alex
@insertScript
@[email protected] # http://insert-script.blogspot.co.at Array(10).join('a'-1)+ Batman! #Cure53
Вам может понравиться
I can really recommend his book. I should know, I have read his previous books :-D

In a shameless effort to promote my book. I've crafted some very special vectors for you. If you like them please purchase my book to read more. amazon.com/dp/B0BRD9B3GS

Want to learn how to craft payloads like these? Read JavaScript for Hackers to master creative XSS techniques and understand exactly why they work. 🧠 Learn to think like a hacker ⚡ Master the art of payload design Grab your copy 👉 amazon.com/JavaScript-hac…
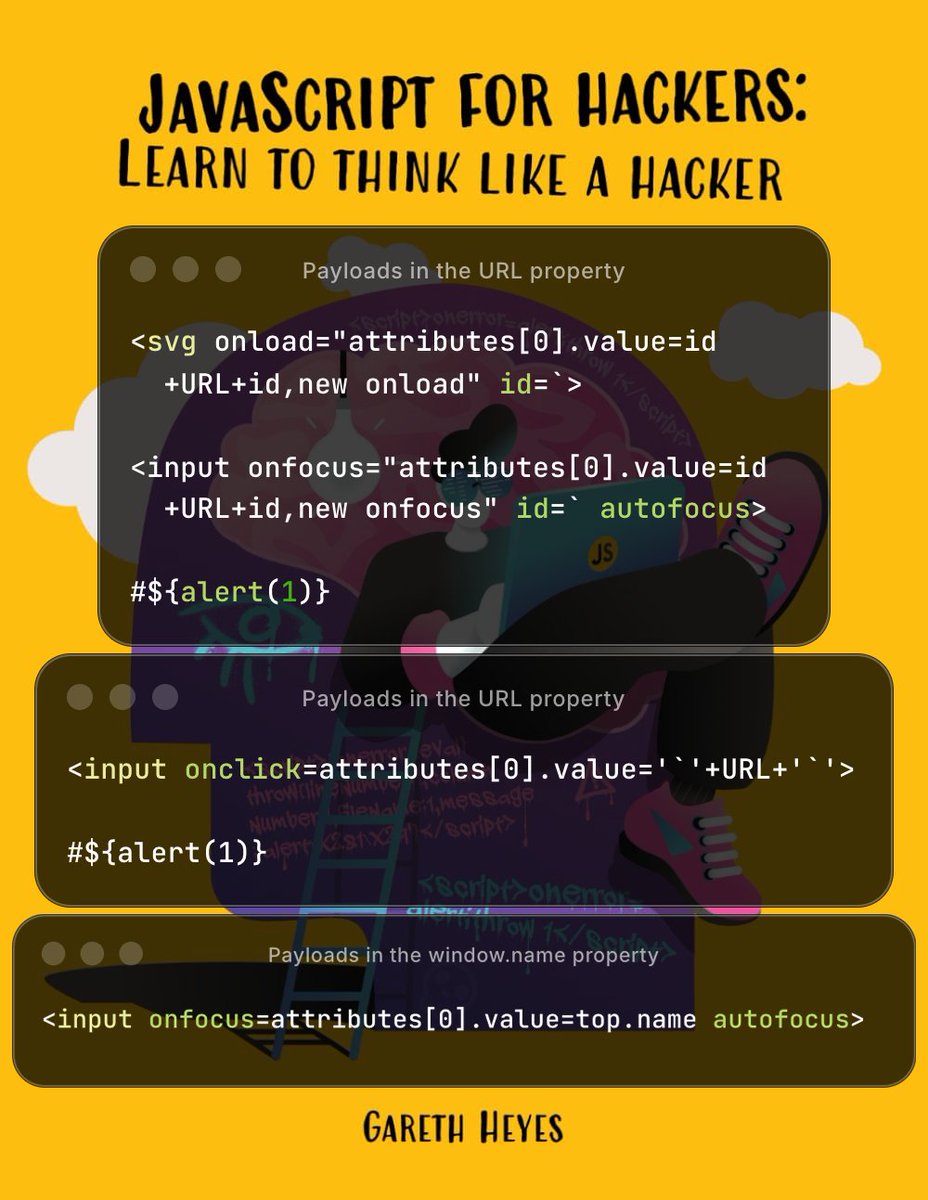
Even if you are familiar with these vectors, its a really good summary to freshen up your memory.
How to turn iframes and window.open into weapons for XSS. From origin manipulation to sandbox escape, this paper by @aszx87410 is stacked with juicy info. Huli dives deep into the magical world of iframes and and is definitely worth a read!…

GMSGadget (Give Me a Script Gadget) is a collection of JavaScript gadgets that can be used to bypass XSS mitigations such as Content Security Policy (CSP) and HTML sanitizers like DOMPurify. gmsgadget.com A useful tool by @kevin_mizu
I’ve just published slides on Shadow DOM & security! 遅ればせながら #shibuyaxss の資料を公開しました!Shadow DOMとセキュリティの話です~ speakerdeck.com/masatokinugawa… (日本語) speakerdeck.com/masatokinugawa… (English)
<meta http-equiv="refresh" content="0;url='//example.com'@x.com/'"> Chrome redirects to x.com, Safari and Firefox redirect to example.com.
publication of my latest modest paper; Eclipse on Next.js: Conditioned exploitation of an intended race-condition - (CVE-2025-32421) enabling a partial bypass of my previous vulnerability, CVE-2024-46982 by chaining a race-condition to a cache-poisoning zhero-web-sec.github.io/research-and-t…

