FuzzingLabs
@FuzzingLabs
Research-oriented Cybersecurity startup specializing in #fuzzing, Vulnerability Research & Offensive security on Mobile, Browser, AI/LLM, Network & Blockchain.
You might like
💥 We’ve just raised €1M in pre-seed funding to accelerate the development of FuzzForge. When I started FuzzingLabs, everything was bootstrapped: our audits, our trainings, our R&D. No investors, no funding. Just a passionate team obsessed with offensive security and the…

Preparing my slides for my BSides Berlin 2025 keynote, and I thought we could play a little game ;) Let’s call it “The AI #AppSec Keyword Games” Your mission: - Match each AppSec company to its AI-powered marketing tagline. This slide is part of my section “From Automation to…

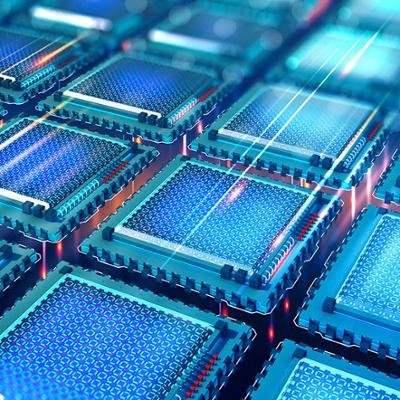
LLMs are beating regex in secret detection. We benchmarked Gitleaks, TruffleHog, and two LLMs on real-world codebases. GPT-5-mini hits 84.4% recall vs Gitleaks at 37.5% vs TruffleHog at 0.0% LLMs catch: – Split secrets – Obfuscated tokens – Decoded vars – Even commented-out…
One of the last steps prior to launching ZK Arcade on mainnet was a code audit by @FuzzingLabs. You can see the full results of the audit here: github.com/yetanotherco/z…
We are back at #Pwn2Own !! Excited to be part again at the most famous offensive competition in the world organized by @thezdi ;) Good luck everyone but especially for our team :p

The schedule for #Pwn2Own Ireland is now live! 53 entries from 25 teams over three days of excitement and pwnage. We'll be updating the schedule with live streaming information as we get them set up. zerodayinitiative.com/blog/2025/20/p… #P2OIreland
Thanks for updating attribution, that’s a necessary step. One remaining factual point must be clear for the public record: your post still states that PoCs were not copied verbatim. That is incorrect. Below is concrete evidence: the Ollama PoC we published intentionally…


Disappointed to see public accusations without reaching out first, especially after launching a competitive product. We work directly with maintainers via GitHub, not bounty platforms. Neither we nor the maintainers knew about your Huntr reports at the time, otherwise they would…
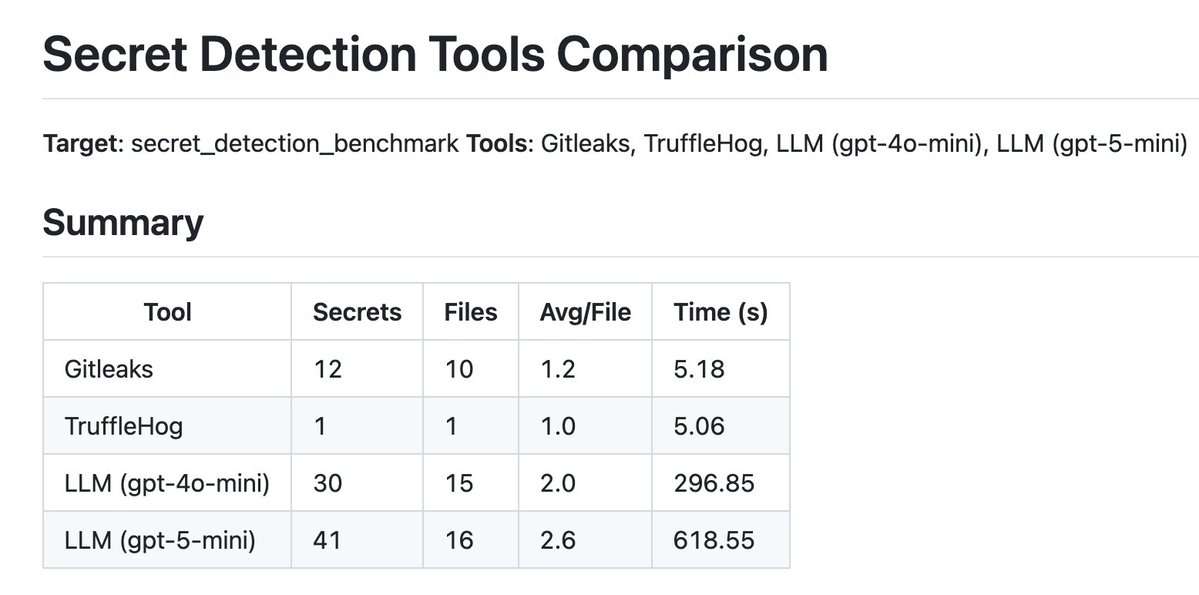
💣 We caught @ycombinator–backed @gecko_sec stealing two of our CVEs, one on @ollama , one on @Gradio. They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts. Here’s the full story 👇
#BSidesBerlin Speaker Showcase @pat_ventuzelo will deliver our closing keynote: how AI is shifting from automation to autonomy in AppSec & offensive security, envisioning AI-driven red teams. Get your tickets here 👉bsides.berlin @SecurityBSides #AI #RedTeam

