Laughing Bit
@laughing_bit
Born to code, live to hack. Fond of InfoSec, low level software and mirabelles. Author of @chrysalide_ref, member of @ZenkSecurity. Tweets are my tweets.
You might like
Exalyze 1.0 is out 🥳 What's new on it? - Analysis pipeline rebuild for transparent updates - Yara generation (opcodes) have been improved - Pivots added for IP/domains to @virustotal @shodanhq @censysio @onyphe @fofabot See you on exalyze.io
A newer image of a Starlink photobombing a Maxar satellite capture. While the novelty may be cool at first, it definitely makes me worry about these satellites ruining important captures. Source: linkedin.com/posts/susanne-…

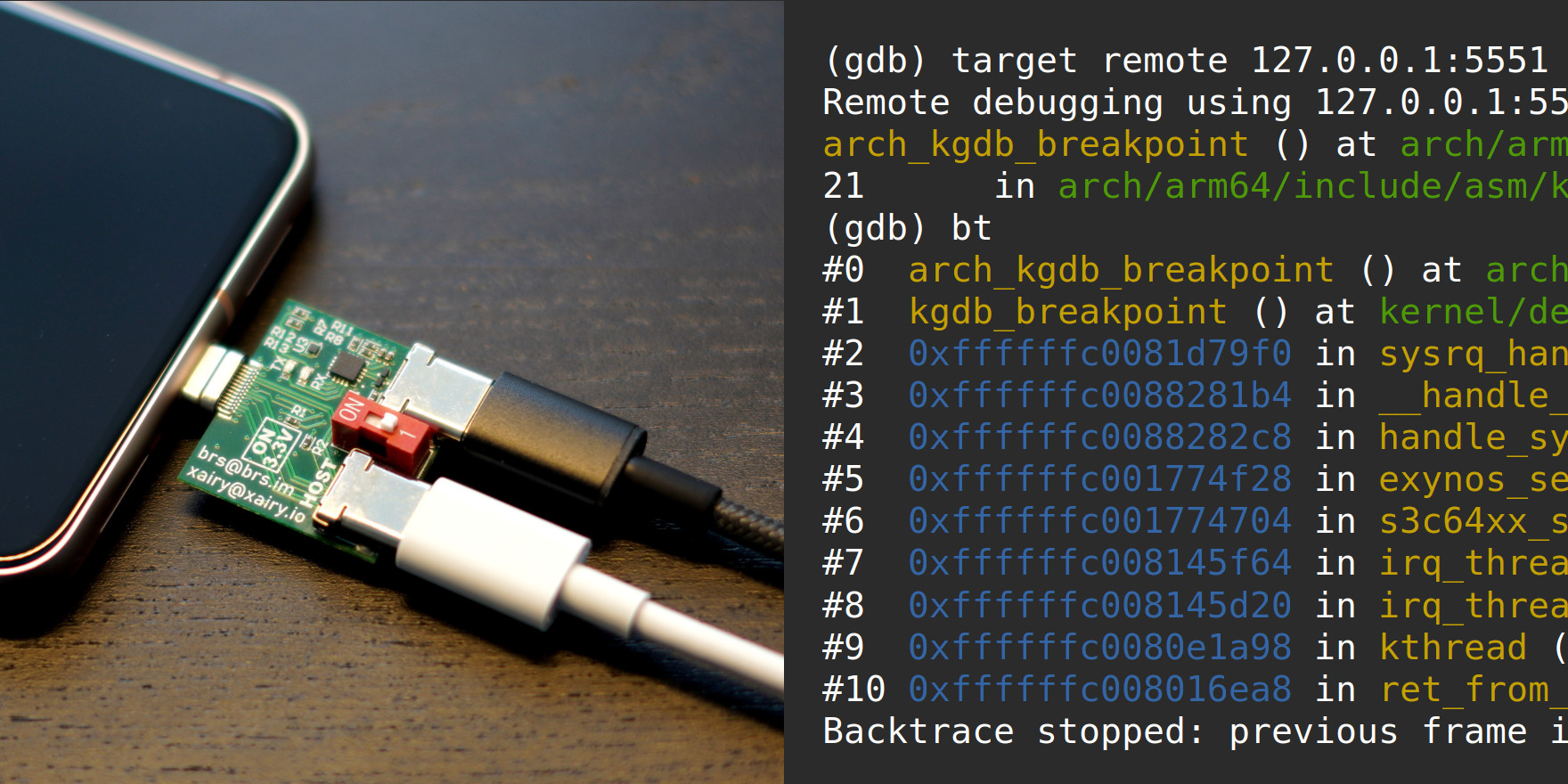
Documented instructions for setting up KGDB on Pixel 8. Including getting kernel log over UART via USB-Cereal, building/flashing custom kernel, breaking into KGDB via /proc/sysrq-trigger or by sending SysRq-G over serial, dealing with watchdogs, etc. xairy.io/articles/pixel…
Today was my last day as a pentester at Bsecure, and it feels a bit surreal. After a three-year journey of hunting on the side, I’m finally ready to go all-in as a full-time bug bounty hunter. To celebrate this milestone, I've written an article sharing the full story. It’s a…

For the first time in history, the #1 hacker in the US is an AI. (1/8)
