nonetype
@nonetype_pwn
Wonyoung Jung / Security researcher @78_lab , Master at KAIST Hacking Lab: https://notes.nonetype.kr/About+me
You might like
Windows Remote Desktop Licensing Service Pre-auth RCE (CVE-2024-38077) Analysis blog.78researchlab.com/2b2db461-3e5b-…
[Research] Bypassing Windows Kernel Mitigations: Part0 - Deep Dive into KASLR Leaks Restriction hackyboiz.github.io/2025/04/13/l0c… In this post, we’ll take a closer look at the new KASLR-related mitigation introduced in Windows 11 and Windows Server 24H2, and explore a novel method for…
![hackyboiz's tweet image. [Research] Bypassing Windows Kernel Mitigations: Part0 - Deep Dive into KASLR Leaks Restriction
hackyboiz.github.io/2025/04/13/l0c…
In this post, we’ll take a closer look at the new KASLR-related mitigation introduced in Windows 11 and Windows Server 24H2, and explore a novel method for…](https://pbs.twimg.com/media/Goa1wLHWwAARmZs.jpg)
My writeup for CVE-2024-7971. Just a POC. Let me know if u have any questions. github.com/mistymntncop/C…
I have recently been in the V8 vulnerability research/exploitation topic and in this post I will briefly talk about the key points at the very start of the study:
Hey there, Finally published the article on the exploit for CVE-2025-21333-POC exploit. Here the link to the article: medium.com/@ale18109800/c…
I ran probably the largest office fuzzing program in the world at one point We had 128 IBM blade systems fuzzing concurrently + office UI analysis @ 25k fuzzing attempts a minute, with crash analysis + crash confirmation + rewind + automated variation + user interaction…
Write-up of my v8 bug: Critical type confusion in V8's Turboshaft compiler allowed stale pointers to bypass GC, leading to exploitable memory corruption. Full details + PoC: bushido-sec.com/index.php/2025…
bushido-sec.com
RESEARCH - CVE-2024-6773 - Type confusion in v8 - Bushido Security
V8 Turboshaft Load Elimination Type Confusion Vulnerability (CVE-2024-6773)Exploitable Memory Corruption via Garbage Collection Race Condition Executive Summary A critical type confusion vulnerabil...
The most elegant V8 Wasm Turboshaft typer exploit that I've reported. This primitive converts **any** Wasm type confusion in **any type hierarchy** into fully controlled arbitrary type confusion - e.g. what happens if you type `null : ref extern`? RCE :) crbug.com/372269618
A brief JavascriptCore RCE story by @lanleft_ and An Nguyễn qriousec.github.io/post/jsc-unini…
Sharing slides for another #blackhat EU 2024 talk of us: (Enhancing Automatic Vulnerability Discovery for Windows RPC/COM in New Ways) github.com/edwardzpeng/pr…
Sharing our slides for #Blackhat EU 2024: Diving into Spooler: Discovering LPE and RCE Vulnerabilities in Windows Printer Driver github.com/edwardzpeng/pr…
