ya.ko.
@likeitcool
Cyber Security Researcher: Advanced Threat Analysis, Malware Analysis, DFIR
You might like
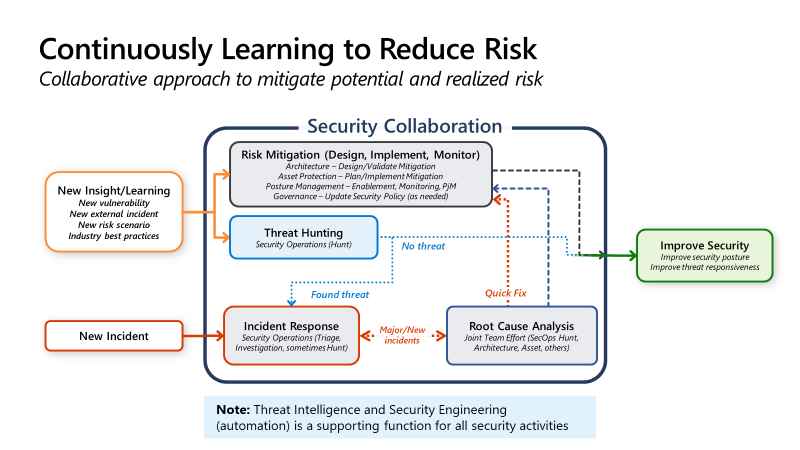
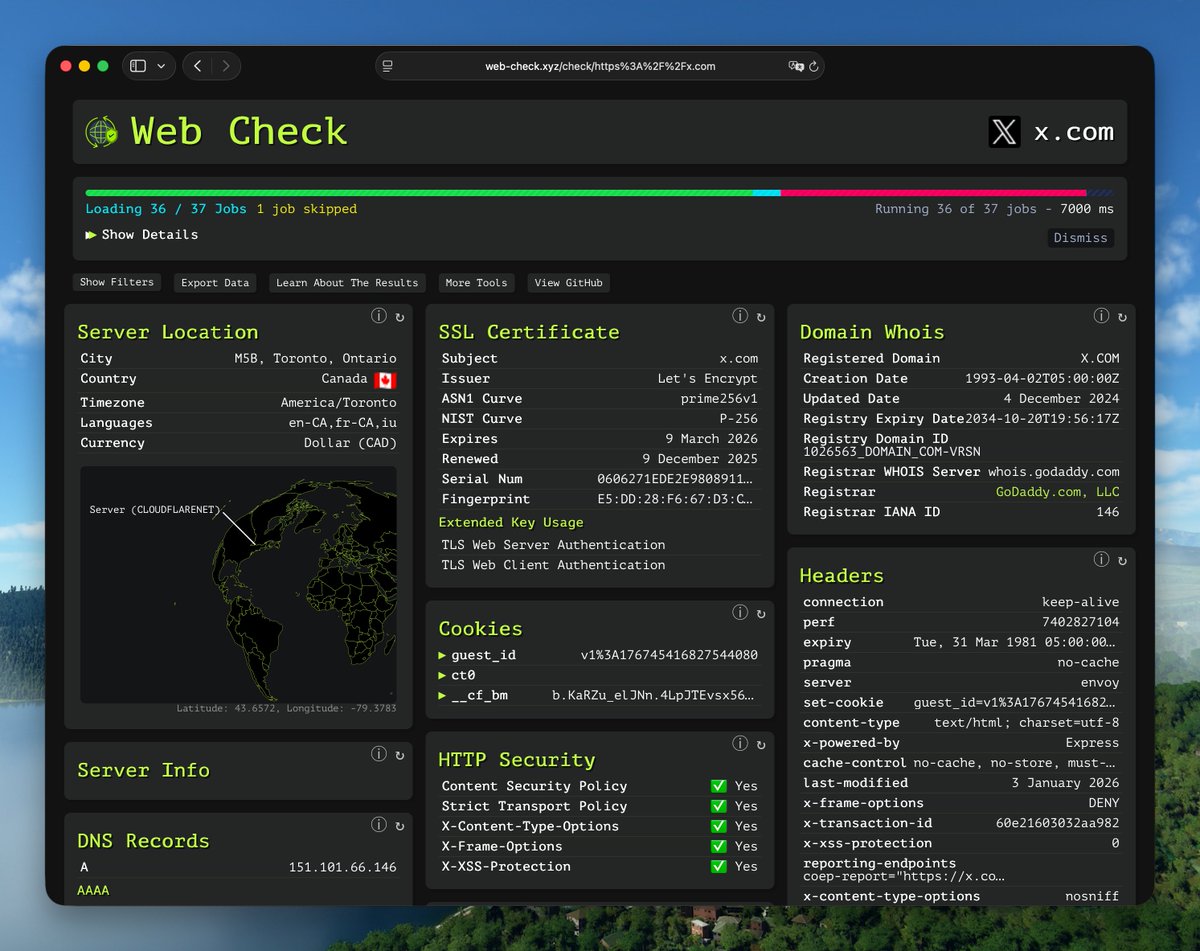
I recently discovered a super cool website inspection tool called Web-Check. It has a strong hacker vibe. It lets you inspect almost everything about a website: IP details, SSL, DNS records, cookies, domain info, crawler rules, server location, redirect history, open ports,…
