
Encryption Consulting LLC
@encryptioncons
We offer Code Signing and Certificate Lifecycle Management products along with PKI, HSM, and Other Encryption platform Consulting, Support, and Training.
You might like
Every CISO has seen some scary things… but nothing compares to the horror of discovering that certificates are still being tracked in an Excel sheet. This means manual issuance, missed renewals. unmonitored expirations and hidden risks everywhere. CertSecure Manager eliminates…

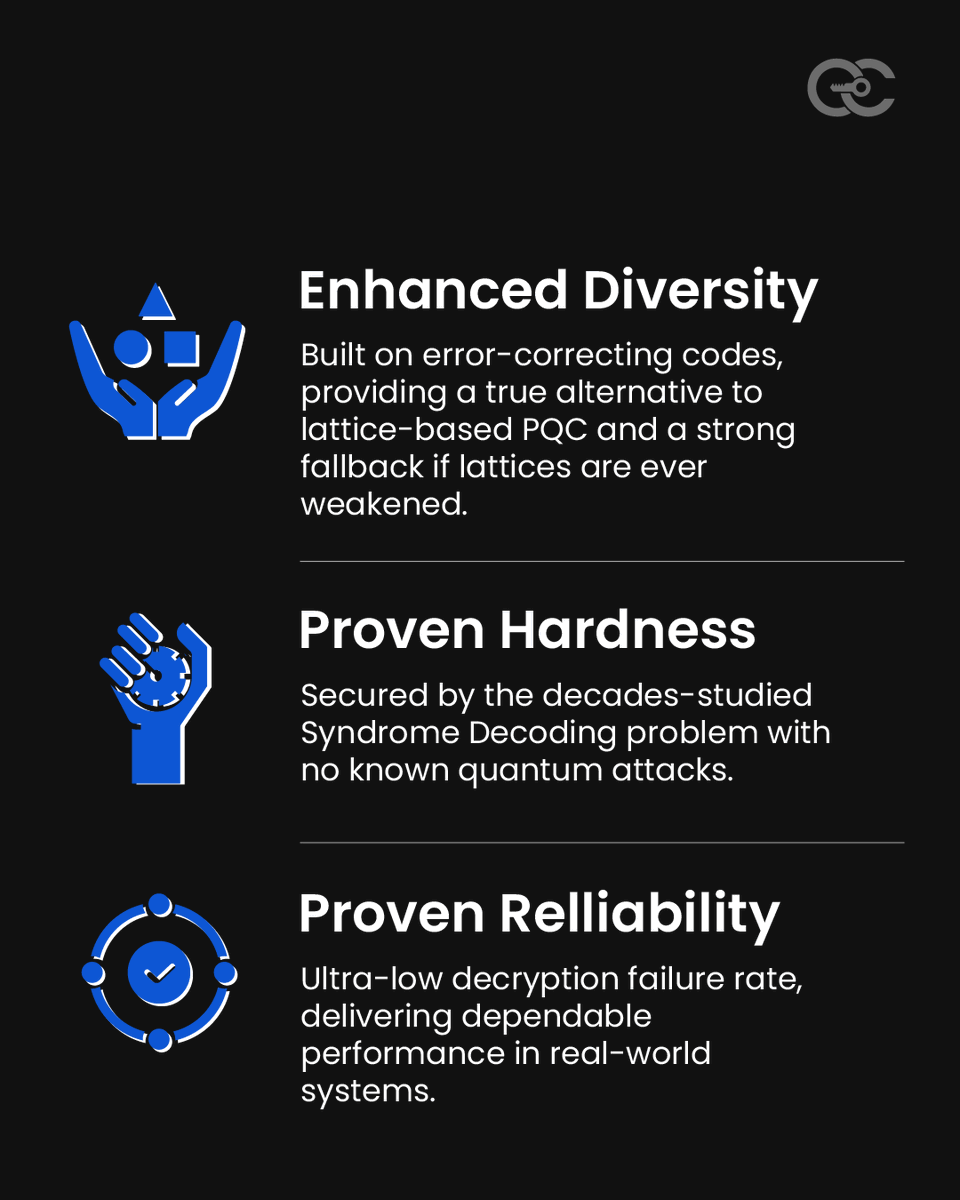
Strengthen your security with confidence. 🔐 As quantum computing accelerates, cryptographic resilience is essential. This post breaks down why HQC stands out as a powerful, reliable, and diverse post-quantum option for organizations preparing for Q-Day. From enhanced…


