You might like
I have completed the FORCED ENTRY RCE + SBX chain with a PAC bypass. The calculator payload can be found here: github.com/jeffssh/CVE-20…. I learned a lot about iOS exploitation and can't wait to share that in a blog post, which I'll release along with the code to generate this PDF.
We really should be talking about this more....KASLR is just not working properly on Android right now, and it hasn't for a long time. googleprojectzero.blogspot.com/2025/11/defeat…
As the operator of a soup kitchen, I don’t see why I should be expected to fix health code violations people report. After all, we are run almost entirely by volunteers
Pointer leaks through pointer-keyed data structures googleprojectzero.blogspot.com/2025/09/pointe…
Me and the homies are dropping browser exploits on the red team engagement 😎. Find out how to bypass WDAC + execute native shellcode using this one weird trick -- exploiting the V8 engine of a vulnerable trusted application. ibm.com/think/x-force/…
I'm thrilled to announce that my talk Ghost Calls: Abusing Web Conferencing for Covert Command & Control was accepted to #BHUSA 2025 (CC: @BlackHatEvents) blackhat.com/us-25/briefing…
Dammit, that's a typo and I can't edit the post. Well anyway project-zero.issues.chromium.org/issues/42451725
V8 Sandbox escape/bypass/violation and VR collection github.com/xv0nfers/V8-sb…
Chrome Browser Exploitation: from zero to heap sandbox escape by @matteomalvica youtube.com/watch?v=RL2po1…

youtube.com
YouTube
Chrome Browser Exploitation: from zero to heap sandbox escape -...
Pwndbg 2025.01 is out! It adds official LLDB support including support for macOS and Mach-O binaries, improved performance, enhanced embedded debugging & many more! Also, want to support us or buy us a coffee? See our GH sponsors: github.com/sponsors/pwndbg github.com/pwndbg/pwndbg/…
