You might like
hardened_malloc version 13 released: github.com/GrapheneOS/har… See the linked release notes for a summary of the improvements over the previous release and a link to the full changelog. Forum discussion thread: discuss.grapheneos.org/d/16445-harden… This is a standalone release for use…
github.com
Release 13 · GrapheneOS/hardened_malloc
Changes in version 13: add support for ARM hardware memory tagging (MTE) which has been shipped in production on GrapheneOS for the past year (see the README section on memory tagging for details)...
Due to the current events I'm selling my #hexacon2024 ticket. If anyone wants it please DM me.
backdoor in upstream xz/liblzma leading to ssh server compromise openwall.com/lists/oss-secu…
Finally there is a PCILeech Thunderbolt device! ZDMA offers much improved PCILeech DMA performance 😈 github.com/ufrisk/pcileec…

The best of bests security vulnerability report in 2023 which is the solid evidence about we're all trapped in 90s!
Looney Tunables: Local Privilege Escalation in the glibc's ld.so (CVE-2023-4911) qualys.com/2023/10/03/cve…
Introducing deep-TEMPEST: a deep learning method that recovers great quality images from unintentional electromagnetic emanations of HDMI. Great work (in progress) by E. Martinez, S. Fernandez and G. Varela 💪💪 (co-mentored with @muse_pablo). Expect more news in the next weeks.
Van Eck phreaking... It ACTUALLY works?!?!
Introducing deep-TEMPEST: a deep learning method that recovers great quality images from unintentional electromagnetic emanations of HDMI. Great work (in progress) by E. Martinez, S. Fernandez and G. Varela 💪💪 (co-mentored with @muse_pablo). Expect more news in the next weeks.
Dirty Pagetable: A Novel Exploitation Technique To Rule Linux Kernel An article by @NVamous about the Dirty Pagetable exploitation technique. yanglingxi1993.github.io/dirty_pagetabl…
Nice blog post on exploiting VirtualBox on Windows (CVE-2023-21987 and CVE-2023-21991) qriousec.github.io/post/vbox-pwn2… #virtualbox #infosec




Sekiryu V0.0.2 Is out! A Comprehensive toolkit to pilot Ghidra Headless, including some nice features such as vulnerability hunting, BinExport, etc. It allows users to load their own script and even interact with the "API" More => github.com/20urc3/Sekiryu
github.com
GitHub - 20urc3/Sekiryu: Comprehensive toolkit for Ghidra headless.
Comprehensive toolkit for Ghidra headless. Contribute to 20urc3/Sekiryu development by creating an account on GitHub.
#FF @hashcat @BSidesLV @sk3rts @IonTodd @S1ckB0y1337 @PasswordVillage @thorsheim @BSidesAth @secjay @Daemontamer @jpgoldberg @homakov @Xanadrel @Chick3nman512 @cantcomputer @unix_ninja @nickvourd @noptrix @hops_ch @jmgosney @dcuthbert @mubix @pgt_r2ursystem
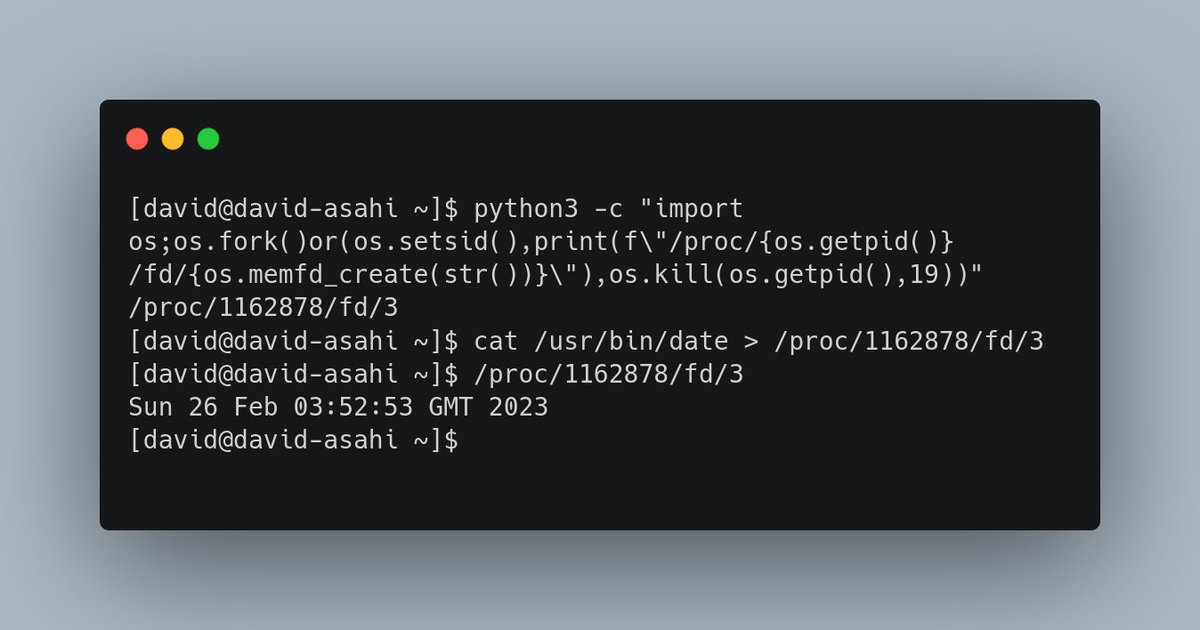
python memfd_create() oneliner: python3 -c "import os;os.fork()or(os.setsid(),print(f\"/proc/{os.getpid()}/fd/{os.memfd_create(str())}\"),os.kill(os.getpid(),19))" This prints the path of a memfd, which you can use to do whatever you want (like fileless ELF execution!)
📣 Announcing the tmp.0ut Volume 3 Call For Papers! For information on submission guidelines and ways to contact us, visit the CFP page: tmpout.sh/blog/vol3-cfp.…

