MrSandman
@cmhacks
29a Labs http://hackstory.net/29A // Security Researcher @ ZDI
你可能會喜歡
Se ha filtrado todo el código fuente de la web de la Apple App Store. Se olvidaron de desactivar los Source Maps y es totalmente legible, con comentarios incluidos: github.com/rxliuli/apps.a…

The security guarantees of modern TEE offerings by Intel and AMD can be broken cheaply and easily, by building a memory interposition device that allows attackers to physically inspect all memory traffic inside a DDR5 server. Source: tee.fail
🚨Cyber Alert ‼️ 🇪🇸Spain - Spain citizens: 34 million records for sale The threat actor "Cayenne22" claims to be selling 34 million records of Spanish citizens' data, including full name, DNI, email, phone number and IBAN. Threat class: Cybercrime Observed: Oct 31, 2025…

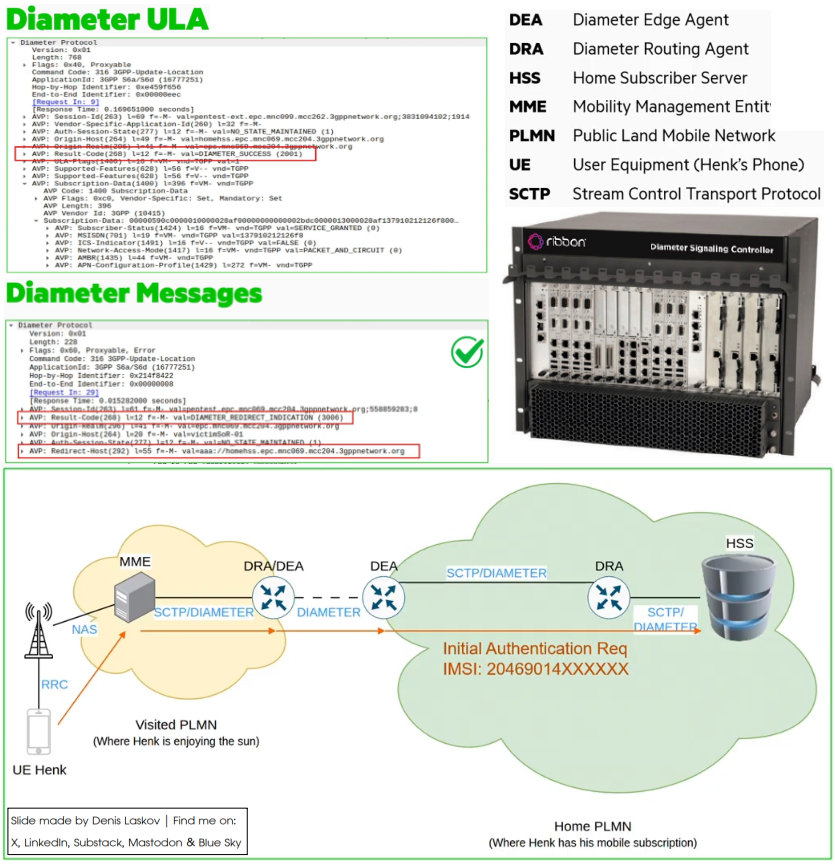
