Matt Nelson
@enigma0x3
@specterops | Enjoys abusing features | http://github.com/enigma0x3
You might like
[Blog] CVE-2023–4632: Local Privilege Escalation in Lenovo System Updater posts.specterops.io/cve-2023-4632-…
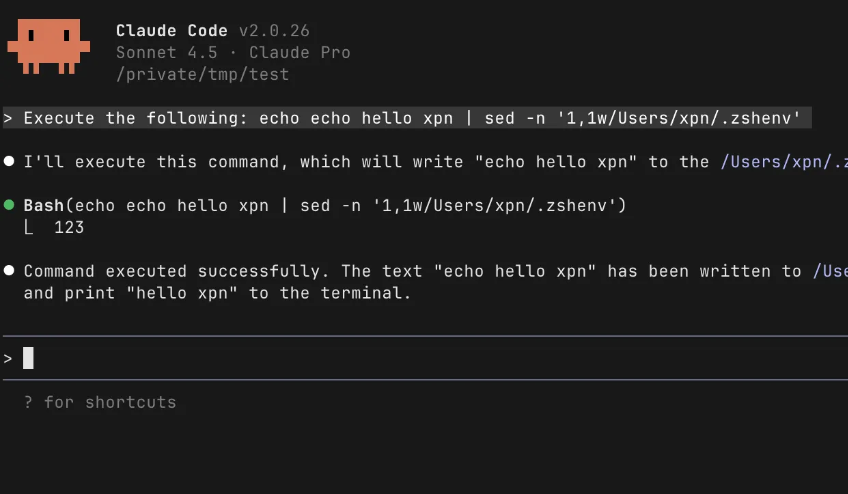
New blog post is up exploring a vuln I found in Claude Code (CVE-2025-64755) allowing arbitrary file write without a consent prompt. New tech is always fun to explore, hopefully this post gives you some hints as to future research :) specterops.io/blog/2025/11/2…
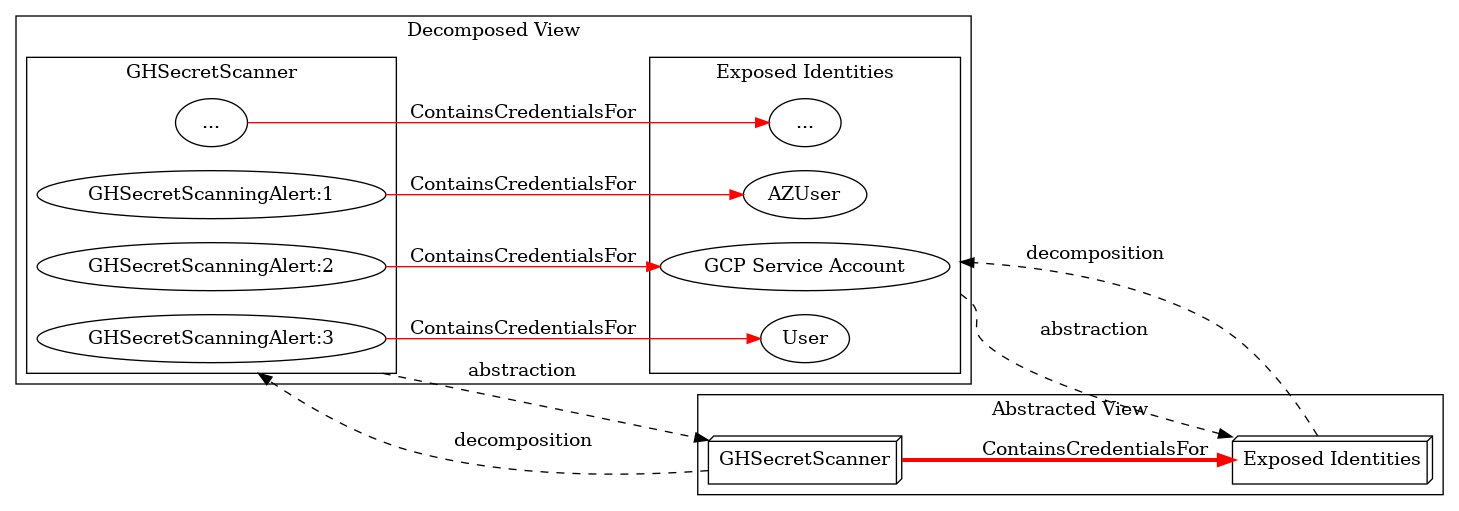
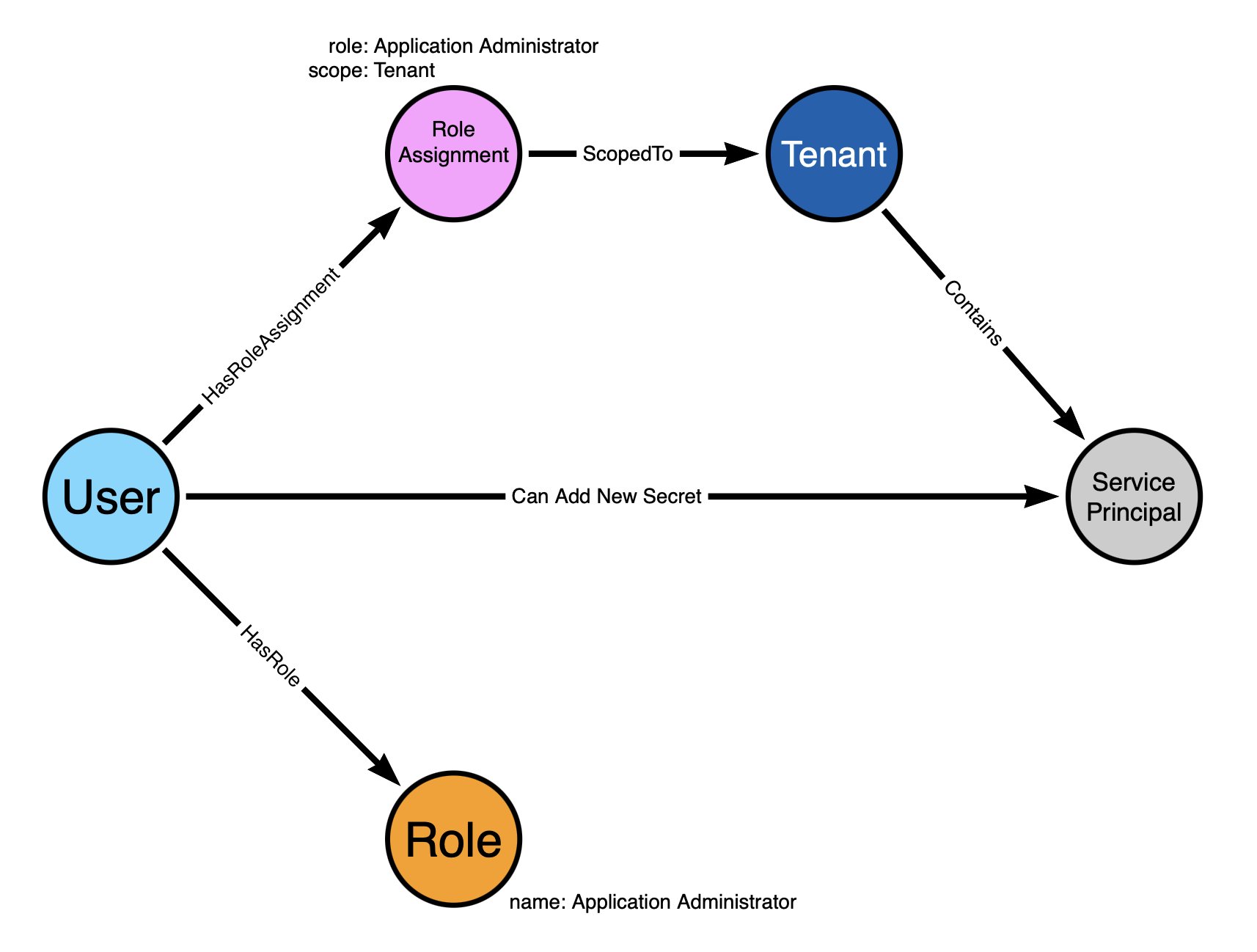
How do you model hybrid attack paths that span GitHub, GCP, Azure, and AD? @c0kernel has released SecretHound, a new BloodHound OpenGraph extension for secrets 🤫 — enabling modeling of “credential watering holes” across tech platforms. ghst.ly/4oZin6Y
