
Encryption Consulting LLC
@encryptioncons
We offer Code Signing and Certificate Lifecycle Management products along with PKI, HSM, and Other Encryption platform Consulting, Support, and Training.
你可能會喜歡
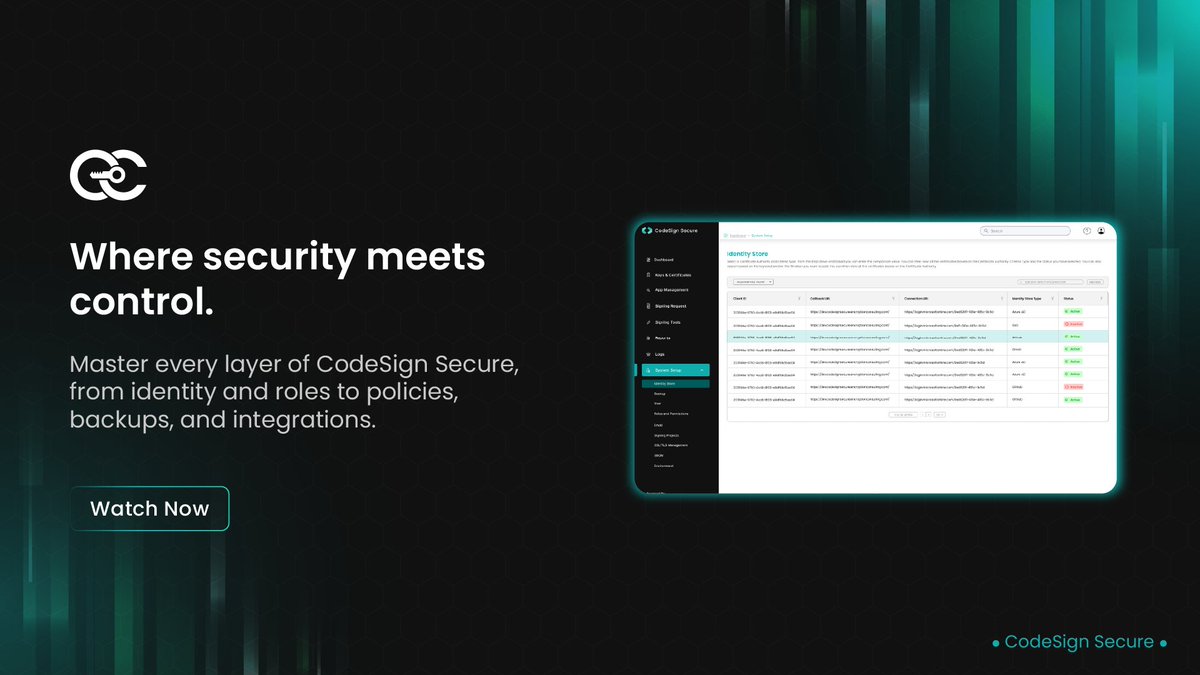
In a secure code signing environment, precise configuration and access control are non-negotiable. Our walkthrough explores how these essentials come together in CodeSign Secure. It covers identity store setup, user management, and role-based permissions in action. You’ll also…
The PQC Readiness Assessment serves as the definitive, critical strategy for organizations to proactively defend against the imminent threat of quantum computers breaking current encryption. This blog fluently the necessary steps, walking through the entire process: discovering…
Cryptographic discovery is the starting point for any serious PQC journey, giving organizations a clear understanding of where their cryptography lives and how prepared they truly are for the quantum shift. This video unpacks that foundation in a relatable, easy-to-follow way…
In every Public Key Infrastructure (PKI), trust is defined and enforced through two foundational documents: the Certificate Policy (CP) and the Certification Practice Statement (CPS). These documents govern how certificates are issued, managed, and trusted across digital…

