Adam Mariš 🇺🇦🇵🇸
@neuralhax
Interested in hacking, red teaming, exploits and coffee. Opinions are anything but mine.
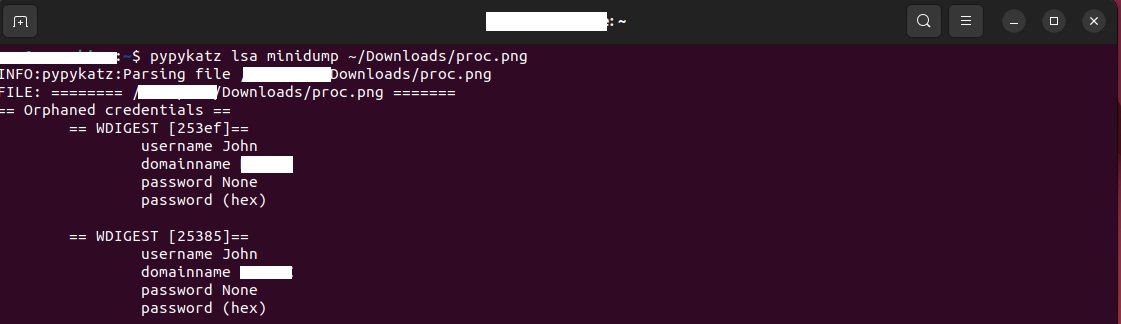
I published my first blog post, the topic is about novel technique to enable WDigest in order to dump plaintext passwords from LSASS, while bypassing existing detections. Hope some of you will find it useful! neuralhax.github.io/wdigest-diggin…
Credential Guard was supposed to end credential dumping. It didn't. @bytewreck just dropped a new blog post detailing techniques for extracting credentials on fully patched Windows 11 & Server 2025 with modern protections enabled. Read for more ⤵️ ghst.ly/4qtl2rm
Lateral movement getting blocked by traditional methods? @werdhaihai just dropped research on a new lateral movement technique using Windows Installer Custom Action Server, complete with working BOF code. ghst.ly/4pN03PG
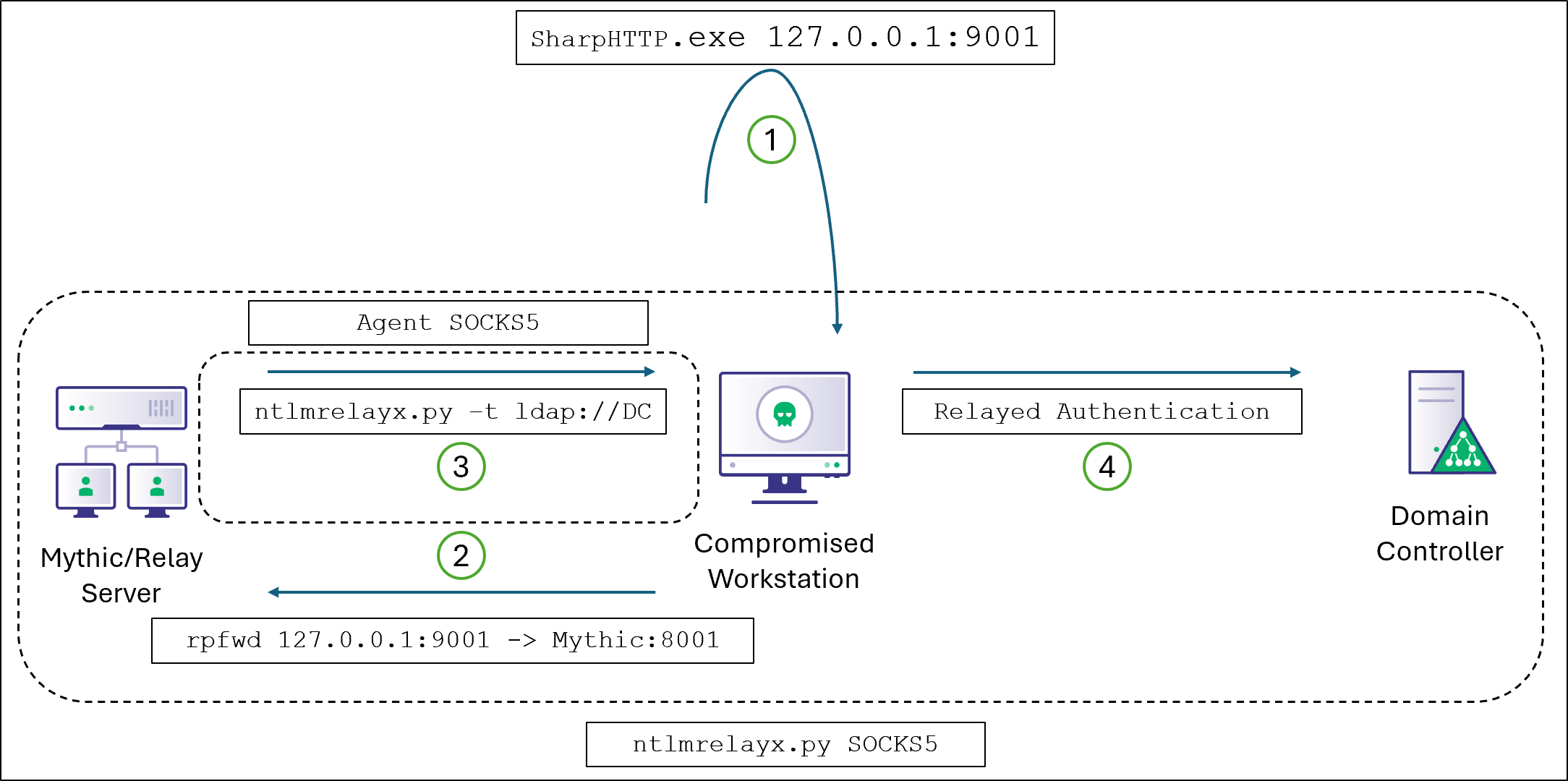
Trying to fly under EDR's radar? @_logangoins explains how to use HTTP-to-LDAP relay attacks to execute tooling completely off-host through the C2 payload context. Perfect for when you need LDAP access but want to avoid being caught stealing creds. ghst.ly/41mjMv7
