Paul Rascagnères
@r00tbsd
Lord of Loaders at @Volexity | Mastodon account: 🐘 @[email protected] | Bsky @r00tbsd.bsky.social
Вам может понравиться
We released a blogpost concerning #StromBamboo (aka Evasive Panda). @volexity was involved in an incident where the attackers compromised an ISP to poison the customers' DNS requests to hijack software updates (using the HTTP protocol): volexity.com/blog/2024/08/0… 1/3
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: volatilityfoundation.org/announcing-the…
Congratulations to all of the Volatility contributors - this was no small feat! We are proud to be a sustaining sponsor of this important open-source project that remains the world’s most widely used memory forensics platform. #dfir
We are very excited to announce that Volatility 3 has reached parity with Volatility 2! With this achievement, Volatility 2 is now deprecated. See the full details in our blog post: volatilityfoundation.org/announcing-the…
.@Volexity #threatintel: Multiple Russian threat actors are using Signal, WhatsApp & a compromised Ukrainian gov email address to impersonate EU officials. These phishing attacks abuse 1st-party Microsoft Entra apps + OAuth to compromise targets. volexity.com/blog/2025/04/2… #dfir
Check out this great research and new open source tool by our threat intel team!
Today, @Volexity released GoResolver, open-source tooling to assist reverse engineers with obfuscated Golang samples. @r00tbsd & Killian Raimbaud presented details at INCYBER Forum earlier today. Learn how GoResolver works + where to download it: volexity.com/blog/2025/04/0… #dfir

Today, @Volexity released GoResolver, open-source tooling to assist reverse engineers with obfuscated Golang samples. @r00tbsd & Killian Raimbaud presented details at INCYBER Forum earlier today. Learn how GoResolver works + where to download it: volexity.com/blog/2025/04/0… #dfir

📣 Oops!... They did it again!!! 61 Talks submitted and so many too good that, once again, we had to increase a bit the number of accepted talks. 🔥 #PIVOTcon25 Agenda is finally here, and the caliber is insane!!! Check it out ➡️ link below in second post #CTI #ThreatIntel 1/19

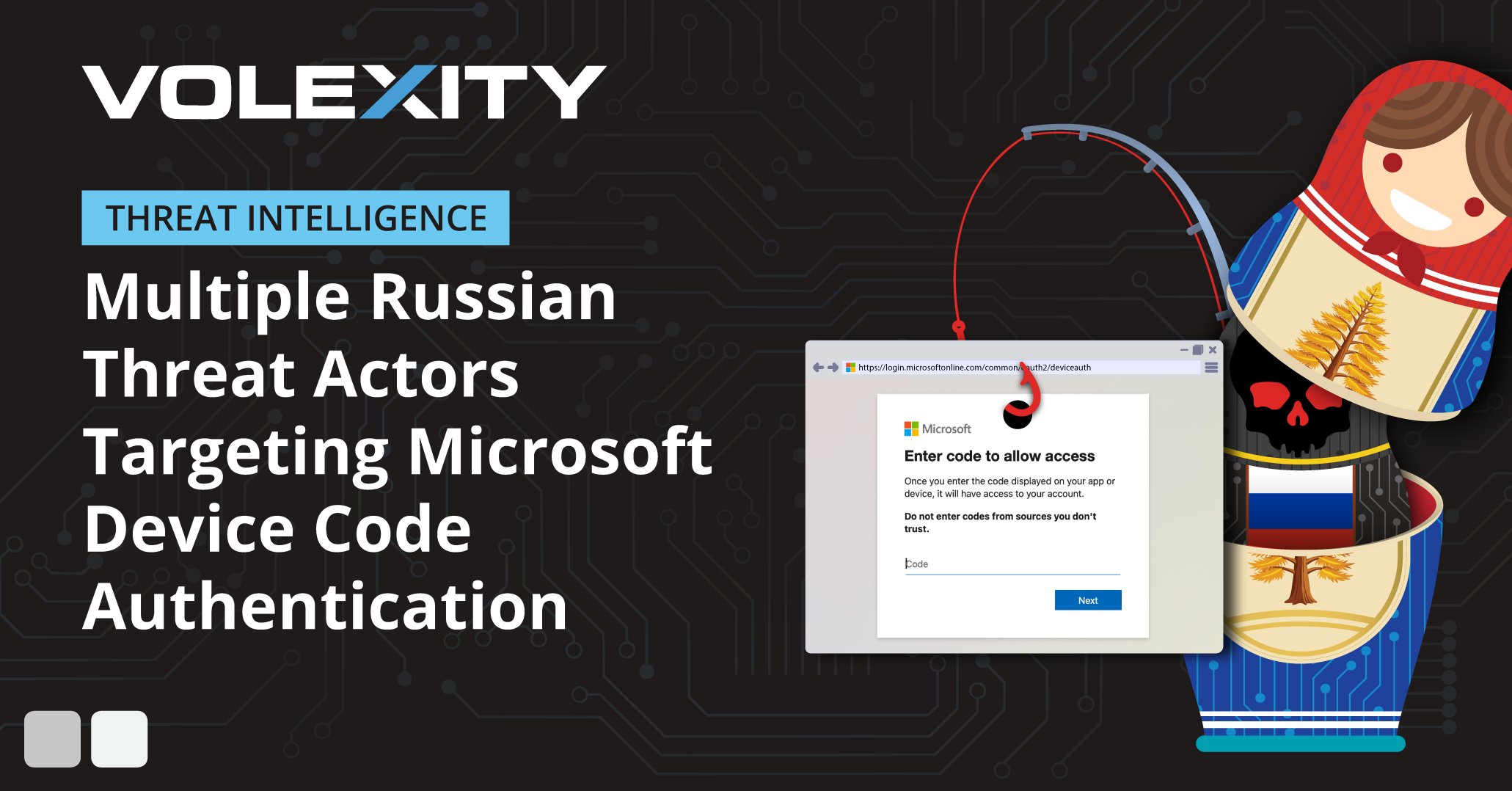
.@Volexity recently identified multiple Russian threat actors targeting users via #socialengineering + #spearphishing campaigns with Microsoft 365 Device Code authentication (a well-known technique) with alarming success: volexity.com/blog/2025/02/1… #dfir #threatintel #m365security