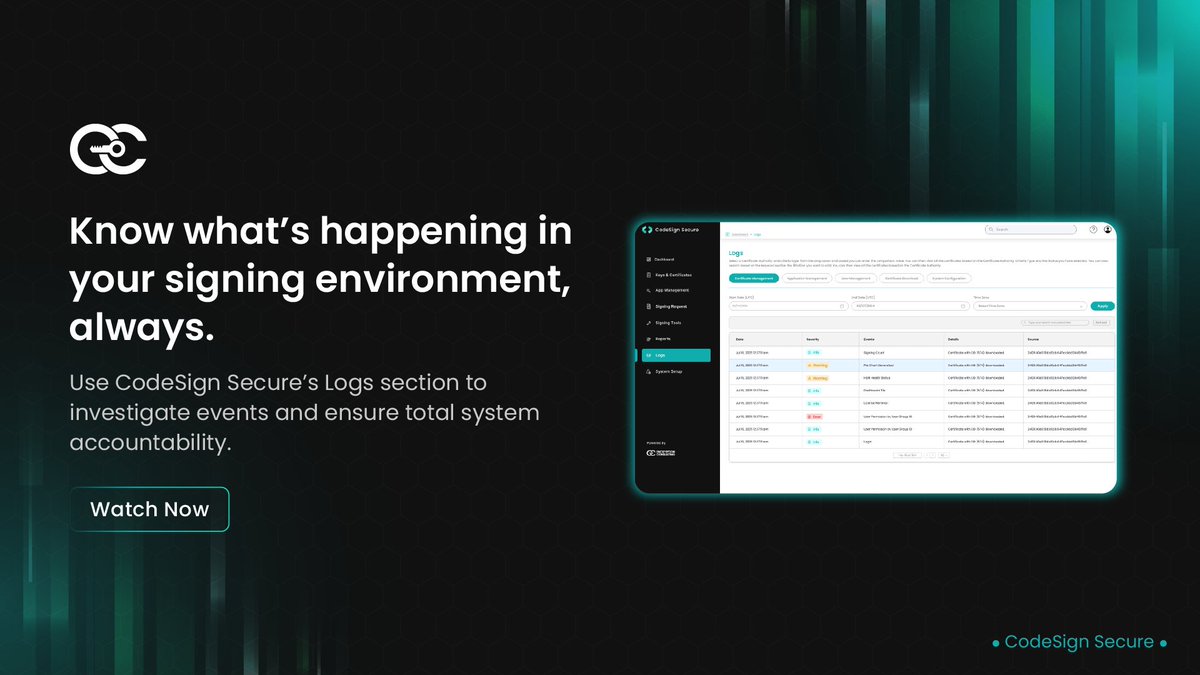
This video provides a concise overview of CodeSecure’s log management interface. It outlines how operational events are captured and structured for analysis. The walkthrough demonstrates how JSON-formatted logs enhance SIEM performance. It also highlights export options and…
CertSecure Manager’s integration with Azure Key Vault elevates cloud-ready certificate management for modern enterprises. The blog outlines how automated uploads, centralized controls, and secure workflows optimize PKI operations. It also breaks down admin prerequisites,…

The System Setup module is central to operationalizing enterprise-grade code signing. This video breaks down the core configuration components that underpin secure platform governance. It walks through identity store integration, backup orchestration, user administration, and…

Driving enterprise resilience requires a structured, policy-driven approach to certificate governance that aligns with emerging security mandates. This blog unpacks the rising complexity of certificate ecosystems and outlines why CLM is now a board-level priority. It provides a…