The time finally arrived! Reach out to us to contribute!
📣 Announcing the tmp.0ut Volume 3 Call For Papers! For information on submission guidelines and ways to contact us, visit the CFP page: tmpout.sh/blog/vol3-cfp.…

Of course the master heap #xdev @qualys managed to achieve significant progress in #exploiting the recent double-free #vulnerability in #OpenSSH server 9.1 (CVE-2023-25136) 💚 seclists.org/oss-sec/2023/q…
👏New tool from @g3rzi and @CyberArkLabs!👏 PipeViewer - A GUI tool for viewing Windows Named Pipes and searching for insecure permissions. github.com/cyberark/PipeV…
United States Trends
- 1. Penn State 23.1K posts
- 2. Indiana 38.6K posts
- 3. Mendoza 20.2K posts
- 4. Gus Johnson 6,692 posts
- 5. #UFCVegas111 5,050 posts
- 6. #iufb 4,197 posts
- 7. Sayin 68.9K posts
- 8. Omar Cooper 9,487 posts
- 9. Estevao 38.6K posts
- 10. Iowa 19.5K posts
- 11. Josh Hokit N/A
- 12. Sunderland 154K posts
- 13. Mizzou 3,694 posts
- 14. Texas Tech 13.8K posts
- 15. Kirby Moore N/A
- 16. Jim Knowles N/A
- 17. James Franklin 8,713 posts
- 18. Happy Valley 1,905 posts
- 19. Oregon 33.7K posts
- 20. Carter Smith N/A
You might like
-
 xer0dayz
xer0dayz
@xer0dayz -
 ς๏гєɭคภς0๔3г ([email protected])
ς๏гєɭคภς0๔3г ([email protected])
@corelanc0d3r -
 Chris Magistrado
Chris Magistrado
@REal0day -
 b1ack0wl
b1ack0wl
@b1ack0wl -
 Spiros Fraganastasis
Spiros Fraganastasis
@m3g9tr0n -
 James Hooker
James Hooker
@g0blinResearch -
 Miroslav Stampar
Miroslav Stampar
@stamparm -
 Luke Rogerson
Luke Rogerson
@NullMode_ -
 yappare
yappare
@yappare -
 Raz0r
Raz0r
@theRaz0r -
 Roman Shafigullin
Roman Shafigullin
@shafigullin -
 RuraPenthe / Dimitri
RuraPenthe / Dimitri
@RuraPenthe0 -
 Vahagn Israelian 🇦🇲
Vahagn Israelian 🇦🇲
@0xKonqi -
 Tatramaco
Tatramaco
@Tatramaco -
 Security Addicted
Security Addicted
@SecurAddicted
Something went wrong.
Something went wrong.