You might like
It's great that AWS already shared a postmortem, and we can understand some things that went wrong, starting the outage. A summary of the events, based on what the AWS team shared
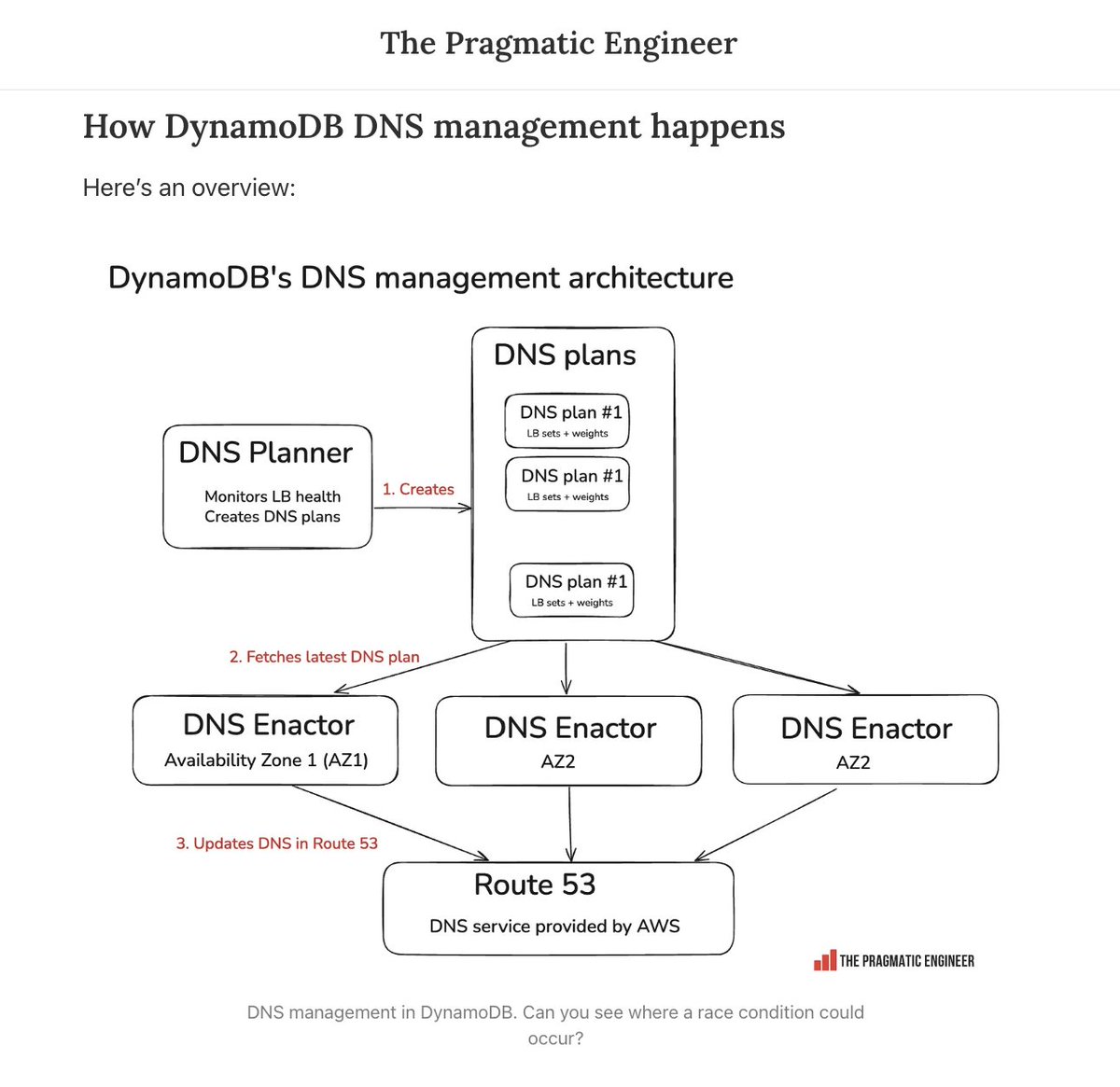
What caused the AWS outage that felt like it took down half the internet on Monday? It started with a race condition in DynamoDB's DNS propagation, which ended up setting the dynamod.us-east-1 .amazonaws .com DNS to empty. A deepdive and more details: blog.pragmaticengineer.com/aws-outage-us-…
MIT literally packed 7 hours with everything you need to know about Gen AI for free

