
Caroline
@kirbytypes
Incident Response & Threat Hunting at TrustedSec. Striving cloud nerd. Recovering scene kid. Opinions are my own.
You might like
Check out my first blog contribution here where we discuss a recent intrusion my team investigated, from an initial access Gootloader infection, 2nd stage payloads, and lateral movement to credential access. Super proud of this! reliaquest.com/blog/gootloade…
Hey that's me y'all! Open to anyone :)
Business Email Compromise (BEC) attacks are becoming increasingly common. Register for our next #webinar where we will cover: 📥Microsoft 365 License levels 📈Log sources and accompanying data 🔎Common evidence locations hubs.la/Q02ZCRdF0 @kirbytypes @StevenErwin

Business Email Compromise (BEC) can threaten an organization's security at any level. During our next webinar, our experts will cover how pinpoint critical logs and artifacts essential for detecting suspicious BEC activities. Register now! hubs.la/Q02Q6WFv0

Surely nothing bad can come from publicly posting a monetary reward email pertaining to one of the biggest IT outages in history, right?
lol Crowdstrike crashed millions of computers with a glitch and then sent an apology to partners in the form of a $10 Uber Eats gift card

I don't post on here much, but figured since this is my "professional" account, I would share that I'm thrilled to have joined the @TrustedSec DFIR & Threat Hunting team back in May! It's been a great couple months so far, with lots of learning ahead of me. Truly thankful!
A massive data breach at AT&T exposed the data of "nearly all" of its customers. Incident Response Practice Lead Tyler Hudak spoke with Scripps News about what type of data could have been compromised and steps you can take to protect yourself. Watch now! hubs.la/Q02GnMfF0
youtube.com
YouTube
Massive AT&T data breach exposes ‘nearly all’ customers | Scripps News
🚀DFIR Labs CTF🚀 Our next CTF will be July 6, 16:00 – 20:00 UTC. ➡️Only $9.99 to join! ➡️Choose Elastic or Splunk as your SIEM ➡️Join our DFIR Labs CTF Discord Server ➡️Top 3 players win free swag! Register: the-dfir-report-store.myshopify.com/products/dfir-… More info: thedfirreport.com/services/dfir-…
Brute force attacks against VPNs? Groundbreaking.
Cisco warns of large-scale brute-force attacks against VPN services - @billtoulas bleepingcomputer.com/news/security/…
!!!!!
This is why I do cloud. Its the new wild west of hacking.
Was offline for 3 days for personal stuff, wtf is "Xmail", why is LE cosplaying as a TA, why does Optum seemingly touch everything, and what in god's name is going on with U.S. mobile carriers????
🎉Happy International Enable Sysmon and 4688 Auditing Day🎉grab yourself a slice of cake, chat to a colleague about it, bring it up at your all hands company meeting, talk to your kids about the most exciting day in the cyber calendar - github.com/reprise99/4688…

