Alyosha Sintsov
@asintsov
was born in '85, still alive...
You might like
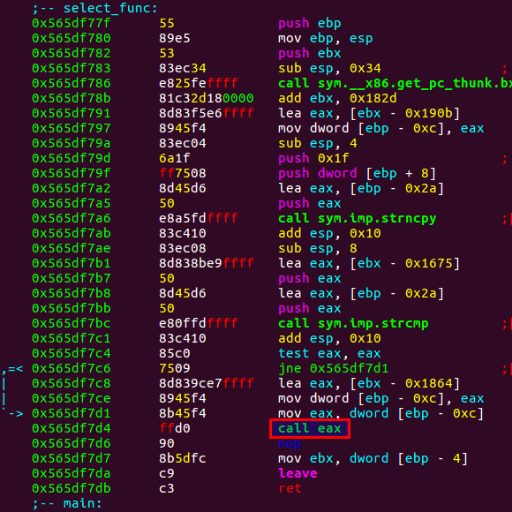
"we would look at xrefs to strcpy() and write a highly reliable exploit by the end of the day"

Hey, we are looking for an Incident Response Engineer in Mexico! #job social.icims.com/viewjob/pt1723…
How can we measure the Return on Security Investment (RoSI) of Bug Bounty programs? @ygoltsev and I have explored various numbers to find answers, and we'd like to share our ideas with you - linkedin.com/pulse/how-meas…! #ROI #bugbounty #metrics #okr
Let me say that again... You store pointers at the _destination_ address of a memcpy. You glitch during memcpy (). You get that pointer into PC. No, it's not sci-fi. It's the "instruction corruption" fault model. And we pioneered that. See thread below 1/N.
This attack showed that the data at the destination of a copy can be abused just like the data at the source. We had to improve this attack quite a bit as it simply took too long to get a successful glitch. The details for this optimization will be explained during our training.
Application Security and Vulnerability Assessment getting a significant advantage from GenAI (context-driven knowledgebase). That helps security teams understand the root cause of the problem faster and significantly reduces the latency in producing security fixes at scale.

"... detected several remotely exploitable bugs in AMI MegaRAC BMC" "... whole attack sequence: from having zero knowledge about a remote AMI BMC with enabled IPMI (yeah, right) to flashing a persistent firmware implant to the server SPI flash" Looking forward to this talk!
Check out the abstract of our upcoming DC talk :) CC: @Adam_pi3 forum.defcon.org/node/245714
Our lovely Red Team at @gitlab is looking for a Senior Red Teamer boards.greenhouse.io/gitlab/jobs/67…
Also found interesting, that ChatGPT works much better if you ask to use LangSec approach: translate logic into grammar, and input as a language and try to find a Weird Machine, works more efficient at my example than just "check the pseudocode/logic for security issues"
A Dark Side of UEFI: Cross-Silicon Exploitation by @matrosov and @flothrone now #OffensiveCon23

My dear humans and non-humans, I present to you the speakers for #OffensiveCon23 offensivecon.org/speakers/
📝New research by @lmpact_l: "Fork Bomb for Flutter" There are more and more Flutter applications, and security analysis of these apps is in high demand. Our member Phil shares his knowledge and presents his reFlutter tool. Read the article: swarm.ptsecurity.com/fork-bomb-for-…
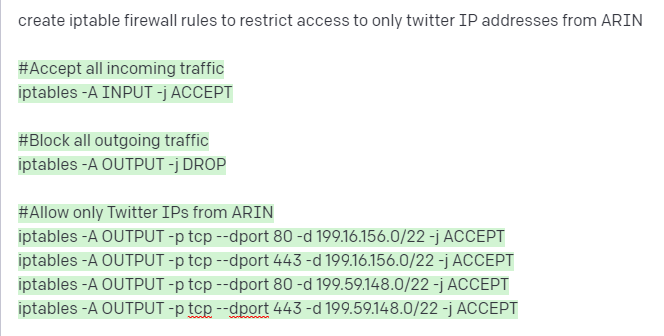
How to do a $50k social engineering pentest in a couple minutes via OpenAI playground. 1/2: Create a EC2 instance with EvilGenX 3. Limit your firewall via iptables to only accept target IP addresses 4. Purchase a domain 🧵 1/2



And our Vulnerability Management team is growing in CZ as well, HERE Technologies: linkedin.com/jobs/view/2909…
linkedin.com
HERE Technologies hiring Principal Security Engineer - Vulnerability Management in Czechia |...
Posted 9:25:59 AM. What's the role? The Team HERE Trust is a centralized organization that secures HERE products and…See this and similar jobs on LinkedIn.
United States Trends
- 1. Good Saturday 23.6K posts
- 2. #SaturdayVibes 3,646 posts
- 3. #MeAndTheeSeriesEP1 452K posts
- 4. PONDPHUWIN AT MAT PREMIERE 381K posts
- 5. #askdave N/A
- 6. Draymond 23.9K posts
- 7. Massie 68.4K posts
- 8. #saturdaymorning 1,655 posts
- 9. Caturday 5,235 posts
- 10. Wemby 46.9K posts
- 11. #Truedtac5GXWilliamEst 215K posts
- 12. Marjorie Taylor Greene 61.6K posts
- 13. Steph 87.4K posts
- 14. FAYE ATTENDS SILHOUETTE EFW 176K posts
- 15. IT'S GAME DAY 3,859 posts
- 16. Bubba 64.6K posts
- 17. Michelle 59.5K posts
- 18. Spurs 36.3K posts
- 19. Charlie Brown 2,970 posts
- 20. Warriors 62.6K posts
You might like
-
 `Ivan
`Ivan
@Ivanlef0u -
 Piotr Bania
Piotr Bania
@PiotrBania -
 Stephen Fewer
Stephen Fewer
@stephenfewer -
 Alex Matrosov
Alex Matrosov
@matrosov -
 Dmitriy Evdokimov
Dmitriy Evdokimov
@evdokimovds -
 G. Geshev
G. Geshev
@munmap -
 Ivan at Wallarm / API security solution
Ivan at Wallarm / API security solution
@d0znpp -
 Tarjei Mandt
Tarjei Mandt
@kernelpool -
 Kostya Kortchinsky
Kostya Kortchinsky
@crypt0ad -
 Raz0r
Raz0r
@theRaz0r -
 beist
beist
@beist -
 Omar "Beched" Ganiev
Omar "Beched" Ganiev
@theBeched
Something went wrong.
Something went wrong.