Scott Sutherland
@_nullbind
Security Researcher @NetSPI | PowerUpSQL Author
Talvez você curta
📢 New Chapter: #MicrosoftEntra Attack & Defense Playbook ☁️ 🔑 @samilamppu and I have focused on Application-based Authentication (ABA) in #EntraConnect. Huge thanks to @DrAzureAD and @RobbeVdDaele for reviewing. Check out the new chapter: github.com/Cloud-Architek…




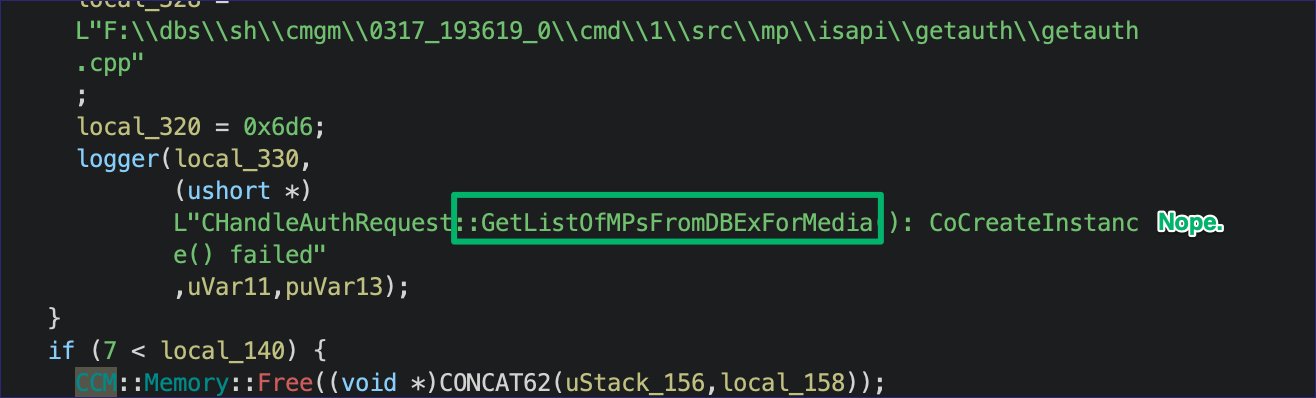
Added CRED-8 to Misconfiguration Manager, which is @unsigned_sh0rt's MP relay to dump machine policy secrets. MM link: github.com/subat0mik/Misc… Blog link: specterops.io/blog/2025/07/1…
Lots of cool new Nemesis features merging in soon from @tifkin_ and I! Development definitely didn't stop with the 2.0 release :) github.com/SpecterOps/Nem…
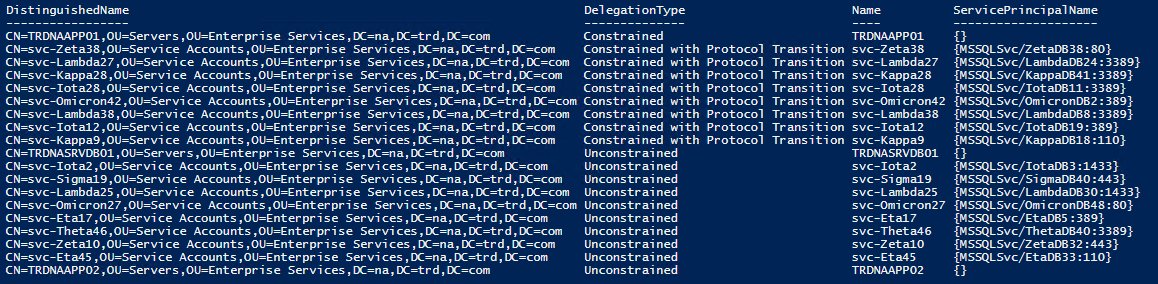
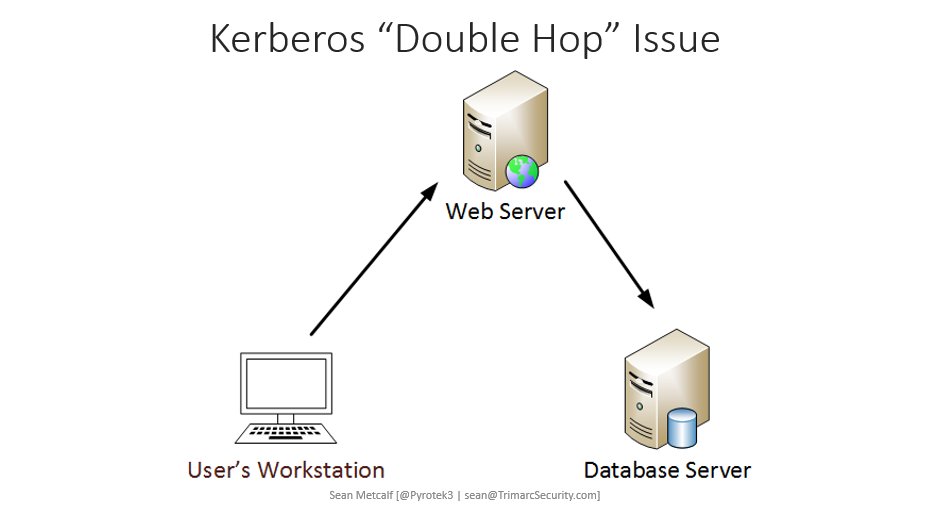
Last week we covered Active Directory Group Policy permissions (x.com/PyroTek3/statu…). This week, we dig into Active Directory Kerberos delegation. I have mentioned in several presentations that Kerberos delegation is impersonation. Kerberos delegation is used when a service…