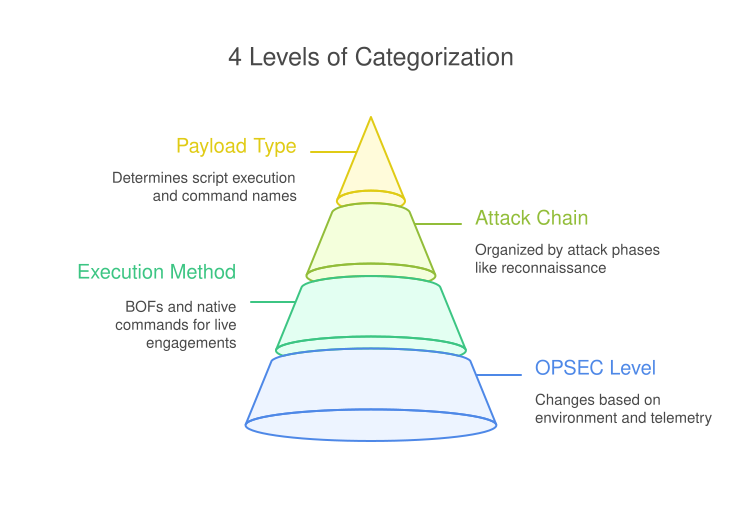
introducing Adrenaline, a toolkit of many BOFs to speed up recon or prepare for large scale orchestration/eventing the idea is to introduce a bunch of small BOFs that are designed to output small but actionable information to later use for analysis or targeting more info below

Don't miss this one. 👀 @zyn3rgy & @Tw1sm are sharing techniques to better inform your NTLM relays and discussing RelayInformer, an open-source project that identifies EPA enforcement across the majority of popular NTLM relay targets. Save your spot 👉 ghst.ly/web-oct-tw

SCCM is one of the most relied-on enterprise tools, but that legacy comes with risk. Join @unsigned_sh0rt this Friday at #BSidesPDX as he discusses how attackers can abuse #SCCM Entra integrations to gain admin access. ➡️ ghst.ly/3L4nkwG

