Kev
@kevin_backhouse
Security researcher @GHSecurityLab @GitHub. Opinions are my own. he/him
Talvez você curta
You know what else is interesting about Kong? @pwntester reported an Actions injection (which is probably still viable) that the Kong security team claimed was not a valid report. securitylab.github.com/advisories/GHS…
🎉 You can now enable code scanning in your GitHub Actions workflow files! ✅ By opting-in to this feature, you can enhance the security of repositories using GitHub Actions. github.blog/changelog/2024…
🚀 CodeQL zero to hero part 4: Gradio case study is out! This time we dive into how I wrote CodeQL to support the Gradio framework, scaled the research to a thousand repositories on GitHub, and found 11 vulnerabilities. gh.io/codeql-part-4
Solid advice usually. Not convinced it'll work on a smart meter though.

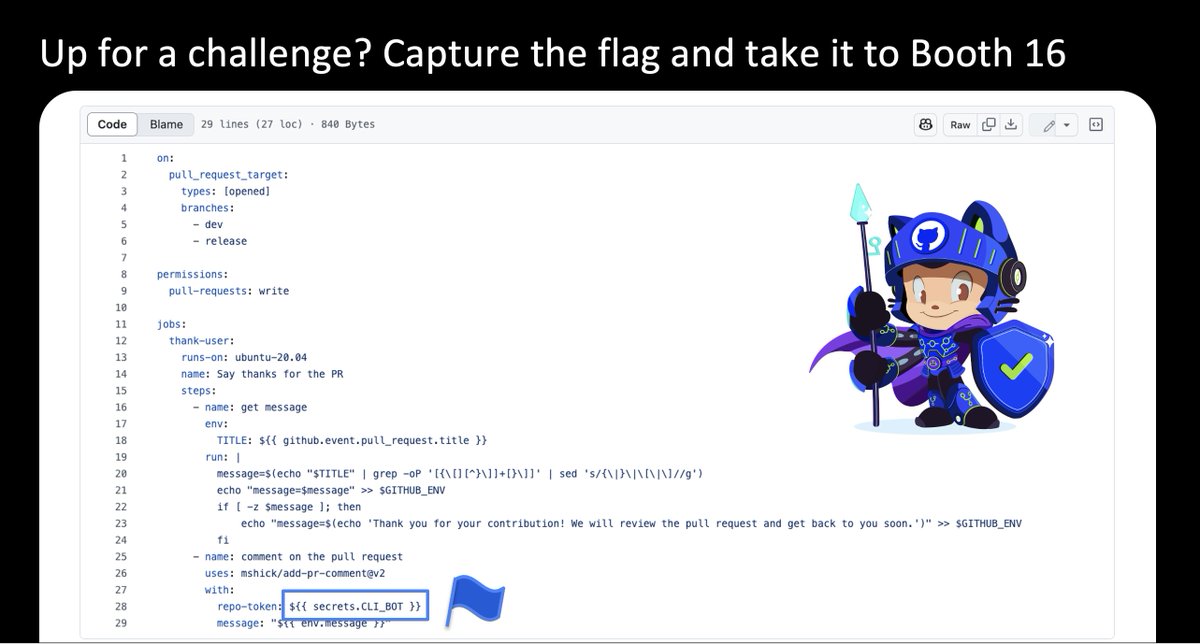
This is one of the real world vulnerabilities found by the new CodeQL packs. Can you exploit it to get the flag? Bring us your solution to GitHub boot at @ekoparty to win some swag!
Up for a challenge? This is the CTF challenge that we shared during the "Security in Action(s)" talk at @ekoparty Be the first one to send us the PR title that could get you the flag and gain some GitHub Swag if you are #EkoParty2024
Next week I'll be at @ekoparty talking about vulnerabilities in GitHub Actions and how I extended CodeQL to find them at scale. I've wanted to go to Eko for years - it's a dream come true, and on their 20th anniversary no less! So excited!