🛡️ 𝐀 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐄𝐧𝐠𝐢𝐧𝐞𝐞𝐫'𝐬 𝐆𝐮𝐢𝐝𝐞 𝐭𝐨 𝐌𝐂𝐏 If you need to learn how to test & secure MCPs in your org in a hurry... Get up to speed in 10min + a free MCP security cheatsheet of exactly what to look for.
I am once again begging you to put your database servers and application servers in the same region.
AI for Security has never been more exciting. Let me present MAPTA, our multi-agent framework that found multiple (now confirmed!) Remote Code Executions (RCE's) in flagship web products of Tier-1 companies. Why the secrecy? We're good boys, letting them cook patched through…

Everything You Need to Know About WebSockets ⚡ If you’re building chat apps, live dashboards, multiplayer games, or real-time systems then WebSockets are your best friend. Here’s a full breakdown 👇

uops.info is an excellent resource for performance optimization - it shows actual latency, throughput, and port usage for every x86 instruction's micro-ops. Essential for anyone doing low-level optimization!

Have you ever wondered what happens if we break compiler conventions? I was able to obfuscate the control flow of a program and hide code by modifying non-volatile registers to modify the behavior of library code. blog.elmo.sg/posts/the-art-…
😈 𝐓𝐫𝐚𝐢𝐧𝐢𝐧𝐠 𝐒𝐩𝐞𝐜𝐢𝐚𝐥𝐢𝐬𝐭 𝐌𝐨𝐝𝐞𝐥𝐬: 𝐀𝐮𝐭𝐨𝐦𝐚𝐭𝐢𝐧𝐠 𝐌𝐚𝐥𝐰𝐚𝐫𝐞 𝐃𝐞𝐯𝐞𝐥𝐨𝐩𝐦𝐞𝐧𝐭 How to make an LLM train itself to write more evasive malware. Outflank’s Kyle Avery describes how a small, specially trained LLM (Dante-7B, based on…


how to find all of the good LLM prompts from darpa's AIxCC including @trailofbits 's Buttercup that just got 2nd place

I just found kubespec.dev and I love it! It's a great way to quickly look up the syntax for Kubernetes objects.
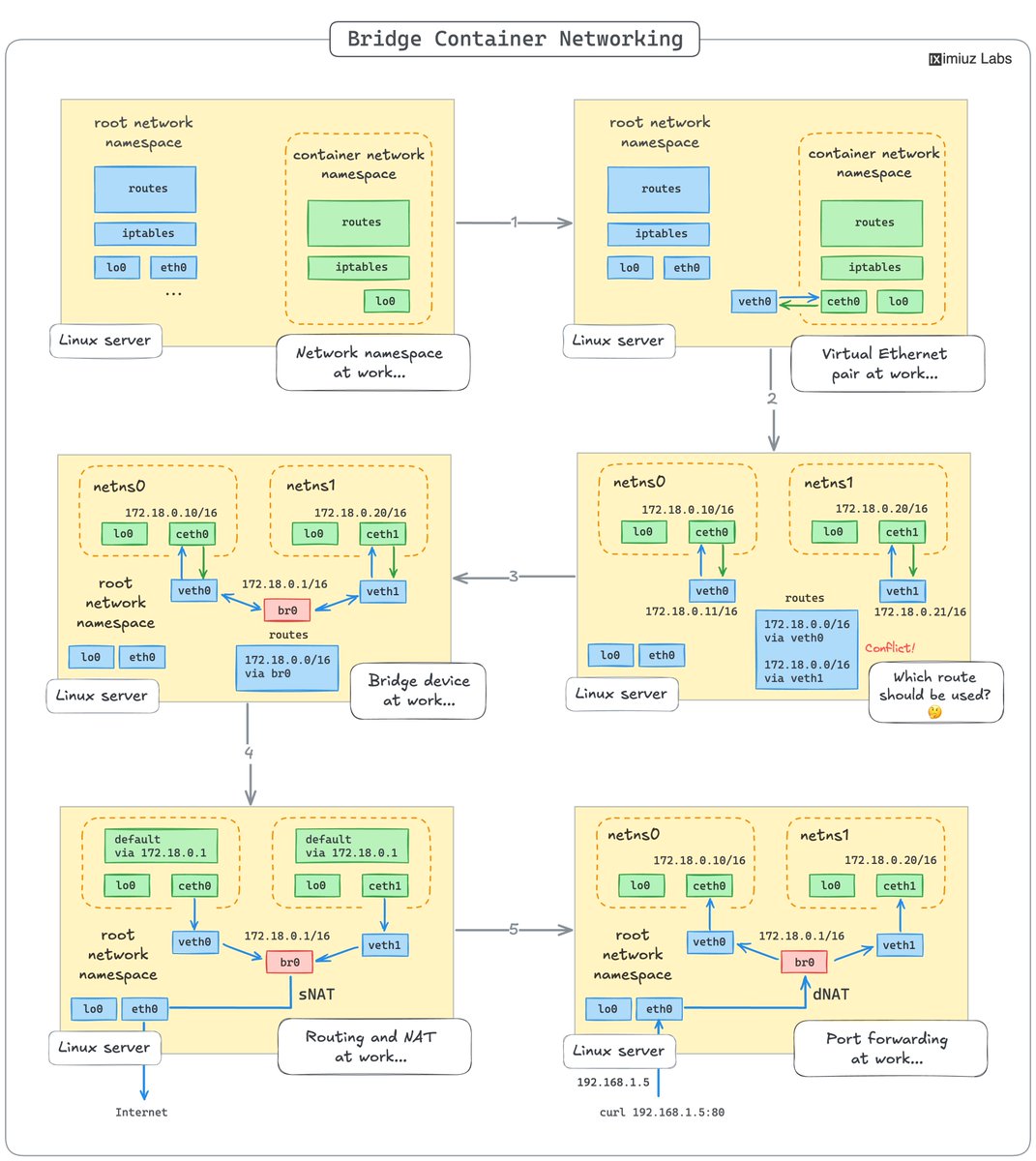
The Keystone of Container Networking: Linux Bridge 🔽 Each container is placed into its own network namespace. Connecting to it can be done via a pair of virtual Ethernet devices (veth). But how to combine multiple such devices into one network? Learn at labs.iximiuz.com/challenges/con…