@xnl_h4ck3r for WAYMORE the ultimate historical link finder! github.com/xnl-h4ck3r/way…
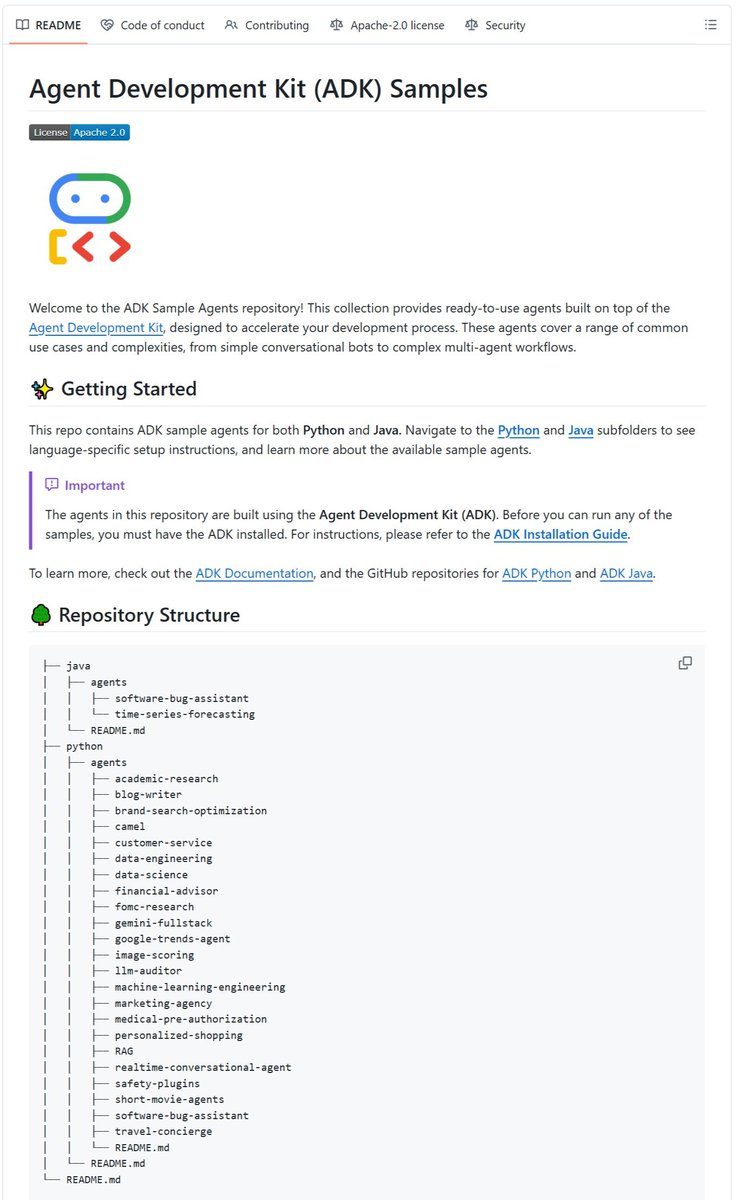
Google literally just made the best way to create AI Agents
New details on multiple state and criminal actors now exploiting React2Shell. cloud.google.com/blog/topics/th…
cloud.google.com
Multiple Threat Actors Exploit React2Shell (CVE-2025-55182) | Google Cloud Blog
Widespread exploitation of the React2Shell vulnerability (CVE-2025-55182) by multiple threat actors, including China and cyber criminals.
