CAPE Sandbox
@CapeSandbox
Payloads or it didn't happen. https://github.com/kevoreilly/CAPEv2
คุณอาจชื่นชอบ
Malware abusing the finger protocol (this one makes a comeback now and again). bleepingcomputer.com/news/security/… Caught with @CapeSandbox :)

New cmd.exe batch deobfuscation capability integrated in CAPE! FindFixAndRun hook😎 For example: capesandbox.com/analysis/23842/ Thanks KingKDot github.com/KingKDot/Exorc…🙏 and KillerInstinct for the integration!

#Amadey config extraction capesandbox.com/analysis/21966/ Thanks @YungBinary

Dropping a new malware config parser for #Amadey! Update your CAPEv2 parsers: > sudo -u cape bash -c 'cd /opt/CAPEv2 && poetry add CAPE-parsers@latest && systemctl restart cape cape-web cape-processor' Check it out here: github.com/CAPESandbox/CA…

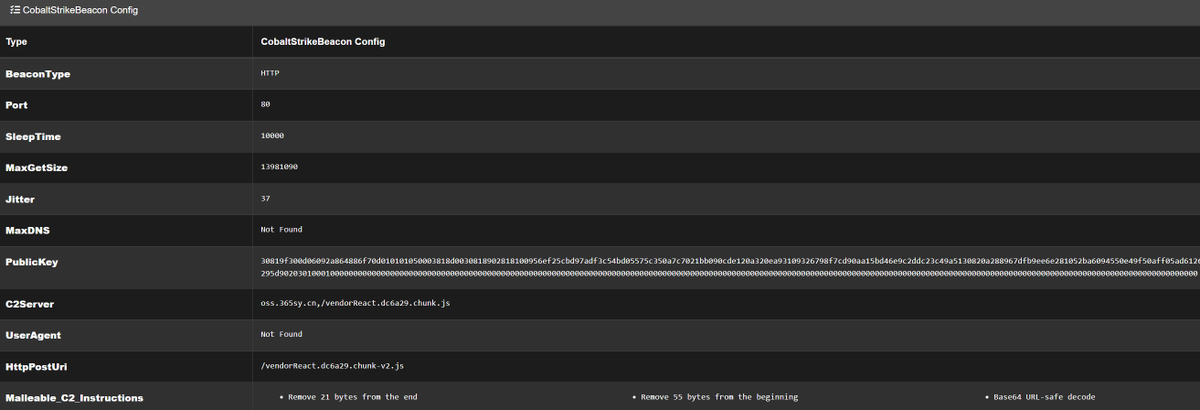
SLOW#TEMPEST #CobaltStrike config & payload extraction capesandbox.com/analysis/14224/
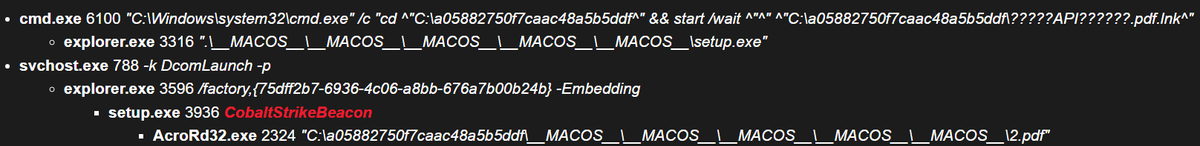
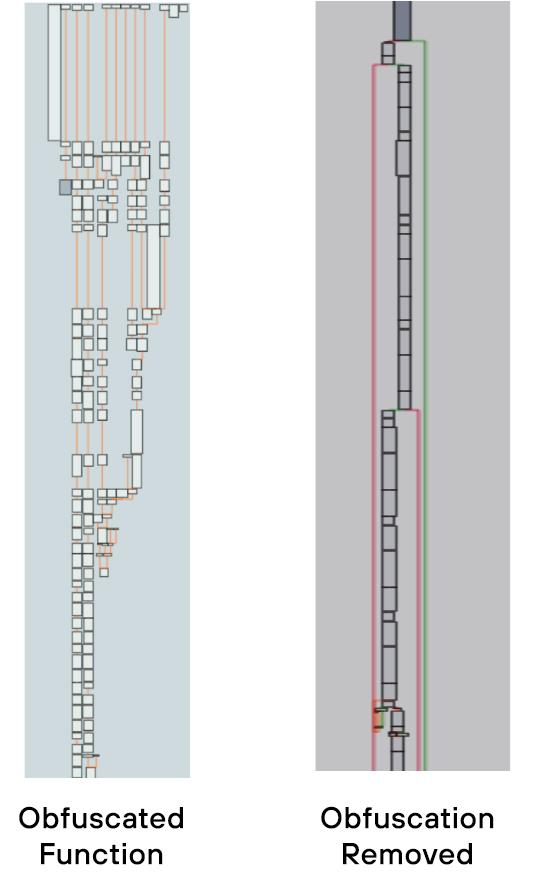
Palo Alto Networks researchers explore the obfuscation techniques employed by the malware authors in the SLOW#TEMPEST campaign and highlight methods and code that can be used to detect and defeat these techniques. unit42.paloaltonetworks.com/slow-tempest-m…
#Lumma config & payload extraction capesandbox.com/analysis/13458/ Thanks @YungBinary