"We can confirm that the situation is under control and it is safe to use AnyDesk. " uh huhhhh......
AnyDesk says hackers breached its production servers, resets passwords - @LawrenceAbrams bleepingcomputer.com/news/security/…
Can I send like the biggest fruit basket ever to the people behind this pls
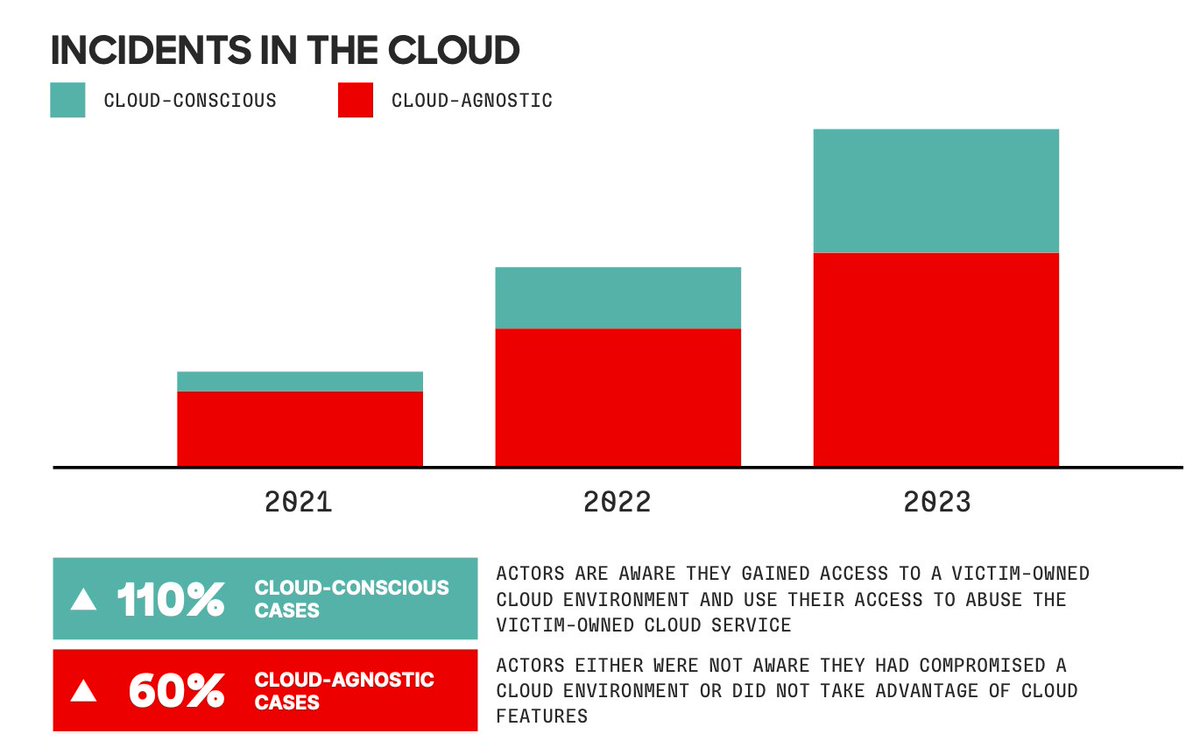
💥 BOOM! Introducing "Cloud Threat Landscape": our extensive (internal) cloud security incident database is now public! Explore 107 incidents, 96 threat actors, and 100+ attack techniques: wiz.io/cloud-threat-l…
Has seriously helped me a in a pinch - def recommend :)
Not enough people know about Hayabusa. github.com/Yamato-Securit… Hands down one of the best tools to use on assessments of all sorts (threat hunting especially!)
I wish we could collectively ban the citation of bleeping computer articles in intelligence updates. Good lord.
Thinking about starting my own Github page for cloud stuff. Hmmmm.
I was on another lil episode of ShadowTalk :) talking MFA bypass, Microsoft storage leak & ALPHV/Scattered Spider: open.spotify.com/episode/0vxZ9C…
The absolute cesspool of assumptions surrounding MGM/Caesars is mind boggling. You'd think at least the cyber community would be able to spot an ACTUAL source of confirmation.
Another lil blog by yours truly about a handful of macOS infostealers reliaquest.com/blog/5-macos-i…
United States Trends
- 1. Ferran 18K posts
- 2. Sonny Gray 7,826 posts
- 3. Rush Hour 4 11.9K posts
- 4. Chelsea 340K posts
- 5. Godzilla 21.4K posts
- 6. Red Sox 7,546 posts
- 7. Barca 122K posts
- 8. Happy Thanksgiving 21.9K posts
- 9. Raising Arizona 1,084 posts
- 10. Dick Fitts N/A
- 11. 50 Cent 5,173 posts
- 12. National Treasure 5,826 posts
- 13. Gone in 60 2,150 posts
- 14. Giolito N/A
- 15. Muriel Bowser N/A
- 16. Brett Ratner 3,639 posts
- 17. Clarke 6,552 posts
- 18. Man in the Mirror 1,409 posts
- 19. Ghost Rider 2,552 posts
- 20. Lord of War 1,519 posts
Something went wrong.
Something went wrong.













































































































