CodeX
@codex_tf2
advanced persistent clown 🤡 📕 redteam blog: http://codex-7.gitbook.io 🛠️ github: http://github.com/CodeXTF2
You might like
[Pin] My maldev link dump if anyone else wants to read :D (Will be updated) raw.githubusercontent.com/CodeXTF2/malde…
Added my ICMP, NTP and Websocket C2 channel examples to the public repo. github.com/CodeXTF2/Custo… Also accompanying blog post explaining the template: codex-7.gitbook.io/codexs-termina… pls no flame bad code :D Websocket channel in action:
Added a few more example C2 channels to the Cobalt Strike custom c2 channel template on top of the existing file read/write PoC: - named pipe - TCP - UDP github.com/CodeXTF2/Custo…
Open sourced my template code for implementing custom C2 channels via a UDRL hook in Cobalt Strike Hopefully this makes developing custom c2 channels for CS easier, because externalC2 spec is a pain. Or just use the upcoming UDC2 interface /shrug github.com/CodeXTF2/Custo…
Been using @_RastaMouse 's crystal kit as a UDRL dev template for the past few days and did quite a few cool things, among them was implementing a custom c2 channel template (in this case, PoC using files on disk as the channel) using IAT hooks on the wininet functions

mfw hashcat v7 b4 gta6
hashcat v7.0.0 released! After nearly 3 years of development and over 900,000 lines of code changed, this is easily the largest release we have ever had. Detailed writeup is available here: hashcat.net/forum/thread-1…

Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…
Swimming deep inside Windows Security Center service to re-engineer API access allowing to disable Windows Defender. COM interface reconstruction and integrity checks bypassed to inform WD that its not the-boss-in-the-house anymore... A post by @es3n1n. Nicely done! Repo:…

This is my research project in creating read, write and allocate primitives that can be turned into an injection in order to evade certain telemetry which I presented last year in RedTreat. I hope everyone likes it \m/. trickster0.github.io/posts/Primitiv…
Truly excited for the upcoming workshop. Covering modern ransomware evasion & detection and also implementing your own ransomware/decryptor for Windows, MacOS and Linux. See you soon! 👻


So excited to speak at #BHUSA for the first time this year! I'll talk about training LLMs on verifiable tasks (including what exactly that means) with a case study automating some maldev work.
I'm finally releasing a project that I've been working on for a little while now. Here's Boflink, a linker for Beacon Object Files. github.com/MEhrn00/boflink Supporting blog post about it. blog.cybershenanigans.space/posts/boflink-…
I'm super happy to announce an operationally weaponized version of @YuG0rd's BadSuccessor in .NET format! With a minimum of "CreateChild" privileges over any OU it allows for automatic escalation to Domain Admin (DA). Enjoy your inline .NET execution! github.com/logangoins/Sha…
Learn to evade and strengthen security controls by building your own ransomware. For a teaser on what to expect, check out my talk 'Windows Ransomware Detection' youtu.be/5t67BFcC-MQ Excited to have y'all join us next month.

youtube.com
YouTube
OnlyMalware: Windows Ransomware Detection
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: volatilityfoundation.org/announcing-the…
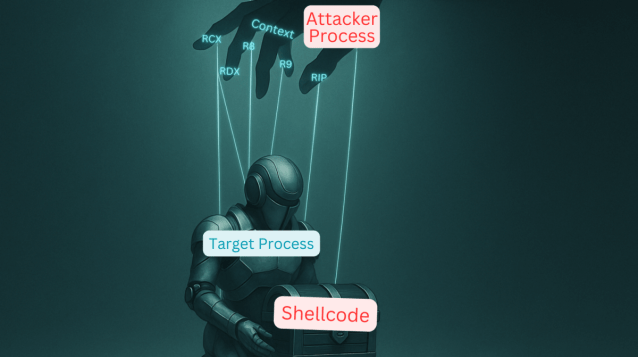
What if you skipped VirtualAlloc, skipped WriteProcessMemory and still got code execution? We explored process injection using nothing but thread context. Full write-up + PoCs: blog.fndsec.net/2025/05/16/the…
United States Trends
- 1. Lamar 33.7K posts
- 2. Ravens 41.2K posts
- 3. Ravens 41.2K posts
- 4. Chiefs 100K posts
- 5. Joe Burrow 12.8K posts
- 6. Cowboys 84.4K posts
- 7. Zay Flowers 2,497 posts
- 8. Derrick Henry 3,759 posts
- 9. Zac Taylor 2,263 posts
- 10. Tanner Hudson 1,131 posts
- 11. Mahomes 31.4K posts
- 12. Cam Boozer 1,686 posts
- 13. #CINvsBAL 2,138 posts
- 14. Tinsley 1,500 posts
- 15. Sarah Beckstrom 175K posts
- 16. #WhoDey 2,322 posts
- 17. Myles Murphy N/A
- 18. Duke 19.2K posts
- 19. Pickens 31.7K posts
- 20. Jason Garrett N/A
You might like
-
 Octoberfest7
Octoberfest7
@Octoberfest73 -
 NULL
NULL
@NUL0x4C -
 klez
klez
@KlezVirus -
 Josh
Josh
@passthehashbrwn -
 Moloch
Moloch
@LittleJoeTables -
 Ido Veltzman
Ido Veltzman
@Idov31 -
 waldoirc
waldoirc
@waldoirc -
 x86matthew
x86matthew
@x86matthew -
 Austin
Austin
@ilove2pwn_ -
 S3cur3Th1sSh1t
S3cur3Th1sSh1t
@ShitSecure -
 mgeeky | Mariusz Banach
mgeeky | Mariusz Banach
@mariuszbit -
 an0n
an0n
@an0n_r0 -
 Kyle Avery
Kyle Avery
@kyleavery -
 d1rkmtr
d1rkmtr
@d1rkmtr -
 Bobby Cooke
Bobby Cooke
@0xBoku
Something went wrong.
Something went wrong.