#Amatera payload extraction & direct syscall capture capesandbox.com/analysis/11082/



New Octowave Loader sample > Amatera Stealer. 0 VT. Proofpoint rules detect the traffic. My Yara rule detects the installer. Adobe printer driver sideloads tbb.dll, tbb.dll loads app-2.3.dll which gets stego from blood.wav, uses zxing.presentation.dll. virustotal.com/gui/file/f5c8b…


We're proud to announce our support for @CapeSandbox , a fully open-source malware sandbox developed and maintained by a dedicated group of volunteers. After almost a year of downtime, we are extremely happy that we were able to help CAPE get back online again! 🥳 👉…

[1/n] In the hope that it might be useful to someone, I am happy to share with the community my basic (and cheap) implementation of a @CapeSandbox in physical machine config, integrating Elastic Stack and Elastic agents, Suricata, Aurora-Lite agent and Sysmon. #malwareanalysis
![marsomx_'s tweet image. [1/n] In the hope that it might be useful to someone, I am happy to share with the community my basic (and cheap) implementation of a @CapeSandbox in physical machine config, integrating Elastic Stack and Elastic agents, Suricata, Aurora-Lite agent and Sysmon. #malwareanalysis](https://pbs.twimg.com/media/Ge1NHBdXkAAVqfx.jpg)
#Lumma config & payload extraction



It is really interesting to find anti-VM techniques being used by threat actors in the wild. This is a PowerShell script protecting a #Lumma Stealer build and being spread on YouTube videos. In this case, this was enough to make @anyrun_app to fail based on Screen Resolution



More #BruteRatel...



