#elasticsecuritylabs search results
In September, #ElasticSecurityLabs published 78 new rules! Take a look at the overview and learn how we manage these rulesets.

In July and August, #ElasticSecurityLabs published 113 new rules! Take a look at the overview and learn how we manage these rulesets.

#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
#ElasticSecurityLabs saw phishing campaigns deploying LNK files masquerading as PDFs ([.]pdf[.]lnk) to load a Rust-based implant, using Discord C2 via the serenity crate. Bot Token/Server ID were AES-encrypted and Base64-encoded; for our PoC, we used our own.
![elasticseclabs's tweet image. #ElasticSecurityLabs saw phishing campaigns deploying LNK files masquerading as PDFs ([.]pdf[.]lnk) to load a Rust-based implant, using Discord C2 via the serenity crate.
Bot Token/Server ID were AES-encrypted and Base64-encoded; for our PoC, we used our own.](https://pbs.twimg.com/media/G0a0MnDWUAAzS2Q.jpg)
#ElasticSecurityLabs is observing #ValleyRAT infections using the following #LOLBins for execution: - DeviceCredentialDeployment.exe (proxy execution) - Tttracer (proxy execution) - Renames curl[.]exe (masquerade) - Ttdinject (remote injection) - Pester (proxy execution)
![elasticseclabs's tweet image. #ElasticSecurityLabs is observing #ValleyRAT infections using the following #LOLBins for execution:
- DeviceCredentialDeployment.exe (proxy execution)
- Tttracer (proxy execution)
- Renames curl[.]exe (masquerade)
- Ttdinject (remote injection)
- Pester (proxy execution)](https://pbs.twimg.com/media/G0-StOlXQAAJeIF.jpg)
#ElasticSecurityLabs releases nightMARE, a Python-based library for malware analysts that we use to build tools for acquiring intelligence. Read more about it here: go.es.io/46Zt8Ac
#ElasticSecurityLabs gets to the root cause of an Authenticode signature error, reverse-engineering an undocumented Microsoft function in the process. Learn how we solved the problem here: go.es.io/3K2vG7u
#ElasticSecurityLabs has kept tabs on #WARMCOOKIE, a backdoor we disclosed in June 2024 that used employment-related phishing lures to infect victims. Learn how this threat’s evolving: go.es.io/46O8pOo
#ElasticSecurityLabs is monitoring infections deploying #Akira Stealer, a Python stealer rewritten in Golang. Distribution involves packaging a malicious Electron application with the intended application in a .RAR archive. NodeJS Electron App -> Python loader -> Akira Stealer

Greetings from the floor! Devon Kerr here from #ElasticSecurityLabs. We’re in Las Vegas this week at #BHUSA giving you a behind the scenes look at the big show. Stay tuned and come say hi! — DK (@_devonkerr_)

#ElasticSecurityLabs continues to observe phishing campaigns leveraging Cloudflare tunnels distributing multiple malware families (#VenomRAT, #DCRat, #XWorm) simultaneously. These threat actors are abusing LLMs to produce simple Python shellcode loaders for injection

The #ElasticSecurityLabs takeover continues on day 2 at #BHUSA! Come on over to booth 3546 to see Dhrumil in about 10 minutes, he’s breaking down AI for the modern SOC. I will see you there! -DK (@_devonkerr_)

In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

In June, #ElasticSecurityLabs published 13 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/4kOcbfR

