
OSSEM
@OSSEM_Project
Open Source Security Event Metadata ! Data engineers! #ThreatHunting @OTR_Community
Talvez você curta
Thank you so much for sharing the @OSSEM_Project Detection Model 🙏 and all your contributions to it! Very happy to see the project helping others in the community 🌎🎊 github.com/OTRF/OSSEM-DM/…
Will be coming on Windows soon ;)
🚀 Any NEW fields on the schemas for #SysmonForLinux events compared to Windows🤔? @Cyb3rPandaH used our #Sysmon for Windows & Linux data dictionaries in a python 🐍 script to answer that😎 ✅ ParentUser (ProcessCreate) ✅ User (EID 5,9,11) 🖇️ Script: github.com/OTRF/OSSEM-DD/…


🚨 Learning how to install #Sysmon for Linux 🐧 & send security events to #AzureSentinel in a research lab environment!! 🧪 #MSTIC #Microsoft 📡 Sysmon (SysinternalsEBPF) -> Syslog -> SIEM 🚀 ✅ Scripts ✅ ARM templates ✅ Sysmon configs and more.. techcommunity.microsoft.com/t5/azure-senti…
Today, Microsoft is open sourcing Cloud Katana, a cloud-native serverless application built on the top of Azure Functions to assess security controls in the cloud and hybrid cloud environments. Read about the design principles and learn how to deploy: msft.it/6011n46MT

🚨 We decided to re-brand Mordor to @SecDatasets 😈 We’ll cover new types of datasets to extend its application 💜 more coming soon.. 🍻 Help us build the largest library of datasets for the InfoSec community! 🚀 Site: securitydatasets.com/introduction.h… Repo: github.com/OTRF/Security-…
🚨 New version of the Windows Security Events connector from #AzureSentinel reached public preview Looking for a way to test & filter the collection of event logs via XPath queries? I got you! 💜🍻 @MSThreatProtect #MSTIC @OTR_Community @OSSEM_Project techcommunity.microsoft.com/t5/azure-senti…
🚨 In less than 24h 😉, we are sharing telemetry ( #Sysmon, Security & System) through the @Mordor_Project to help everyone 🌎 expedite the validation process of detection rules! @Cyb3rPandaH #CobaltStrike 🗒️Metadata: mordordatasets.com/notebooks/smal… 😈Dataset: raw.githubusercontent.com/OTRF/mordor/ma…


APTSimulator 0.9.0 featuring #CobaltStrike beacon activity simulation with - NamedPipe Creation - Service installation & exec pattern - HTTP beaconing github.com/NextronSystems… If you want to help, add some steps in here: github.com/NextronSystems…




What started w/ talks at ATT&CKcon & analysis of event logs, We're happy to see @Cyb3rPandaH & @Cyb3rWard0g initial research helping ATT&CK users improve their data collection strategies. Join us to collab 🍻 @OTR_Community 🎙️ bit.ly/OTRDiscord 🛡️ github.com/OTRF/OSSEM-DM/…
It has launched! ATT&CK v9 is now live with refactored data sources, ATT&CK for Containers, Google Workspace as a platform and more! Read about new data sources and the rest of the update at medium.com/mitre-attack/a… or attack.mitre.org/resources/upda… for new/changed groups/techniques/sw.
Sharing some data samples (PCAP & WinEvents) to validate detection of lateral movement via remote scheduled task creation & update 🍻 @OTR_Community 1⃣ Creation: mordordatasets.com/notebooks/smal… 2⃣ Update: mordordatasets.com/notebooks/smal… @HunterPlaybook Library Doc: github.com/OTRF/ThreatHun…
💥😱 @tiraniddo added "named pipe RPC client transport" to NtObjectManager 🔥 Thank you very much James for all your work 👏! I'll create PS scripts to cover a few scenarios 🍻 (Img 4) If anyone would like to help me, let me know 😉 @OTR_Community github.com/Cyb3rWard0g/Wi…




Looking forward to it! 🍻 Let's talk about some of the steps taken before sharing a dataset with the community 💜
THIS FRIDAY: Catch @Cyb3rWard0g in conversation with @mattifestation for the last #AtomicFriday of 2020! bit.ly/33AKlil

Thinking about contributing to an os project during the holidays? 😉The @OTR_Community have updated our Detection Model 1⃣Contribute security events to @MITREattack data sources github.com/OTRF/OSSEM-DM/… 2⃣Provide feedback github.com/OTRF/OSSEM-DM/… 3⃣Have fun ossemproject.com/notebooks/dm/a…




