Vulnmod
@pwnderer1
You might like
I got sometime to write a basic x86 debugger. Why? Simply for the fun of ptrace. Features? 1. A dumb length based mutation fuzzer integrated into the debugger itself. 2. Execution trace display at any instance of debugging. Here's a peek into it. asciinema.org/a/Ue8KEpPZcoeH…
asciinema.org
untitled
Recorded by Cyb0rG
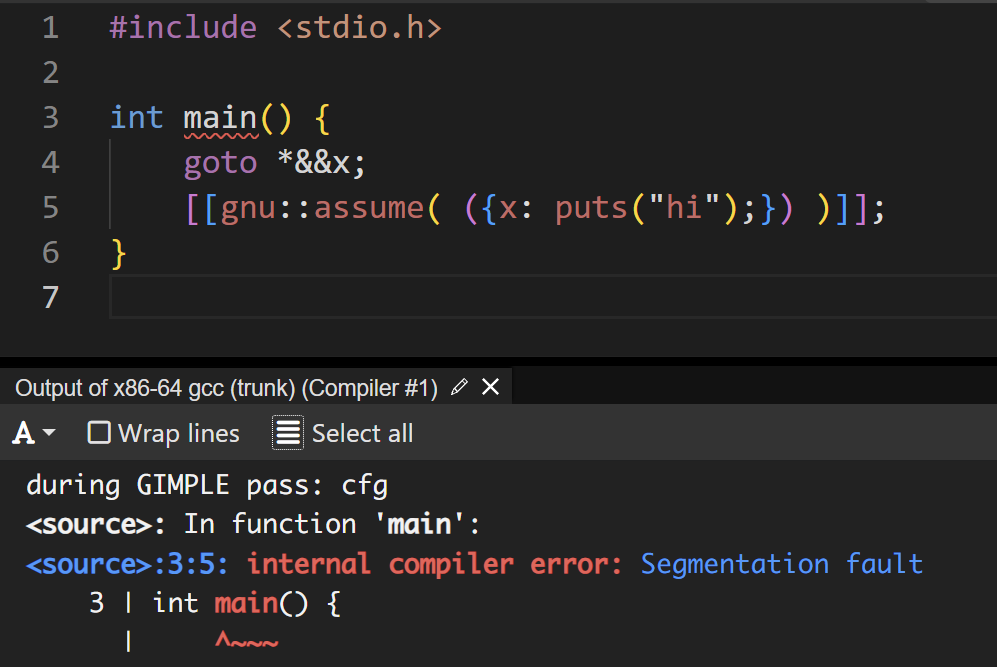
Look GCC, I don't think I'm being unreasonable here
Some IDA MCP servers can be tricked into executing arbitrary code directly from the malware sample
Did you know that pressing CTRL+D in linux terminal is like pressing ENTER? (to some extent, of course) Well, I didn't, so after randomly investigating what CTRL+D actually does, I've decided it's a fun topic to write about: hackarcana.com/article/ctrl-d…
Making memcpy(NULL, NULL, 0) well-defined. @nikita_ppv @rhdevelopers developers.redhat.com/articles/2024/…
Always.
Normalize deleting a repo and re-cloning it on the first error. Don’t give in to git bullying.