#BruteRatel #Latrodectus A New JS Nasty Obfuscation #TTPs & #IOCs - Multi-Line Comments🚨 [+] JS T1059.007 [+] Msiexec T1218.007 TA abuses multi-line (/* ,*/) comments to hide malcode and bypass detections - VT detections 20/62 Distro MSI IP: tp://95.164.17[.]212/BEST[.]msi
![Max_Mal_'s tweet image. #BruteRatel #Latrodectus A New JS Nasty Obfuscation #TTPs & #IOCs - Multi-Line Comments🚨
[+] JS T1059.007
[+] Msiexec T1218.007
TA abuses multi-line (/* ,*/) comments to hide malcode and bypass detections - VT detections 20/62
Distro MSI IP: tp://95.164.17[.]212/BEST[.]msi](https://pbs.twimg.com/media/GZNpAq5X0AA-aoX.jpg)
![Max_Mal_'s tweet image. #BruteRatel #Latrodectus A New JS Nasty Obfuscation #TTPs & #IOCs - Multi-Line Comments🚨
[+] JS T1059.007
[+] Msiexec T1218.007
TA abuses multi-line (/* ,*/) comments to hide malcode and bypass detections - VT detections 20/62
Distro MSI IP: tp://95.164.17[.]212/BEST[.]msi](https://pbs.twimg.com/media/GZNq39UXwAAP5gU.png)
![Max_Mal_'s tweet image. #BruteRatel #Latrodectus A New JS Nasty Obfuscation #TTPs & #IOCs - Multi-Line Comments🚨
[+] JS T1059.007
[+] Msiexec T1218.007
TA abuses multi-line (/* ,*/) comments to hide malcode and bypass detections - VT detections 20/62
Distro MSI IP: tp://95.164.17[.]212/BEST[.]msi](https://pbs.twimg.com/media/GZNreiNXUAAdXsT.jpg)
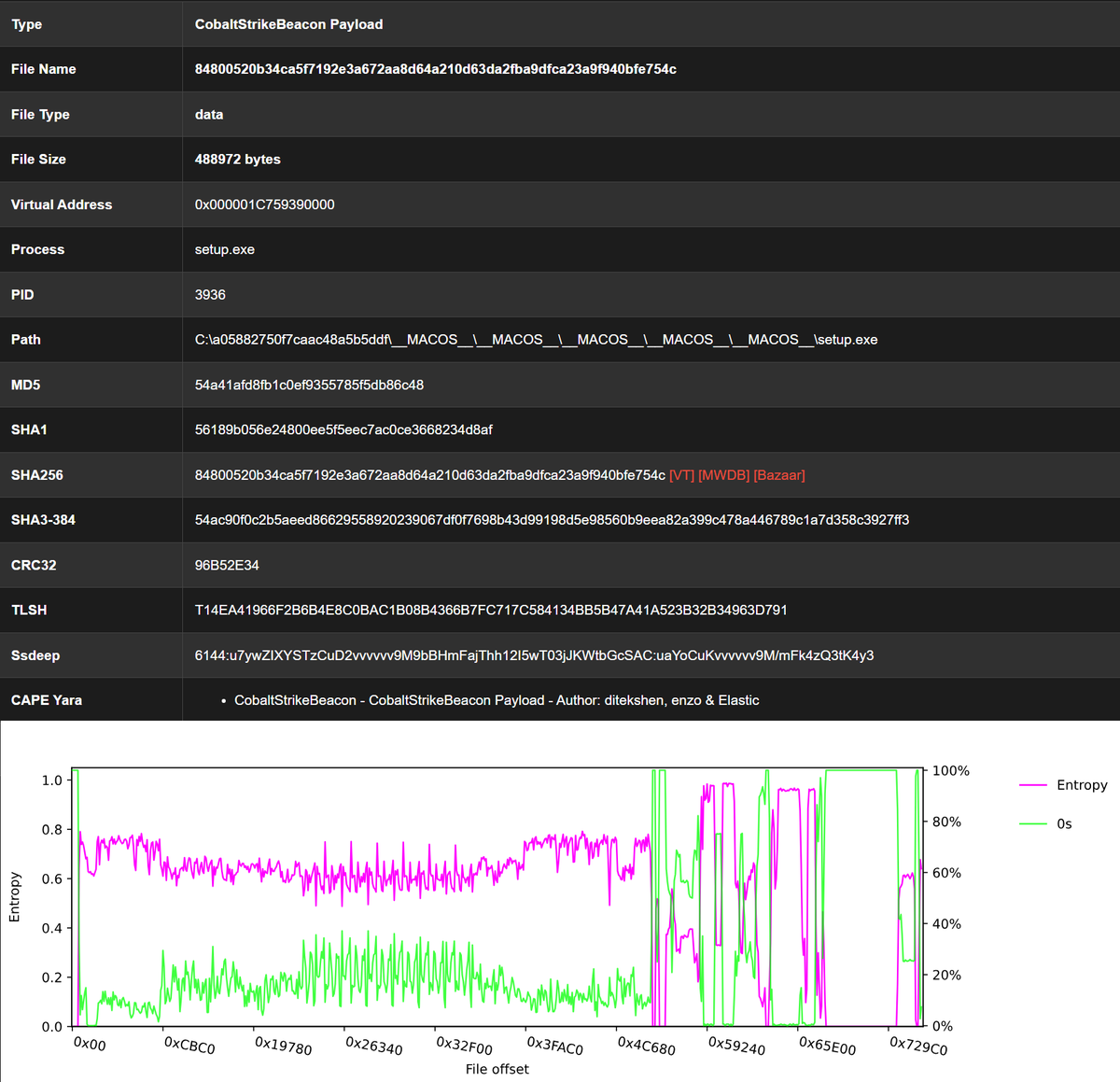
#BruteRatel config & payload extraction, syscall capture #BRC4