Not sure why but we have lots of new followers! FFmpeg makes extensive use of hand-written assembly code for huge (10-50x) speed increases so we are providing assembly lessons to teach a new generation of assembly language programmers. Learn more here: github.com/FFmpeg/asm-les…
OpenAI has released a guide on how to finetune their open-source models: cookbook.openai.com/articles/gpt-o…

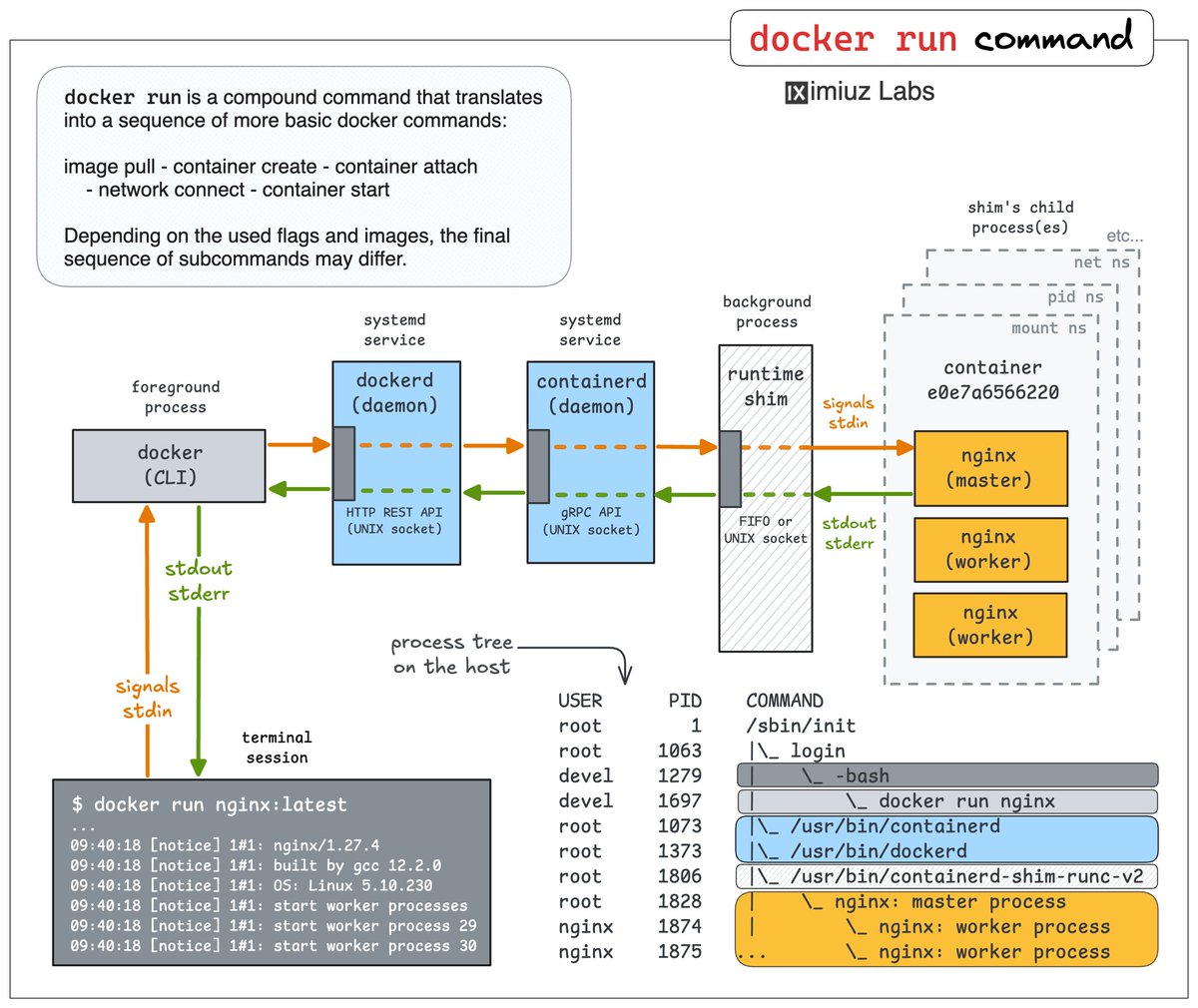
What Exactly Does "docker run -it" Do? 🧐 When a container needs to run an interactive app such as a shell, language REPL, or text editor, the "docker run" command requires two extra flags: -i and -t. Explore how they work by solving this challenge labs.iximiuz.com/challenges/doc…