AI and ML Papers Explained (HUGE list): github.com/dair-ai/ML-Pap… Compiled by @omarsar0 @dair_ai #ML #MachineLearning #DataScience #Algorithms #NeuralNetworks #DeepLearning #Mathematics
Just watched @datadoghq talk at @firstdotorg CTI on "Automating Cyber Threat Intelligence" youtube.com/watch?v=t8M3VY…. Great tips on streamlining vulnerability classification, gather abuse data, and report it to customers. Also check HASH github.com/datadog/HASH #cti #automation
github.com
GitHub - DataDog/HASH: HASH (HTTP Agnostic Software Honeypot)
HASH (HTTP Agnostic Software Honeypot). Contribute to DataDog/HASH development by creating an account on GitHub.
The entire 3rd-edition of @rossjanderson's "Security Engineering" is available free as PDFs now! cl.cam.ac.uk/archive/rja14/…
Detecting and mitigating Active Directory compromises cyber.gov.au/resources-busi…
Further enhance phishing investigations with @MISPProject playbooks! 'URL Remediation' streamlines finding abuse contacts via AbuseFinder, @lookyloo_app , @FIRSTdotOrg , and RDAP, while reporting malicious sites to MSRC, Google Safe Browsing and Netcraft. github.com/MISP/misp-play…