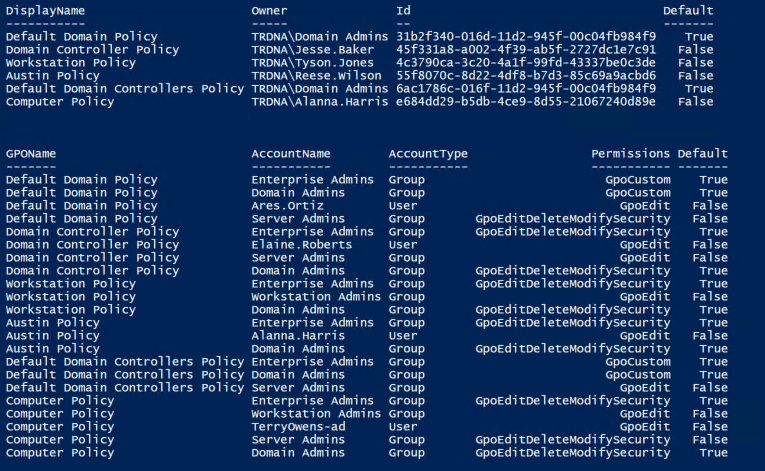
Recently, we looked at Active Directory built-in groups (x.com/PyroTek3/statu…) This week, we focus on Active Directory Group Policy Objects (GPOs). GPOs should be audited regularly to identify the configured owner as well as the permissions to ensure they are appropriate. In…
During my #BHUSA talk I've released many ETW research tools, of which the most notable is BamboozlEDR. This tool allows you to inject events into ETW, allowing you to generate fake alerts and blind EDRs. github.com/olafhartong/Ba… Slides available here: github.com/olafhartong/Pr…
👋 Say hello to Nemesis 2.0, a streamlined, Docker Compose-based platform that is laser-focused on file triage. After introducing v1 two years ago, the team has reworked the platform to better serve what people need from it. Read more from @harmj0y. ⤵️ ghst.ly/4mxQzFU
In our latest blog, @shncldwll breaks down the process of creating a fully integrated, self-verifying agentic system that can do modern Windows Active Directory red team operations, without human interaction. Read about our approach to building cyber evals to measure model…