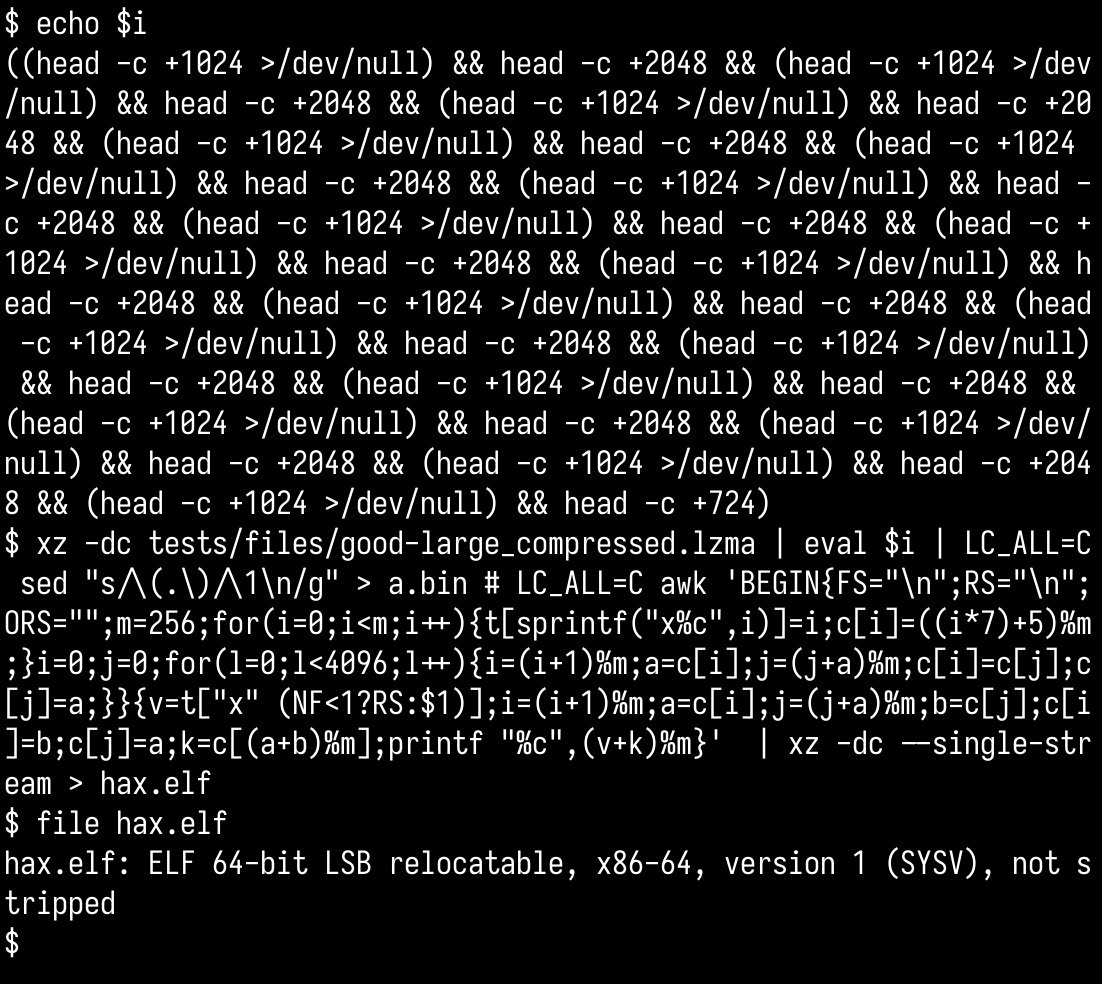
you gotta appreciate the way they shipped the backdoored object file. added some "test" data to the source