Al-hassan abbas | الحسن عباس
@exploit_msf
Certifed : #Ecptxv2 #Oscp #Ecpptv2 #Ceh11 #Ejpt #ECES #Metasploit_pro_specialist #Ewpt #Ceh_master Snap & instagram : exploit.msf CVE-2021-40303
你可能會喜歡
I earned $200 for my submission on @bugcrowd bugcrowd.com/alhasan_abbas #ItTakesACrowd #bugbountytips Tip: CVE-2022-46463 Download repo's in harbor
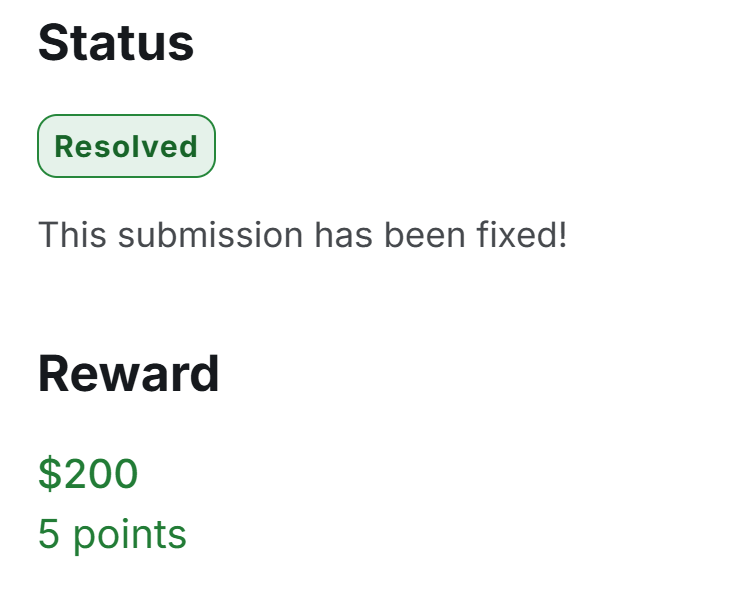
I was awarded a $3,100 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder

Just scored a reward 1875€ @intigriti #HackWithIntigriti #bugbountytips Tip: I played ctf this year and i found this vulnerability because i solve machine challenge with same bug If you found apache airflow use flask-unsign to found secret key and generate new jwt for admin

I was awarded a $290 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: CVE-2025-29927 via /admin

I was awarded a $450 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder

3 Simple rewards in last week Tips: 1- Django debug /anypath 2- CVE-2019-11248 /debug/pprof/ 3- Spring heapdump disclosure /heapdump

I was awarded a $350 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder Tip: CVE-2025-0133 RXSS

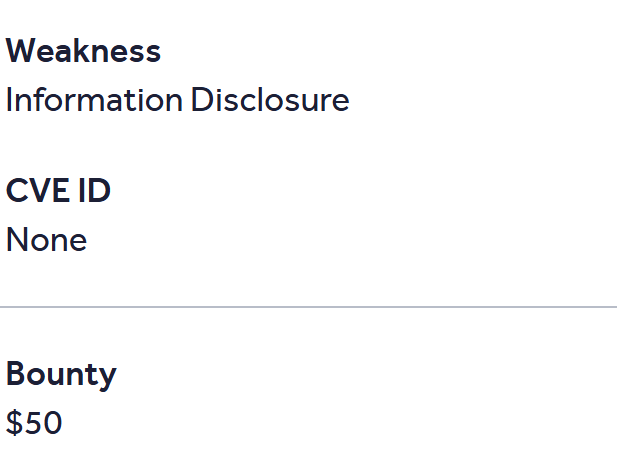
Just got a reward for a vulnerability submitted on @yeswehack -- Information Disclosure (CWE-200). yeswehack.com/hunters/exploi… #YesWeRHackers #bugbountytips Tip: Read senesitive data for aem cloud in /.json

Yay, I was awarded a $250 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: Stored xss via cache in header (X-Forwarded-For)