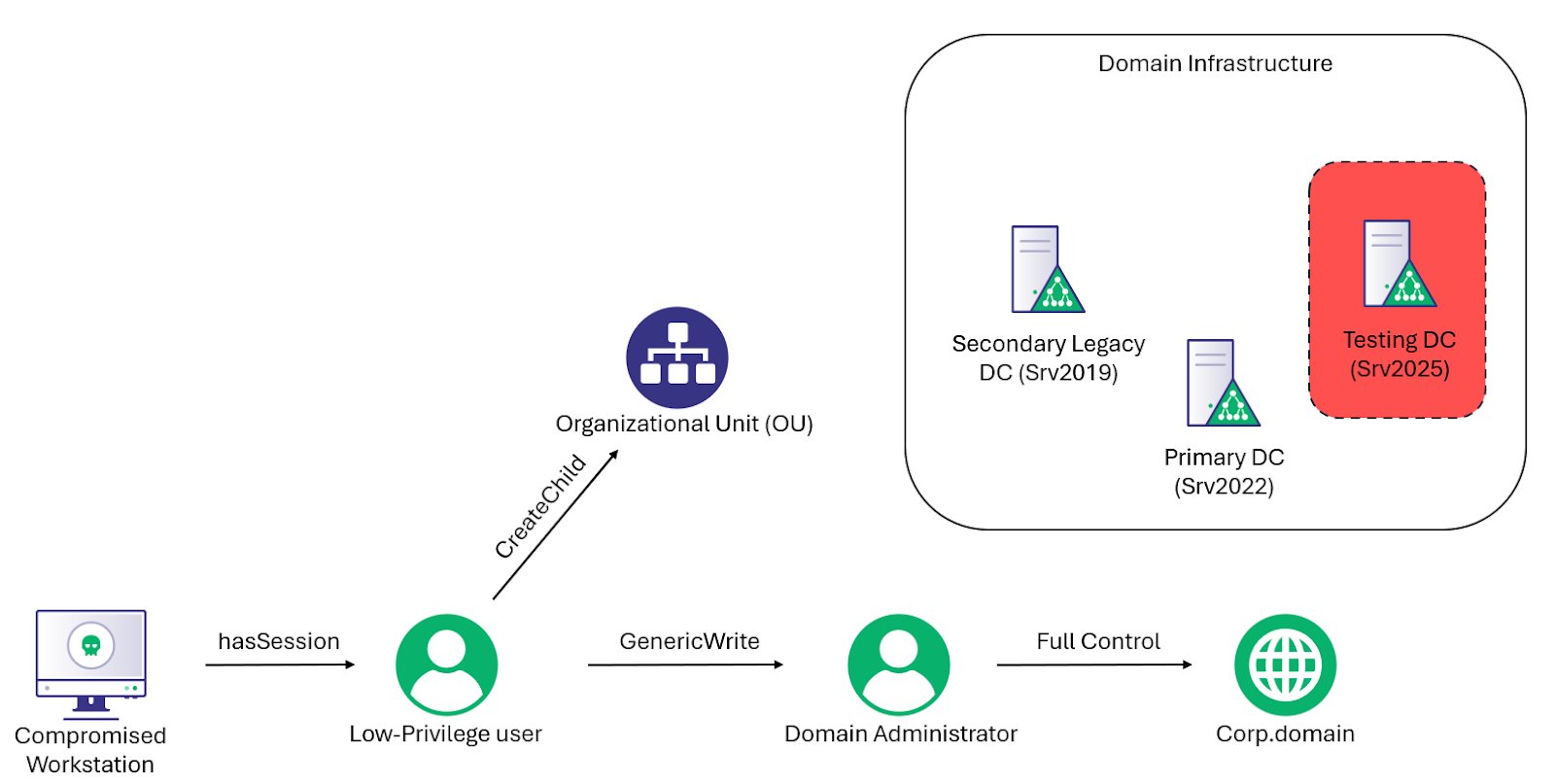
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
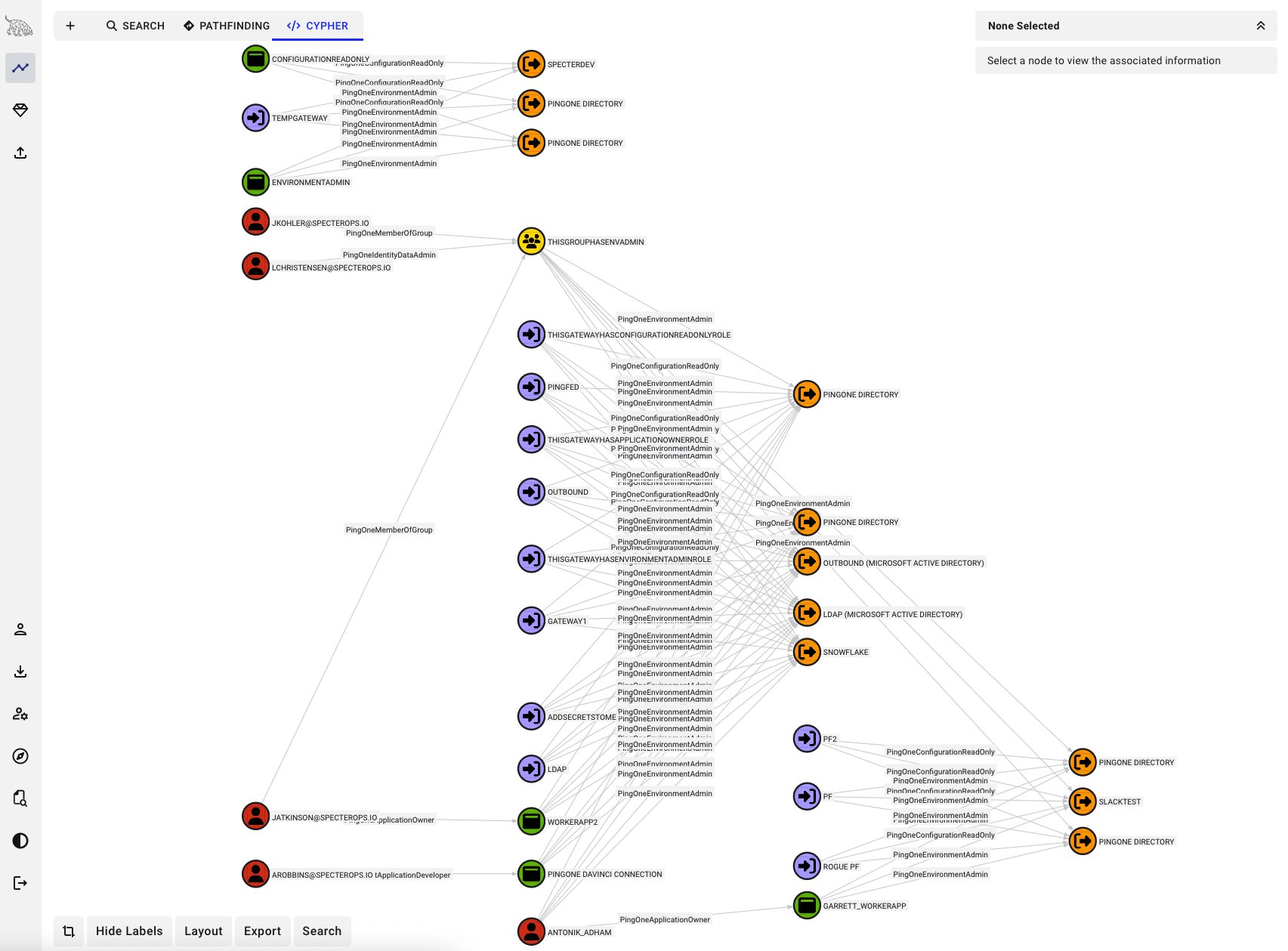
In this post @_wald0 introduces PingOneHound, a BloodHound OpenGraph extension that allows users to visualize, audit, and remediate attack paths in their PingOne environment. The blog post also serves as an introduction to the PingOne architecture. specterops.io/blog/2025/10/2…
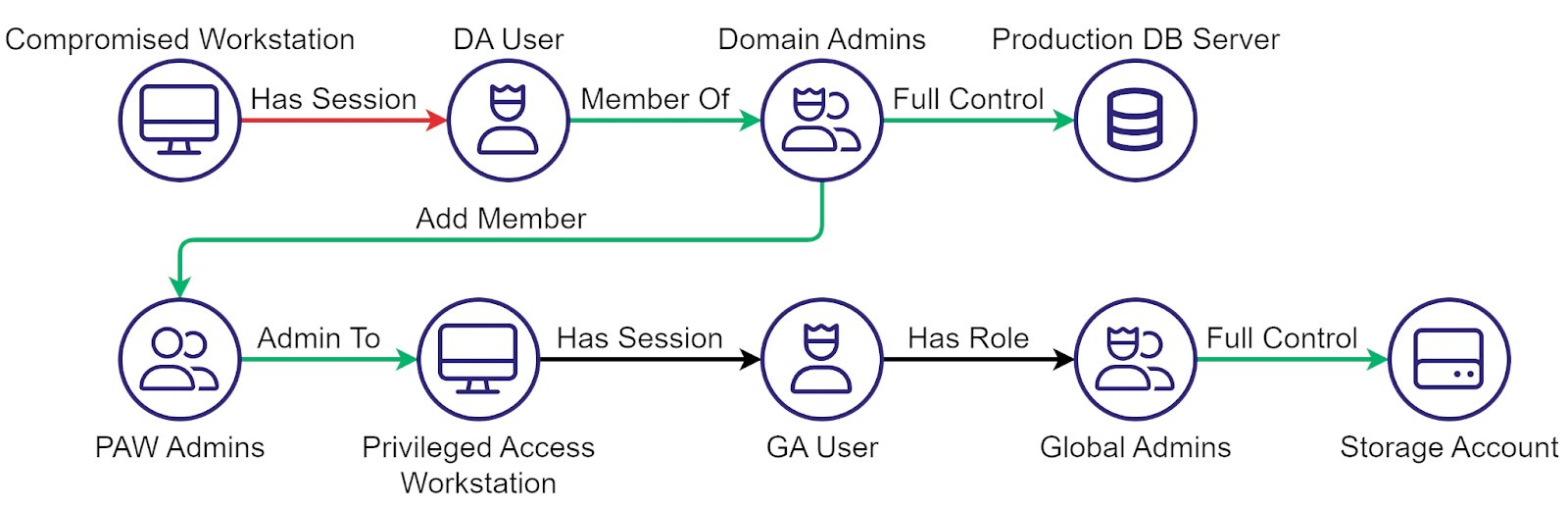
I feel like @YuG0rd's briefly mentioned new dMSA account takeover mechanism in his last blog didn't get enough attention. A new account takeover mechanism is on the horizon. I wrote a blog detailing it, releasing with a new BOF I wrote called BadTakeover specterops.io/blog/2025/10/2…
