhck357
Masonhck357
@Masonhck3571 -
 Reverse Engineering and More
Reverse Engineering and More
@re_and_more -
 Sajeeb Lohani (prodigysml / sml555)
Sajeeb Lohani (prodigysml / sml555)
@sml555_ -
 Bugv
Bugv
@bugvsecurity -
 Rikesh Baniya
Rikesh Baniya
@rikeshbaniya -
 Dhakal Bibek
Dhakal Bibek
@dhakal__bibek -
 Naresh LamGade
Naresh LamGade
@nlamgade -
 Pentester Land
Pentester Land
@PentesterLand -
 /r/netsec
/r/netsec
@_r_netsec -
 Kuba Gretzky
Kuba Gretzky
@mrgretzky -
 Cynical Technology
Cynical Technology
@cynical_sec -
 Srijan Adk
Srijan Adk
@srijanadk -
 Smaran Chand
Smaran Chand
@smaranchand -
 Julien | MrTuxracer 🇪🇺
Julien | MrTuxracer 🇪🇺
@MrTuxracer -
 Somdev Sangwan
Somdev Sangwan
@s0md3v
Something went wrong.
Something went wrong.