🚨 New to security & Splunk SPL? We've got you covered! 🚀👩💻🕵️♂️ Here’s how to jumpstart your journey: 🎮 Boss of the SOC (BOTS): Play hands-on scenarios to sharpen your skills! 🕹️ Start here: bots.splunk.com. Bonus: Check out Chris Long's blogs (clo.ng/blog/bots-part… )…
CTI Threat Quantification & Prioritization 101 - A Practical Guide to Building (& Maintaining) Your Cyber Threat Profile (From 2023 FIRST CTI Conference): first.org/resources/pape…
Great repository of MISP playbooks for common SOC, CSIRT, CTI use-cases: github.com/MISP/misp-play…
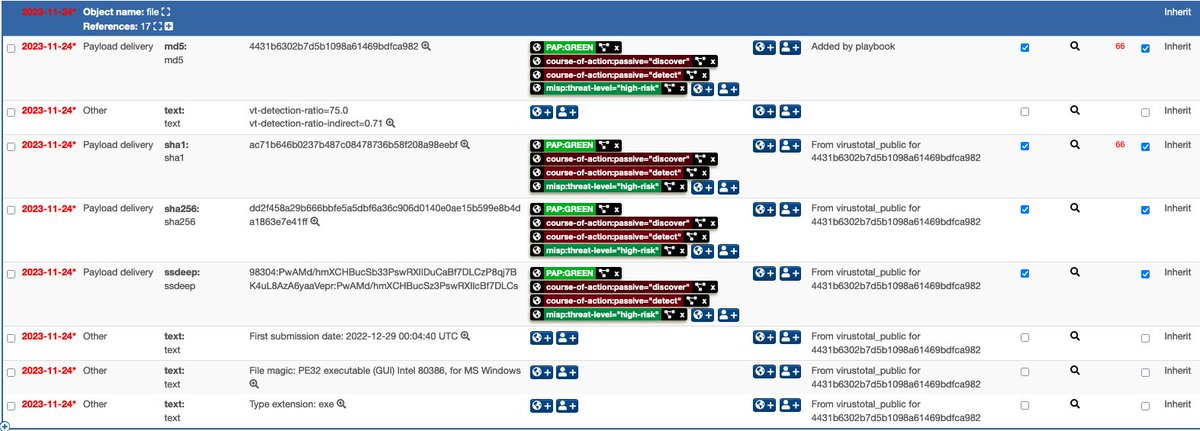
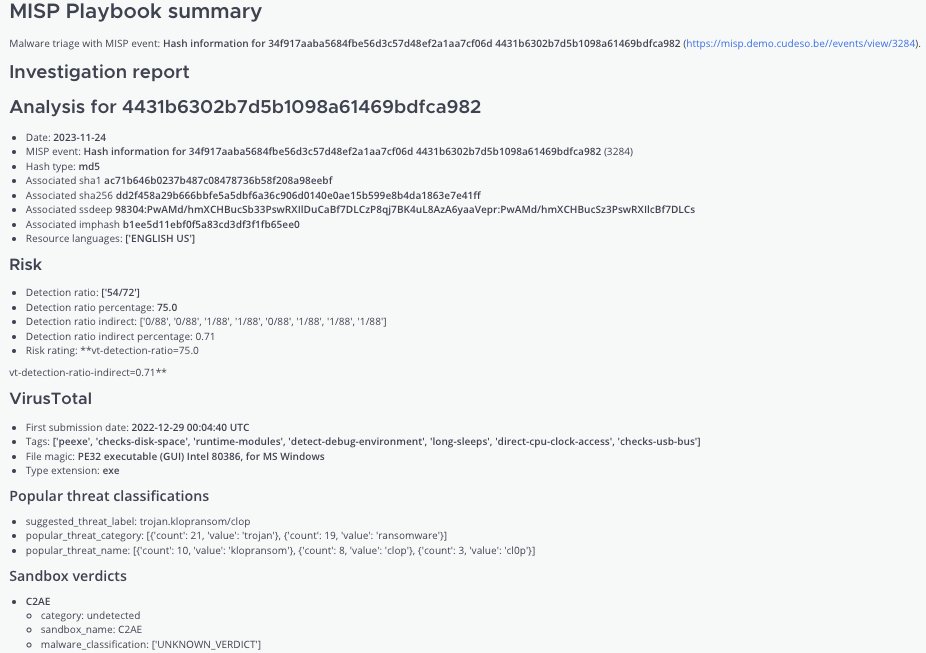
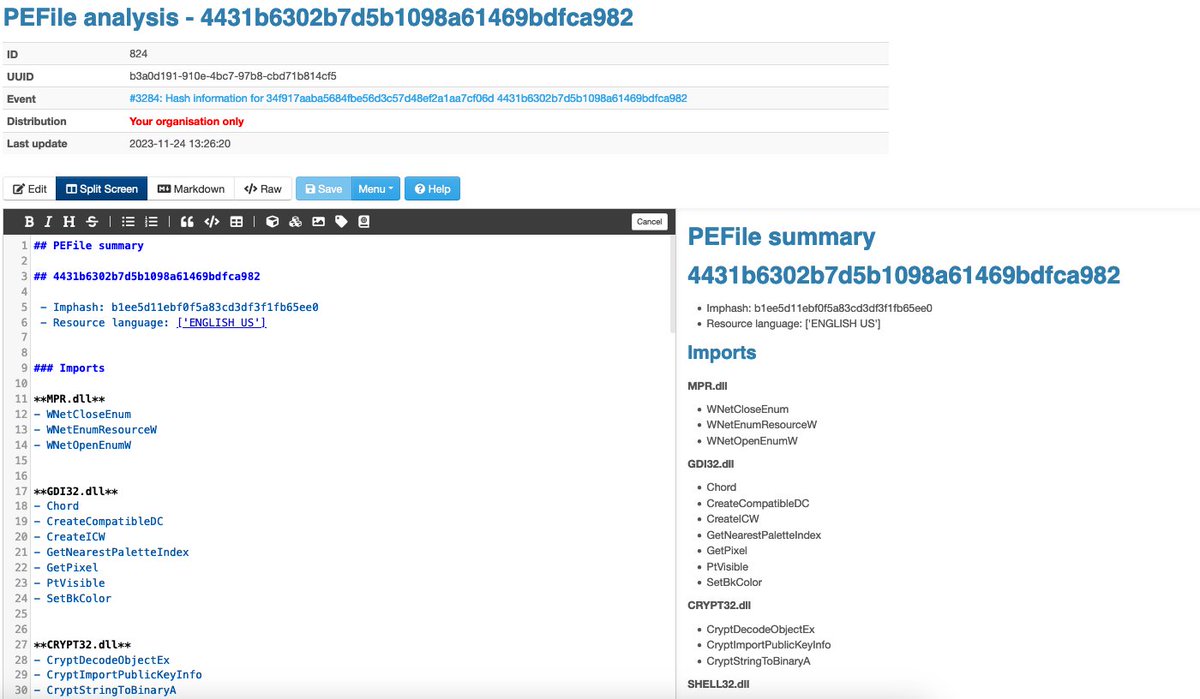
Concluding the series of @MISPProject playbooks for malware analysis, "Query hash information" helps discovering which malware is associated with a hash. You get a MISP report on the hash investigation, peinfo details and a summary is sent to Mattermost. github.com/MISP/misp-play…

Just released my latest analysis of Defender for Endpoint features by OS. Targeted at folks deploying MDE to understand what can be used and where; what capabilities you might have missed; or potential customers evaluating options. Blog + download: campbell.scot/mde-comparison…

This is an important one, so allow me quote it. 🔥 Primary reason: most believe they need to achieve EVENT normalization (ex.: Splunk's CIM) before actually crafting the matching queries. Secondary reason: no clearly defined CTI framework/workflow and IOC lifecycle management.
