You might like
United States Trends
- 1. Tulane 25.2K posts
- 2. Oregon 24.2K posts
- 3. Eagles 75.1K posts
- 4. Ben Johnson 2,846 posts
- 5. Josh Johnson 3,636 posts
- 6. #Bears 3,946 posts
- 7. #GoPackGo 3,862 posts
- 8. Jake Elliot 3,678 posts
- 9. Andrew Tate 38K posts
- 10. NFC East 14.2K posts
- 11. Saquon 8,502 posts
- 12. Malik Willis N/A
- 13. Austin Booker N/A
- 14. #GBvsCHI N/A
- 15. Dante Moore 1,261 posts
- 16. Group of 5 7,736 posts
- 17. #Packers 1,983 posts
- 18. Steen 4,321 posts
- 19. Notre Dame 36.6K posts
- 20. Jordan Davis 1,357 posts
You might like
-
 Alexandre Borges
Alexandre Borges
@ale_sp_brazil -
 Arkbird
Arkbird
@Arkbird_SOLG -
 Joe Security
Joe Security
@joe4security -
 Dee
Dee
@ViriBack -
 Pavel Yosifovich
Pavel Yosifovich
@zodiacon -
 0verfl0w
0verfl0w
@0verfl0w_ -
 Frost
Frost
@fr0s7_ -
 Felipe Duarte
Felipe Duarte
@dark0pcodes -
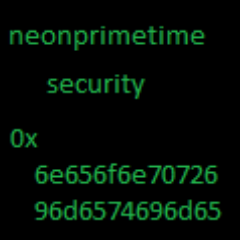 neonprimetime
neonprimetime
@neonprimetime -
 sysopfb
sysopfb
@sysopfb -
 Ring3API 🇺🇦
Ring3API 🇺🇦
@ntlmrelay -
 avman
avman
@avman1995 -
 Joe Roosen
Joe Roosen
@JRoosen -
 JAMESWT
JAMESWT
@JAMESWT_WT -
 Frank Boldewin
Frank Boldewin
@r3c0nst
Loading...
Something went wrong.
Something went wrong.