We can exploit the #securityvulnerability of Windows Error Reporting to put EDRs and #antimalware into a coma-like state. By using the EDR-Freeze #redteam tool: Github: TwoSevenOneT/EDR-Freeze

I've been researching the Microsoft cloud for almost 7 years now. A few months ago that research resulted in the most impactful vulnerability I will probably ever find: a token validation flaw allowing me to get Global Admin in any Entra ID tenant. Blog: dirkjanm.io/obtaining-glob…
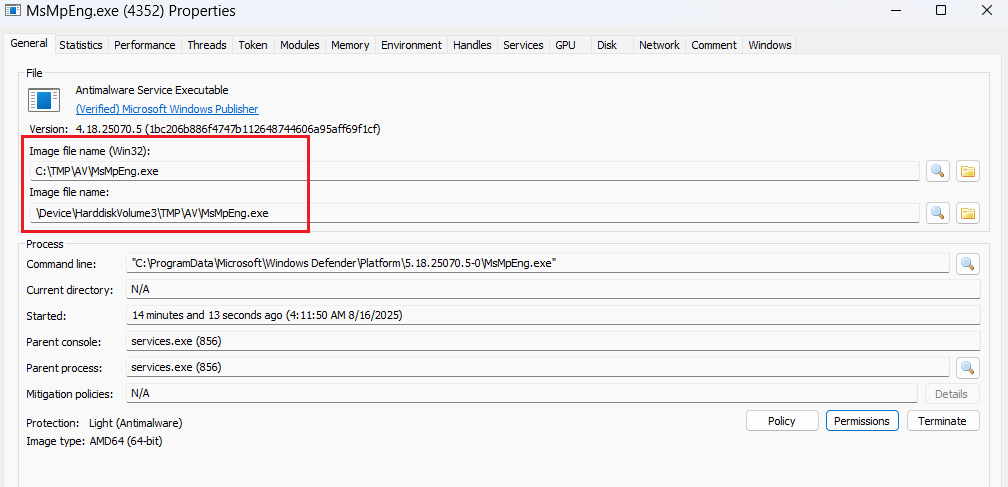
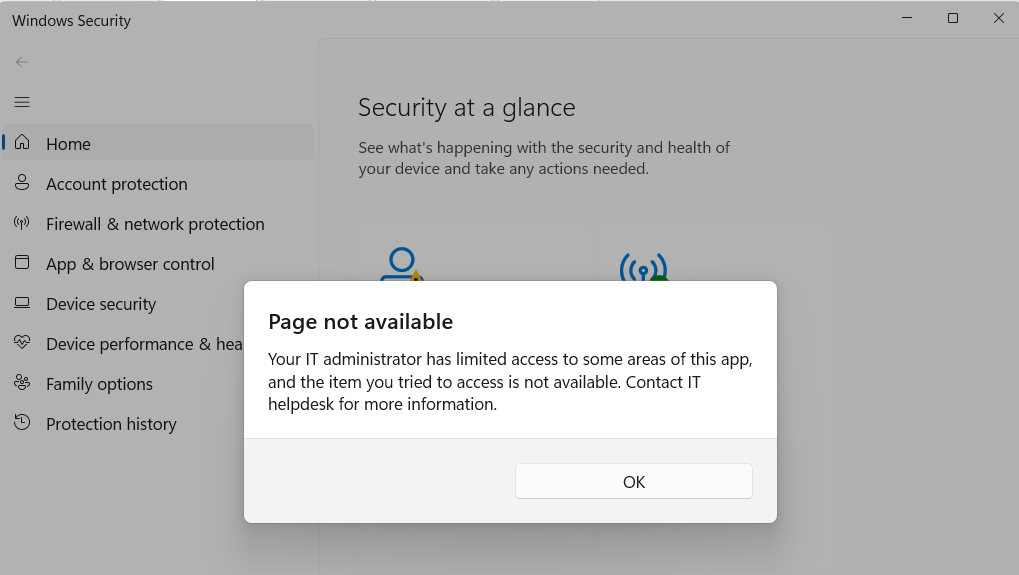
#redteam You can exploit the update functionality vulnerability of #Windows Defender to move its executable folder to a location of your choosing. After that, you can use DLL Sideloading for persistence, inject code, or simply disable it... #blueteam
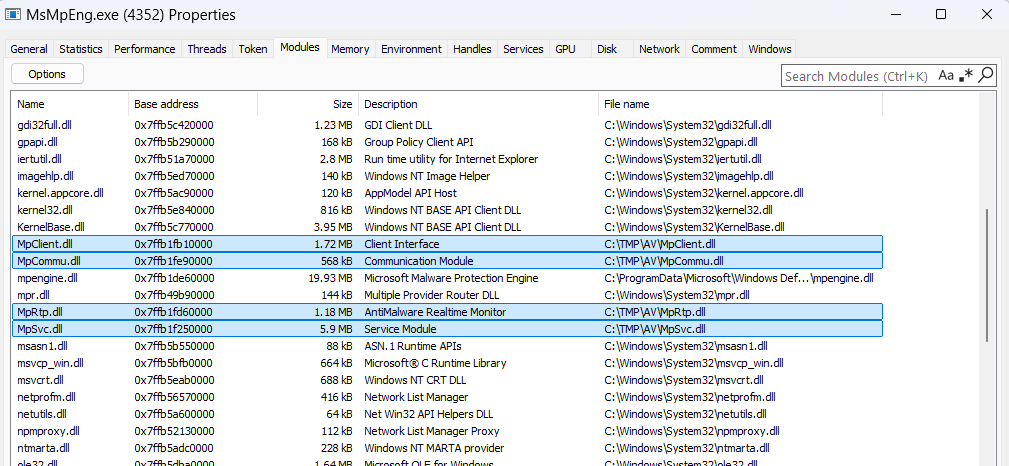
#redteam Now, you can dump the #Windows password from the LSASS process with help from the past: WerFaultSecure.exe Github: 2x7EQ13/WSASS Experimental version: Windows 11 24H2 #Blueteam


“They” weren’t responsible. An individual did this, not whatever group you want to blame, same thing as “they” did not kill those Minnesota House Democrats, an individual did. If a “they” is responsible, I’m not sure how killing a social media influencer is more of a wake up call…
They killed a 31 year old father of two whose only crime was to go to university campuses and engage in good faith with people who disagreed with him. If this isn’t a wake up call then we’re never going to wake up.
Exciting times. I'm publishing Dittobytes today after presenting it at @OrangeCon_nl ! Dittobytes is a true metamorphic cross-compiler aimed at evasion. Use Dittobytes to compile your malware. Each compilation produces unique, functional shellcode. github.com/tijme/dittobyt…
gpoParser, which I presented at #leHACK2025 and #DEFCON, is available here: github.com/synacktiv/gpoP… It is a specialized utility designed to enumerate Group Policy Objects (GPOs) and identify potential security misconfigurations.