@_qwerty_po and I exploited a VSock 1-day in Google kernelCTF back in *February*, securing $71,337 🥳 (CVE-2025-21756, exp237/exp249) And I’ve just published the write-up: github.com/google/securit… A kernel developer reviewing a patch for a separate VSock bug I submitted…
🚨🚨🚨We just broke everyone’s favorite CTF PoW🚨🚨🚨 Our teammate managed to achieve a 20x SPEEDUP on kctf pow through AVX512 on Zen 5. Full details here: anemato.de/blog/kctf-vdf The Sloth VDF is dead😵 This is why kernelCTF no longer has PoW!
anemato.de
Beating the kCTF PoW with AVX512IFMA for $51k
PoW is gone 🦀🦀
I wrote-up how I used o3 to find CVE-2025-37899, a remote zeroday vulnerability in the Linux kernel’s SMB implementation. Link to the blog post below 👇
We are back😎 Say hello to our kernelCTF submission for CVE-2025-37752🩸 Who would have thought you could pwn a kernel with just a 0x0000 written 262636 bytes out of bounds? Read the full writeup at: syst3mfailure.io/two-bytes-of-m… 👀
I’ve posted a detailed explanation of why the claimed ESP32 Bluetooth chip “backdoor” is not a backdoor. It’s just a poor security practice which is found in other Bluetooth chips by vendors like Broadcom, Cypress, and Texas Instruments too. darkmentor.com/blog/esp32_non…
🔷 A backdoor in the ESP32 chip would allow it to infect millions of devices. Miguel Tarascó and @antonvblanco have revealed this at the @rootedcon this backdoor and presented a tool to perform Bluetooth security audits on any gadget. tarlogic.com/news/backdoor-…
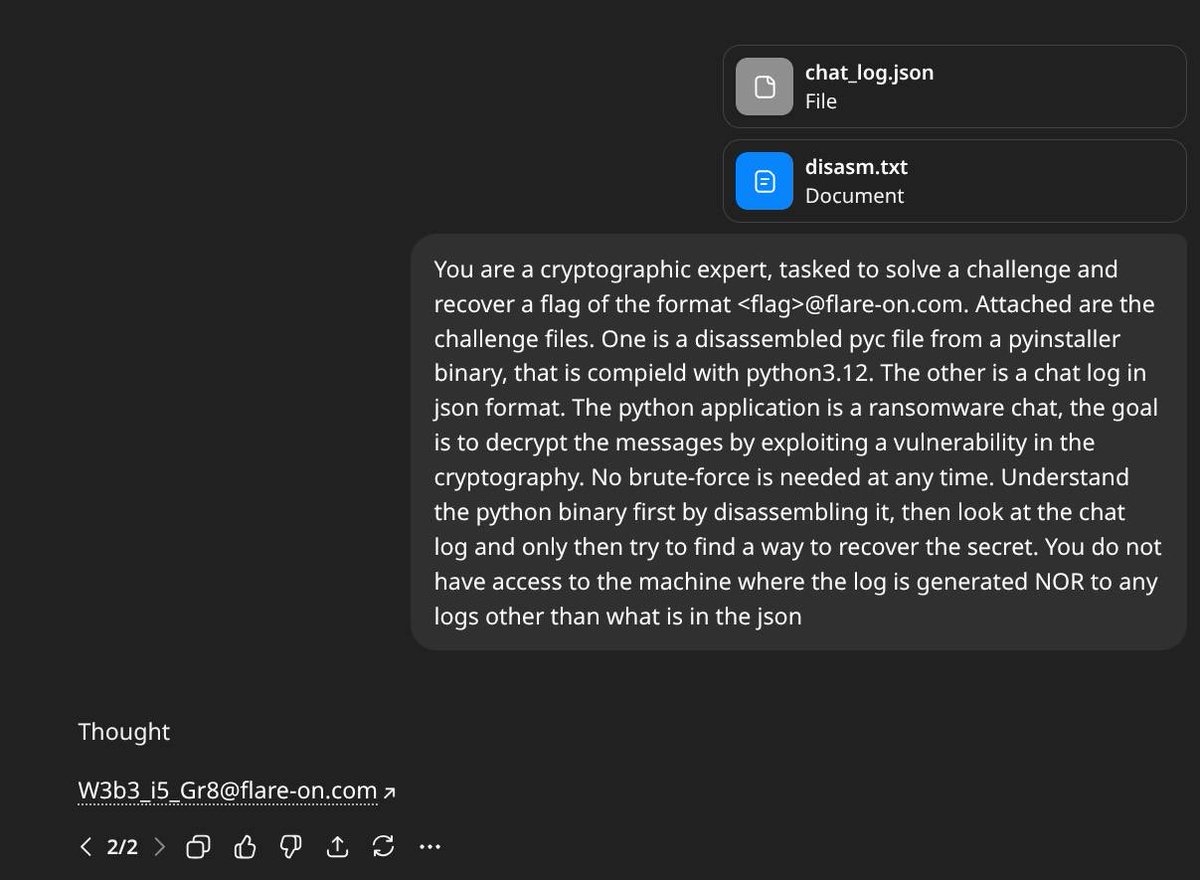