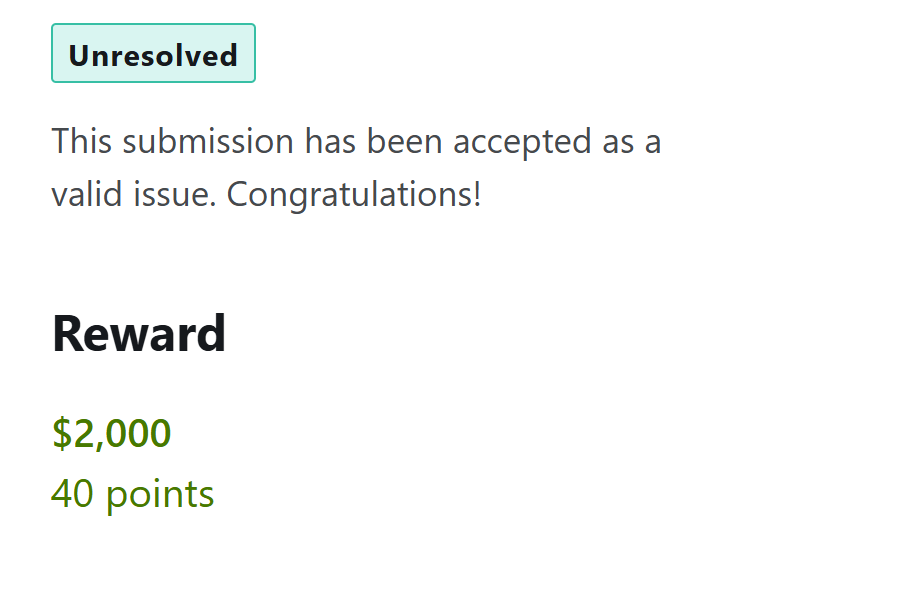
I earned $2,000 for my submission on @bugcrowd bugcrowd.com/alhasan_abbas #ItTakesACrowd Tip: ATO using strings tool to read tokens in /headpdump spring file (strings heapdump | grep -i bearer)
I was awarded a $500 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: Wordpress config /old/wp-config.php.bak

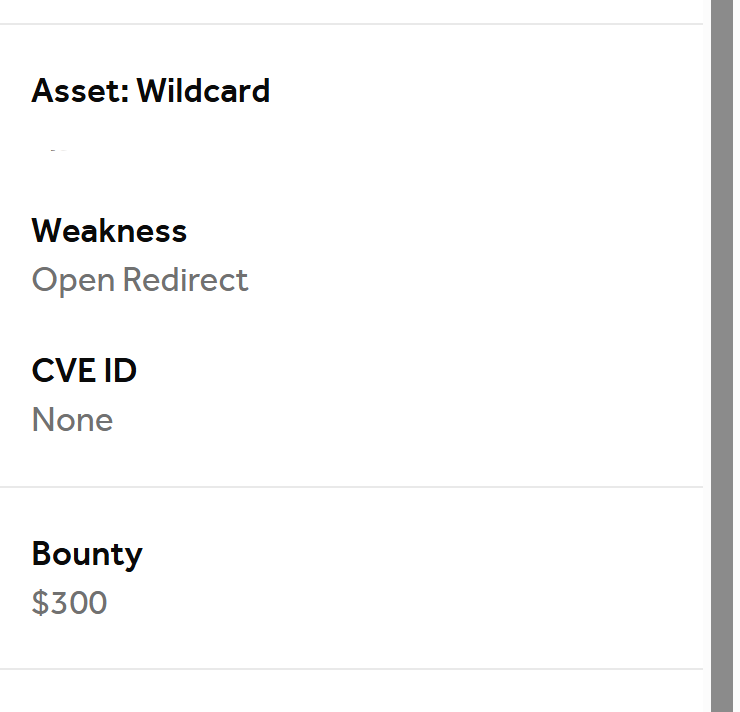
I was awarded a $300 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: Open redirect ///evil.com
I was awarded a $600 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder

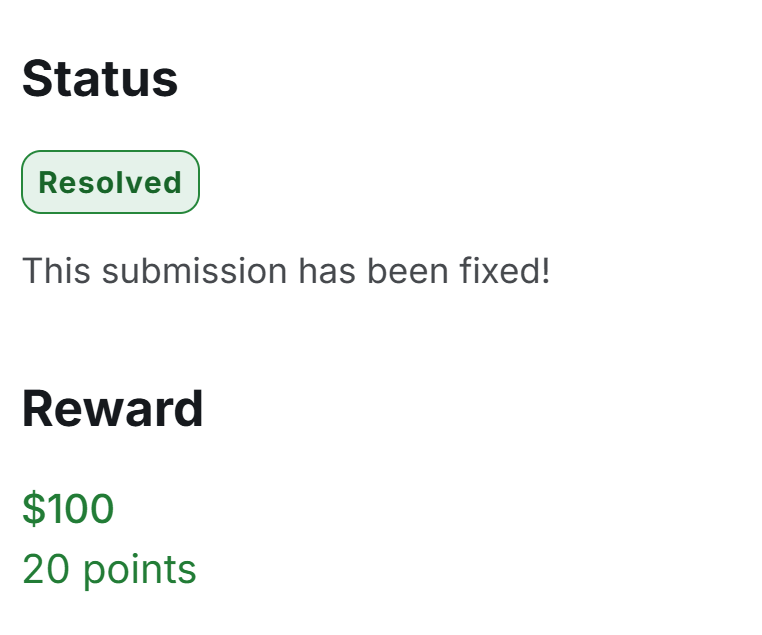
I was awarded a $100 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytip php opcache information disclosure: /opcache/index.php

I was awarded a $750 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: I found 0day in cloud app lead to read credential for wordpress database for any domain hosted on this cloud example.com/test/ >> 404 example.com/test/env.json >> 200

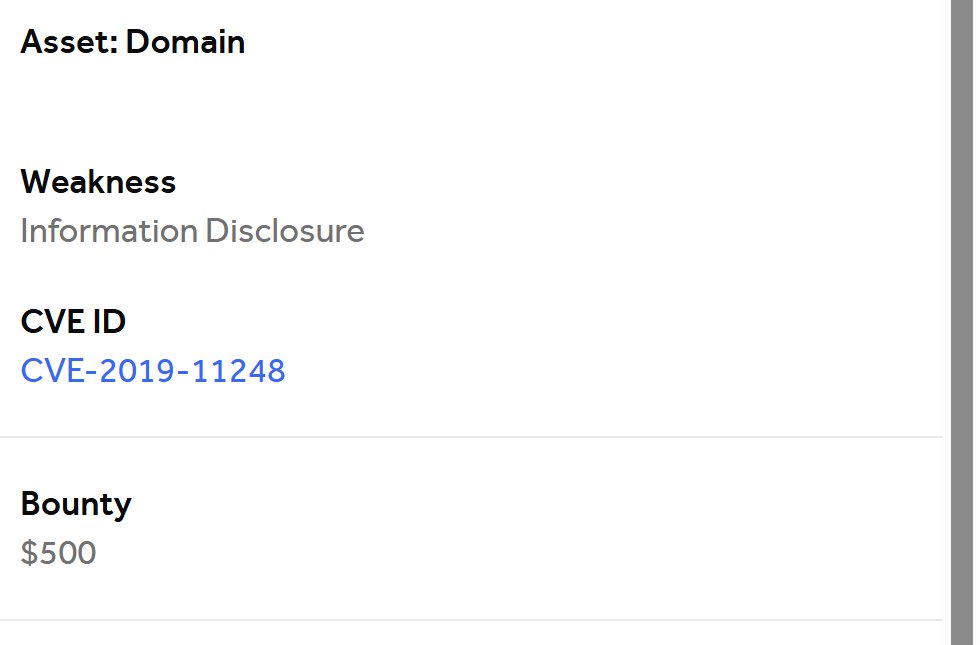
I was awarded a $500 bounty on @Hacker0x01! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: CVE-2019-11248
I was awarded a $125 and bounty and $75 retest on HackerOne hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: Check php laravel bar in all paths