Linux syscall hooks were forever changed with kernel 6.9, check out this article from #ElasticSecurityLabs describing #FlipSwitch– the latest in Linux hooking: go.es.io/4nSrCW3
New research on NOVABLIGHT, a NodeJS infostealer sold as MaaS! Discover its tactics, from credential theft & cryptowallet compromise to advanced obfuscation & anti-analysis techniques: go.es.io/459JGDA #ElasticSecurityLabs #infostealer
New research from our #ElasticSecurityLabs team: we dive into how infostealers are leveraging a stolen Shellter evasion tool to deploy data-stealing malware. Learn more & get our unpacker: go.es.io/4ldCM72 #malware #rhadamanthys #ghostpulse
The #ElasticSecurityLabs team is observing exploitation activity targeting on-premise SharePoint servers related to a series of CVEs, which can be chained together, allowing remote code execution. Use these two rules to help identify this activity: go.es.io/4f70FLk
New research from #ElasticSecurityLabs uncovers a new ClickFix campaign! Learn how attackers are using GHOSTPULSE and ARECHCLIENT2 (SECTOPRAT) in multi-stage attacks to deploy RATs and steal data. Stay informed: go.es.io/4l912GO
Ebury is some fascinating and sophisticated malware! Props to @ESETresearch for their extensive threat research report. Happy to see our coverage at @elastic is on point. 🔍👏 #ebury #ElasticSecurityLabs #elastic
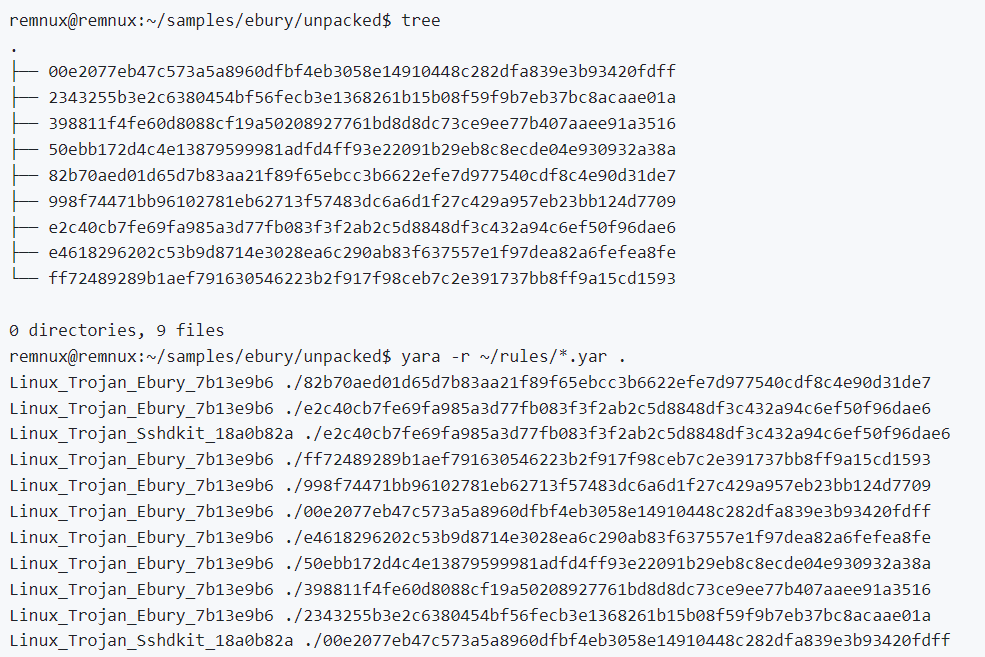
#Breaking #ESETresearch releases a paper about Ebury, among the most advanced server-side Linux malware, which was deployed to 400,000 servers over the course of 15 years, primarily for financial gain. @marc_etienne_ welivesecurity.com/en/eset-resear… 1/8
#ElasticSecurityLabs releases nightMARE, a Python-based library for malware analysts that we use to build tools for acquiring intelligence. Read more about it here: go.es.io/46Zt8Ac
#ElasticSecurityLabs joins forces with @tamusystem and discloses TOLLBOOTH, an IIS module used for SEO abuse that relies on publicly exposed ASP. NET machine keys: go.es.io/3L68p57
In September, #ElasticSecurityLabs published 78 new rules! Take a look at the overview and learn how we manage these rulesets.

#ElasticSecurityLabs has kept tabs on #WARMCOOKIE, a backdoor we disclosed in June 2024 that used employment-related phishing lures to infect victims. Learn how this threat’s evolving: go.es.io/46O8pOo
Linux syscall hooks were forever changed with kernel 6.9, check out this article from #ElasticSecurityLabs describing #FlipSwitch– the latest in Linux hooking: go.es.io/4nSrCW3
In July and August, #ElasticSecurityLabs published 113 new rules! Take a look at the overview and learn how we manage these rulesets.

