ICYMI - DPRK's training video on making Civil Engineering profiles to perform fraudulent CIV-E work. #DRPK #kimhasabigfacemole @aptwhatnow youtu.be/m4XmJUBorKU
Patiently waiting for the new X account location feature to propagate so I can revisit all the DPRK 🇰🇵 X accounts.
Gen Threat Labs uncover evidence of rare cross-country coordination between Russia’s Gamaredon and North Korea’s Lazarus | gendigital.com/blog/insights/… @GenThreatLabs
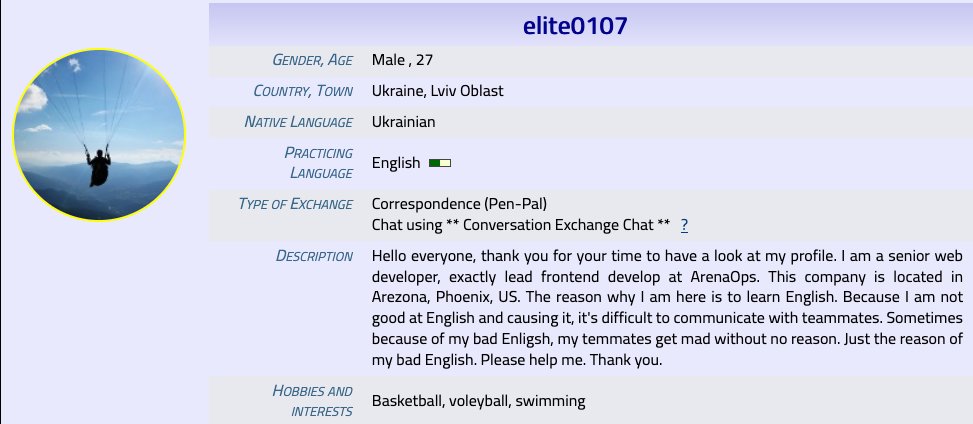
Blast from the past Our boy @AMangus7 - AKA "Tyler Minegar, Brock Patterson, Tretiak Sashka" LMAO Bro, where did you find this X PFP? Boy be manifesting. Surprised Daddy lets you on X I hope you find someone to help you with your english so your ITW frenz stop pickin' on you

‼️🇰🇵 Another North Korean hacker using AI to alter his face caught while trying to infiltrate Bitso. Meet "Sebastian," a software engineer from Colombia who can't speak Spanish. Strange, right?
🇰🇵 Meet "Mateo" and "Alfredo", two young #Lazarus agents who thought it was a good idea to steal someone else's ID and resume to try to get a job with us. 🪶 We recorded them and found interesting data on how they operate. ⬇️ Read our article on the #QuetzalTeam Blog below!


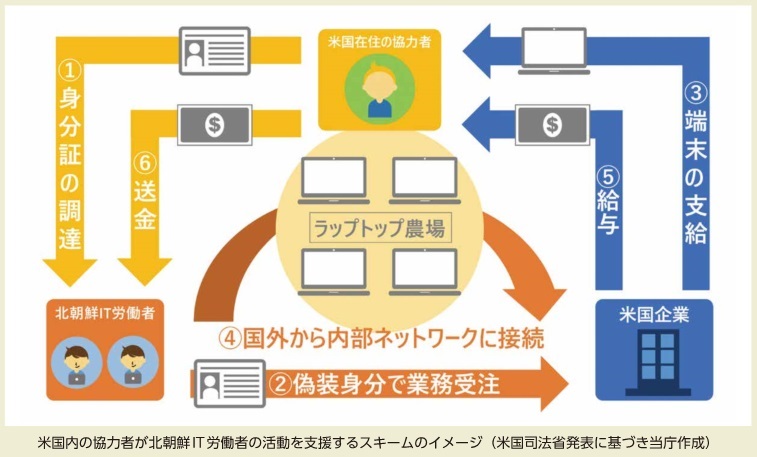
Multilateral Sanctions Monitoring Team’s DPRK IT Worker report. msmt.info/view/save/2025… #DPRK

