Elastic Security Labs
@elasticseclabs
Elastic Security Labs is democratizing security by sharing knowledge and capabilities necessary to prepare for threats. Spiritually serving humanity since 2019.
You might like
Fantastic work by the @harfanglab team describing and documenting indicators and detection logic for "RudePanda," described with complementary analysis by the @elasticseclabs team as "TOLLBOOTH." harfanglab.io/insidethelab/r…
Late summer our stuff stopped an infection chain involving a driver, a previously undocumented malicious IIS module, and ASP .NET viewstate abuse.
#ElasticSecurityLabs releases nightMARE, a Python-based library for malware analysts that we use to build tools for acquiring intelligence. Read more about it here: go.es.io/46Zt8Ac
Really great research from @bluish_red_ and the team at @elasticseclabs! Worth a read and if you're running IIS, should definitely check if you're impacted.
Amazing experience to work the great folks @elasticseclabs on this write up to showcase some interesting activity we discovered together! Excited to keep our collaboration going to give back what we can to the security community!
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
Your team and the customer squashing it from the get go was great! Love talking about good folks doin' the good work!
This was a cool project for a few reasons. First, some of us have been working with Texas A&M since Endgame and it’s a partnership with a ton of history! Also it is a blast for us to work with other experts to achieve successes!
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
Thanks for being generous with your time and expertise on this @SreekarMad! Good stuff! @ValidinLLC
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
Thank y'all for reading it, Michael!
Love some IIS modules on a Tuesday. Thank you all for sharing
In September, #ElasticSecurityLabs published 78 new rules! Take a look at the overview and learn how we manage these rulesets.

Heading to my 3rd #OBTS 🌴☀️🌊today! Best conference out there. Honored to be speaking again this year alongside so many other incredible #Apple 🍎 security researchers. It’s gonna be a blast, can’t wait to see everyone! Pumped to get to share my research into using and abusing…
@elasticseclabs is currently researching a new family of IIS malware impacting a large number of organizations globally. With a US university-based MDR provider, we’ve observed a novel attack chain, RMMs, a Godzilla-forked framework, and a malicious driver. Details coming soon.
i'm gonna keep on dancing at the WARMCOOKIE string_bank

#ElasticSecurityLabs has kept tabs on #WARMCOOKIE, a backdoor we disclosed in June 2024 that used employment-related phishing lures to infect victims. Learn how this threat’s evolving: go.es.io/46O8pOo
Predictive indicator for WARMCOOKIE 🍪🍪🍪 infrastructure. @ValidinLLC @500mk500

#ElasticSecurityLabs has kept tabs on #WARMCOOKIE, a backdoor we disclosed in June 2024 that used employment-related phishing lures to infect victims. Learn how this threat’s evolving: go.es.io/46O8pOo
#ElasticSecurityLabs has kept tabs on #WARMCOOKIE, a backdoor we disclosed in June 2024 that used employment-related phishing lures to infect victims. Learn how this threat’s evolving: go.es.io/46O8pOo
Linux syscall hooks were forever changed with kernel 6.9, check out this article from #ElasticSecurityLabs describing #FlipSwitch– the latest in Linux hooking: go.es.io/4nSrCW3
nice technique! #Elastic EDR (Elastic Defend) is not affected + we do have an existing behavior protection rule that will terminate WerFaultSecure.exe (to protect other processes) github.com/elastic/protec…