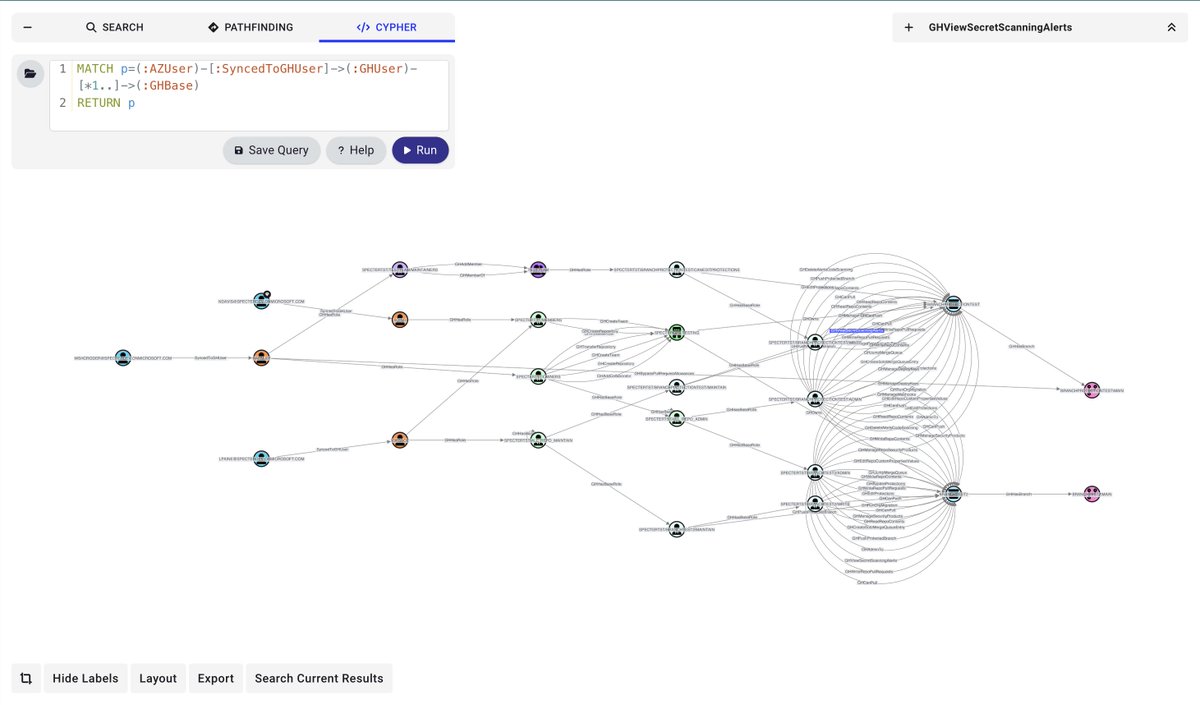
Your devs aren’t just writing code, they’re holding keys to your kingdom. BloodHound now supports GitHub identities, so you can visualize access and control in your org’s dev pipeline. Check it out at github.com/SpecterOps/Git…
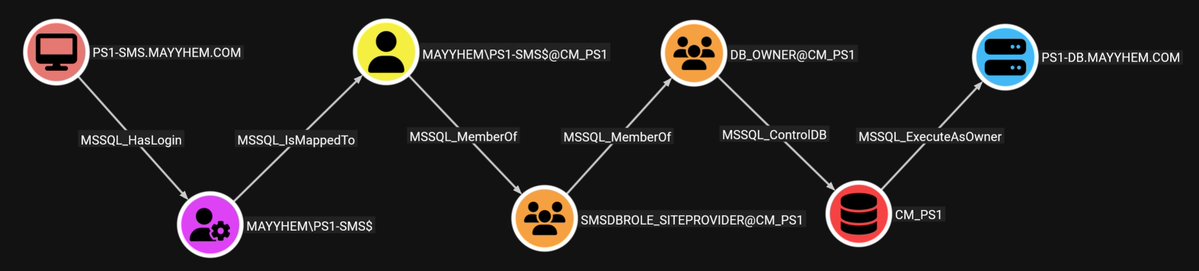
I'm SO hyped to finally make MSSQLHound public! It's a new BloodHound collector that adds 37 new edges and 7 new nodes for MSSQL attack paths using the new OpenGraph feature for 8.0!. Let me know what you find with it! - github.com/SpecterOps/MSS… - specterops.io/blog/2025/07/2…
Get to know what's new w/ SCCMHunter. Join @unsigned_sh0rt's #BHUSA Arsenal session on the post-exploitation tool & learn about the updates, including site system profiling, extended admin modules, & credential relaying capabilities. ghst.ly/3GkhpBV