Hi, does anyone here have a contact at @ycombinator? cc @paulg Quick context: @FuzzingLabs developed an open-source, AI-driven fuzzing tool that discovered a number of significant vulnerabilities which we disclosed publicly. A competing team backed by YC, @gecko_sec, has since…

💣 We caught @ycombinator–backed @gecko_sec stealing two of our CVEs, one on @ollama , one on @Gradio. They copied our PoCs, claimed CVE IDs, and even back-dated their blog posts. Here’s the full story 👇

Our friends and partners of @piku_dao @sinankoc__ created a yieldcoin returning above 15% by investing in arbitrage strategies, carry trades, on-chain yield, and RWAs. It simplifies the access to complex strategies. I highly recommend you check what they are doing. With Lambda…
The primary goal of PikuDAO is to create a stablecoin that maintains its purchasing power that also generates yield for its holders. This is achieved through a backing model that includes arbitrage strategies, carry trades, on-chain yield, and RWAs. The goal is to hedge against…
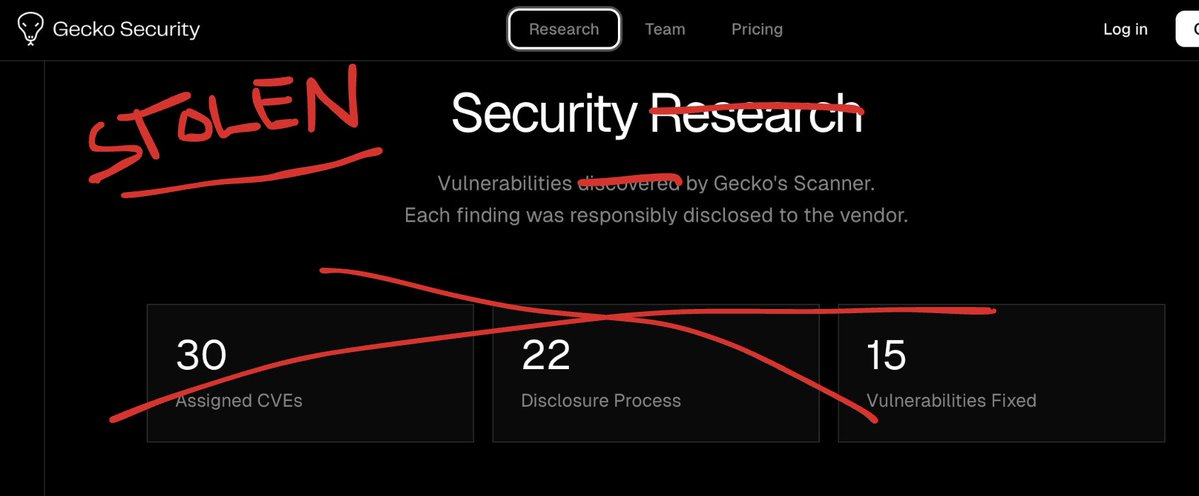
🚀 Big news from FuzzingLabs Academy We’re expanding our training lineup with a brand new format: Masterclasses 🎓 Short, ultra-focused sessions on cutting-edge security topics, perfect to boost your skills fast! 📅 Our Q4 2025 Course Lineup is live: - Fuzzing Windows…
United States Trends
- 1. $APDN $0.20 Applied DNA N/A
- 2. yeonjun 266K posts
- 3. #CARTMANCOIN 1,958 posts
- 4. $LMT $450.50 Lockheed F-35 N/A
- 5. $SENS $0.70 Senseonics CGM N/A
- 6. Broncos 67.9K posts
- 7. Raiders 67.2K posts
- 8. Bo Nix 18.7K posts
- 9. #iQIYIiJOYTH2026 1.27M posts
- 10. Geno 19.4K posts
- 11. daniela 55.8K posts
- 12. Kehlani 11.5K posts
- 13. #Pluribus 3,146 posts
- 14. Sean Payton 4,882 posts
- 15. #PowerForce 1,068 posts
- 16. #NOLABELS_PART01 114K posts
- 17. Danny Brown 3,328 posts
- 18. John Wayne 1,096 posts
- 19. Kenny Pickett 1,526 posts
- 20. Tammy Faye 1,675 posts
You might like
-
 reverseame
reverseame
@reverseame -
 seal
seal
@seal9055 -
 Linux Kernel Security
Linux Kernel Security
@linkersec -
 Patrick Ventuzelo
Patrick Ventuzelo
@Pat_Ventuzelo -
 Brandon Falk
Brandon Falk
@gamozolabs -
 starlabs
starlabs
@starlabs_sg -
 Orange Tsai 🍊
Orange Tsai 🍊
@orange_8361 -
 sakura
sakura
@eternalsakura13 -
 [email protected]
[email protected]
@0xdea -
 Interrupt Labs
Interrupt Labs
@InterruptLabs -
 Samuel Groß
Samuel Groß
@5aelo -
 pfiatde
pfiatde
@pfiatde -
 Alisa Esage Шевченко
Alisa Esage Шевченко
@alisaesage -
 Dohyun Lee
Dohyun Lee
@l33d0hyun -
 Pessimistic Security
Pessimistic Security
@pessimistic_io
Something went wrong.
Something went wrong.