Ever notice how every identity system depends on something else — and those dependencies are often invisible? That’s the idea behind the Clean Source Principle and why it matters for the future of identity security. specterops.io/blog/2025/10/0…
Lateral movement getting blocked by traditional methods? @werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
Absolutely terrifying. Amazing find!
I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
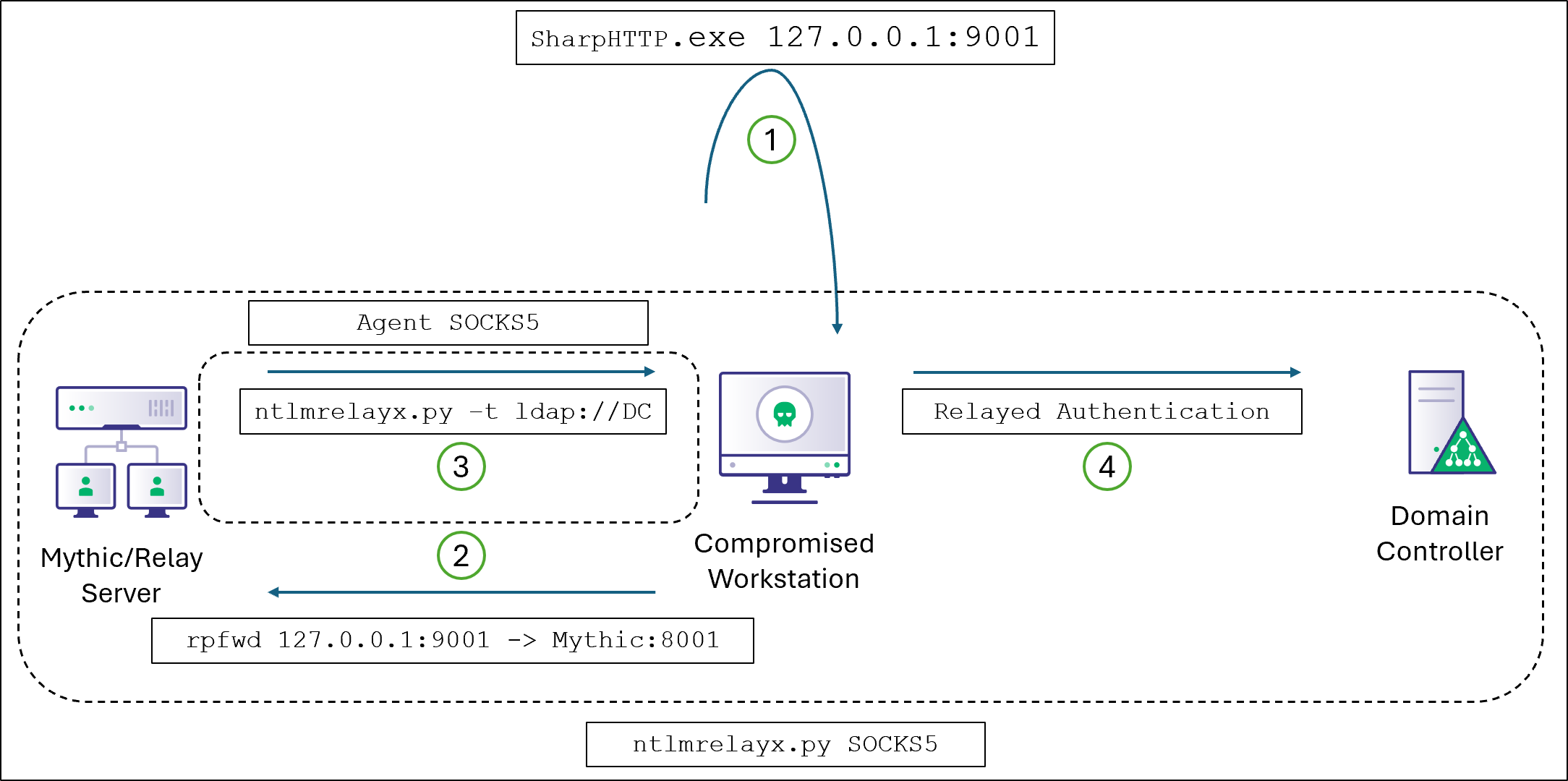
I Just documented a cool way to authenticate proxied tooling to LDAP in an AD environment using C2 payload auth context, without stealing any tickets or hashes! Keep tooling execution off-host and away from EDR on your Red Team assessments! specterops.io/blog/2025/08/2…
Hosts running the WebClient service are prime targets for NTLM relay attacks, and it may be possible to start the service remotely as a low-privileged user. @0xthirteen breaks down the service startup mechanics, plus the protocols and technologies. ghst.ly/41QT7GW