🚨 I am publishing my research on the File System API. FileJacking might used to establish Initial Access. Key points: - File smuggling via File System API - Backdooring files directly from a browser - Reading / creating folders and files from a browser print3m.github.io/blog/filejacki…
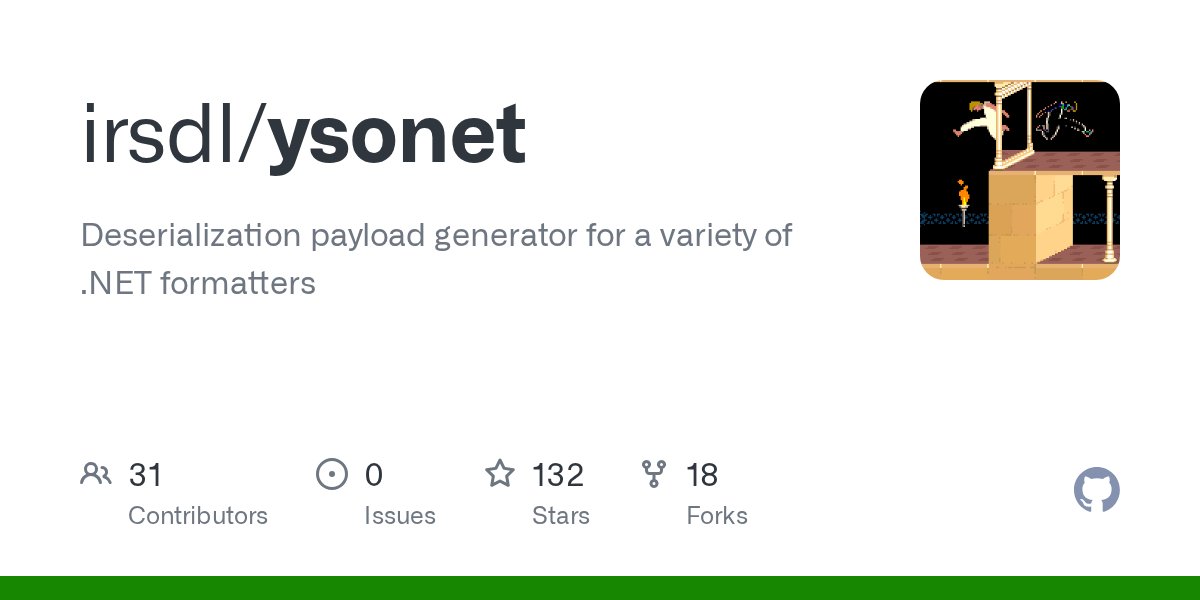
A great #SharePoint vuln by @chudyPB especially when paired with the ToolShell auth bypass by @_l0gg. CVE-2024-38018 highlights: - Implemented in ysonet.net - With the right gadget, this 0-day lands on fully-patched SP13 / SP10- and both are EoL, so no fix is…
Btw, I described my SharePoint CVE-2024-38018 at a PL conference last year, and they've recently uploaded it. I guess you don't know Polish, but slides are in English 😅 RCE part starts at 30:30 youtu.be/a2_onBMte8I?si…

youtube.com
YouTube
Piotr Bazydło: Szukanie podatności w Microsoft SharePoint: Case Study...
