You might like
How I Fumbled $430,000 By Selling Too Soon I thought I was a genius when I turned $1K into $15K selling BNB at $30. Then it soared to $860… I missed out on $430K. The regret is real, but the lesson is bigger. Want to avoid my mistake? Read on 🧵
Based on the research of Akamai, I made a new module on netexec to find every principal that can perform a BadSuccessor attack and the OUs where it holds the required permissions 🔥 github.com/Pennyw0rth/Net…

🚀 We just released my research on BadSuccessor - a new unpatched Active Directory privilege escalation vulnerability It allows compromising any user in AD, it works with the default config, and.. Microsoft currently won't fix it 🤷♂️ Read Here - akamai.com/blog/security-…

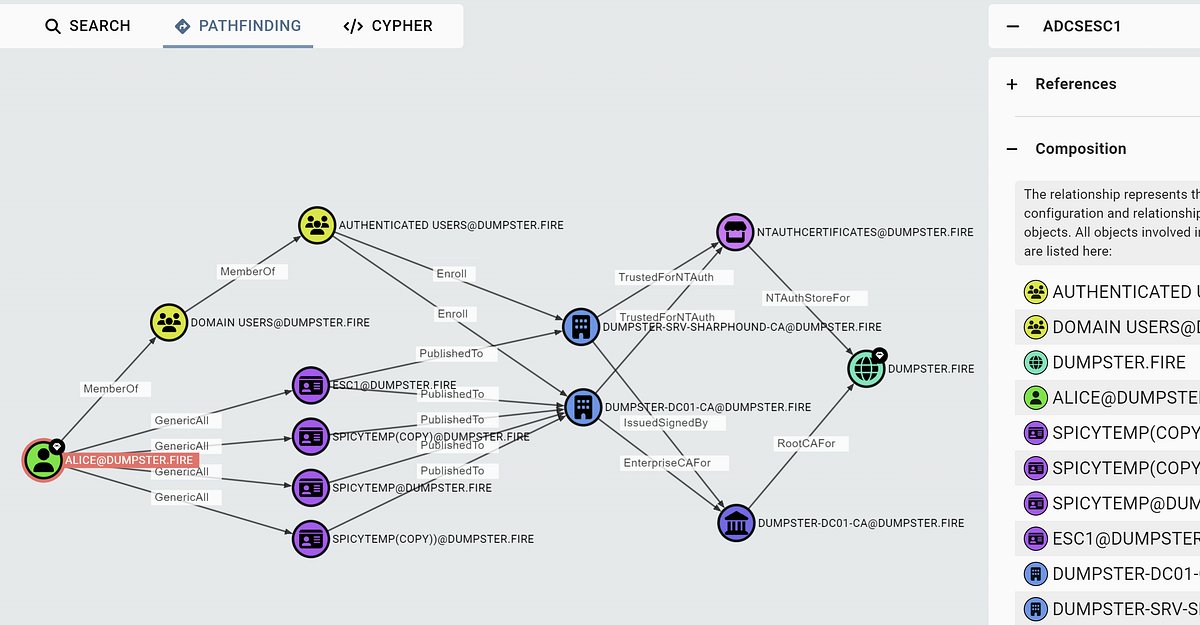
ADCS attack paths in BloodHound! 🥳 This blog post breaks down the implementation of the ESC1 requirements and guides you on effectively leveraging BloodHound to identify attack paths that include ESC1 privileges. posts.specterops.io/adcs-attack-pa…
"Pentesting with Secure LDAP and LDAP Channel Binding" #infosec #pentest #redteam rootsecdev.medium.com/pentesting-wit…
The first version of an SMTP smuggling scanner is now available at github.com/The-Login/SMTP…. More tools to come! Feedback is much appreciated!
Merry Christmas, here is my gift to you 🎁 I'm releasing "Internal All The Things", which contains all my cheatsheets and methodologies for Active Directory, Internal Pentests and Cloud Assessments 🎅 swisskyrepo.github.io/InternalAllThe…
Do you store your "DNS dynamic update registration credentials" in a DHCP? Cute, it means I have a new tool for you 😁😈 Enjoy the DHCP Server DNS Password Stealer. The C source code, and the compiled exe, as usual: github.com/gtworek/PSBits…

Got initial access to the azure cloud via token theft? Wondering what to do? Step 1: Roadrecon github.com/dirkjanm/ROADt… Commands: roadrecon auth —access-token roadrecon gather Bonus: extract conditional access policies roadrecon plugin policies -f caps.html Run GUI:…
"Infecting SSH Public Keys with backdoors" #infosec #pentest #redteam blog.thc.org/infecting-ssh-…