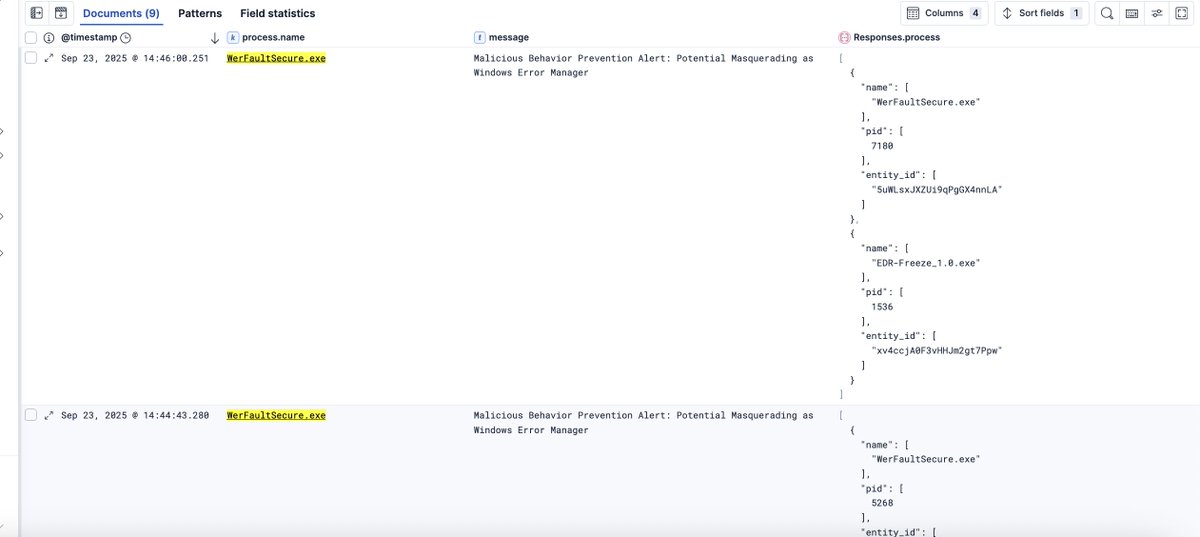
We can exploit the #securityvulnerability of Windows Error Reporting to put EDRs and #antimalware into a coma-like state. By using the EDR-Freeze #redteam tool: Github: TwoSevenOneT/EDR-Freeze

Elastic Security Labs MCP tool research shows how tool-poisoning, orchestration injection, and rug-pulls lead to data exfil & RCE. Includes actionable detections + hardening. Read it if you run agents: go.es.io/3VofX5m
In July and August, #ElasticSecurityLabs published 113 new rules! Take a look at the overview and learn how we manage these rulesets.

United States Trends
- 1. Lakers 64.5K posts
- 2. Luka 63K posts
- 3. Wemby 24.4K posts
- 4. Marcus Smart 5,177 posts
- 5. #LakeShow 5,189 posts
- 6. Blazers 7,564 posts
- 7. Russ 9,523 posts
- 8. Ayton 13.8K posts
- 9. Richard 45.4K posts
- 10. Horford 1,763 posts
- 11. #RipCity N/A
- 12. #AmphoreusStamp 5,190 posts
- 13. Podz 2,332 posts
- 14. Champagnie 1,188 posts
- 15. Spencer Knight N/A
- 16. #AEWDynamite 19.8K posts
- 17. Thunder 31.2K posts
- 18. Kuminga 3,234 posts
- 19. #dispatch 59.9K posts
- 20. Nico Harrison 1,492 posts
You might like
-
 ACE Responder
ACE Responder
@ACEResponder -
 Michael Koczwara
Michael Koczwara
@MichalKoczwara -
 Olaf Hartong
Olaf Hartong
@olafhartong -
 Kostas
Kostas
@Kostastsale -
 Samir
Samir
@SBousseaden -
 Mehmet Ergene
Mehmet Ergene
@Cyb3rMonk -
 sigma
sigma
@sigma_hq -
 Aaron Jornet
Aaron Jornet
@RexorVc0 -
 RussianPanda 🐼 🇺🇦
RussianPanda 🐼 🇺🇦
@RussianPanda9xx -
 Jai Minton
Jai Minton
@CyberRaiju -
 Andrew Pease
Andrew Pease
@andythevariable -
 Jonny Johnson
Jonny Johnson
@JonnyJohnson_ -
 SOC Prime
SOC Prime
@SOC_Prime -
 Nasreddine Bencherchali
Nasreddine Bencherchali
@nas_bench -
 Joe Desimone
Joe Desimone
@dez_
Something went wrong.
Something went wrong.