#ElasticSecurityLabs is observing #ValleyRAT infections using the following #LOLBins for execution: - DeviceCredentialDeployment.exe (proxy execution) - Tttracer (proxy execution) - Renames curl[.]exe (masquerade) - Ttdinject (remote injection) - Pester (proxy execution)
![elasticseclabs's tweet image. #ElasticSecurityLabs is observing #ValleyRAT infections using the following #LOLBins for execution:
- DeviceCredentialDeployment.exe (proxy execution)
- Tttracer (proxy execution)
- Renames curl[.]exe (masquerade)
- Ttdinject (remote injection)
- Pester (proxy execution)](https://pbs.twimg.com/media/G0-StOlXQAAJeIF.jpg)
#ElasticSecurityLabs saw phishing campaigns deploying LNK files masquerading as PDFs ([.]pdf[.]lnk) to load a Rust-based implant, using Discord C2 via the serenity crate. Bot Token/Server ID were AES-encrypted and Base64-encoded; for our PoC, we used our own.
![elasticseclabs's tweet image. #ElasticSecurityLabs saw phishing campaigns deploying LNK files masquerading as PDFs ([.]pdf[.]lnk) to load a Rust-based implant, using Discord C2 via the serenity crate.
Bot Token/Server ID were AES-encrypted and Base64-encoded; for our PoC, we used our own.](https://pbs.twimg.com/media/G0a0MnDWUAAzS2Q.jpg)
#ElasticSecurityLabs gets to the root cause of an Authenticode signature error, reverse-engineering an undocumented Microsoft function in the process. Learn how we solved the problem here: go.es.io/3K2vG7u
#ElasticSecurityLabs continues to observe phishing campaigns leveraging Cloudflare tunnels distributing multiple malware families (#VenomRAT, #DCRat, #XWorm) simultaneously. These threat actors are abusing LLMs to produce simple Python shellcode loaders for injection

#ElasticSecurityLabs is monitoring infections deploying #Akira Stealer, a Python stealer rewritten in Golang. Distribution involves packaging a malicious Electron application with the intended application in a .RAR archive. NodeJS Electron App -> Python loader -> Akira Stealer

Summarizing hundreds of events and proving analysts with short, clear guidance is how it progresses— but it ends with a human decision to ACT. #ElasticSecurityLabs expertise is inside to help you do that. Stop spectating, start operating. -DK (@_devonkerr_)
The #ElasticSecurityLabs takeover continues on day 2 at #BHUSA! Come on over to booth 3546 to see Dhrumil in about 10 minutes, he’s breaking down AI for the modern SOC. I will see you there! -DK (@_devonkerr_)

Greetings from the floor! Devon Kerr here from #ElasticSecurityLabs. We’re in Las Vegas this week at #BHUSA giving you a behind the scenes look at the big show. Stay tuned and come say hi! — DK (@_devonkerr_)

New research on NOVABLIGHT, a NodeJS infostealer sold as MaaS! Discover its tactics, from credential theft & cryptowallet compromise to advanced obfuscation & anti-analysis techniques: go.es.io/459JGDA #ElasticSecurityLabs #infostealer
The #ElasticSecurityLabs team is observing exploitation activity targeting on-premise SharePoint servers related to a series of CVEs, which can be chained together, allowing remote code execution. Use these two rules to help identify this activity: go.es.io/4f70FLk
In June, #ElasticSecurityLabs published 13 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/4kOcbfR

New research from our #ElasticSecurityLabs team: we dive into how infostealers are leveraging a stolen Shellter evasion tool to deploy data-stealing malware. Learn more & get our unpacker: go.es.io/4ldCM72 #malware #rhadamanthys #ghostpulse
New research from #ElasticSecurityLabs uncovers a new ClickFix campaign! Learn how attackers are using GHOSTPULSE and ARECHCLIENT2 (SECTOPRAT) in multi-stage attacks to deploy RATs and steal data. Stay informed: go.es.io/4l912GO
In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

In July and August, #ElasticSecurityLabs published 113 new rules! Take a look at the overview and learn how we manage these rulesets.

In September, #ElasticSecurityLabs published 78 new rules! Take a look at the overview and learn how we manage these rulesets.

#ElasticSecurityLabs is observing #ValleyRAT infections using the following #LOLBins for execution: - DeviceCredentialDeployment.exe (proxy execution) - Tttracer (proxy execution) - Renames curl[.]exe (masquerade) - Ttdinject (remote injection) - Pester (proxy execution)
![elasticseclabs's tweet image. #ElasticSecurityLabs is observing #ValleyRAT infections using the following #LOLBins for execution:
- DeviceCredentialDeployment.exe (proxy execution)
- Tttracer (proxy execution)
- Renames curl[.]exe (masquerade)
- Ttdinject (remote injection)
- Pester (proxy execution)](https://pbs.twimg.com/media/G0-StOlXQAAJeIF.jpg)
#ElasticSecurityLabs saw phishing campaigns deploying LNK files masquerading as PDFs ([.]pdf[.]lnk) to load a Rust-based implant, using Discord C2 via the serenity crate. Bot Token/Server ID were AES-encrypted and Base64-encoded; for our PoC, we used our own.
![elasticseclabs's tweet image. #ElasticSecurityLabs saw phishing campaigns deploying LNK files masquerading as PDFs ([.]pdf[.]lnk) to load a Rust-based implant, using Discord C2 via the serenity crate.
Bot Token/Server ID were AES-encrypted and Base64-encoded; for our PoC, we used our own.](https://pbs.twimg.com/media/G0a0MnDWUAAzS2Q.jpg)
In August, Elastic Security published 46 brand new detection rules! Check out the details: #ElasticSecurityLabs