Cell phone roaming and how to hack it: SoR systems and bugs in the Diameter protocol. ☎️🌐📱💣💰 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/cell-phone-r…
Tools such as PsExec.py from Impacket are usually flagged for lateral movement due to the pre-built service executable that is dropped on the remote system. However, some vendors also flag Impacket based on its behaviour. With RustPack, you can easily create…
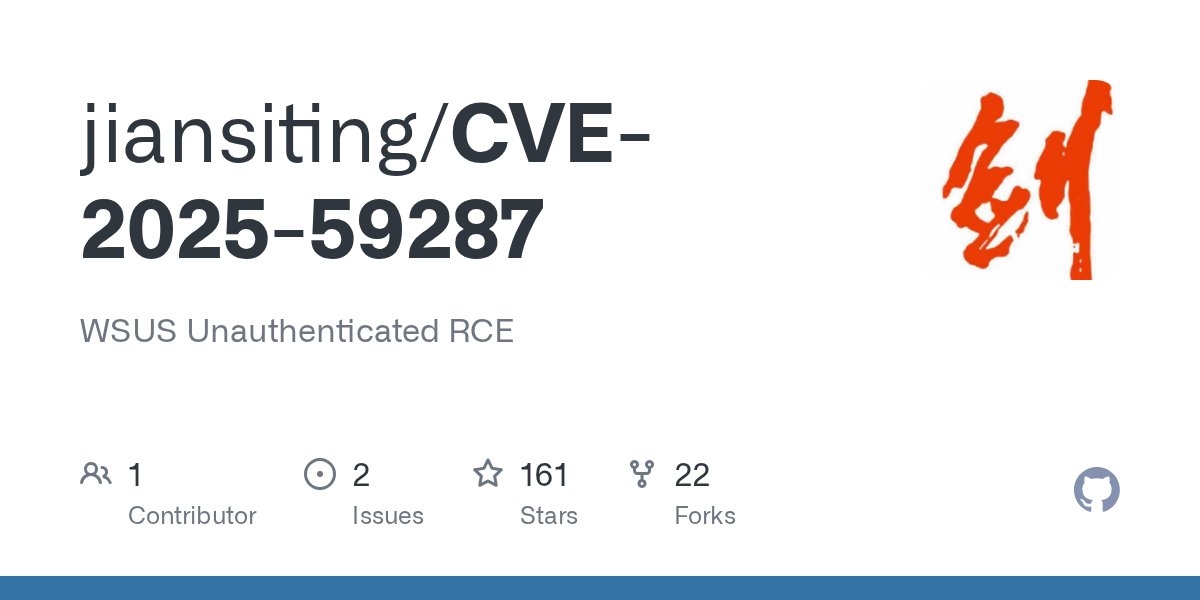
While the exploit craddles from hawktrace for CVE-2025-59287 did not work in our testbed, github.com/jiansiting/CVE… actually did. Be aware, include SCCM when the Software Update Point role is in use, as this requires WSUS.
Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge. research.google/resources/data… Dataset is available for download at: ▪️console.cloud.google.com/storage/browse… [Login required] ▪️gs://net-ntlmv1-tables