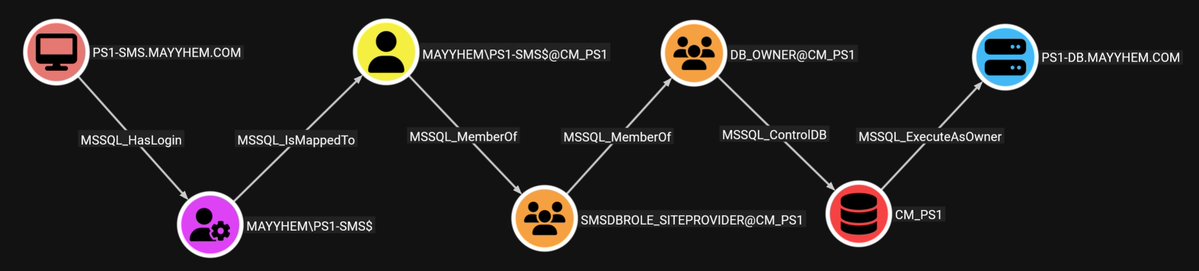
I'm SO hyped to finally make MSSQLHound public! It's a new BloodHound collector that adds 37 new edges and 7 new nodes for MSSQL attack paths using the new OpenGraph feature for 8.0!. Let me know what you find with it! - github.com/SpecterOps/MSS… - specterops.io/blog/2025/07/2…
It's been almost a year since my last blog... So, here is a new one: Extending AD CS attack surface to the cloud with Intune certificates. Also includes ESC1 over Intune (in some cases). dirkjanm.io/extending-ad-c… Oh, and a new tool for SCEP: github.com/dirkjanm/scepr…
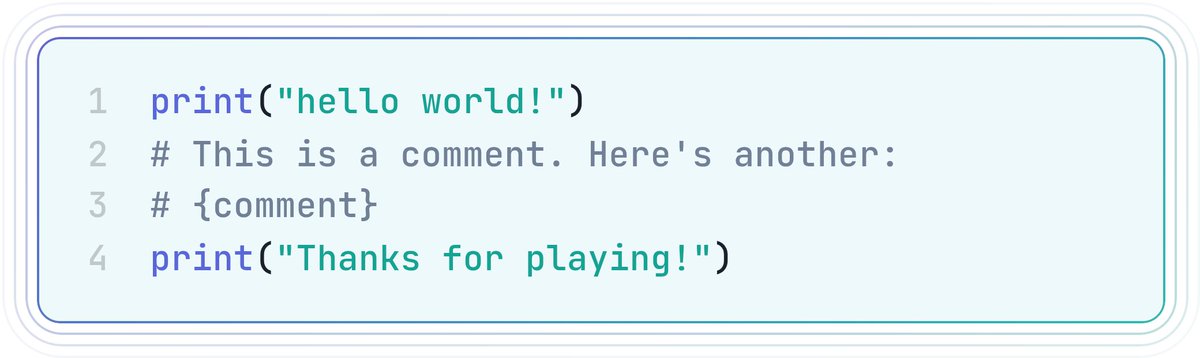
Can you execute arbitrary Python code from only a comment? This was the premise of a recent CTF challenge, which I solved after diving into the CPython source code with the help of @HacktronAI (after a long night chasing a dead end, customising a few Hacktron agents helped me to…
Fidèle à son engagement historique pour une paix juste et durable au Proche-Orient, j’ai décidé que la France reconnaîtra l’État de Palestine. J’en ferai l’annonce solennelle à l’Assemblée générale des Nations unies, au mois de septembre prochain.…


To trigger local SYSTEM authentication for relaying to ADCS or LDAP for LPE you would usually need the printer service or EFS service to be enabled (printerbug/petitpotam). Here is an alternative without this requirement 🤠 github.com/rtecCyberSec/R…

Inaction & silence are complicities. Under our watch, #Gaza has become the graveyard of children & starving people. No way out. Their choice is between 2 deaths: starvation or being shoot at. The most cruel & machiavellian scheme to kill, in total impunity. Our norms & values…
Introducing Havoc Professional: A Lethal Presence We’re excited to share a first look at Havoc Professional, a next-generation, highly modular Command and Control framework, and Kaine-kit our fully Position Independent Code agent engineered for stealth! infinitycurve.org/blog/introduct…
The Blog post about "Revisiting Cross Session Activation attacks" is now also public. Lateral Movement with code execution in the context of an active session? 😎 Here you go: r-tec.net/r-tec-blog-rev…
r-tec.net
r-tec Blog | Revisiting Cross Session Activation Attacks
This blog post revisits Cross Session Activation attacks
United States 趨勢
- 1. #HardRockBet 3,803 posts
- 2. RIP Beef N/A
- 3. SNAP 631K posts
- 4. #IDontWantToOverreactBUT 4,270 posts
- 5. Jamaica 87K posts
- 6. #MondayMotivation 41K posts
- 7. Roger McCreary N/A
- 8. MRIs 2,261 posts
- 9. #ChelleyxTrueReligion 2,317 posts
- 10. Victory Monday 3,868 posts
- 11. jungkook 365K posts
- 12. #MondayVibes 4,058 posts
- 13. Berghain 37.7K posts
- 14. $QCOM 15.5K posts
- 15. Chapman 3,674 posts
- 16. John Dickerson N/A
- 17. WINWIN 27.7K posts
- 18. Melissa 123K posts
- 19. Good Monday 54.9K posts
- 20. Sports Equinox 3,769 posts
Something went wrong.
Something went wrong.