
HackingHub
@hackinghub_io
Educating the next generation of ethical hackers.
You might like
Do you know about Nuclei Templates? You should get familiar with them. Learn the tool behind modern automation, reconnaissance, and high-impact vulnerability discovery. Check out our Nuclei Masterclass on HackingHub now👇 ✅app.hackinghub.io/course/nuclei-…
New video covering the solution to the Mother Printers challenge I created for @hackinghub_io 💜 Tried to make it as beginner friendly as possible as I know many players aren't familiar with rev/pwn 😇 youtu.be/ebNYtX_8lOY
youtube.com
YouTube
Mother Printers (Print2Own) - Full Exploit Chain Walkthrough [Hacki...
🚨THIS CYBER MONDAY Our bundles are 67% OFF. But here's the catch: This promo code is only valid for the first 100 uses OR until EODMonday – whichever comes FIRST! Get started: 💻The Hackers Arsenal: hhub.io/ARSENALCYBERMO… 🐞Bug Bounty Essentials: hhub.io/BBECYBERMONDAY…

🚨Turn on your notifications! Tomorrow, we've got a surprise for you. You won't want to miss it!
Many starting hackers quit when the first IDOR attempt fails. How do you keep hunting after the easy targets are gone? @NahamSec breaks down the full process you need to succeed.👇
The one thing you need to master Blind XSS? Assumptions. @nahamsec tells you why. Want to learn the fundamentals of Blind XSS and stop guessing? Grab our Black Friday sale here👇 hhub.io/blackfriday202…
🚨LAST CHANCE! Our Black Friday Sale officially ends tomorrow at Midnight PT! Don't let this incredible opportunity to build your hacking skills: 👤The Hackers Arsenal: hhub.io/2025blackfrida… 🐞Bug Bounty Essentials: hhub.io/blackfriday202…
Why is it a good practice to switch from simple XSS payloads (like alert() or confirm()) to a Blind XSS payload that includes a tracking mechanism? 🕵️♀️ (with @NahamSec) ✅Master Blind XSS: Get our Masterclass at Black Friday Prices! Limited time deal👇 hhub.io/2025blackfrida…
Our Black Friday Sale ends Friday, November 28th, at Midnight Pacific Time! Don't miss out on this opportunity. Start building your hacking skills now: 👤The Hackers Arsenal: hhub.io/2025blackfrida… 🐞Bug Bounty Essentials: hhub.io/blackfriday202…

Do you know the difference between the greedy and lazy quantifiers when using regular expressions (regex)? 🤔 Don't miss out on our Black Friday sale to master Regex👇 hhub.io/2025blackfrida…
One week left for our Black Friday Sale! Don't miss out on this opportunity Start building your hacking skills now ✅Get started: 👤The Hacker's Arsenal: hhub.io/2025blackfrida… Voucher: 2025blackfriday 🐞Bug Bounty Essentials: hhub.io/blackfriday202… Voucher: blackfriday2025