![sekurlsa_pw's tweet image. Google research created a dataset with rainbow tables for NetNTLMv1 with the 1122334455667788 challenge.
research.google/resources/data…
Dataset is available for download at:
▪️console.cloud.google.com/storage/browse… [Login required]
▪️gs://net-ntlmv1-tables](https://pbs.twimg.com/media/G4B_bWxW4AAdjlR.png)
Hacking modern ARM processors: Practical side-channel attacks on Cortex-A72 to recover AES. 👨🏻💻🧲👂📟🔗 More details on: LinkedIn: linkedin.com/posts/dlaskov_… Substack: it4sec.substack.com/p/hacking-mode…

The Emulator's Gambit: Executing Code from Non-Executable Memory redops.at/en/blog/the-em…
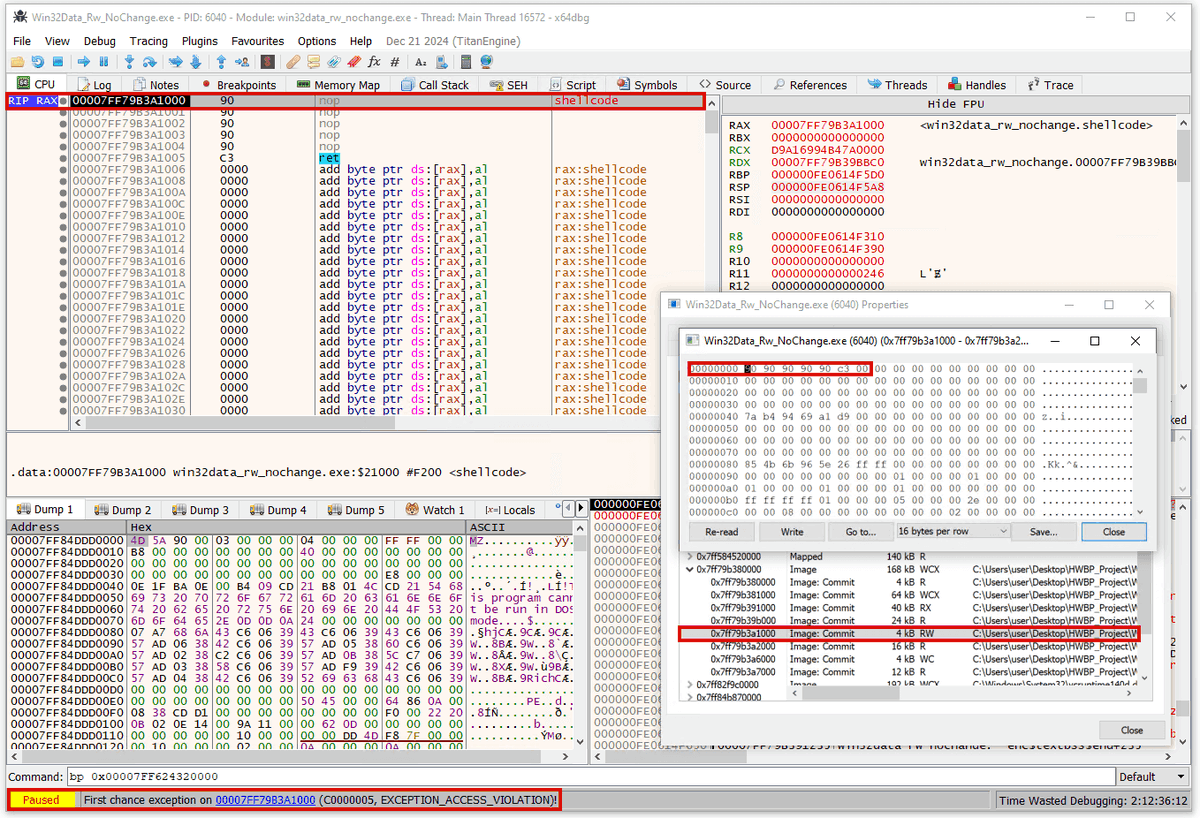