Happy Thanksgiving from the entire team at Encryption Consulting LLC! 🦃✨ We're all putting our laptops aside today to pause and say thank you. We are truly grateful for the trust you put in us every day to help secure your digital world. To our clients, partners, and…

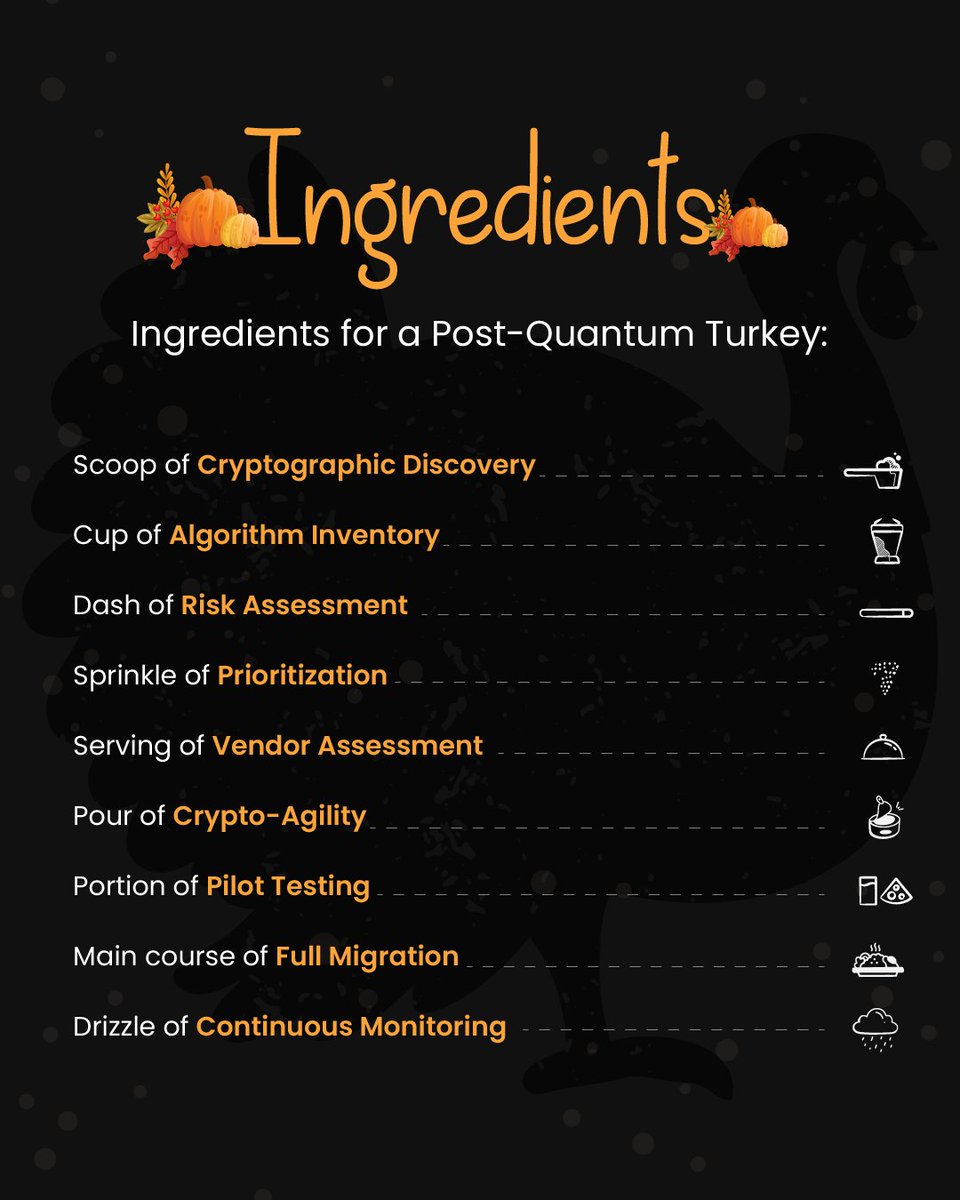
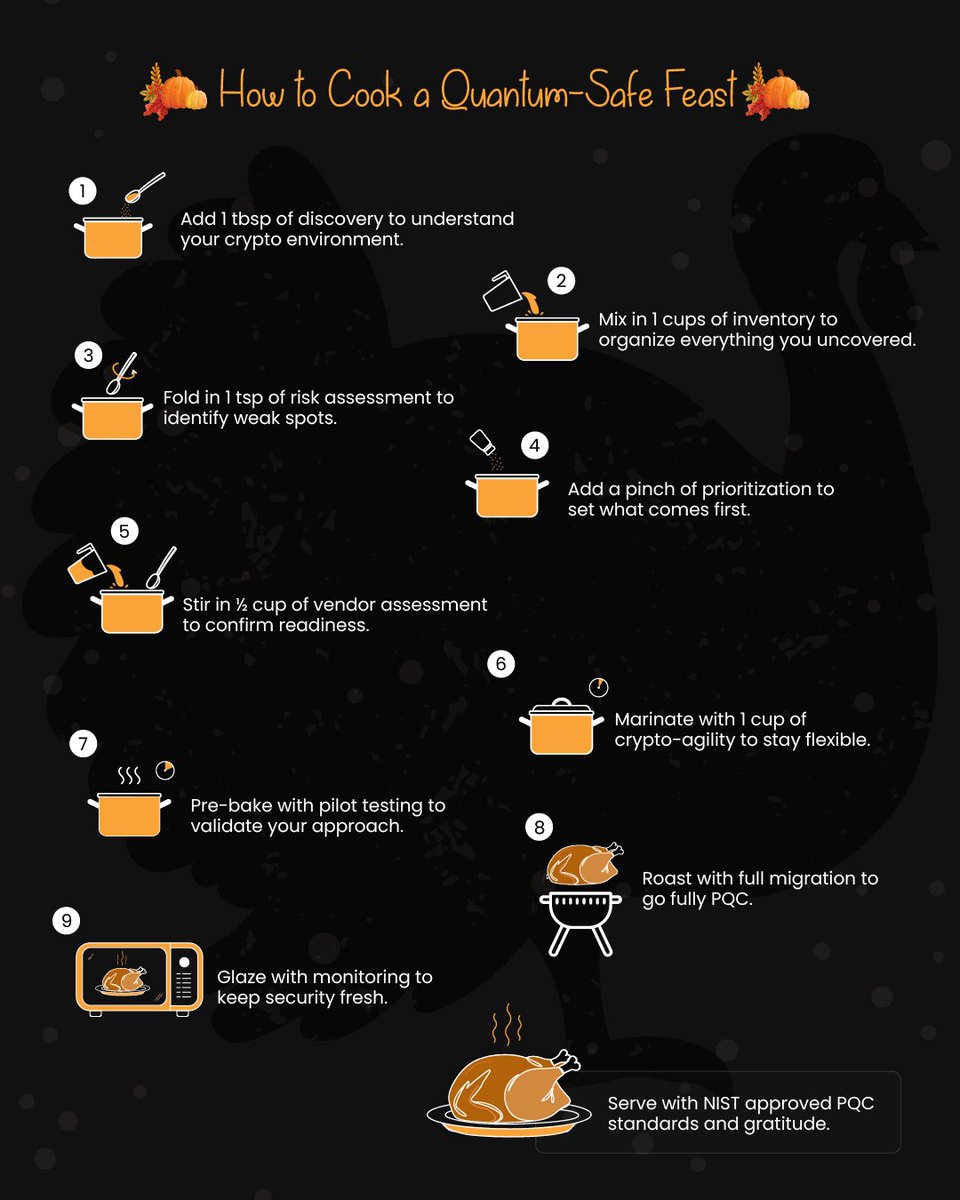
Happy Thanksgiving from Encryption Consulting! 🦃 As you gather for your holiday feast, we are serving up a special main course for your security strategy: The Post-Quantum Turkey. This is your perfect Thanksgiving recipe for a quantum-resistant future. To prepare a truly…

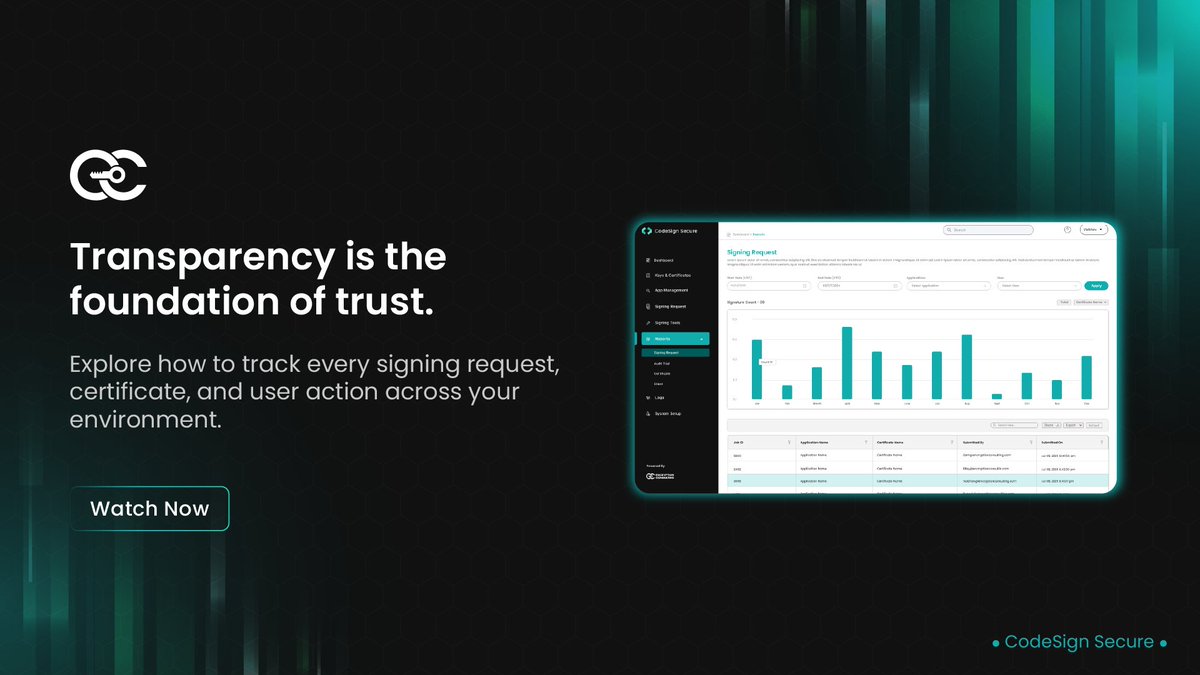
This video walks through the Reports section of CodeSign Secure, showcasing how organizations can view, filter, and export detailed reports of all code signing activities. It explains how the Signing Requests, Audit Trail, Certificates, and Clients tabs work together to provide a…
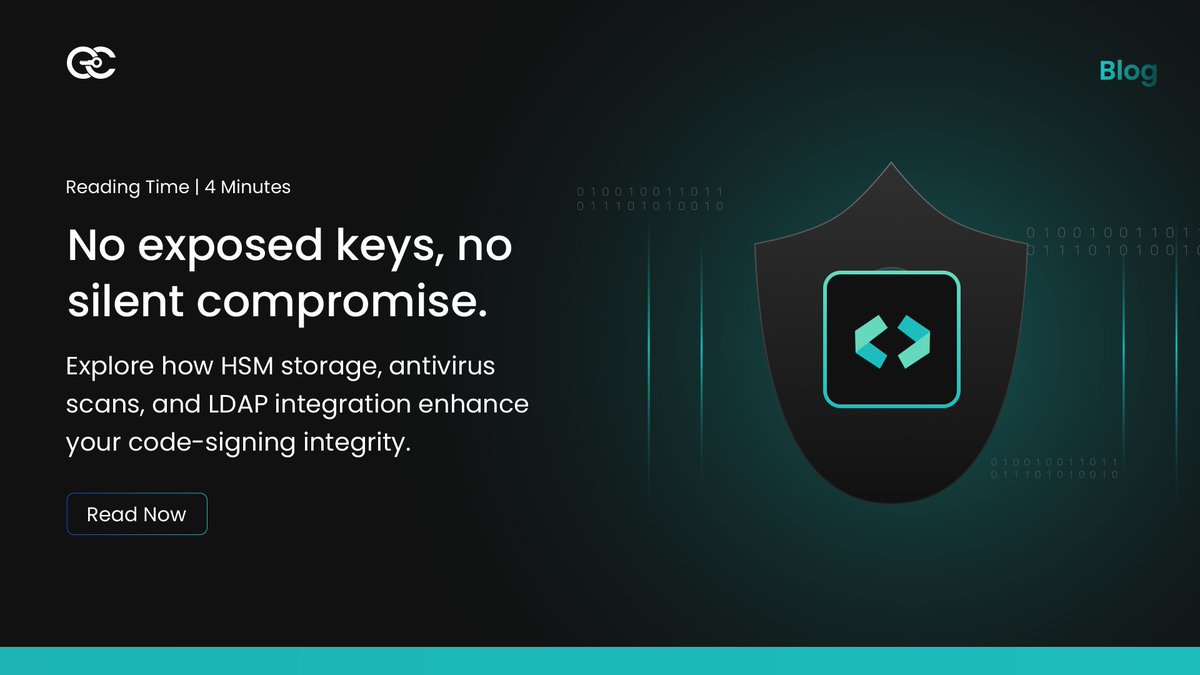