This talk is a great way to watch/listen to the details behind the work @stevenadair, @5ck, @tlansec + @volexity’s #threatintel & IR teams did to investigate the Nearest Neighbor Attack. The related blog post is here: volexity.com/blog/2024/11/2…
volexity.com
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access
In early February 2022, notably just ahead of the Russian invasion of Ukraine, Volexity made a discovery that led to one of the most fascinating and complex incident investigations Volexity had ever...
We were happy to have @Volexity’s @stevenadair & @5ck present “The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access” for the #FTSCon Keynote in October. The video of their talk is now available here: youtu.be/qSNlDCg-IOM. #dfir
.@Volexity has developed a new #opensource tool, “HWP Extract”, a lightweight Python library & CLI for interacting with Hangul Word Processor files. It also supports object extraction from password-protected HWP files. Download here: github.com/volexity/hwp-e… #dfir #threatintel
github.com
GitHub - volexity/hwp-extract: A library and cli tool to extract HWP files.
A library and cli tool to extract HWP files. Contribute to volexity/hwp-extract development by creating an account on GitHub.
Just gave a talk about the Nearest Neighbor Attack at #CYBERWARCON and had a great time detailing our findings. This was a lot of great work by our @Volexity team and special thanks to @5ck and @tlansec for the long hours working on it! Def. one of our wildest #DFIR engagements!
.@Volexity’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target, while the attacker was halfway around the world. volexity.com/blog/2024/11/2… #dfir
volexity.com
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access
In early February 2022, notably just ahead of the Russian invasion of Ukraine, Volexity made a discovery that led to one of the most fascinating and complex incident investigations Volexity had ever...
.@Volexity’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target, while the attacker was halfway around the world. volexity.com/blog/2024/11/2… #dfir
volexity.com
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access
In early February 2022, notably just ahead of the Russian invasion of Ukraine, Volexity made a discovery that led to one of the most fascinating and complex incident investigations Volexity had ever...