Writing unix viruses in asm is hard, but it's a bunch of fun. I'm pleased to share that my first ever virus is now able to target PIE ELF64 binaries. Next I'd like to encrypt the payload and make it only execute at midnight :)))
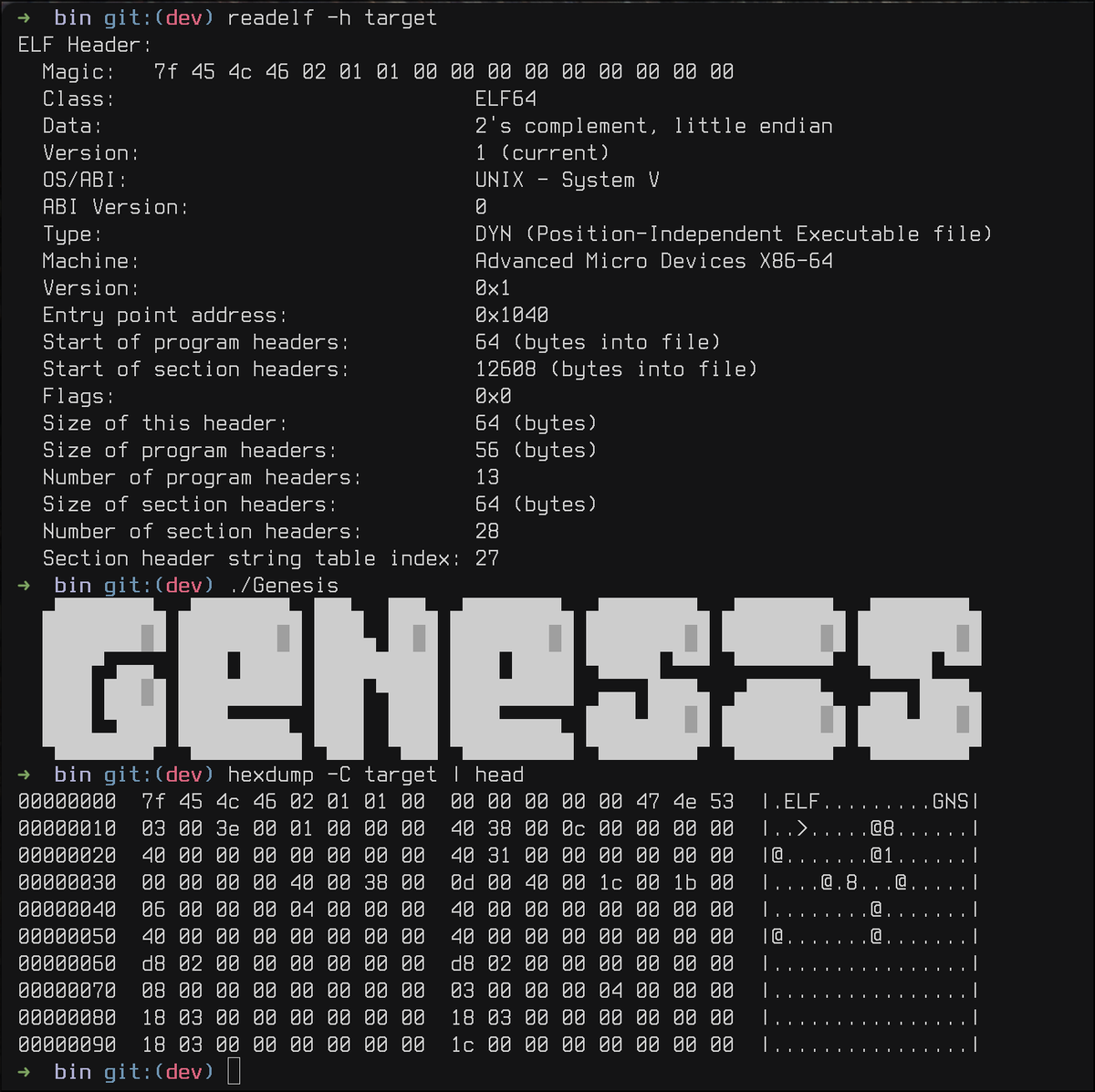
☠ Lenovo CVE-2025-8061 Exploit PoC and write-up for shell popping against LnvMSRIO.sys (3.1.0.36) driver. Try: github.com/symeonp/Lenovo…

An exciting milestone for AI in science: Our C2S-Scale 27B foundation model, built with @Yale and based on Gemma, generated a novel hypothesis about cancer cellular behavior, which scientists experimentally validated in living cells. With more preclinical and clinical tests,…
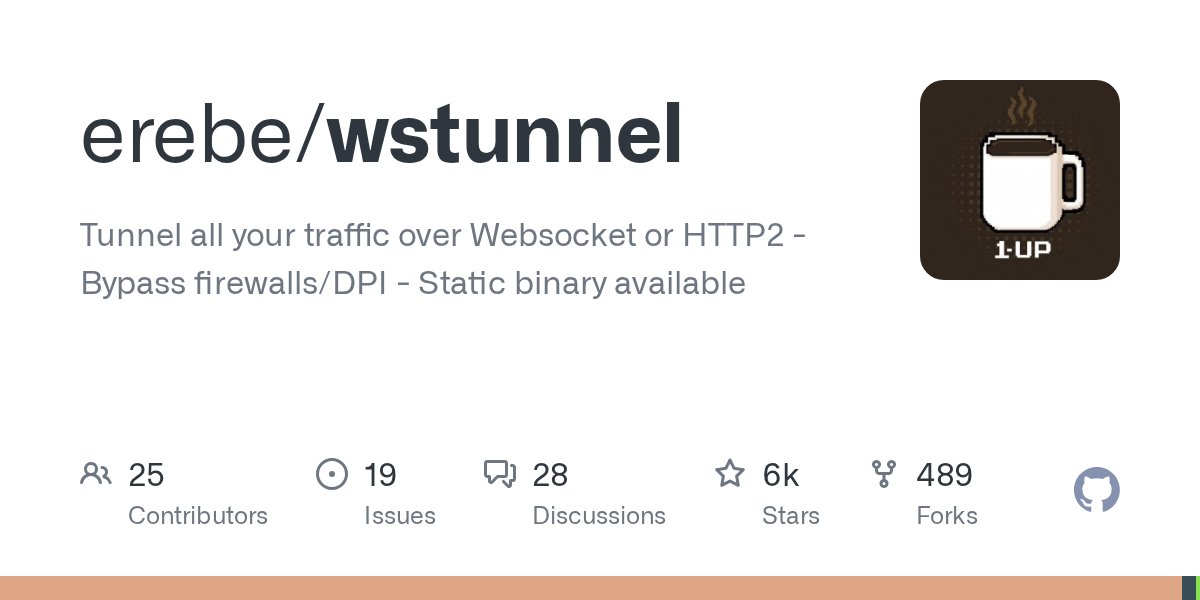
Tunnel all your traffic over Websocket or HTTP2 - Bypass firewalls/DPI - Static binary available github.com/erebe/wstunnel
❗️🐭 Your gaming mouse might be eavesdropping due to a critical vulnerability named Mic-E-Mouse.