Code signing ensures software remains authentic, verified, and free from tampering. It protects executables, scripts, libraries, containers, and every component in the delivery chain. This blog explains how CodeSign Secure safeguards private keys using HSM storage while…
HQC serves as a resilient foundation for post-quantum security, engineered to withstand future cryptanalytic advancements. Rapid receiver-side operations reinforce throughput at scale, accelerating key generation and decryption handling. Patent-free implementation enables…



The Cyber Resilience Act establishes a unified regulatory baseline to ensure software, firmware and connected devices remain secure, trusted and tamper-proof across their lifecycle. It enforces strong cryptographic controls, authenticated updates and auditable signing practices…

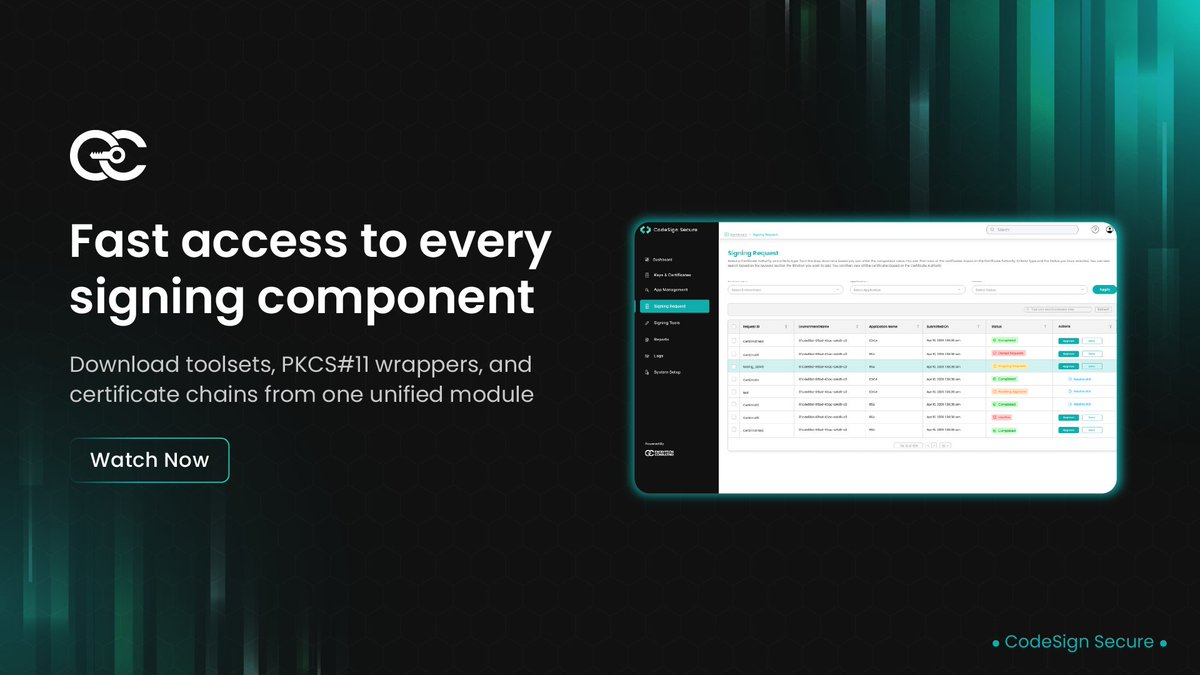