Can you tell why this is so difficult or why so many fail at this?
Applied attack scenarios against SCM systems and possible mitigations by IBM X-Force. "Controlling the Source: Abusing Source Code Management Systems" ibm.com/downloads/cas/… #DevSecOps #redteam
Microsoft is tracking threats taking advantage of the CVE-2021-44228 remote code execution (RCE) vulnerability in Apache Log4j 2 ("Log4Shell"). Get technical info and guidance for preventing, detecting, and hunting for related attacks: msft.it/6019ZENIW
Oh my god, this stuff is absolutely brutal. RCE on Apple, Tencent, Steam, Twitter. github.com/YfryTchsGD/Log…
United States Trends
- 1. Insurrection Act N/A
- 2. #BTS_ARIRANG N/A
- 3. Kuminga N/A
- 4. Lara Croft N/A
- 5. Arrest Tim Walz N/A
- 6. Giants N/A
- 7. InfoFi N/A
- 8. Clayton Kershaw N/A
- 9. Apple Music N/A
- 10. #thursdayvibes N/A
- 11. Mahmoud Khalil N/A
- 12. BTS IS COMING N/A
- 13. #BuschColdAndSmoothSweeps N/A
- 14. The Great Healthcare Plan N/A
- 15. #BTSComeback2026 N/A
- 16. #thursdaymotivation N/A
- 17. Tomb Raider N/A
- 18. Good Thursday N/A
- 19. Happy Founders N/A
- 20. DePaul N/A
Something went wrong.
Something went wrong.