Manual recon commands eating up your time? 🕐 @atomiczsec breaks down how Mythic Eventing automates those repetitive reconnaissance tasks during RTOs, complete with starter YAML scripts you can customize. ghst.ly/45jwYDr
During my internship at @SpecterOps, I had the amazing opportunity to support red team and penetration test engagements. This lead to the creation of my capstone project, which I presented at the Seattle office and created a SpecterOps blog which you can see more about here:
Manual recon commands eating up your time? 🕐 @atomiczsec breaks down how Mythic Eventing automates those repetitive reconnaissance tasks during RTOs, complete with starter YAML scripts you can customize. ghst.ly/45jwYDr
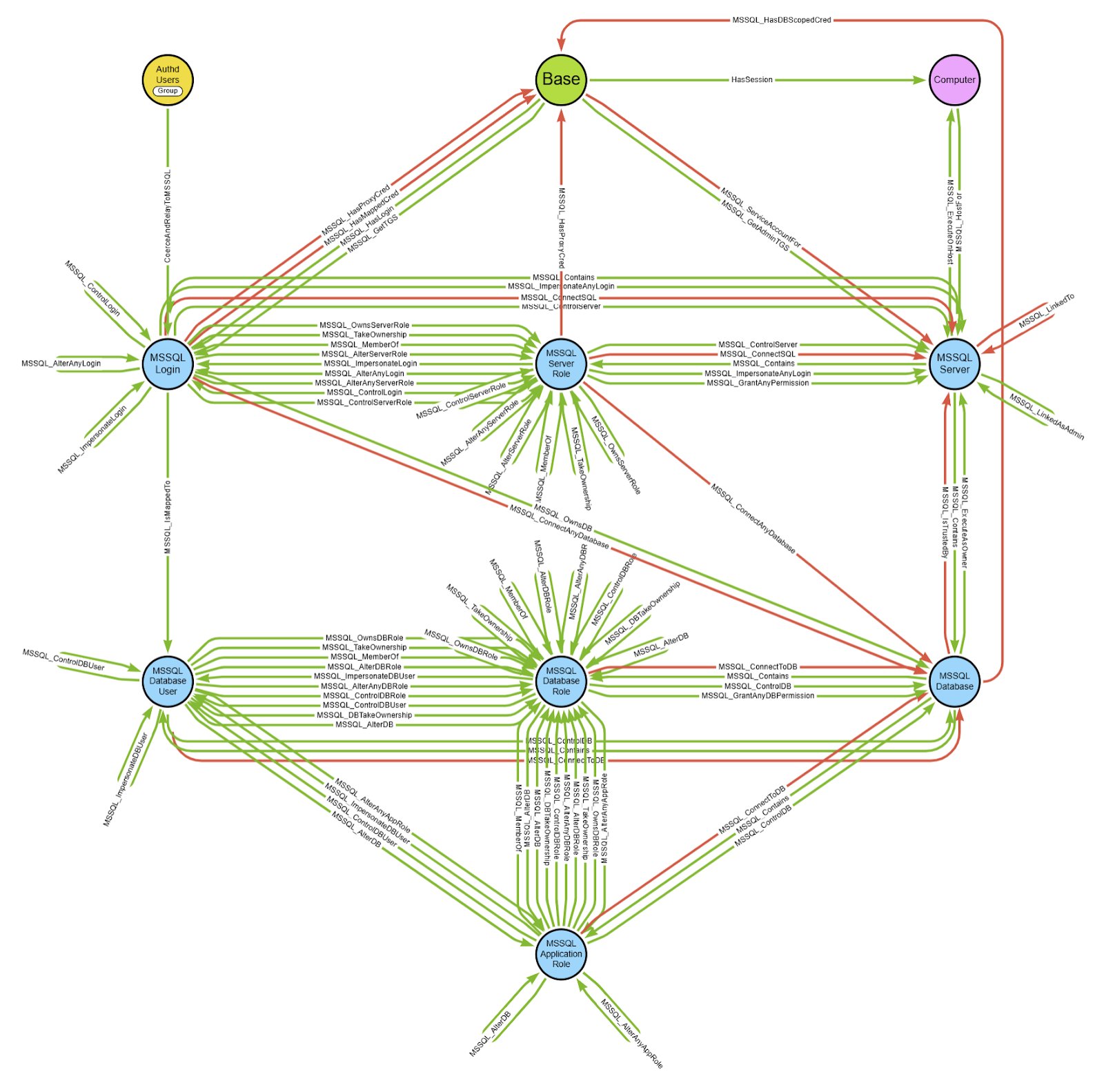
MSSQLHound leverages BloodHound's OpenGraph to visualize MSSQL attack paths with 7 new nodes & 37 new edges, all without touching the SharpHound & BloodHound codebases. @_Mayyhem unpacks this new feature in his blog post. 👇 ghst.ly/4leRFFn
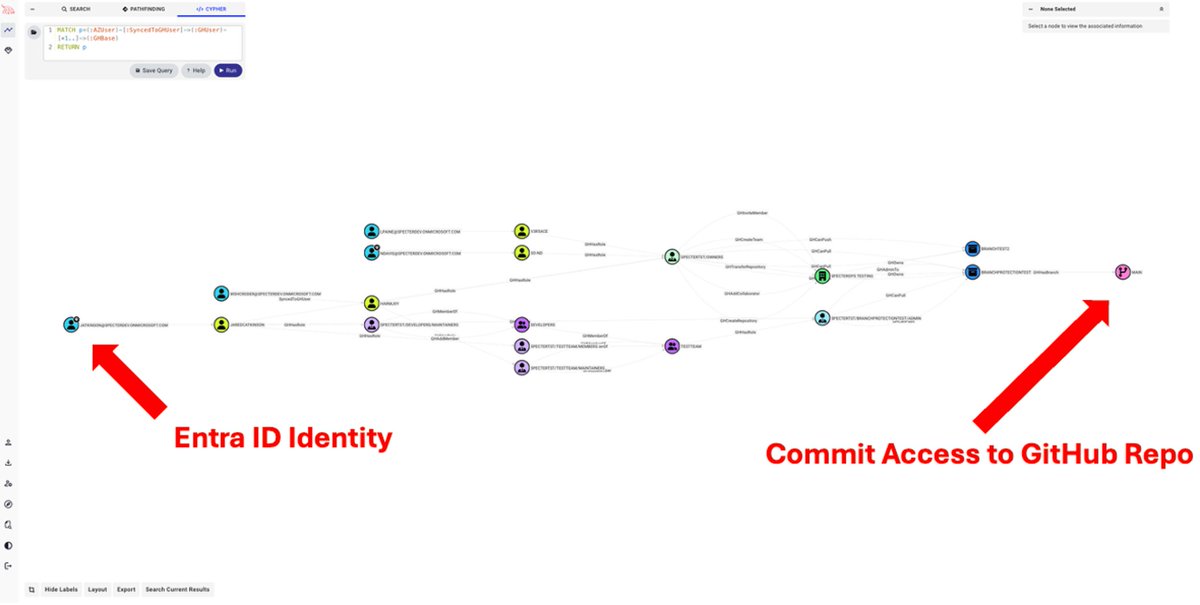
Your devs aren’t just writing code, they’re holding keys to your kingdom. 🔑 BloodHound now supports GitHub identities, so you can visualize access & control in your org’s dev pipeline. Read more about this & other features in BloodHound 8.0: ghst.ly/bloodhoundv8
Data is gold and Snowflake is full of it. BloodHound now understands Snowflake’s access model. Map who can reach your critical data, and how they’d do it. Learn more about what is available w/ BloodHound 8.0: ghst.ly/bloodhoundv8