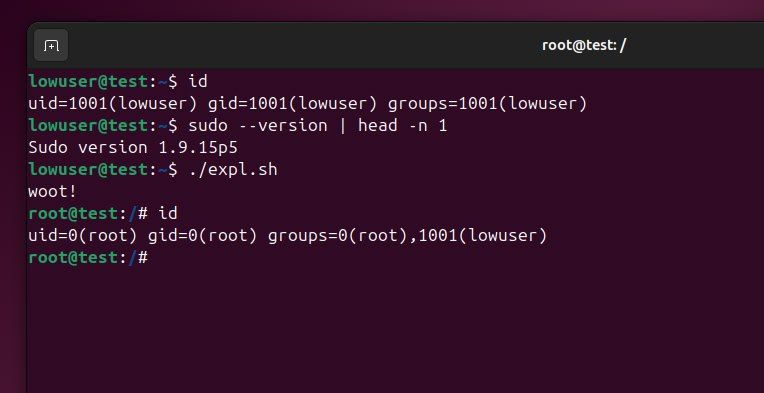
CVE-2025-32463: Sudo before 1.9.17p1 allows local users to obtain root access because /etc/nsswitch.conf from a user-controlled directory is used with the --chroot option. PoC: github.com/kh4sh3i/CVE-20… CVSS: 9.3 Affected Versions: ▪️Vulnerable: sudo 1.9.14 – 1.9.17…
‼️ Iranian nation-state APT CharmingKitten exposed on GitHub. Exposure includes: - Official APT internal network documents - Employee photos - Attack reports - Translation documents - Internal chat files

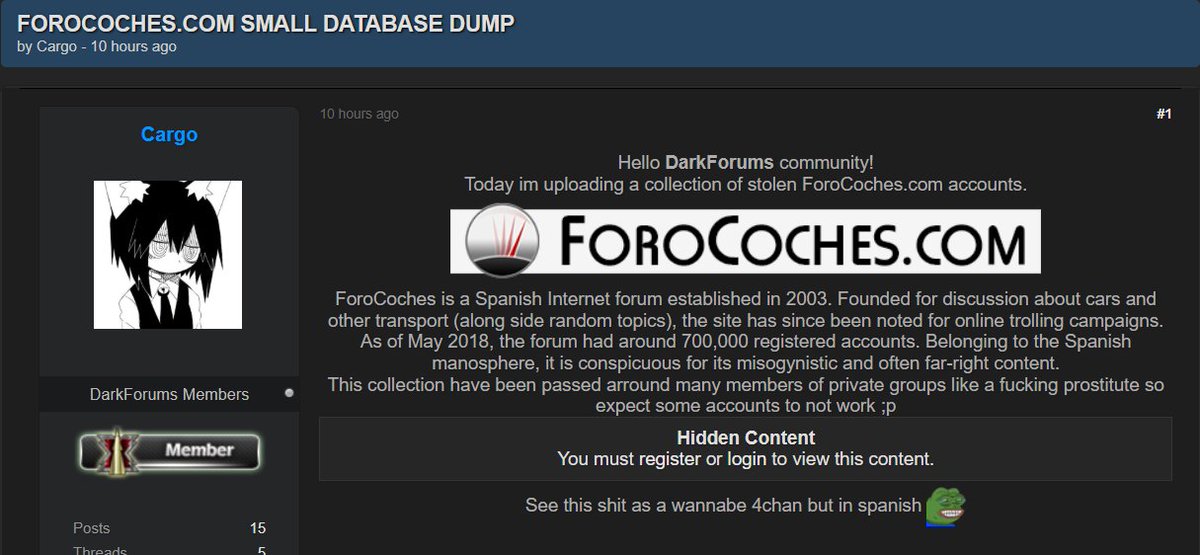
🚨Cyber Alert ‼️ 🇪🇸 Spain - Forocoches The threat actor known as Cargo is leaking a database allegedly belonging to Forocoches. He stated that this collection has been passed around many members of private groups, warning that some accounts may no longer work. discover…
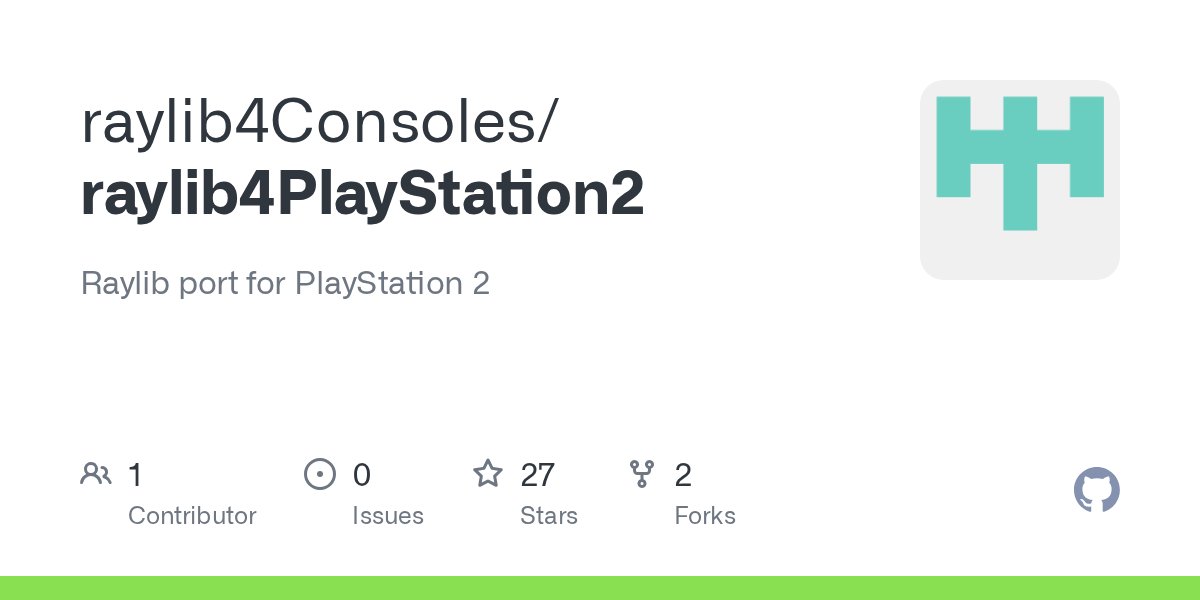
Some raylib love for PlayStation 2 consider it wip. github.com/raylib4Console…
🚨Cyber Alert ‼️ 🇪🇸Spain – A threat actor going by the alias N4t0x has leaked a dataset allegedly containing personal data of Spanish politicians, law enforcement officials, intelligence officers, and their families. The attacker claims to have used a tool called SpainData,…