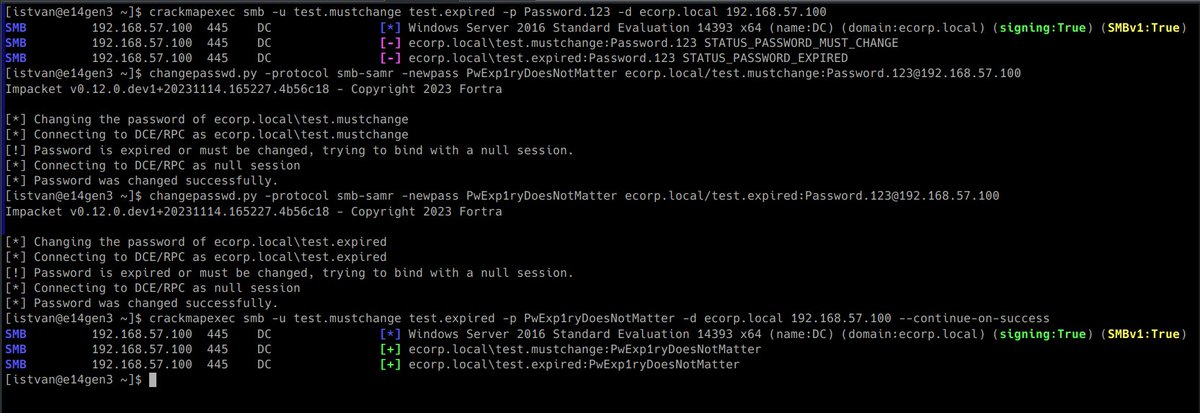
I was a little bit uncertain about expired AD passwords, but fortunately @n00py1 has a great blogpost about it: n00py.io/2021/09/resett… TL;DR: whether the password is MUST_CHANGE or EXPIRED, usually doesn't matter, you need to be able to change it remotely in different ways.
It's been quiet for a while around bloodhound Python, however I'm happy to share that I am now maintaining the project at my personal GitHub. The latest version fixes many bugs/issues, also thanks to the many PRs that were submitted (thanks all!). github.com/dirkjanm/blood…
"Most common Active Directory misconfigurations and default settings that put your organization at risk" #infosec #pentest #redteam blog.nviso.eu/2023/10/26/mos…

Check your MFA configurations github.com/dafthack/MFASw…
Dear Tenants that only have a P1 license, Just a reminder ...
New tool by @Prepouce_ and @hackoura for local privilege escalation on a Windows machine, from a service account to NT SYSTEM. Should work on any recent versions of Windows. Watch out the explanatory blog: blog.hackvens.fr/articles/Coerc… And the tool : github.com/hackvens/Coerc…
You can do drop the mic and rbdc as per @n00py1 blog n00py.io/2022/10/practi…
My team just released a Kubernetes attack path tool named KubeHound! Release blog post (with examples) securitylabs.datadoghq.com/articles/kubeh… Website / docs: kubehound.io :D Should be able to handle large k8s env! Feedback welcome!
A cheat sheet that contains common enumeration and attack methods for Windows Active Directory. github.com/S1ckB0y1337/Ac…
New blog: Understanding Red to Be Better at Blue: Navigating New CrackMapExec Updates ✅Keeping up with the red team ✅Breaking down CME’s new key features ✅From code to behavioural hunting & detections ✅Illustrations with examples buff.ly/47Xm6KF
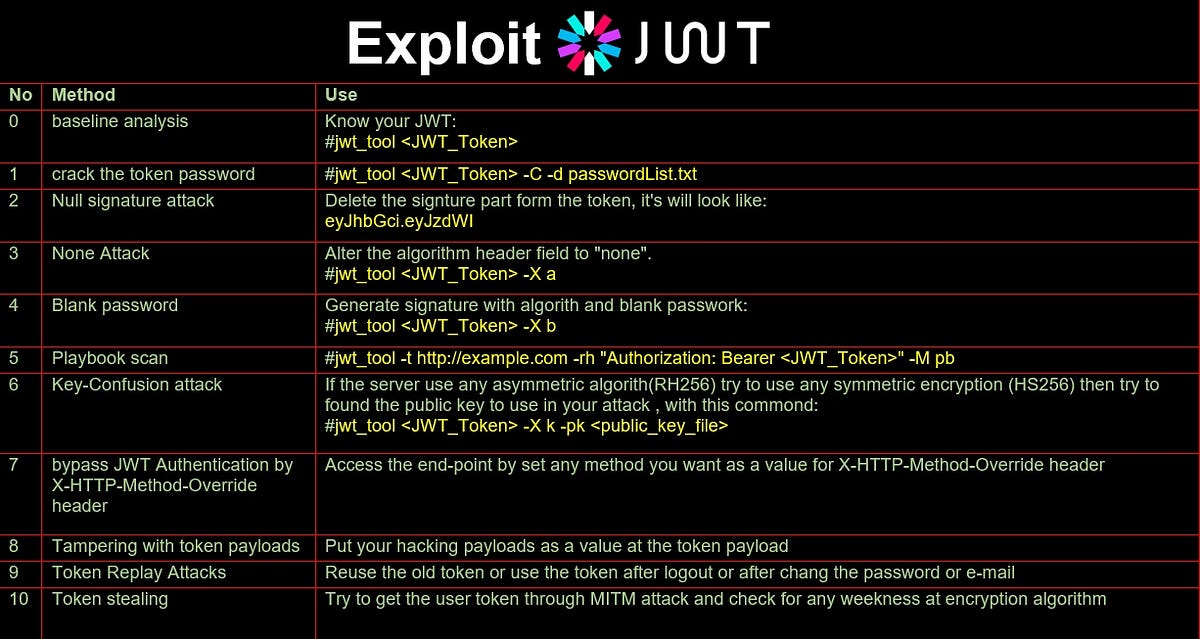
10 ways to exploit JWT (JSON Web Token): by @3mSecurity medium.com/@musab_alharan…
United States Trends
- 1. #DWTS 74.4K posts
- 2. Robert 115K posts
- 3. Elaine 42.2K posts
- 4. Alix 13.4K posts
- 5. Jordan 115K posts
- 6. Dylan 34.4K posts
- 7. NORMANI 4,037 posts
- 8. Carrie Ann 3,975 posts
- 9. Anthony Black 2,933 posts
- 10. #DancingWithTheStars 1,930 posts
- 11. Drummond 2,874 posts
- 12. #WWENXT 8,242 posts
- 13. Sixers 4,550 posts
- 14. Suggs 2,675 posts
- 15. Collar 30.2K posts
- 16. Godzilla 33.3K posts
- 17. Michigan 85.1K posts
- 18. Jalen Johnson 3,783 posts
- 19. Auburn 9,496 posts
- 20. #iubb 1,323 posts
Something went wrong.
Something went wrong.