In September, Elastic Security published 77 brand-new detection rules! Check out the overview ⬇️ #ElasticSecurityLabs

#ElasticSecurityLabs is monitoring infections deploying #Akira Stealer, a Python stealer rewritten in Golang. Distribution involves packaging a malicious Electron application with the intended application in a .RAR archive. NodeJS Electron App -> Python loader -> Akira Stealer

#ElasticSecurityLabs continues to observe phishing campaigns leveraging Cloudflare tunnels distributing multiple malware families (#VenomRAT, #DCRat, #XWorm) simultaneously. These threat actors are abusing LLMs to produce simple Python shellcode loaders for injection

Greetings from the floor! Devon Kerr here from #ElasticSecurityLabs. We’re in Las Vegas this week at #BHUSA giving you a behind the scenes look at the big show. Stay tuned and come say hi! — DK (@_devonkerr_)

In May, #ElasticSecurityLabs published 52 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/45JHiVR #detectionengineering #SIEM #EDR

In October, Elastic Security published 81 brand-new detection rules! Check out the overview and see all of our detection rules here: go.es.io/48IpI4g #ElasticSecurityLabs #SIEM #EDR

In November and December, #ElasticSecurityLabs published 47 new rules to @elastic Security! Browse these rules and more: go.es.io/3VzdBRz Our next protection update will occur in early February. Happy holidays from our detection engineering team!




In March, #ElasticSecurityLabs published 67 new rules! Take a look at the overview, or check out our entire library of protections here: go.es.io/42qPQhc #detectionengineering #SIEM #EDR

You can access our #detectionengineering repos, but how about a closer look? The 2025 State of Detection Engineering at Elastic is a new #report from #ElasticSecurityLabs detailing how we create and assess our prebuilt rules. Check it out: go.es.io/4jnrXhA

In April, #ElasticSecurityLabs published 62 new rules! Take a look at the overview and learn how we manage these rulesets: go.es.io/3EX0NiN #detectionengineering #SIEM #EDR

The #ElasticSecurityLabs takeover continues on day 2 at #BHUSA! Come on over to booth 3546 to see Dhrumil in about 10 minutes, he’s breaking down AI for the modern SOC. I will see you there! -DK (@_devonkerr_)

In February, #ElasticSecurityLabs published 55 brand new rules! Take a look at the overview, or check out our entire library of #detectionrules here: go.es.io/4kadFBQ #detectionengineering #EDR

Did you miss our webinar on the 2024 Elastic Global Threat Report? It’s available on-demand for your viewing entertainment! Our expert recap is ready whenever you are: go.es.io/3YrKPmq #ElasticSecurityLabs

In January, Elastic Security published 77 brand-new rules! Take a look at the overview, or check out our entire detection rule library here: go.es.io/4hpyAir #ElasticSecurityLabs

Ebury is some fascinating and sophisticated malware! Props to @ESETresearch for their extensive threat research report. Happy to see our coverage at @elastic is on point. 🔍👏 #ebury #ElasticSecurityLabs #elastic

#Breaking #ESETresearch releases a paper about Ebury, among the most advanced server-side Linux malware, which was deployed to 400,000 servers over the course of 15 years, primarily for financial gain. @marc_etienne_ welivesecurity.com/en/eset-resear… 1/8
Something went wrong.
Something went wrong.
United States Trends
- 1. #WWERaw 49.5K posts
- 2. John Cena 47.1K posts
- 3. Packers 40.7K posts
- 4. Eagles 65.8K posts
- 5. #RawOnNetflix 1,331 posts
- 6. GRAND SLAM CENA 10.3K posts
- 7. #GoPackGo 4,400 posts
- 8. Jalen 14.7K posts
- 9. Cade Horton 1,093 posts
- 10. Drake Baldwin 4,943 posts
- 11. Go Birds 17.3K posts
- 12. Tush Push 9,735 posts
- 13. Dirty Dom 1,491 posts
- 14. Shipley N/A
- 15. Triple H 5,327 posts
- 16. Monday Night Football 6,105 posts
- 17. Edgerrin Cooper N/A
- 18. FINE SPEECH 1,618 posts
- 19. Green Bay 10K posts
- 20. Dominik Mysterio 9,019 posts