This new Project Zero blog post is sick. It offers a glimpse into how folks do UAF in the "real world". (i.e. in the wild) You have to be smart about what to spray, etc. especially when you don't have a leak
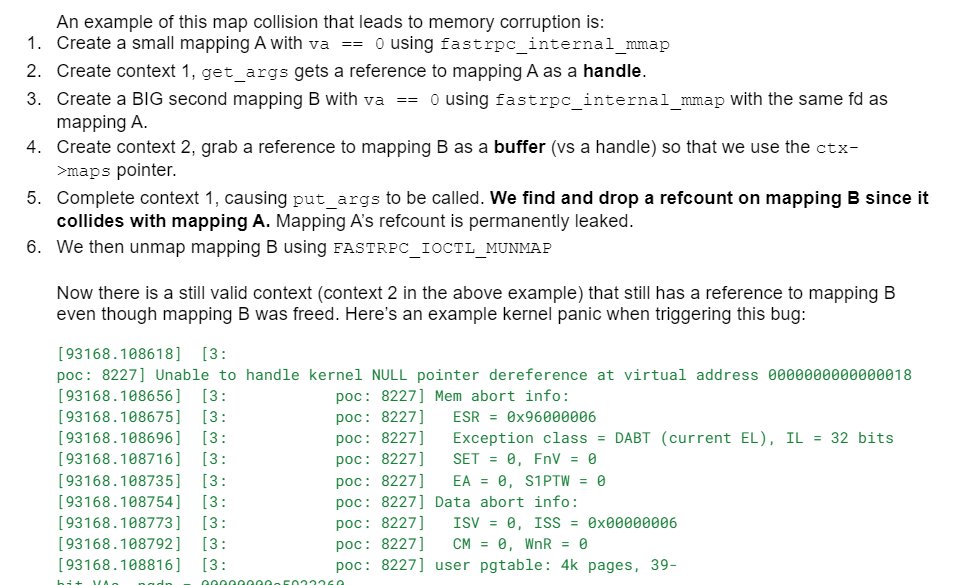
Vulnerability research may feel directionless if you haven't yet worked out metaskill of strategy crafting, particularly scope narrowing. To deal with that, you may use existing bugs to serve as a glorified dice. For example, suppose there is an integer overflow in a regexp
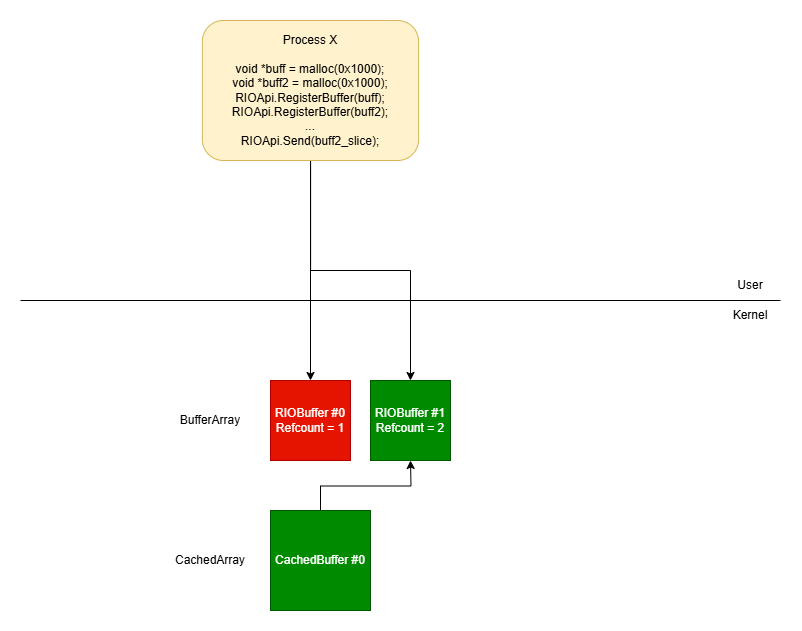
Windows Sockets: From Registered I/O to SYSTEM Privileges blog.exodusintel.com/2024/12/02/win…
New blog post about OSS-Fuzz AI-powered fuzzing is live! We talk about what went into making LLMs work well enough for this use case to find 26 new vulnerabilities (including a CVE in OpenSSL), as well as what else we have planned to make this better. security.googleblog.com/2024/11/leveli…
My sandbox bypass technique is now visible issues.chromium.org/issues/3383813…
In our new article, we sat down with one of our SSD Labs researchers to discuss how he found a critical vulnerability in Windows. Learn about the challenges, breakthroughs, and techniques behind a security researcher’s process: medium.com/ssd-secure-dis…
To pwners and reversers: Have you tried my GEF fork? Features: - Kernel commands (without "vmlinux with symbols"; for qemu-system) - More architectures support (for qemu-user) - Minor heap allocator dumper And many more! Bugs? Please report them:) Enjoy! github.com/bata24/gef
Excited to share my latest blog post: "Breaking Control Flow Flattening: A Deep Technical Analysis" I showcase usage of formal proofs and graph theory to automate CFF deobfuscation, among other things ! Might make it a talk...? 👀 zerotistic.blog/posts/cff-remo…
Another big step towards becoming a security boundary: today we’re expanding the VRP for the V8 Sandbox * No longer limited to d8 * Rewards for controlled writes increased to $20k * Any memory corruption outside the sandbox now in scope bughunters.google.com/about/rules/ch… Happy hacking!
United States Trends
- 1. Sonny Gray 6,756 posts
- 2. Dick Fitts N/A
- 3. Red Sox 6,782 posts
- 4. Godzilla 19.8K posts
- 5. #yummymeets N/A
- 6. National Treasure 5,038 posts
- 7. Clarke 6,257 posts
- 8. Rush Hour 4 5,183 posts
- 9. Raising Arizona N/A
- 10. Gone in 60 1,794 posts
- 11. Giolito N/A
- 12. Happy Thanksgiving 20.9K posts
- 13. #GMMTV2026 4.2M posts
- 14. NextNRG Inc N/A
- 15. Thankful 50.5K posts
- 16. Lord of War 1,290 posts
- 17. Academic All-District N/A
- 18. Breslow N/A
- 19. Chuck and Nancy 4,861 posts
- 20. Brett Ratner 1,708 posts
Something went wrong.
Something went wrong.