This will be one of the few occasion I will mention a brand, its not IT Security related and positive. My @HyperX wireless headset started to dismantle itself and the support just requested proof pictures and all was good, a new one was shipped.
I think many people are familiar with the topic of blind CSS exfiltration, especially after the post by @garethheyes However, an important update has occurred since then, which I wrote below ->
the research paper is out: Next.js and the corrupt middleware: the authorizing artifact result of a collaboration with @inzo____ that led to CVE-2025-29927 (9.1-critical) zhero-web-sec.github.io/research-and-t… enjoy the read!

What an awesome research! Also really well explained
I'm thrilled to finally share my research on HTML parsing and DOMPurify at @GreHack 2024 📜 The research article is available here: mizu.re/post/exploring… The slides are available here: slides.com/kevin-mizu/gre… 1/3

Absolutely stunning work from @pspaul95 on this CSS Injection - > text node exfil technique. blog.pspaul.de/posts/bench-pr…
MXSS Part 2: Why Client-Side HTML Sanitization is hard In this video, we dive into Parser Differentials, Namespace Confusion, and the Nesting Depth Limit that led to an XSS on Google and multiple DOMPurify bypasses. youtu.be/vVwo5tW6d3w

I really liked it - can't wait for any additional research in this field
This talk by Paul Gerste from @Sonar_Research is really cool 🤩 It applies the principles of "HTTP Desync" attacks to non-HTTP protocols, here database wire protocols 🧠 media.defcon.org/DEF%20CON%2032…
MXSS Explained Part 1: Why Server-Side HTML Sanitizers Are Doomed to Fail with this XSS! In this video, I dive into how sanitizers work, discuss the first known MXSS in IE, and showcase an MXSS vulnerability in the popular Node.js module, sanitize-html. youtu.be/aczTceXp49U

here is the story about CUPS unauthenticated RCE and the messy info dicslosure process the researcher had gone through... evilsocket.net/2024/09/26/Att…
really interesting documentation how history.back, iframes srcdoc and the sandbox attribute are evaluated/loaded to achieve XSS.
there is a challenge in idekCTF 2024 called srcdoc-memos made by icesfont, it's about iframe, sandbox, CSP, navigation, session history and policy container. I spent like a week to understand how it works lol, really complex but also interesting. blog.huli.tw/2024/09/07/en/…
XSS in PDF.js! I think this is going to cause some chaos both client-side and server-side... really nice finding by @CodeanIO codeanlabs.com/blog/research/…
Can't wait to see the payload - especially as I had looked at PDF.js in the past and back then their implementation seemed quite good to ensure XSS can't occure.
Holy shit, CVE-2024-4367 PDF.js vulnerable to arbitrary JavaScript execution upon opening a malicious PDF github.com/advisories/GHS… #infosec
I've built a brand new version of my fuzzing tool Shazzer🚀 shazzer.co.uk - Easy fuzz browser behaviour - Find bugs - Share the results with the world
United States Тренды
- 1. #GrandEgyptianMuseum 26.9K posts
- 2. #capcutlovers N/A
- 3. Chovy 7,272 posts
- 4. Good Saturday 14.8K posts
- 5. GenG 4,200 posts
- 6. Happy New Month 194K posts
- 7. #Worlds2025 49.2K posts
- 8. Game 7 76.7K posts
- 9. Nigeria 432K posts
- 10. jungkook 700K posts
- 11. #RUNSEOKJIN_epTOUR_ENCORE 346K posts
- 12. Kawhi 8,785 posts
- 13. vmin 5,293 posts
- 14. Shirley Temple N/A
- 15. #Jin_TOUR_ENCORE 300K posts
- 16. Tinubu 47.4K posts
- 17. Ja Morant 6,095 posts
- 18. Barger 6,196 posts
- 19. Glasnow 6,958 posts
- 20. Halloween 2025 184K posts
Вам может понравиться
-
 Gareth Heyes \u2028
Gareth Heyes \u2028
@garethheyes -
 Soroush Dalili
Soroush Dalili
@irsdl -
 Nicolas Grégoire
Nicolas Grégoire
@Agarri_FR -
 @[email protected]
@[email protected]
@SecurityMB -
 Jun Kokatsu
Jun Kokatsu
@shhnjk -
 Orange Tsai 🍊
Orange Tsai 🍊
@orange_8361 -
 Josip Franjković
Josip Franjković
@JosipFranjkovic -
 André Baptista
André Baptista
@0xacb -
 Joel Margolis (teknogeek)
Joel Margolis (teknogeek)
@0xteknogeek -
 Eduardo Vela
Eduardo Vela
@sirdarckcat -
 terjanq
terjanq
@terjanq -
 Masato Kinugawa
Masato Kinugawa
@kinugawamasato -
 Alvaro Muñoz
Alvaro Muñoz
@pwntester -
 Jon Bottarini
Jon Bottarini
@jon_bottarini -
 Ashar Javed
Ashar Javed
@soaj1664ashar
Something went wrong.
Something went wrong.