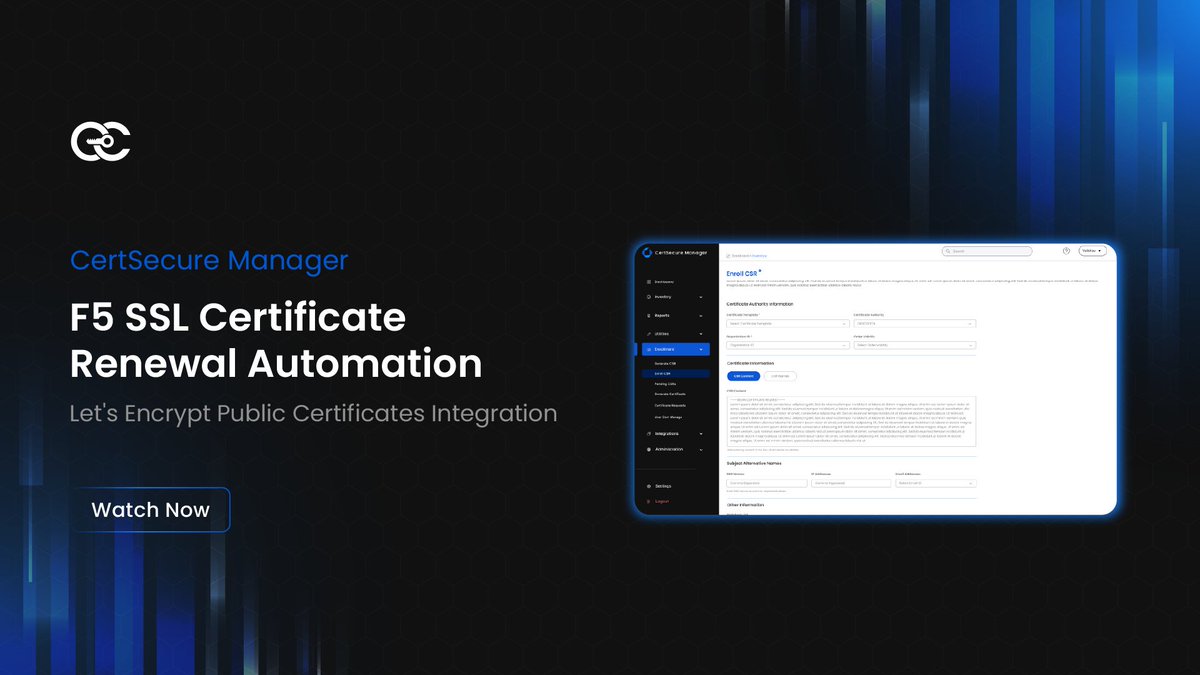
Learn how to simplify SSL/TLS certificate management through a seamless integration process. This video introduces the end-to-end workflow of certificate automation using our platform. It walks you through generating certificates with Let’s Encrypt in the enrollment section.…
In the Barney Stinson spirit, there’s only one rule when facing quantum threats: always “Suit up” and prepare for what’s next. When hackers threaten to use quantum-powered attacks to steal sensitive data, traditional cybersecurity just isn’t enough. That’s where post-quantum…

As organizations brace for the quantum era, understanding and managing cryptography has never been more critical. A Cryptography Bill of Materials (CBOM) offers the visibility needed to secure every algorithm, key, and certificate across your digital ecosystem. This blog unfolds…

Home of the free because of the brave. Forever thankful for the heroes who stood for our freedom. #VeteransDay

As we enter 2025, organizations can’t afford to ignore the risk of quantum attacks. Traditional encryption may soon be breakable, and the “harvest now, decrypt later” threat means data stolen today could be exposed tomorrow. A post-quantum cryptography assessment helps identify…

The global transition to post-quantum cryptography is taking shape through structured national roadmaps that define how nations are securing their digital future. This video breaks down the official PQC strategies from the European Union, Canada, and the UK, detailing their…

In every Public Key Infrastructure (PKI), trust is defined and enforced through two foundational documents: the Certificate Policy (CP) and the Certification Practice Statement (CPS). These documents govern how certificates are issued, managed, and trusted across digital…

That moment when the auditor gives you the green light...pure bliss! We know how much effort it takes to get to that moment. That’s why our Compliance Advisory Services are designed to make your journey smoother, stress-free, and fully compliant. From gap analysis and strategy…