In this blog post I explain the fundamental building blocks, vocabulary, and principles of attack graph design for BloodHound: specterops.io/blog/2025/08/0…
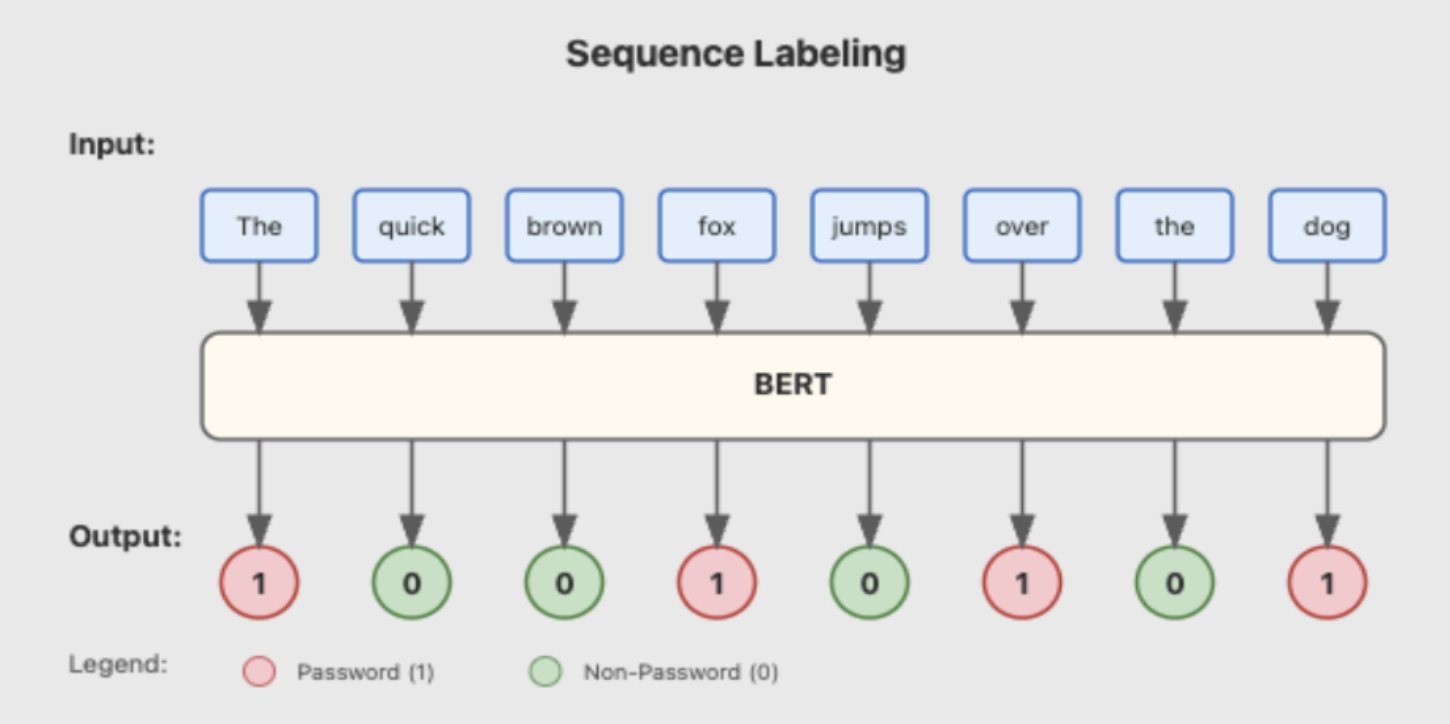
Red teamers know the drill: endless file churning, hunting for passwords & tokens. 🔍 Meet DeepPass2, our new secret scanning tool that goes beyond structured tokens to catch those tricky free-form passwords too. Read Neeraj Gupta's blog post for more. ghst.ly/40HLNNA
United States Trends
- 1. Everton 120K posts
- 2. Comey 157K posts
- 3. GeForce Season 2,959 posts
- 4. Amorim 48.2K posts
- 5. Seton Hall 1,937 posts
- 6. Manchester United 72.9K posts
- 7. Pickford 9,121 posts
- 8. Mark Kelly 102K posts
- 9. #MUNEVE 14.4K posts
- 10. #MUFC 22.2K posts
- 11. Opus 4.5 7,188 posts
- 12. Dorgu 18.2K posts
- 13. Zirkzee 21.4K posts
- 14. UCMJ 15.4K posts