#Latrodectus - #BruteRatel - .pdf > url > .js > .msi > .dll 18.09.2024 👇 wscript.exe Document-21-29-08.js msiexec.exe /V MSI152A.tmp /DontWait rundll32.exe C:\Users\Admin\AppData\Roaming\x64_stealth.dll, clBuildProgram (1/3) 👇 IOC's github.com/pr0xylife/Latr…

capa v7.0 dynamic output now fully integrated in CAPE Sandbox 🎉 For example: capesandbox.com/analysis/475639

Dynamic #capa: Exploring Executable Run-Time Behavior with the @CapeSandbox mandiant.com/resources/blog…
We've uploaded our lecture on Automating Malware Triage from our Introduction to Malware Binary Triage course. Huge shout out to @unpacme @anyrun_app @malpedia @abuse_ch @cybercentre_ca @CapeSandbox @hatching_io @R3MRUM for the amazing projects mentioned youtu.be/8aWnFld4qgc

youtube.com
YouTube
Automating Malware Triage (Course Preview)
Lightweight blog alert! This post goes over fast Bumblebee unpacking and configuration extraction. I've come across posts where authors do the unpacking manually. I use @CapeSandbox. Don't sleep on CAPEv2! nikhilh-20.github.io/blog/fast_furi…
United States เทรนด์
- 1. #WWERaw 71.6K posts
- 2. Moe Odum N/A
- 3. Purdy 27.7K posts
- 4. Panthers 37.2K posts
- 5. Bryce 20.8K posts
- 6. Finch 14.1K posts
- 7. Timberwolves 3,650 posts
- 8. 49ers 40.9K posts
- 9. Canales 13.2K posts
- 10. Gonzaga 3,901 posts
- 11. Keegan Murray 1,309 posts
- 12. Penta 10.4K posts
- 13. #FTTB 5,727 posts
- 14. Niners 5,753 posts
- 15. Mac Jones 4,915 posts
- 16. Zags N/A
- 17. Amen Thompson 2,069 posts
- 18. Malik Monk N/A
- 19. Gunther 15.1K posts
- 20. Streaming 2.0 2,218 posts
คุณอาจชื่นชอบ
-
 Arkbird
Arkbird
@Arkbird_SOLG -
 Cryptolaemus
Cryptolaemus
@Cryptolaemus1 -
 ANY.RUN
ANY.RUN
@anyrun_app -
 abuse.ch
abuse.ch
@abuse_ch -
 Shadow Chaser Group
Shadow Chaser Group
@ShadowChasing1 -
 RedDrip Team
RedDrip Team
@RedDrip7 -
 Dee
Dee
@ViriBack -
 UNPACME
UNPACME
@unpacme -
 reecDeep
reecDeep
@reecdeep -
 Joe Security
Joe Security
@joe4security -
 MalShare
MalShare
@mal_share -
 ExecuteMalware
ExecuteMalware
@executemalware -
 Tommy M (TheAnalyst)
Tommy M (TheAnalyst)
@ffforward -
 James
James
@James_inthe_box -
 avman
avman
@avman1995
Something went wrong.
Something went wrong.