THIS FRIDAY: Catch @Cyb3rWard0g in conversation with @mattifestation for the last #AtomicFriday of 2020! bit.ly/33AKlil

#Eko2020 | @BlueSpaceSec | Roberto y Jose Luis Rodriguez: Open Threat Research (Keynote) "Open Threat Research: Compartiendo herramientas Open Source con el mundo para el desarrollo de detecciones desde casa", una charla de @Cyb3rWard0g y @Cyb3rPandaH. youtube.com/watch?v=6-UVaP…
youtube.com
YouTube
#Eko2020 Blue Space | Roberto y Jose Luis Rodriguez: Open Threat...
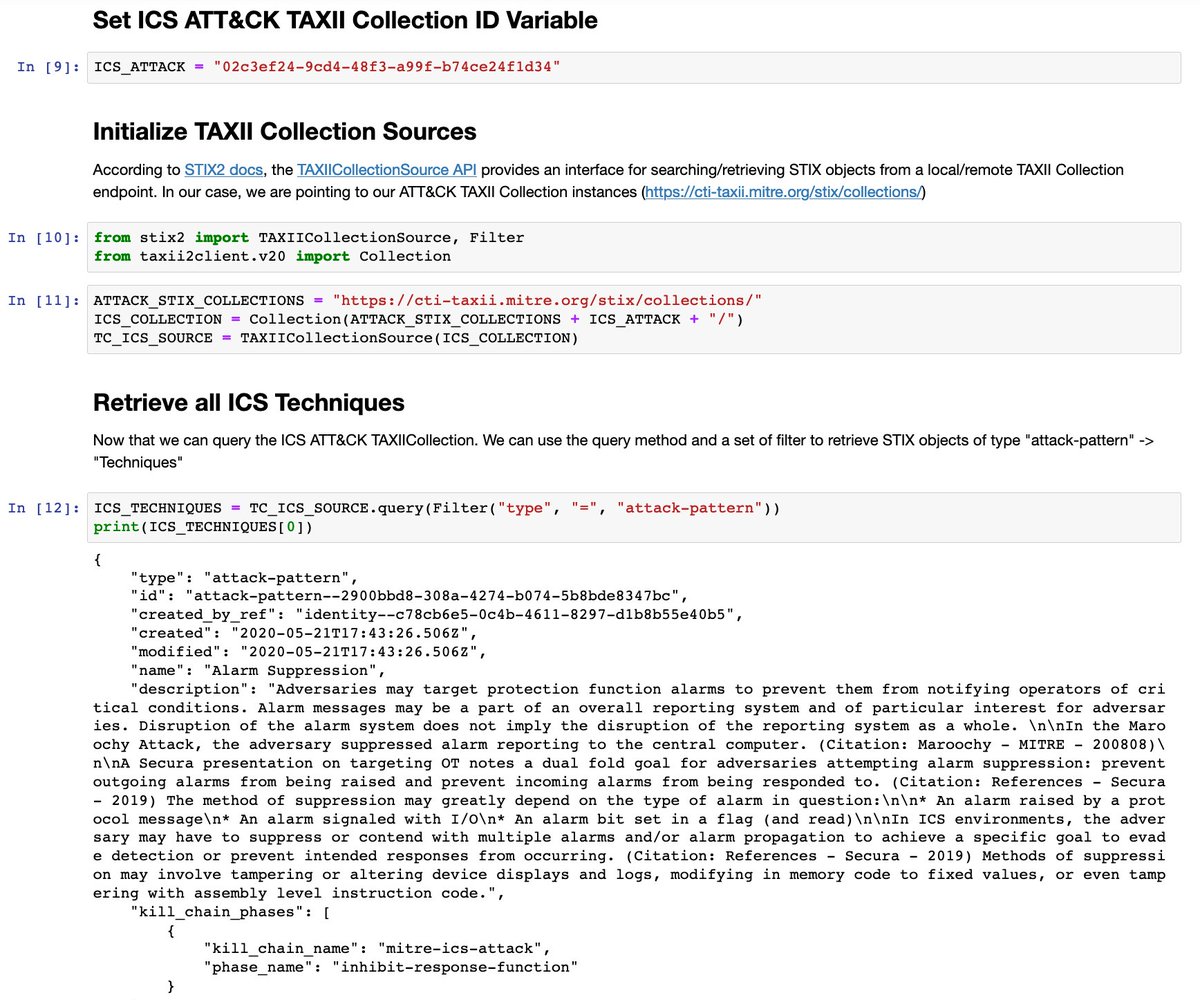
🚨 New version of our "attackcti" Python 🐍 library to query @MITREattack in STIX format via their public TAXII server has been released! 1⃣ ICS ATT&CK Integration ✅ 2⃣ Basic Notebook to explore ICS Content ✅ 📔 Binder: mybinder.org/v2/gh/OTRF/ATT… 📦Repo: github.com/OTRF/ATTACK-Py…