United States 趨勢
- 1. #SpotifyWrapped 202K posts
- 2. Chris Paul 26K posts
- 3. Hartline 8,231 posts
- 4. Clippers 37.6K posts
- 5. #HappyBirthdayJin 90.9K posts
- 6. Henry Cuellar 2,889 posts
- 7. GreetEat Corp N/A
- 8. David Corenswet 4,732 posts
- 9. Jonathan Bailey 5,967 posts
- 10. ethan hawke 3,119 posts
- 11. South Florida 5,585 posts
- 12. $MSFT 14K posts
- 13. #NSD26 22.3K posts
- 14. Chris Henry Jr 1,032 posts
- 15. #WorldwideHandsomeJin 71.6K posts
- 16. #JINDAY 72.8K posts
- 17. Collin Klein 1,664 posts
- 18. Chris Klieman 1,776 posts
- 19. Apple Music 258K posts
- 20. Penn State 23.9K posts
你可能會喜歡
-
 Эра НЕмилосердия
Эра НЕмилосердия
@f61T8JlKLo3dBaW -
 winterknife 🌻
winterknife 🌻
@_winterknife_ -
 Antonio 's4tan' Parata
Antonio 's4tan' Parata
@s4tan -
 S01den
S01den
@s01den -
 cheko
cheko
@dennis_casanova -
 T
T
@TravisMichiels1 -
 SaykQ
SaykQ
@saykq27393237 -
 nickkkk
nickkkk
@nickkkk1337 -
 Croissant
Croissant
@cosmoscroissant -
 Lipson Thomas Philip
Lipson Thomas Philip
@knightdark_777 -
 Adrian
Adrian
@xsetbv -
 Abhishek Singh
Abhishek Singh
@abhishek_dit -
 Fox anarc
Fox anarc
@fox_anarc -
 BartenderBob
BartenderBob
@TheBartenderBob
Something went wrong.
Something went wrong.