@stevenadair and I presented on this last month at #FTSCon (IYKYK). Steven is also presenting today @CYBERWARCON. Really excited to finally share this research publicly! It's probably one of the more crazy/interesting IR engagements we've ever worked! #DFIR #ThreatIntel
.@Volexity’s latest blog post describes in detail how a Russian APT used a new attack technique, the “Nearest Neighbor Attack”, to leverage Wi-Fi networks in close proximity to the intended target, while the attacker was halfway around the world. volexity.com/blog/2024/11/2… #dfir
volexity.com
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access
In early February 2022, notably just ahead of the Russian invasion of Ukraine, Volexity made a discovery that led to one of the most fascinating and complex incident investigations Volexity had ever...
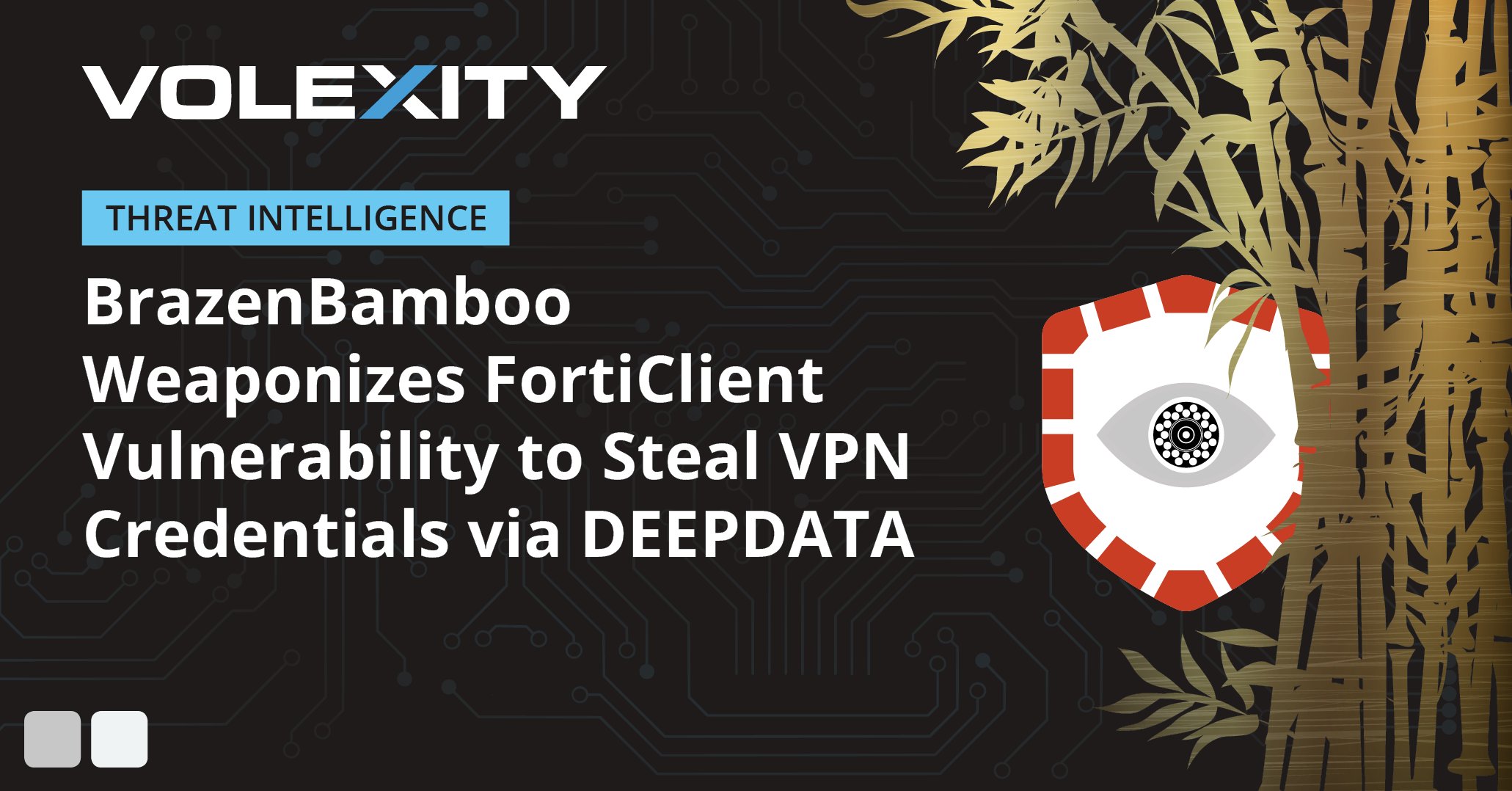
.@Volexity has published a blog post detailing variants of LIGHTSPY & DEEPDATA malware discovered in the summer of 2024, including exploitation of a vulnerability in FortiClient to extract credentials from memory. Read more here: volexity.com/blog/2024/11/1… #dfir #threatintel
Tomorrow I will do an unexpected talk about edge-security incidents at @hack_lu. I will present the behind the scenes of the recent incident responses where we have been involved. #hacklu
There are only a few tickets left for #FTSCon & we are planning to close registration Monday! We are excited to see all of you & hear great talks by amazing speakers from across the industry. Register here: events.humanitix.com/from-the-sourc… #dfir
We are hiring! Come join @Volexity's Threat Detection team. This is a SOC-type role with purview across our customers to identify suspicious & malicious activity using our telemetry across network, EDR/AV, email, logs & more! Take a look! volexity.com/company/career…
And here is another opportunity to hear a talk from @Volexity at #FTSCon on October 21: Steven Adair (@stevenadair) and Sean Koessel (@5ck ) will present "The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access" x.com/volatility/sta…