Allocating new exploits Pwning browsers like a kernel & Digging into PartitionAlloc and Blink engine phrack.org/issues/71/10.h…
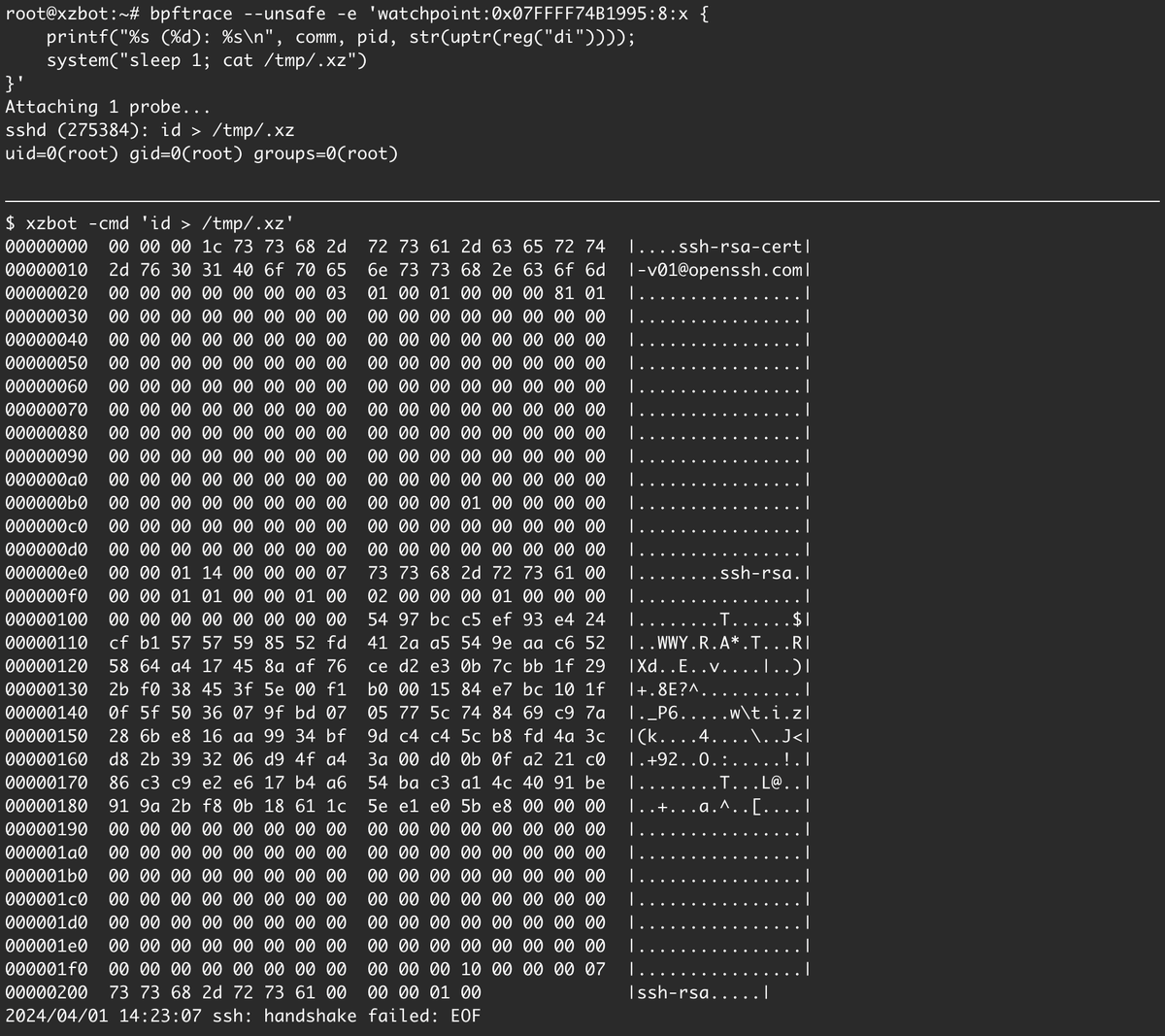
I've been reverse engineering the xz backdoor this weekend and have documented the payload format and written a proof-of-concept exploit for the RCE. The payloads are signed with an ED448 key, so I patched my own key into the backdoor for testing. :-) github.com/amlweems/xzbot
Rough copy of the FORCEDENTRY code is now available. Most relevant code is here: github.com/jeffssh/CVE-20… Blog soon!
Does See No Eval deserve some kind of Most Underrated Research nomination?
they’re called 0days because ive found 0 of them
United States Trends
- 1. Grammy 411K posts
- 2. #FliffCashFriday 2,215 posts
- 3. Dizzy 10.9K posts
- 4. James Watson 9,678 posts
- 5. #NXXT 1,186 posts
- 6. Clipse 23.8K posts
- 7. Kendrick 66.9K posts
- 8. Darryl Strawberry 1,500 posts
- 9. #GOPHealthCareShutdown 10.8K posts
- 10. Chase 89.5K posts
- 11. #tnwx N/A
- 12. MANELYK EN COMPLICES 13.2K posts
- 13. Orban 52.6K posts
- 14. Thune 81.3K posts
- 15. Klay 5,863 posts
- 16. #FursuitFriday 12.7K posts
- 17. Bijan 3,263 posts
- 18. Capitol Police 13.7K posts
- 19. Laporta 14.4K posts
- 20. Carmen 48.3K posts
You might like
-
 seal
seal
@seal9055 -
 Interrupt Labs
Interrupt Labs
@InterruptLabs -
 sakura
sakura
@eternalsakura13 -
 Moshe Kol
Moshe Kol
@0xkol -
 Blacktop
Blacktop
@blacktop__ -
 Mickey Jin
Mickey Jin
@patch1t -
 starlabs
starlabs
@starlabs_sg -
 Jiska
Jiska
@naehrdine -
 kylebot
kylebot
@ky1ebot -
 maxpl0it
maxpl0it
@maxpl0it -
 Alex Plaskett
Alex Plaskett
@alexjplaskett -
 Dohyun Lee
Dohyun Lee
@l33d0hyun -
 Blackstorm Security
Blackstorm Security
@blackstormsecbr -
 Dataflow Security
Dataflow Security
@dfsec_com -
 Rado RC1
Rado RC1
@RabbitPro
Something went wrong.
Something went wrong.