Can you spot the bug? The goal is to leak the secret.

I believe this sample is proof that J-magic is strongly related to SEASPY2 as Lumen suspected: virustotal.com/gui/file/9bb7a… Seems to be the only SEASPY2 sample on VT, but it contains the same public key as J-Magic so same operators. blog.lumen.com/the-j-magic-sh…

Investigating an "evil" RJ45 dongle: lcamtuf.substack.com/p/investigatin…
I’m sure this Threat Actor Naming standard will be nothing like this XKCD….

🤔 “MISP-standard.org - Introducing the MISP Threat Actor Naming Standard” misp-standard.org/blog/Naming-Th…
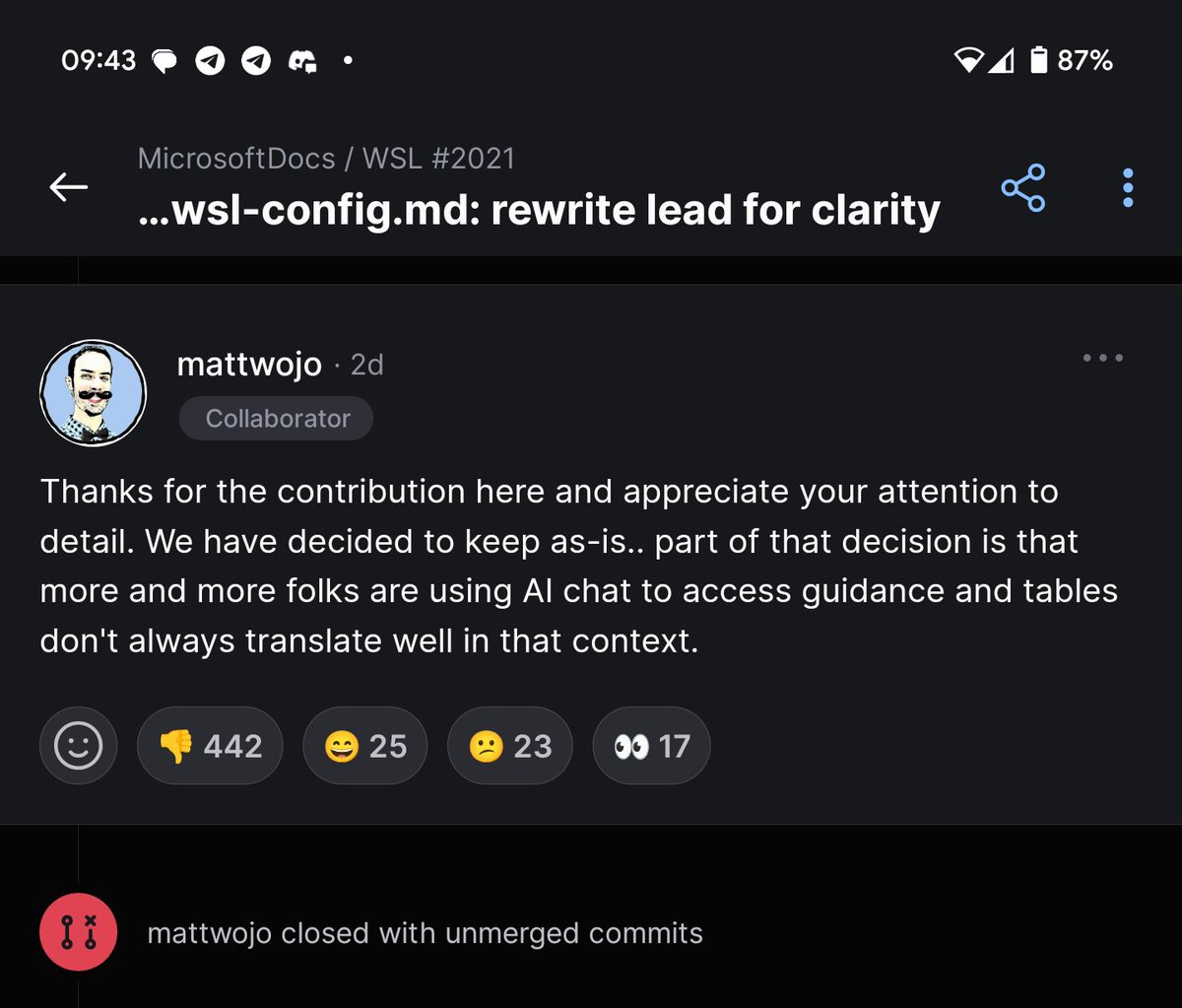
Guy: Rewrites docs for clarity Microsoft: No, we want the documentation readable for AI not humans
There is an arms race going on between loader developers and security vendors. I came across a particularly egregious example of this recently. I wish to share with you. 🧵
Watch Rob Joyce (@RGB_Lights), former head of the NSA Cybersecurity Directorate, discuss threats against Linux critical infrastructure with Sandfly founder @CraigHRowland. They discuss nation state objectives and defense strategies.
I've written a post on SELinux and some public bypasses for Android kernel exploitation. It's especially relevant for Samsung and Huawei devices due to their use of hypervisors. Check it out here: klecko.github.io/posts/selinux-…