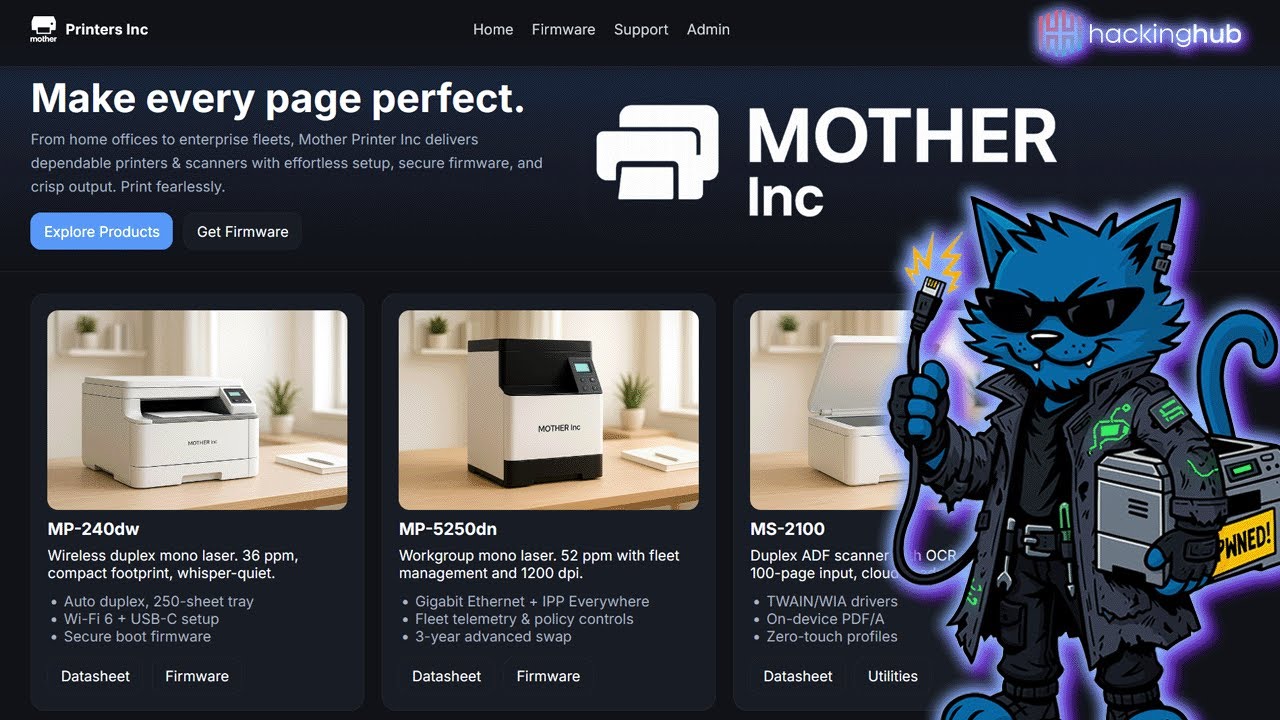
Got a free hour? ⏱️ Stop scrolling and start hacking. Challenges are fast-paced web hacking labs designed to sharpen your offensive skills in under an hour. Get started: app.hackinghub.io/hubs?type=chal…
Picture this: you're hacking on a target, stumble upon a RegEx and don't know what to do 🤔 If this sounds familiar, make sure to check out our RegEx for hackers course, to learn how to turn RegEx's into a powerful offensive tool 👇 app.hackinghub.io/course/regex-f…
This is your sign to master your hacking skills for 2026! 🚀 Our Black Friday Sale is LIVE with incredible deals. ✅Get started: 👤The Hacker's Arsenal: hhub.io/2025blackfrida… Voucher: 2025blackfriday 🐞Bug Bounty Essentials: hhub.io/blackfriday202… Voucher: blackfriday2025

United States Trends
- 1. Penn State 19.4K posts
- 2. Paul Dano 1,603 posts
- 3. #twitchrecap 13.4K posts
- 4. #TADCFriend 1,838 posts
- 5. Pat Kraft 2,315 posts
- 6. Zion 10.1K posts
- 7. Slay 20.1K posts
- 8. Tarantino 8,482 posts
- 9. Romero 23.7K posts
- 10. Bernie 24.5K posts
- 11. #LightningStrikes N/A
- 12. Somali 169K posts
- 13. #GivingTuesday 32.6K posts
- 14. Cody Ponce 1,595 posts
- 15. Sabrina Carpenter 45.1K posts
- 16. Sleepy Don 6,773 posts
- 17. Franklin 68K posts
- 18. Fulham 46.6K posts
- 19. Larry 64.5K posts
- 20. #ShootingStar N/A
You might like
-
 XSS Payloads
XSS Payloads
@XssPayloads -
 Pentester Land
Pentester Land
@PentesterLand -
 Sam Curry
Sam Curry
@samwcyo -
 Altered Security
Altered Security
@AlteredSecurity -
 Bug Bounty Reports Explained
Bug Bounty Reports Explained
@gregxsunday -
 ProjectDiscovery
ProjectDiscovery
@pdiscoveryio -
 InfoSec Community
InfoSec Community
@InfoSecComm -
 Patrik Fehrenbach
Patrik Fehrenbach
@ITSecurityguard -
 Suraj
Suraj
@PwnFunction -
 Nuclei by ProjectDiscovery
Nuclei by ProjectDiscovery
@pdnuclei -
 Adam Langley
Adam Langley
@BuildHackSecure -
 Farah Hawa
Farah Hawa
@Farah_Hawaa -
 todayisnew
todayisnew
@codecancare -
 Nicolas Grégoire
Nicolas Grégoire
@Agarri_FR -
 Tib3rius
Tib3rius
@0xTib3rius
Something went wrong.
Something went wrong.



















































