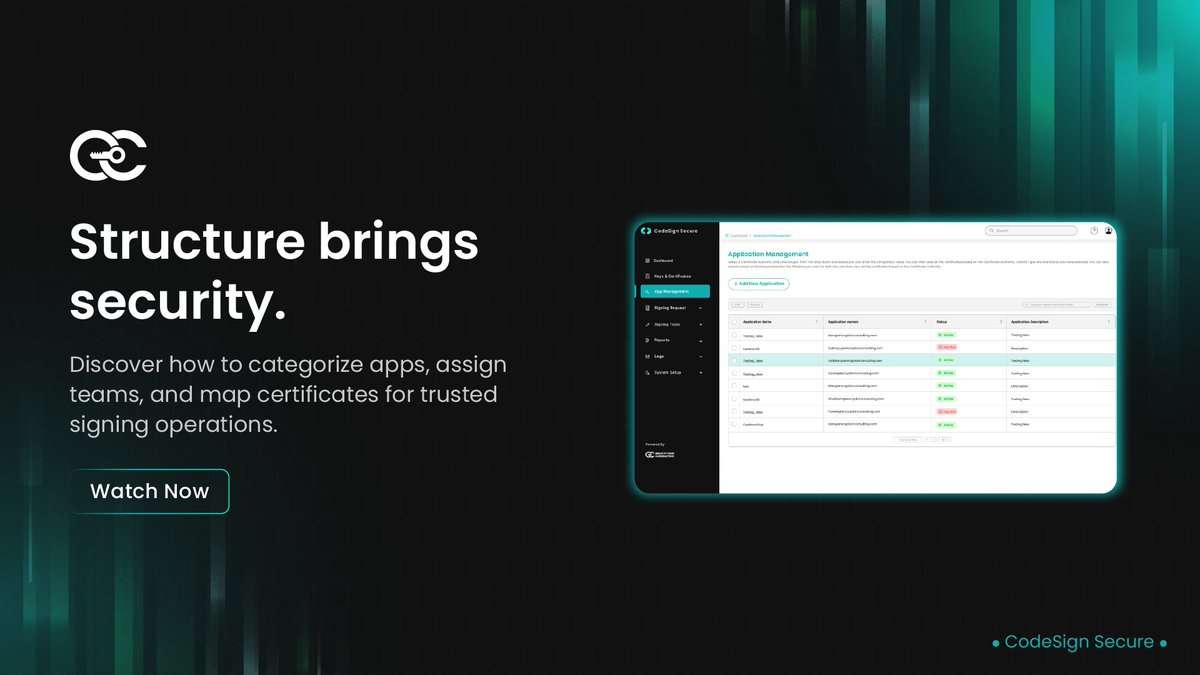
Take full control of your code signing workflow with the Application Management module in CodeSign Secure, purpose-built to simplify, organize, and secure every step of your signing process. In this video, you’ll see how to: 🔒 Create and categorize new applications for signing…
Managing public CA certificates shouldn’t be a manual, error-prone process. With the new GlobalSign–CertSecure Manager v3.1 integration, enterprises can now: 🔒 Automate certificate issuance and renewal 🔒 Centralize visibility across public and private CAs 🔒 Reduce outages and…

Managing code signing certificates can often feel complex, but it doesn’t have to be. In this video, we walk you through the Keys and Certificates tab of CodeSign Secure, showcasing how to effortlessly create, import, and organize certificates. You’ll learn how to configure…