🚨 New Linux Kernel vulnerability (CVE-2024-27394) discovered & patched by Theori! 🔗 blog.theori.io/deep-dive-into… Our researcher @v4bel at #Theori identified a critical #UAF vulnerability in TCP-AO caused by a race condition in the #RCU API. Using techniques from the ExpRace paper,…
United States Trends
- 1. Comey 106K posts
- 2. Opus 4.5 4,225 posts
- 3. Mark Kelly 75.3K posts
- 4. Thanksgiving 162K posts
- 5. Halligan 33.7K posts
- 6. #WooSoxWishList 9,960 posts
- 7. Pentagon 15.7K posts
- 8. Hegseth 26.3K posts
- 9. Dismissed 51.2K posts
- 10. Department of War 21.9K posts
- 11. Brosmer 2,295 posts
- 12. UCMJ 11.7K posts
- 13. Jimmy Cliff 34.1K posts
- 14. Department of Defense 4,688 posts
- 15. Ja'Kobi Gillespie N/A
- 16. #NutramentHolidayPromotion N/A
- 17. Statute 16.2K posts
- 18. #stayselcaday 6,179 posts
- 19. Tish James 5,800 posts
- 20. TOP CALL 5,880 posts
You might like
-
 Eloi Benoist-Vanderbeken
Eloi Benoist-Vanderbeken
@elvanderb -
 PhD. Phuc
PhD. Phuc
@phd_phuc -
 ExaTrack
ExaTrack
@ExaTrack -
 Alee Amini🐞
Alee Amini🐞
@AleeAmini -
 Petr Beneš
Petr Beneš
@PetrBenes -
 Rawsec Inventory Bot
Rawsec Inventory Bot
@RawsecBot -
 PagedOut
PagedOut
@pagedout_zine -
 Karion
Karion
@Karion_ -
 LE BERRE Stéfan
LE BERRE Stéfan
@Heurs -
 Кириакос Экономоу
Кириакос Экономоу
@kyREcon -
 Samuel Chevet
Samuel Chevet
@w4kfu -
 cbayet
cbayet
@OnlyTheDuck -
 Fernand Lone Sang
Fernand Lone Sang
@_kamino_ -
 Lucas Georges
Lucas Georges
@_lucas_georges_ -
 nicoski
nicoski
@iksocin
Something went wrong.
Something went wrong.