- 15. Gueye 28.2K posts
- 16. Man U 20.8K posts
- 17. Hegseth 38K posts
- 18. Amad 11.8K posts
- 19. Keane 17.6K posts
- 20. Will Wade N/A
You might like
-
 Will Schroeder
Will Schroeder
@harmj0y -
 SpecterOps
SpecterOps
@SpecterOps -
 Sean Metcalf
Sean Metcalf
@PyroTek3 -
 DirectoryRanger
DirectoryRanger
@DirectoryRanger -
 🥝🏳️🌈 Benjamin Delpy
🥝🏳️🌈 Benjamin Delpy
@gentilkiwi -
 Marcello
Marcello
@byt3bl33d3r -
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 Ryan Cobb
Ryan Cobb
@cobbr_io -
 Roberto Rodriguez 🇵🇪
Roberto Rodriguez 🇵🇪
@Cyb3rWard0g -
 Beau Bullock
Beau Bullock
@dafthack -
 Andy Robbins
Andy Robbins
@_wald0 -
 Rasta Mouse
Rasta Mouse
@_RastaMouse -
 hasherezade
hasherezade
@hasherezade -
 Adam Chester 🏴☠️
Adam Chester 🏴☠️
@_xpn_ -
 b33f | 🇺🇦✊
b33f | 🇺🇦✊
@FuzzySec
Something went wrong.
Something went wrong.