NetSPI Principal Security Consultant Jason Juntunen recently published findings on a Remote Code Execution vulnerability in SailPoint's IQService component. 👉 Read the full technical breakdown: ow.ly/GbT150WmgRg #proactivesecurity #VulnerabilityResearch

Happy Friday! @tifkin_ and I are happy to announce that we have cut the release for Nemesis 2.0.0 - check out the CHANGELOG for a (brief) summary of changes, and dive into our new docs for more detail! We're extremely proud and excited for this release github.com/SpecterOps/Nem…
Including nice tool release 🔥 github.com/temp43487580/E…
Compromising Entra joined devices with P2P certificate authentication by @TEMP43487580 👀👌

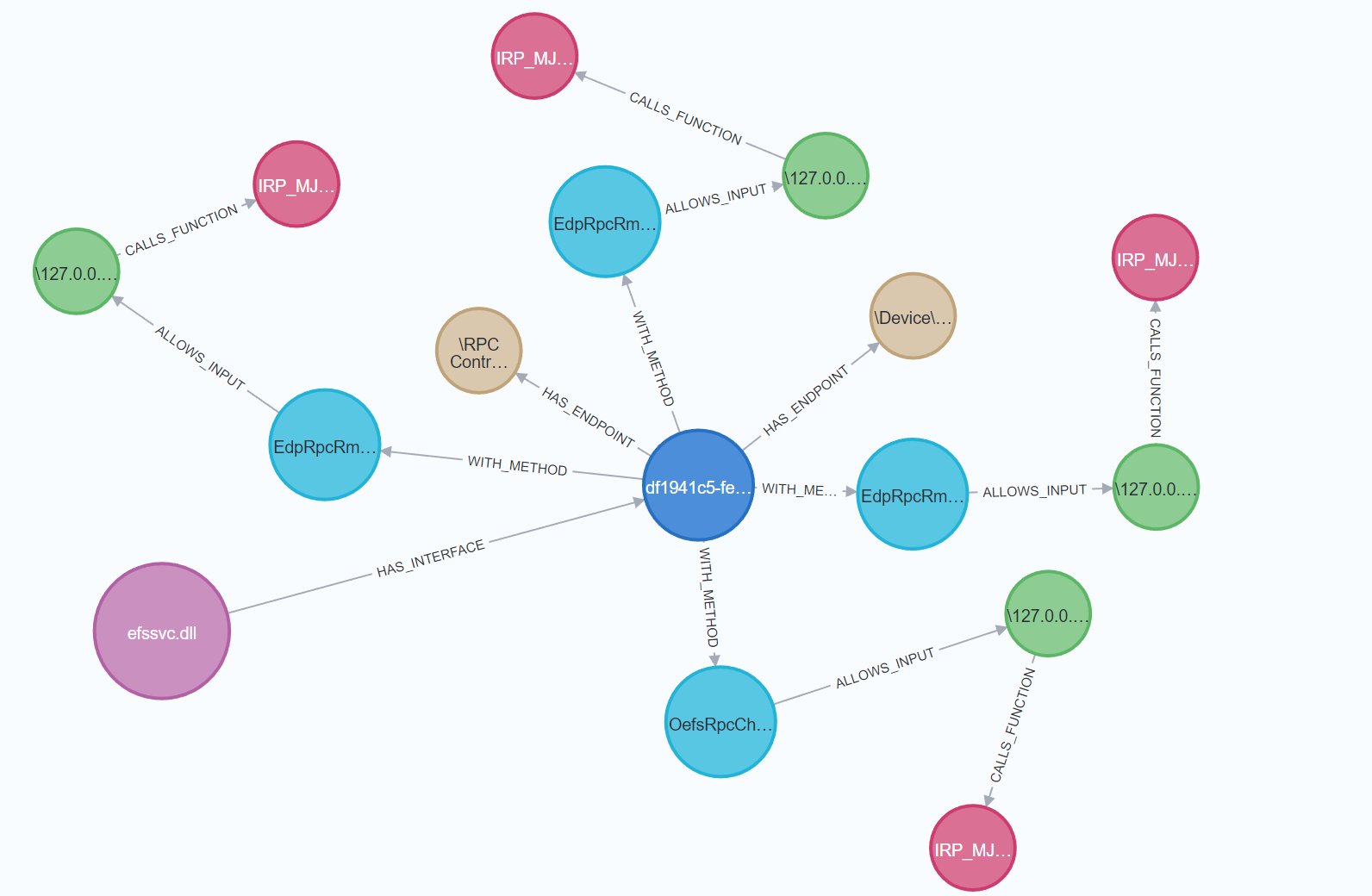
Super interesting blog on how to automate some MS-RPC research 🧐 incendium.rocks/posts/Automati…
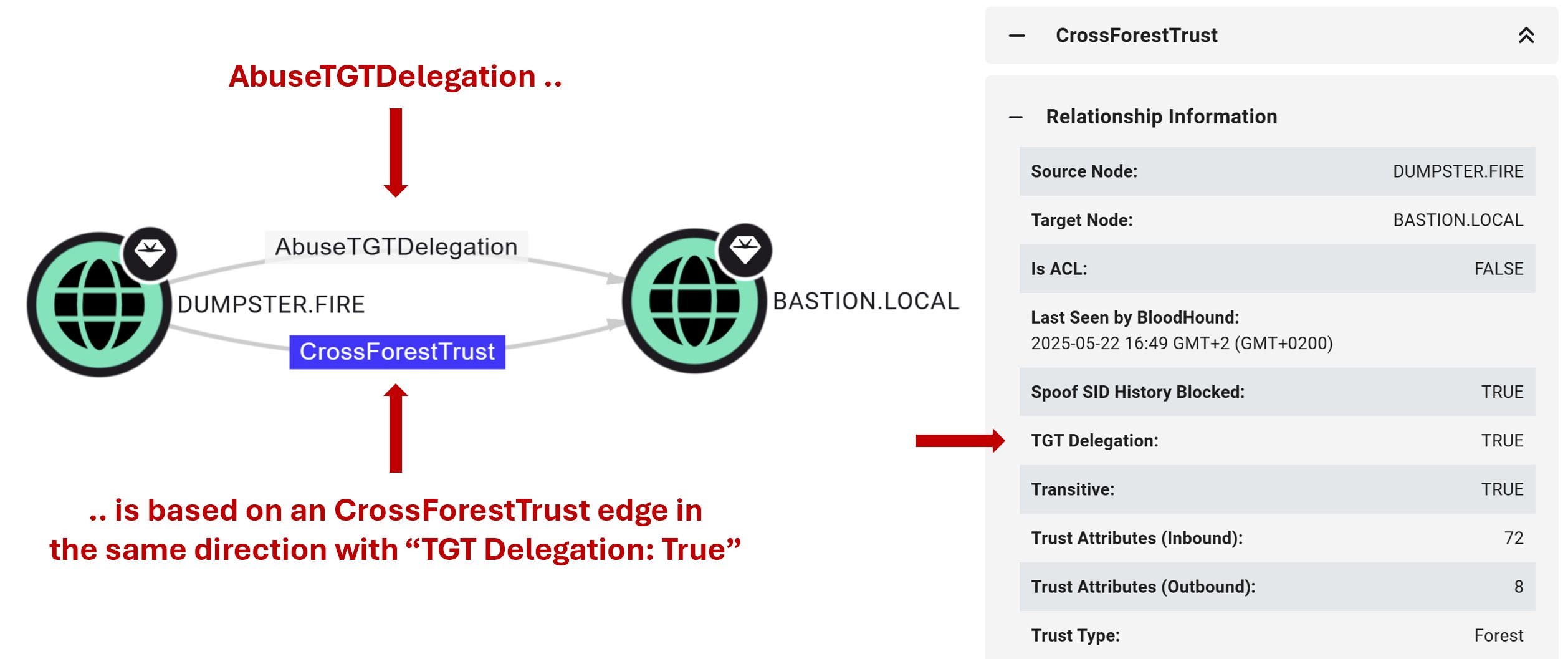
I publish two blog posts today! 📝🐫 The first dives into how we're improving the way BloodHound models attack paths through AD trusts: specterops.io/blog/2025/06/2… The second covers an attack technique I came across while exploring AD trust abuse: specterops.io/blog/2025/06/2…