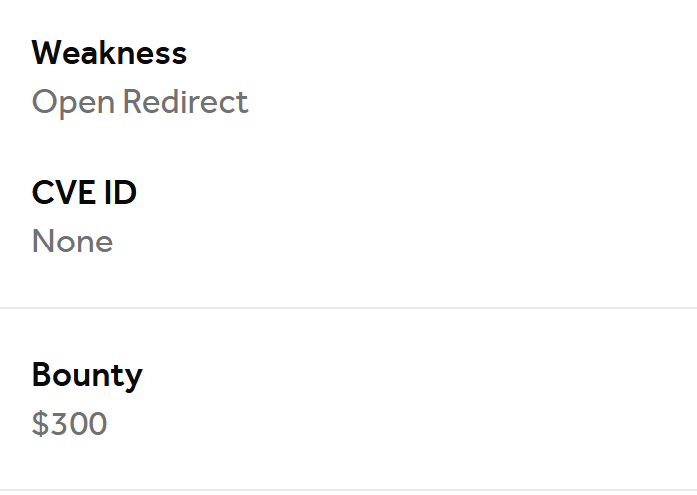
I was awarded a $300 bounty on @Hacker0x01 ! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: Open redirect (test.com///evil.com)
I was awarded a $50 bounty on @Hacker0x01 ! hackerone.com/exploitmsf #TogetherWeHitHarder #bugbountytips Tip: RXSS base64 (PHNjcmlwdD5hbGVydChkb2N1bWVudC5kb21haW4pPC9zY3JpcHQ+)

I earned $150 for my submission on @bugcrowd bugcrowd.com/alhasan_abbas #ItTakesACrowd #bugbountytips Tip: RXSS > ; alert(1);

United States 趨勢
- 1. Chiefs 113K posts
- 2. Harada 6,131 posts
- 3. Mahomes 41.2K posts
- 4. Kelce 25.3K posts
- 5. #ITWelcomeToDerry 71.5K posts
- 6. Texans 49K posts
- 7. Tekken 15K posts
- 8. ORM HAUS NOWHERE GOP 34.9K posts
- 9. #OrmxHausNowhereBKK 35.2K posts
- 10. Good Monday 32.2K posts
- 11. rUSD N/A
- 12. Andy Reid 7,035 posts
- 13. #BaddiesUSA 33.1K posts
- 14. #MondayMotivation 5,792 posts
- 15. #Ormkornnaphat 71.6K posts
- 16. Proverbs 4,760 posts
- 17. Rashee Rice 10.6K posts
- 18. Pennywise 35.8K posts
- 19. doyoung 277K posts
- 20. Stroud 10.8K posts
你可能會喜歡
-
 0xRAYAN 🇸🇦
0xRAYAN 🇸🇦
@0xRAYAN7 -
 Sourav Khan🇧🇩 🇵🇸
Sourav Khan🇧🇩 🇵🇸
@Br0k3n_1337 -
 Abdelrhman Allam 🇵🇸
Abdelrhman Allam 🇵🇸
@sl4x0 -
 Fares
Fares
@_2os5 -
 Rahmat Qurishi
Rahmat Qurishi
@RahmatQurishi -
 Imamul Mursalin
Imamul Mursalin
@d3f7ult -
 Hammad 🇵🇰🇵🇸
Hammad 🇵🇰🇵🇸
@Hammad7361 -
 Lu3ky13 ⚡️⚡️
Lu3ky13 ⚡️⚡️
@lu3ky13 -
 🇸🇦 Murtada Bin Abdullah (Rood)
🇸🇦 Murtada Bin Abdullah (Rood)
@0x_rood -
 /usr/bin/fares
/usr/bin/fares
@SirBagoza -
 Mohamed Elkhayat
Mohamed Elkhayat
@Mohamed87Khayat -
 Nihad
Nihad
@nihad_rekany -
 Naeem Ahmed Sayed 🇧🇩
Naeem Ahmed Sayed 🇧🇩
@0xNaeem -
 Abdulrahman Makki | عبدالرحمن مكي
Abdulrahman Makki | عبدالرحمن مكي
@AMakki1337 -
 Alsanosi
Alsanosi
@01alsanosi
Something went wrong.
Something went wrong.