Docker 101: Run Your First Containers 🛠️ Get started with Docker by solving these practical problems: - Run a hello-world container - Run a web-server container - Run an interactive shell container Automated checks and hints included! labs.iximiuz.com/challenges/doc…
How Container Networking Works 🧐 Most Docker installations and Kubernetes clusters have the same bridge container network setup. The best way to understand how it works? Try reproducing one from scratch using nothing but the standard Linux commands: labs.iximiuz.com/tutorials/cont…
The purpose of the Kubernetes networking guide is to provide an overview of various Kubernetes networking components with a specific focus on exactly how they implement the required functionality ➜ ku.bz/wFZSJh9bK
I was messing around with symbol resolution in ELF and came up with an obfuscation technique on abusing symbol resolution in ELF programs that is able to trick tools (i.e. Ghidra, IDA, GDB) into showing the wrong library function calls. blog.elmo.sg/posts/breaking…
United States Trends
- 1. Veterans Day 34.3K posts
- 2. Packers 101K posts
- 3. Good Tuesday 21.1K posts
- 4. Eagles 129K posts
- 5. SoftBank 4,512 posts
- 6. Benítez 14K posts
- 7. #WWERaw 142K posts
- 8. Jordan Love 15.6K posts
- 9. Matt Lafleur 9,063 posts
- 10. JOONGDUNK BRIGHT SKIN 268K posts
- 11. Bond 59.5K posts
- 12. Berkeley 71.5K posts
- 13. Green Bay 19.2K posts
- 14. Jalen 24.3K posts
- 15. Grayson Allen 4,776 posts
- 16. Sirianni 5,212 posts
- 17. Kevin Patullo 7,170 posts
- 18. AJ Brown 7,320 posts
- 19. Tsushima 2,364 posts
- 20. McManus 4,560 posts
You might like
-
 Exploit Pack
Exploit Pack
@Exploit_Pack -
 DEVCORE
DEVCORE
@d3vc0r3 -
 Austin
Austin
@ilove2pwn_ -
 Mr. Anthony 安東尼
Mr. Anthony 安東尼
@darkfloyd1014 -
 Motasem Hamdan
Motasem Hamdan
@ManMotasem -
 Rayhan0x01
Rayhan0x01
@Rayhan0x01 -
 Ben Spring
Ben Spring
@springjben -
 Bruce Chen
Bruce Chen
@bruce30262 -
 Ken Gannon (伊藤 剣)
Ken Gannon (伊藤 剣)
@Yogehi -
 Ioannis Stais
Ioannis Stais
@Einstais -
 Ch33z_plz🧀🐀
Ch33z_plz🧀🐀
@Ch33z_plz -
 0v3rl04d⚡
0v3rl04d⚡
@ov3rlo4d -
 Ravi Pandey
Ravi Pandey
@ravipandey0007 -
 Brett Hawkins
Brett Hawkins
@h4wkst3r -
 ihack4falafel
ihack4falafel
@ihack4falafel
Something went wrong.
Something went wrong.