Tokenizing has dropped in Rigging. Train models in-line with LLM interactions, tools calls, and metrics. 👀 github.com/dreadnode/rigg…
Thank you so much to @x33fcon and its organizers for an awesome experience! @tifkin_ and I had a blast talking about the new Nemesis 2.0 rewrite (code live at github.com/SpecterOps/Nem… !) and hope to be back next year #x33fcon
One Tool To Rule Them All AMSI, CLM and ETW – defeated* with one Microsoft signed tool by someone called Ian shells.systems/one-tool-to-ru…

I'm doing a talk at BSidesLV on this, but I'm dropping the research early, discovered this in 2022, and releasing now for awareness, how to decrypt F5 Service Account Passwords Standalone tool github.com/evilmog/F5-Dec…
Deception isn’t fluff… it’s friction. And friction slows attackers down, gives defenders an edge, and buys you time. The whole point is to make them second guess their actions, make them have to perform more actions and hopefully increase the chances of detection
United States Tendências
- 1. Go Birds 3,216 posts
- 2. #AskFFT N/A
- 3. #ElClasico 50.4K posts
- 4. Good Sunday 69.4K posts
- 5. Go Bills 4,188 posts
- 6. #sundayvibes 6,237 posts
- 7. Scott Bessent 13.8K posts
- 8. Vini 20.2K posts
- 9. Full PPR N/A
- 10. #ARSCRY 4,594 posts
- 11. Hala Madrid 15.4K posts
- 12. #Talus_Labs N/A
- 13. Mooney 2,098 posts
- 14. NFL Sunday 7,703 posts
- 15. Lamine 90.2K posts
- 16. Sunday Funday 4,340 posts
- 17. Matty Cash 1,897 posts
- 18. Ireland 116K posts
- 19. The Grand Canyon N/A
- 20. Barcelona 167K posts
Talvez você curta
-
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 Beau Bullock
Beau Bullock
@dafthack -
 Matt Hand
Matt Hand
@matterpreter -
 Ryan Cobb
Ryan Cobb
@cobbr_io -
 Marcello
Marcello
@byt3bl33d3r -
 Karl
Karl
@kfosaaen -
 Cn33liz
Cn33liz
@Cneelis -
 Mr.Un1k0d3r
Mr.Un1k0d3r
@MrUn1k0d3r -
 Chris Thompson
Chris Thompson
@retBandit -
 monoxgas
monoxgas
@monoxgas -
 NetSPI
NetSPI
@NetSPI -
 Harley Lebeau
Harley Lebeau
@r3dQu1nn -
 Cody Thomas
Cody Thomas
@its_a_feature_ -
 bohops
bohops
@bohops -
 Dwight Hohnstein
Dwight Hohnstein
@djhohnstein
Something went wrong.
Something went wrong.