Code signing operations rely on purpose-built tools that streamline credential handling and enforce governance across diverse build environments. These tools form the operational backbone for secure, policy-aligned software release workflows. This video provides a walkthrough of…
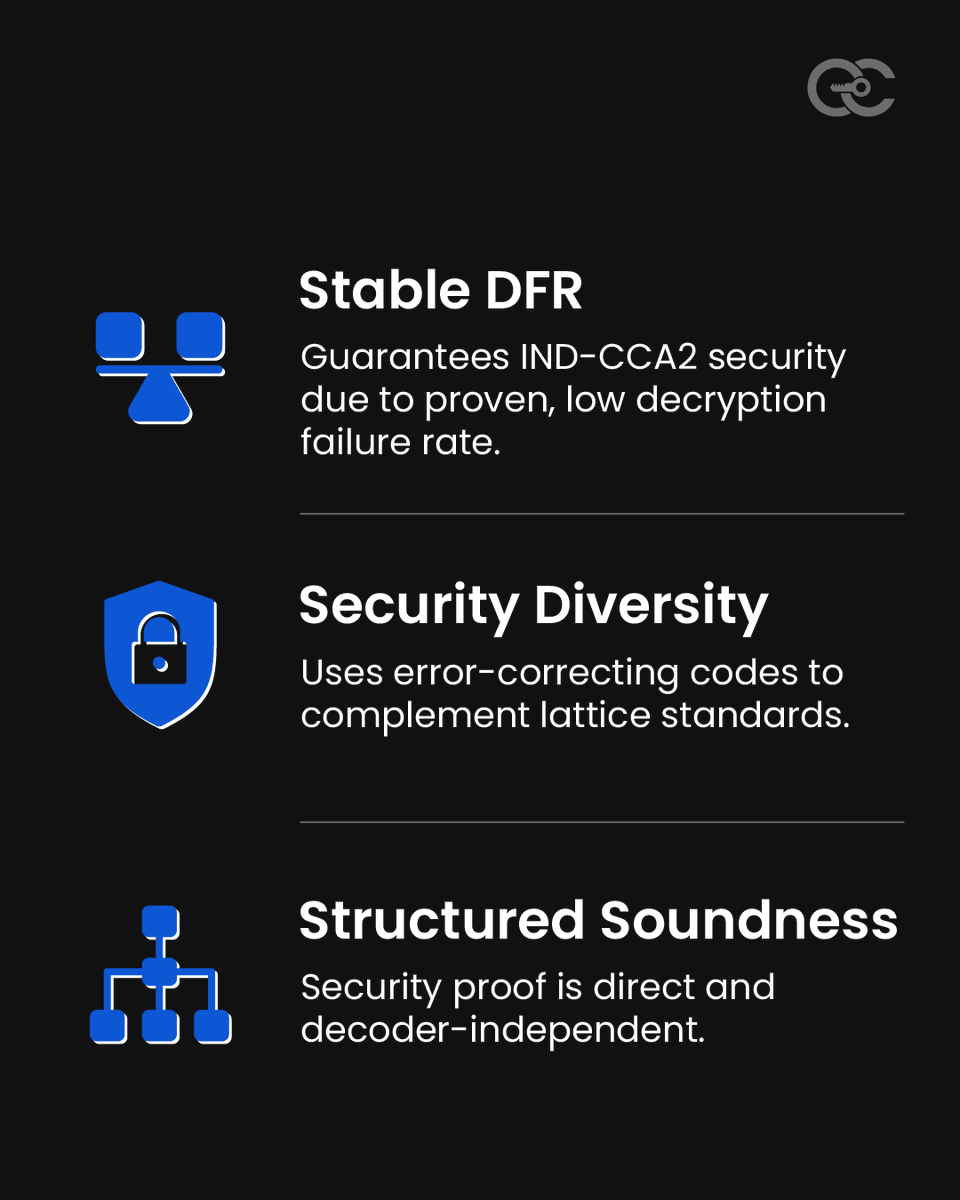
HQC brings a balanced blend of reliability and resilience, backed by stable DFR, strong error-correcting foundations, and clear security proofs. Its core elements make it a dependable building block as organizations explore next-generation cryptographic options. Across the PQC…


With NIST’s post-quantum algorithms officially selected, organizations must begin planning for the deprecation of today’s RSA and ECC standards. This video walks you through what PQC migration really means, covering impacted systems, how to assess your cryptographic assets, and…

Say goodbye to certificate downtime, automate it! Discover how Encryption Consulting’s CertSecure Manager makes SSL/TLS renewals effortless for NGINX. With the NGINX Renewal Agent, you can seamlessly renew and redeploy certificates. No more manual toil, no more risk of…