Thanks for the call out Matt Burgess! It's true, DPRK boyz are acting as architects, structural engineers, and stamping/approving designs in the United States for a quick dollar. They steal legitimate licenses and make up stamps. Time to do something. wired.com/story/north-ko…
Just added a fresh write-up on DPRK-linked GitHub orgs - examples, tactics, and indicators. From fake “startups” to fork farms: how DPRK teams spin up orgs, boost each other, and hunt for facilitators. As at the time of writing, most are still active on Twitter. Link below.
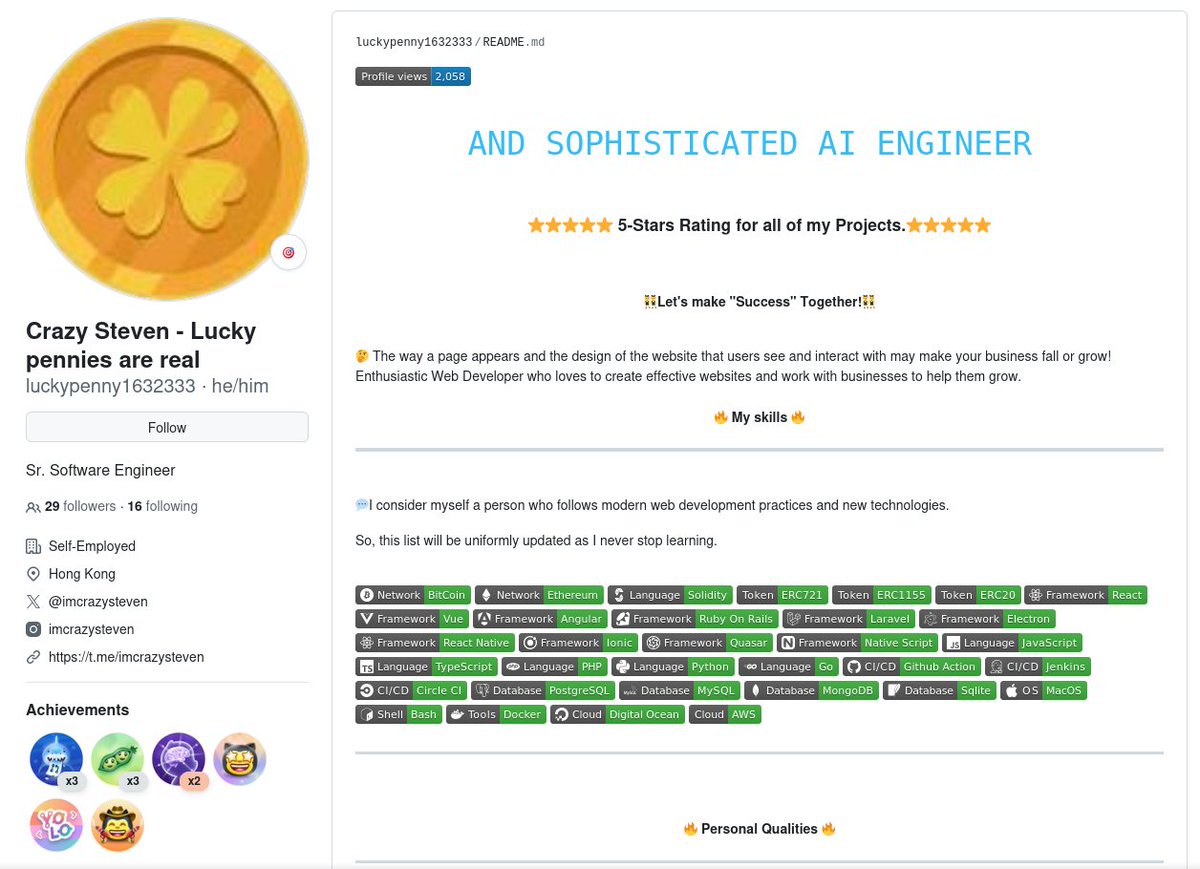
After nuking all of his accounts since @browsercookies and I last looked at him, "Steven Leal" has been hard at work as "Crazy Steven". 🇰🇵 He was kind enough to keep the luckypenny1632333 while he pivoted from shitty crypto grifter to shitty AI grifter.
Using automation with AI voice agents(2): Make.com and N8N orchestrate when your voice agents contact customers. Use cases include inbound Call Handling: Log call metadata received via webhook (e.g., from Retell) into a database or CRM for analysis or follow-up.
Kimsuky used AI deepfake-generated ID cards via ChatGPT to impersonate a South Korean defense institution in an APT spear-phishing attack. genians.co.kr/en/blog/threat… #Kimsuky #ChatGPT #Deepfake

A little fuckin’ dramatic. Luckily there is a pressure release for those who need validation. They become InfoSec influencers, making it their entire identity. Fireside chats, podcasts, new job every 2 years, LinkedIn premium analytics - hard copes. FOR THE LOVE OF THE GAME!
NGL they did him a solid.
Great stuff coming out of Chollima Group. Started months ago but nice to finally see it out there. Come for the juice, stay for the creepy altered images chollima-group.io/posts/dubai-cr…

god bless.
Someone just dropped almost 1.4k email address list used by North Korean IT workers. gofile.io/d/mh6DUE
"Nothing to luck, Everything to effort. Believe yourself and get success."

hi here is ican0220 or RokyangDeveloper0220!. Might also go by Xun Zhu [email protected] [email protected] github.com/ican0220 many nice resources on his Github!

1/ An unnamed source recently compromised a DPRK IT worker device which provided insights into how a small team of five ITWs operated 30+ fake identities with government IDs and purchased Upwork/LinkedIn accounts to obtain developer jobs at projects.


United States 趨勢
- 1. Black Friday 366K posts
- 2. #SkylineSweeps N/A
- 3. Egg Bowl 3,624 posts
- 4. #FanCashDropPromotion 1,401 posts
- 5. NextNRG Inc 1,570 posts
- 6. #Rashmer 23.5K posts
- 7. #LightningStrikes N/A
- 8. #NutramentHolidayPromotion N/A
- 9. WHO DEY 12.4K posts
- 10. Good Friday 62.7K posts
- 11. Andriy Yermak 16K posts
- 12. TODAY ONLY 64K posts
- 13. Mr. President 22.3K posts
- 14. Cyber Monday 6,266 posts
- 15. Clark Lea 1,327 posts
- 16. Third World Countries 61.7K posts
- 17. CONGRATULATIONS JIN 64.6K posts
- 18. $SMX 8,471 posts
- 19. Black Cats 2,997 posts
- 20. Wegmans 2,890 posts
Something went wrong.
Something went wrong.