
harrychew
@harrychewys
#new
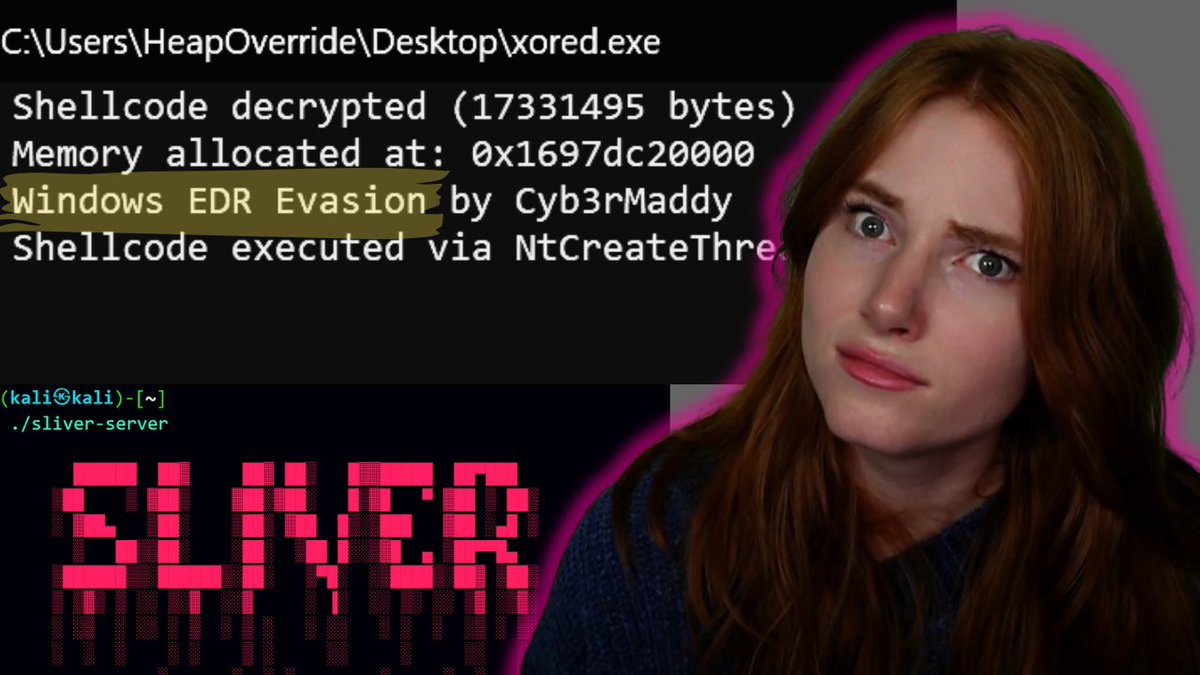
🔥 BYPASS WINDOWS DEFENDER XOR-obfuscate a Sliver C2 payload on Kali, forge a stealth C++ loader, and drop a reverse shell on Win10 in seconds. OUT NOW: youtu.be/lC9zh3_S-zg
We’re seeing a clear trend: attackers are bypassing the endpoint entirely. Not just avoiding traditional EDR-monitored systems by pivoting to embedded and edge devices, but now also operating purely in the cloud. No shell, no malware, no persistence on the endpoint. Just an OAuth…
.@Volexity #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets. volexity.com/blog/2025/04/2… #dfir
W00t W00t! Completed the #CTF for Azure AD Lab from #AlteredSecurity! alteredsecurity.com/azureadlab #AzADLab #EnterpriseSecurity via @alteredsecurity cc @nikhil_mitt

Critical vulnerability (CVE-2024-9956) in Chrome’s WebAuthn on Android allowed attackers to hijack PassKeys via Bluetooth. The vulnerability stemmed from an improper implementation in Chrome’s WebAuthentication API handling: offs.ec/4j9TcvP
Read “New Ransomware Tactic: Adversaries Target ESXi Servers” in the @CrowdStrike blog → bit.ly/2NB2xnm #cybersecurity

United States Trends
- 1. Sam Houston 1,093 posts
- 2. Louisville 14.3K posts
- 3. Boots 28.8K posts
- 4. Boots 28.8K posts
- 5. #GoAvsGo 1,483 posts
- 6. Batum N/A
- 7. Nuss 5,607 posts
- 8. UCLA 7,695 posts
- 9. Emmett Johnson 2,249 posts
- 10. Miller Moss 1,198 posts
- 11. #Huskers 1,065 posts
- 12. Oregon State 4,562 posts
- 13. #FlyTogether 1,823 posts
- 14. #MASHLE 1,304 posts
- 15. Oilers 4,607 posts
- 16. Bama 13.7K posts
- 17. #Toonami 1,857 posts
- 18. Nikki Glaser N/A
- 19. Brohm 1,142 posts
- 20. Lateef 2,254 posts
Something went wrong.
Something went wrong.


























