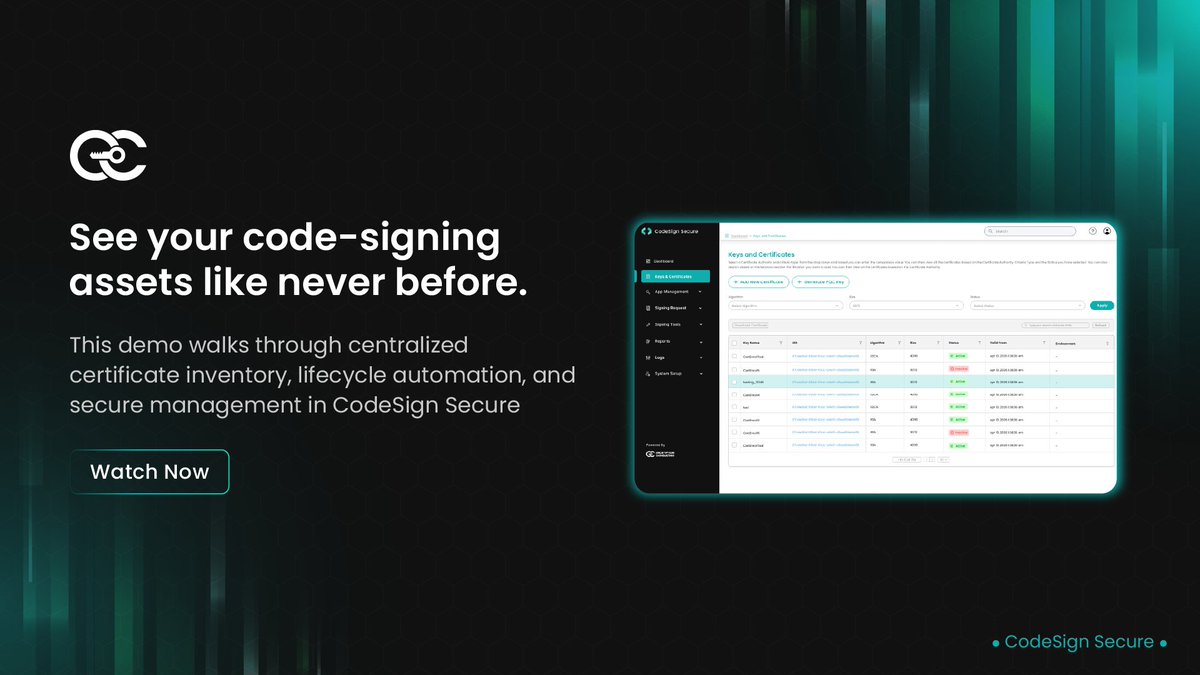
Managing code signing certificates can often feel complex, but it doesn’t have to be. In this video, we walk you through the Keys and Certificates tab of CodeSign Secure, showcasing how to effortlessly create, import, and organize certificates. You’ll learn how to configure…
Cryptographic inventory management is emerging as a mission-critical discipline as organizations confront growing operational, compliance, and quantum-era risks. This blog provides a structured view of why systematic discovery, auditing, and lifecycle oversight of cryptographic…

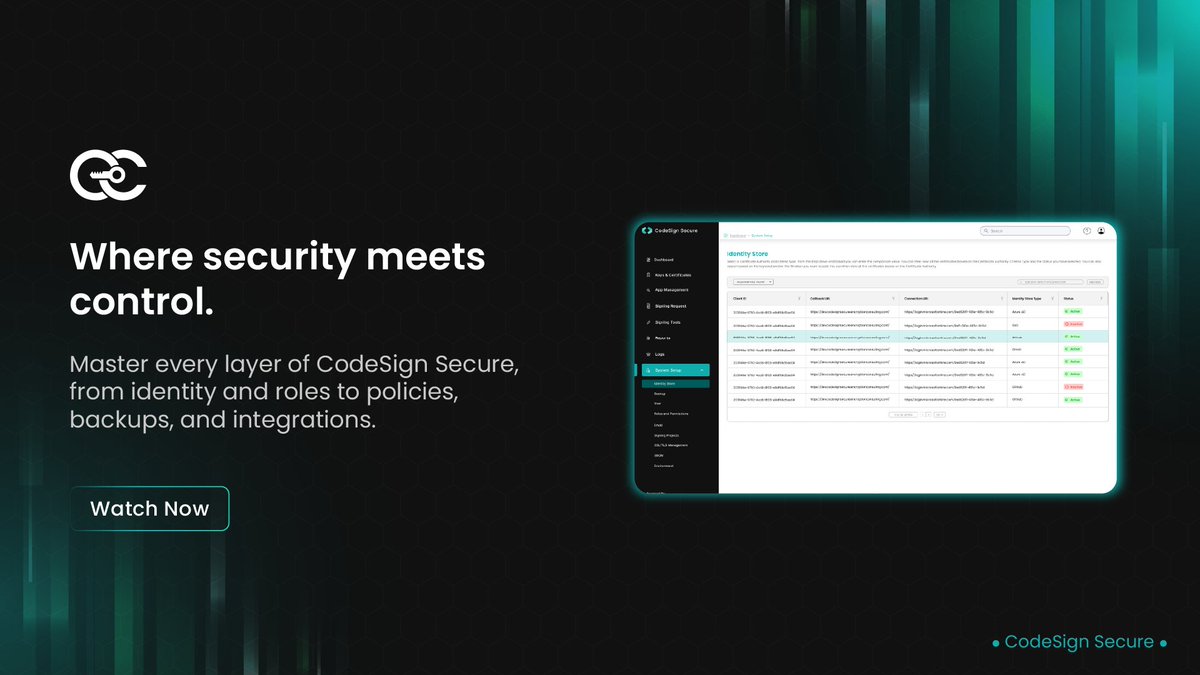
In a secure code signing environment, precise configuration and access control are non-negotiable. Our walkthrough explores how these essentials come together in CodeSign Secure. It covers identity store setup, user management, and role-based permissions in action. You’ll also…