We are excited to announce the opening keynote for #FTSCon: @Volexity's Steven Adair & Sean Koessel will present "The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access". Event details + how to register: volatilityfoundation.org/from-the-sourc… #dfir

We are excited to announce the opening keynote for #FTSCon: @Volexity's Steven Adair & Sean Koessel will present "The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert Access". Event details + how to register: volatilityfoundation.org/from-the-sourc… #dfir

We're hiring @Volexity! Details can be found at the job posting below 👇 volexity.com/company/career… Don't hesitate to reach out with questions!
United States Тренды
- 1. Spotify 1.18M posts
- 2. Chris Paul 34.4K posts
- 3. Clippers 48K posts
- 4. Hartline 11.9K posts
- 5. Ty Lue 3,266 posts
- 6. Henry Cuellar 7,997 posts
- 7. ethan hawke 5,234 posts
- 8. #HappyBirthdayJin 111K posts
- 9. David Corenswet 8,842 posts
- 10. Jonathan Bailey 10K posts
- 11. GreetEat Corp 1,177 posts
- 12. Apple Music 255K posts
- 13. #NSD26 27.4K posts
- 14. SNAP 175K posts
- 15. Chris Henry 2,788 posts
- 16. South Florida 7,084 posts
- 17. Klein 17.3K posts
- 18. Duncan 8,127 posts
- 19. Adam Sandler 5,351 posts
- 20. #JINDAY 86.3K posts
Вам может понравиться
-
 Steve YARA Synapse Miller
Steve YARA Synapse Miller
@stvemillertime -
 Seongsu Park
Seongsu Park
@unpacker -
 Bart
Bart
@bartblaze -
 REhints
REhints
@REhints -
 Karsten Hahn
Karsten Hahn
@struppigel -
 Xylitol
Xylitol
@Xylit0l -
 🥝🏳️🌈 Benjamin Delpy
🥝🏳️🌈 Benjamin Delpy
@gentilkiwi -
Xavier Mertens @[email protected] 🇧🇪
@xme -
 Silas Cutler (p1nk)
Silas Cutler (p1nk)
@silascutler -
 `Ivan
`Ivan
@Ivanlef0u -
 Alexandre Dulaunoy @[email protected]
Alexandre Dulaunoy @[email protected]
@adulau -
 Matt Nelson
Matt Nelson
@enigma0x3 -
 quarkslab
quarkslab
@quarkslab -
 Ange
Ange
@angealbertini -
 James
James
@James_inthe_box
Something went wrong.
Something went wrong.