In their #THIRSummit talk, @Cyb3rPandaH & @jamieantisocial illustrates how we can avoid the typical cat and mouse games by modeling the data sources defined in ATT&CK to recognize, track, and even predict the malicious scent of adversaries. Watch it now: youtu.be/eKeydMrXsOE

Thank you @jaredhaight 😊🙏 With the latest updates to @MITREattack data sources by @Cyb3rPandaH , we are translating that doc to YAML files to create additional documentation and hopefully get contributions from the InfoSec Community 😊 github.com/OTRF/OSSEM-DM/…
THIS FRIDAY: Catch @Cyb3rWard0g in conversation with @mattifestation for the last #AtomicFriday of 2020! bit.ly/33AKlil

Formalizing the mapping of security events to the @MITREattack data source objects concepts 🍻 We would love to hear your feedback and see your contributions to this community-led effort!! 💜 Thank you @Cyb3rPandaH 💜 Blog: medium.com/threat-hunters…

🙏So happy to see our initial data modeling concepts applied to enhance @MITREattack . This is a more practical & less subjective approach to map event logs ➡️ att&ck data sources. We hope this helps the community to improve their data collection strategy. Thanks @Cyb3rPandaH 🍻
Coinciding with @jamieantisocial's and his #ThreatHuntingSummit talk, we've just released part 1 of a blog series by ATT&CK team member @Cyb3rPandaH on a proposed method of enhancing an often overlooked part of ATT&CK, data sources. Check it out at medium.com/mitre-attack/d….
Coinciding with @jamieantisocial's and his #ThreatHuntingSummit talk, we've just released part 1 of a blog series by ATT&CK team member @Cyb3rPandaH on a proposed method of enhancing an often overlooked part of ATT&CK, data sources. Check it out at medium.com/mitre-attack/d….
If you are a student or new to the InfoSec community and would like to attend the #ThreatHuntingSummit 2020 @sansforensics virtually😃, fill out this form by 3 pm (EST) today to win a guest pass (Only one available) Thank you @Cyb3rPandaH 🙏💜 bit.ly/THS20GuestPass
United States Tendências
- 1. Bears 47.6K posts
- 2. Josh Allen 17.2K posts
- 3. JJ McCarthy 8,553 posts
- 4. Packers 35.4K posts
- 5. Chargers 18.4K posts
- 6. Vikings 25.1K posts
- 7. Bengals 19.4K posts
- 8. Bucs 11.3K posts
- 9. Bryce Young 4,850 posts
- 10. Bills 106K posts
- 11. Sean Tucker 3,477 posts
- 12. Ramsey 7,029 posts
- 13. Steelers 32K posts
- 14. Falcons 19.2K posts
- 15. Hyatt 3,324 posts
- 16. Jameis 11.7K posts
- 17. #GoPackGo 5,237 posts
- 18. #HereWeGo 4,867 posts
- 19. Mason Rudolph 2,129 posts
- 20. Caleb 31.3K posts
Talvez você curta
-
 Olaf Hartong
Olaf Hartong
@olafhartong -
 Jose Rodriguez 🇵🇪
Jose Rodriguez 🇵🇪
@Cyb3rPandaH -
 Roberto Rodriguez 🇵🇪
Roberto Rodriguez 🇵🇪
@Cyb3rWard0g -
 sigma
sigma
@sigma_hq -
 Red Canary, a Zscaler company
Red Canary, a Zscaler company
@redcanary -
 SOC Prime
SOC Prime
@SOC_Prime -
 Christopher Glyer
Christopher Glyer
@cglyer -
 Jonny Johnson
Jonny Johnson
@JonnyJohnson_ -
 Applied Network Defense
Applied Network Defense
@NetworkDefense -
 Mehmet Ergene
Mehmet Ergene
@Cyb3rMonk -
 Samir
Samir
@SBousseaden -
 Recon InfoSec
Recon InfoSec
@Recon_InfoSec -
 Ryan K
Ryan K
@meansec -
 Nick Carr
Nick Carr
@ItsReallyNick -
 Nextron Systems
Nextron Systems
@nextronsystems
Something went wrong.
Something went wrong.


















































