The PQC Readiness Assessment serves as the definitive, critical strategy for organizations to proactively defend against the imminent threat of quantum computers breaking current encryption. This blog fluently the necessary steps, walking through the entire process: discovering…
Cryptographic discovery is the starting point for any serious PQC journey, giving organizations a clear understanding of where their cryptography lives and how prepared they truly are for the quantum shift. This video unpacks that foundation in a relatable, easy-to-follow way…
In every Public Key Infrastructure (PKI), trust is defined and enforced through two foundational documents: the Certificate Policy (CP) and the Certification Practice Statement (CPS). These documents govern how certificates are issued, managed, and trusted across digital…

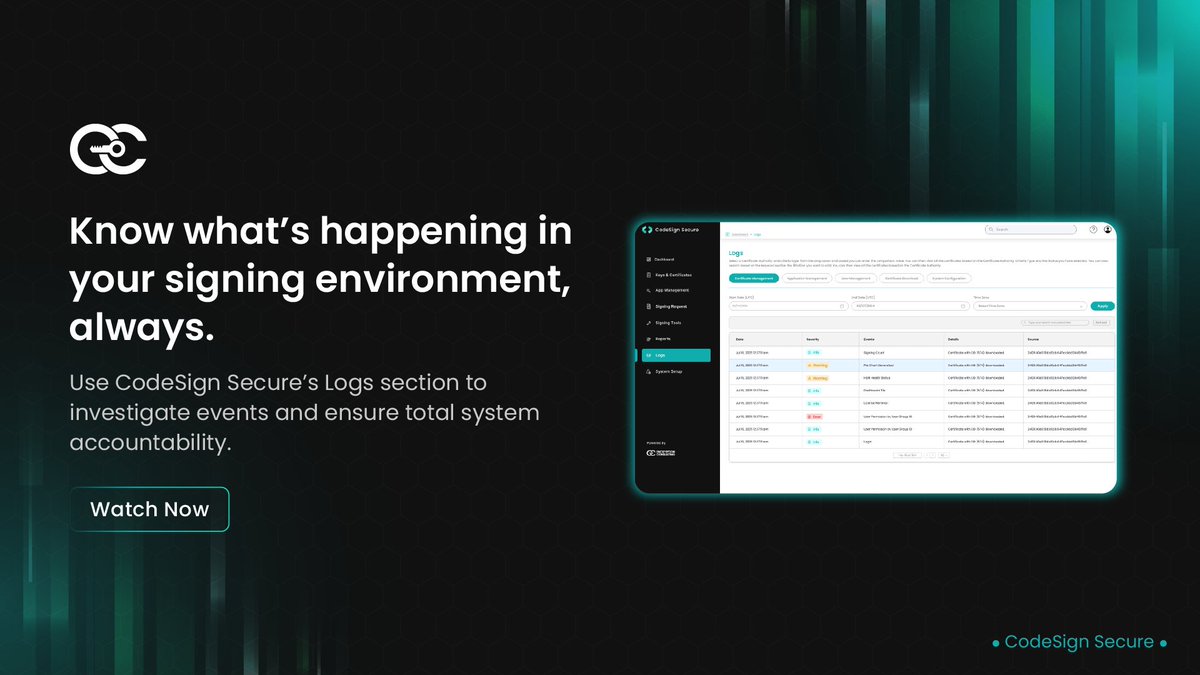
This video provides a concise overview of CodeSecure’s log management interface. It outlines how operational events are captured and structured for analysis. The walkthrough demonstrates how JSON-formatted logs enhance SIEM performance. It also highlights export options and…
CertSecure Manager’s integration with Azure Key Vault elevates cloud-ready certificate management for modern enterprises. The blog outlines how automated uploads, centralized controls, and secure workflows optimize PKI operations. It also breaks down admin prerequisites,…

United States Trends
- 1. Texas 134K posts
- 2. Arch Manning 5,501 posts
- 3. Marcel Reed 3,805 posts
- 4. Aggies 7,521 posts
- 5. Sark 3,673 posts
- 6. Jeff Sims 1,002 posts
- 7. 3-8 Florida N/A
- 8. Georgia 46.2K posts
- 9. SEC Championship 3,923 posts
- 10. #iufb 3,137 posts
- 11. #OPLive 2,256 posts
- 12. #SmackDown 15.5K posts
- 13. Devin Vassell N/A
- 14. #BedBathandBeyondisBack 1,607 posts
- 15. Eagles 144K posts
- 16. Elko 1,807 posts
- 17. Lindor 2,221 posts
- 18. Purdue 6,371 posts
- 19. Bears 131K posts
- 20. #PorVida N/A
You might like
-
 forex strategy factory
forex strategy factory
@jamesboy56 -
 Searchability
Searchability
@SearchabilityUK -
 PKI Solutions
PKI Solutions
@PKISolutions -
 Providence Mutual
Providence Mutual
@provmutual -
 Kenneth van Surksum - MVP
Kenneth van Surksum - MVP
@kennethvs -
 Kismile Official
Kismile Official
@kismileglobal -
 Agile IT
Agile IT
@Agile_IT -
 Futurex
Futurex
@Futurex -
 FoodMaven
FoodMaven
@foodmavenco -
 PNC News
PNC News
@PNCNews -
 SearchBlox
SearchBlox
@searchblox -
 David Benjamin
David Benjamin
@complexitydb
Something went wrong.
Something went wrong.











































































