The contrast between two CUPS vulns is amazing. This one, CVE-2024-35235, seems to have flown completely under the radar - in total contrast to CVE-2024-47176. It was an LPE with an exploit chain that sounds very reliable. I only heard about it for the first time today.
Want more CUPS vulns? Read about how our security labs team chained CUPS with some Ubuntu features for privilege escalation on Ubuntu 24.04: snyk.co/uhxsS
labs.snyk.io
Abusing Ubuntu 24.04 features for root privilege escalation | Snyk Labs
With the recent release of Ubuntu 24.04, we at Snyk Security Labs thought it would be interesting to examine the latest version of this Linux distribution to see if we could find any interesting...
Want to learn how to secure your browser extensions? Read our latest blog post where we talk about the security model of browser extensions and how developers can keep them secure. github.blog/security/vulne…
Morning world! Slept ‘ok’ (not great not terrible) So yesterday I was doing some mitm6 over public WiFi (in the lab) and whilst I was speeding dns responses to Microsoft Google Facebook Twitter etc. My web clients simply did not follow the responses and went to the actual…

Charlas MainTrack #EKO2024 🔥 📌 @artsploit, Security Researcher at GitHub Security Lab 💡 “Breaking corporate Maven repositories”: In the Java ecosystem, companies often use in-house repository managers, such as Sonatype Nexus or JFrog Artifactory, to store artifacts and cache…

We had a short look at the buffer overflow found by fuzzing `process_browse_data` to determine its exploitability. Conclusion: this bug alone won't give you RCE, or even an info leak.
> critical 9.9 cvss "unauthenticated" rce on linux!!!! > look inside > requires local network access, user interaction, and non-default configuration

Considering the amount of hype, it's a bit weak to only have a poc that requires the user to try to print to a new device that just magically appeared on their network.
I love how everybody is like "oooh boring, the user has to print something!" and entirely ignoring the buffer overflows and whatnot in a process running as root :'D small, small people :D
This series is fun. I was buying cable recently and literally couldn't find any information about the technical differences between CAT5e, CAT6a, etc. I ended up buying F/FTP CAT6a and the shielding is so heavy that it doesn't really bend. Looking forward to the CAT8 episode!
have you ever wondered what’s inside a CAT7 twisted pair (ethernet) cable? no? too bad here it is
In August, watchTowr Labs hijacked parts of the global .mobi TLD - and went on to discover the mayhem that we could cause. Enjoy.... labs.watchtowr.com/we-spent-20-to…
GHSL-2024-005_GHSL-2024-008: SSRF, XSS, RCE and Sensitive information disclosure in OpenHAB Web UI - CVE-2024-42467, CVE-2024-42468, CVE-2024-42469, CVE-2024-42470 securitylab.github.com/advisories/GHS…
United States Tendências
- 1. Thanksgiving 147K posts
- 2. #IDontWantToOverreactBUT 1,318 posts
- 3. #GEAT_NEWS 1,422 posts
- 4. Jimmy Cliff 24.3K posts
- 5. #WooSoxWishList 2,317 posts
- 6. #MondayMotivation 13.5K posts
- 7. #NutramentHolidayPromotion N/A
- 8. DOGE 234K posts
- 9. Victory Monday 4,420 posts
- 10. $ENLV 18.9K posts
- 11. TOP CALL 5,038 posts
- 12. Monad 174K posts
- 13. Good Monday 52.3K posts
- 14. Justin Tucker N/A
- 15. Feast Week 2,013 posts
- 16. The Harder They Come 3,695 posts
- 17. $GEAT 1,317 posts
- 18. $MON 34.1K posts
- 19. AI Alert 3,084 posts
- 20. Market Focus 3,222 posts
Talvez você curta
-
 offensivecon
offensivecon
@offensive_con -
 Project Zero Bugs
Project Zero Bugs
@ProjectZeroBugs -
 sakura
sakura
@eternalsakura13 -
 Samuel Groß
Samuel Groß
@5aelo -
 Brandon Falk
Brandon Falk
@gamozolabs -
 Ivan Fratric 💙💛
Ivan Fratric 💙💛
@ifsecure -
 waldoirc
waldoirc
@waldoirc -
 Taszk Security Labs
Taszk Security Labs
@TaszkSecLabs -
 nand2mario
nand2mario
@nand2mario -
 Niklas B
Niklas B
@_niklasb -
 itszn
itszn
@itszn13 -
 Đào Trọng Nghĩa
Đào Trọng Nghĩa
@nghiadt1098 -
 Vitaly Nikolenko
Vitaly Nikolenko
@vnik5287 -
 ohjin
ohjin
@pwn_expoit -
 Jacob Soo
Jacob Soo
@_jsoo_
Something went wrong.
Something went wrong.