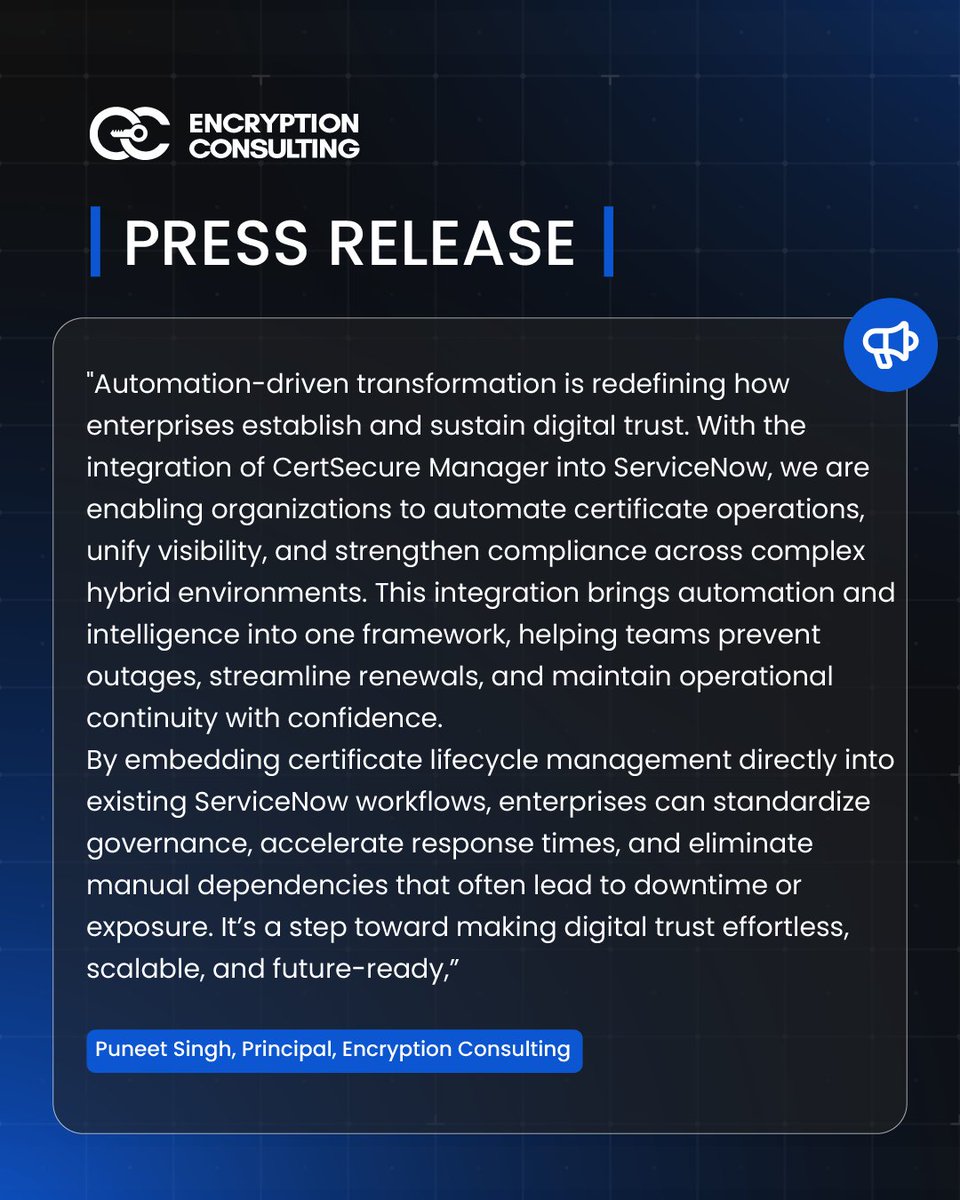
We are thrilled to announce the integration of Encryption Consulting's CertSecure Manager with ServiceNow, redefining how enterprises manage digital trust. This integration unifies automation, visibility, and compliance into a single, seamless workflow, empowering organizations…
United States 趨勢
- 1. Good Thursday 21.1K posts
- 2. Nnamdi Kanu 46.2K posts
- 3. Knicks 13.8K posts
- 4. But Jesus 21.4K posts
- 5. #GirlPower N/A
- 6. Shamet 3,034 posts
- 7. FEMA 72.5K posts
- 8. Sam Harris 3,516 posts
- 9. FREE HAT 1,719 posts
- 10. NO CAP 14.9K posts
- 11. #Survivor49 4,001 posts
- 12. Lute 87.1K posts
- 13. Derik Queen 4,792 posts
- 14. LANDRY 2,925 posts
- 15. Fulani 76.8K posts
- 16. Pink Floyd 2,757 posts
- 17. #LAShortnSweet 4,029 posts
- 18. Nany 2,046 posts
- 19. #CMAawards 5,644 posts
- 20. Crockett 54.6K posts
你可能會喜歡
-
 forex strategy factory
forex strategy factory
@jamesboy56 -
 Searchability
Searchability
@SearchabilityUK -
 PKI Solutions
PKI Solutions
@PKISolutions -
 Providence Mutual
Providence Mutual
@provmutual -
 Kenneth van Surksum - MVP
Kenneth van Surksum - MVP
@kennethvs -
 Kismile Official
Kismile Official
@kismileglobal -
 Agile IT
Agile IT
@Agile_IT -
 Futurex
Futurex
@Futurex -
 FoodMaven
FoodMaven
@foodmavenco -
 PNC News
PNC News
@PNCNews -
 SearchBlox
SearchBlox
@searchblox -
 David Benjamin
David Benjamin
@complexitydb
Something went wrong.
Something went wrong.












































































