tree that gets unxz'd and (dd) carved in a specific way, that is fed into a deobfuscator written in.. awk script and the result gets unxz'd again
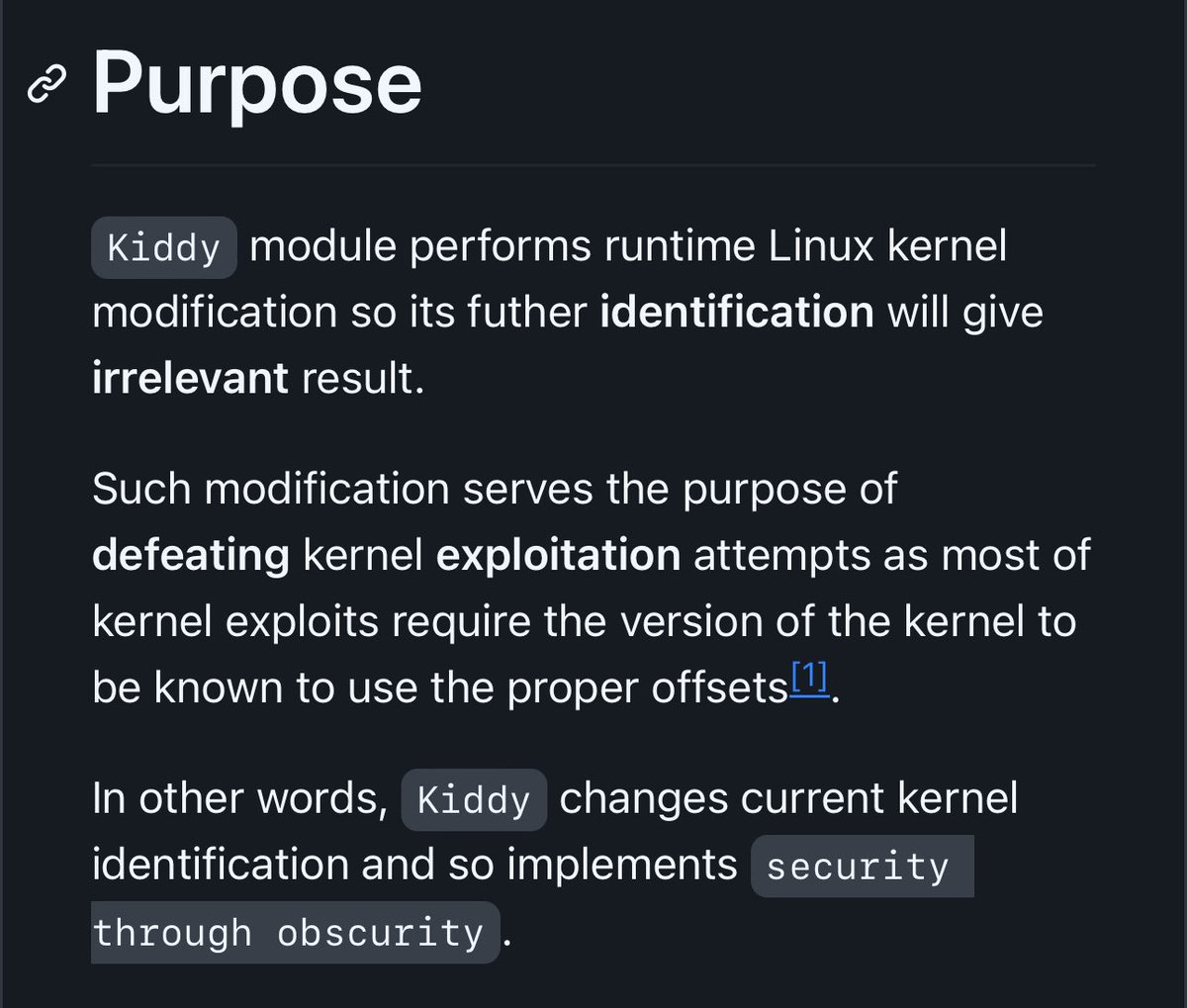
Security through obscurity :)
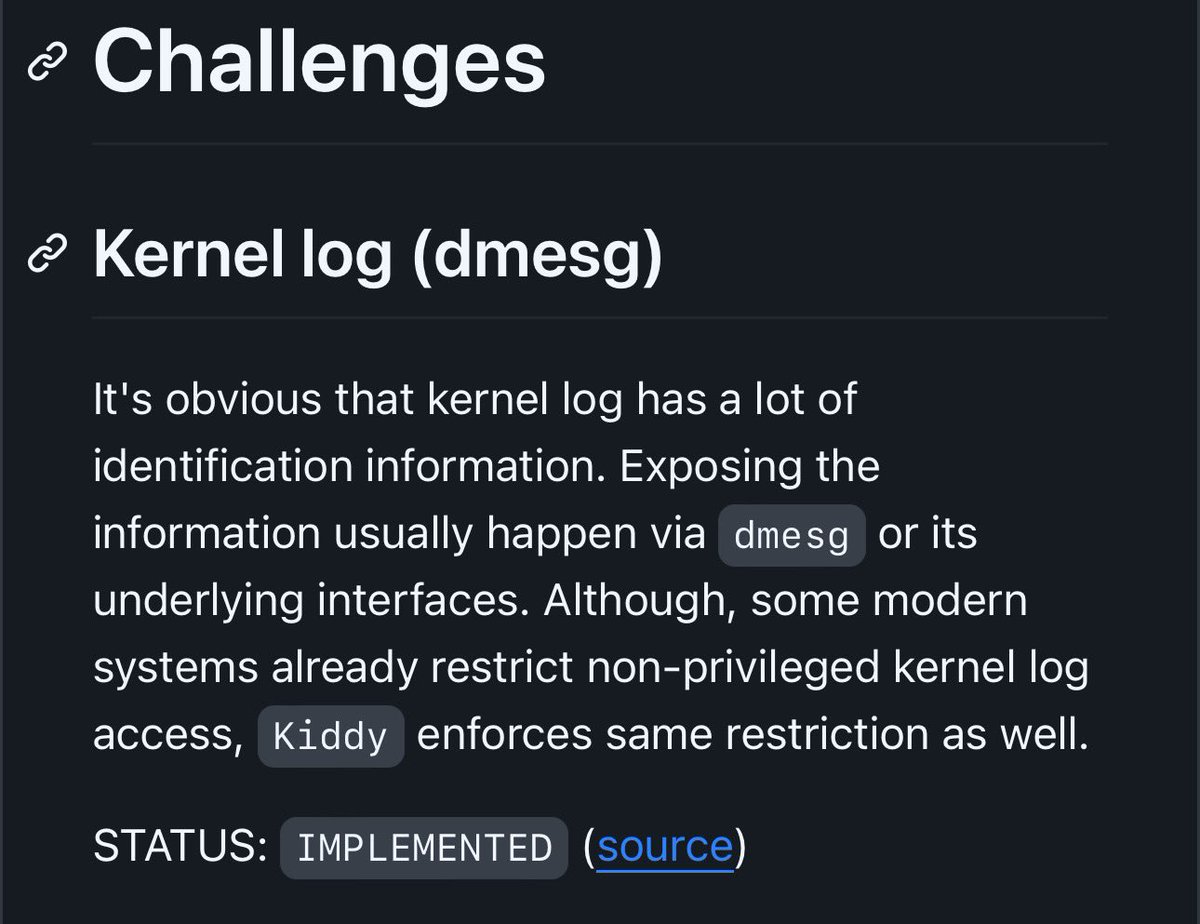
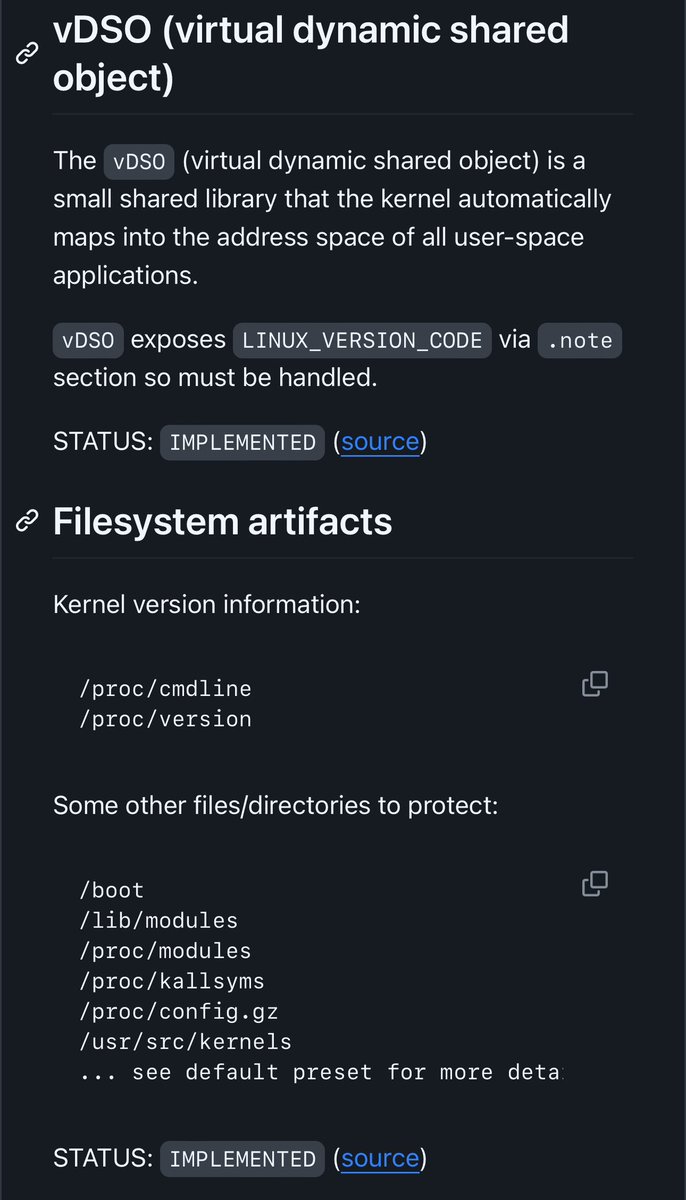
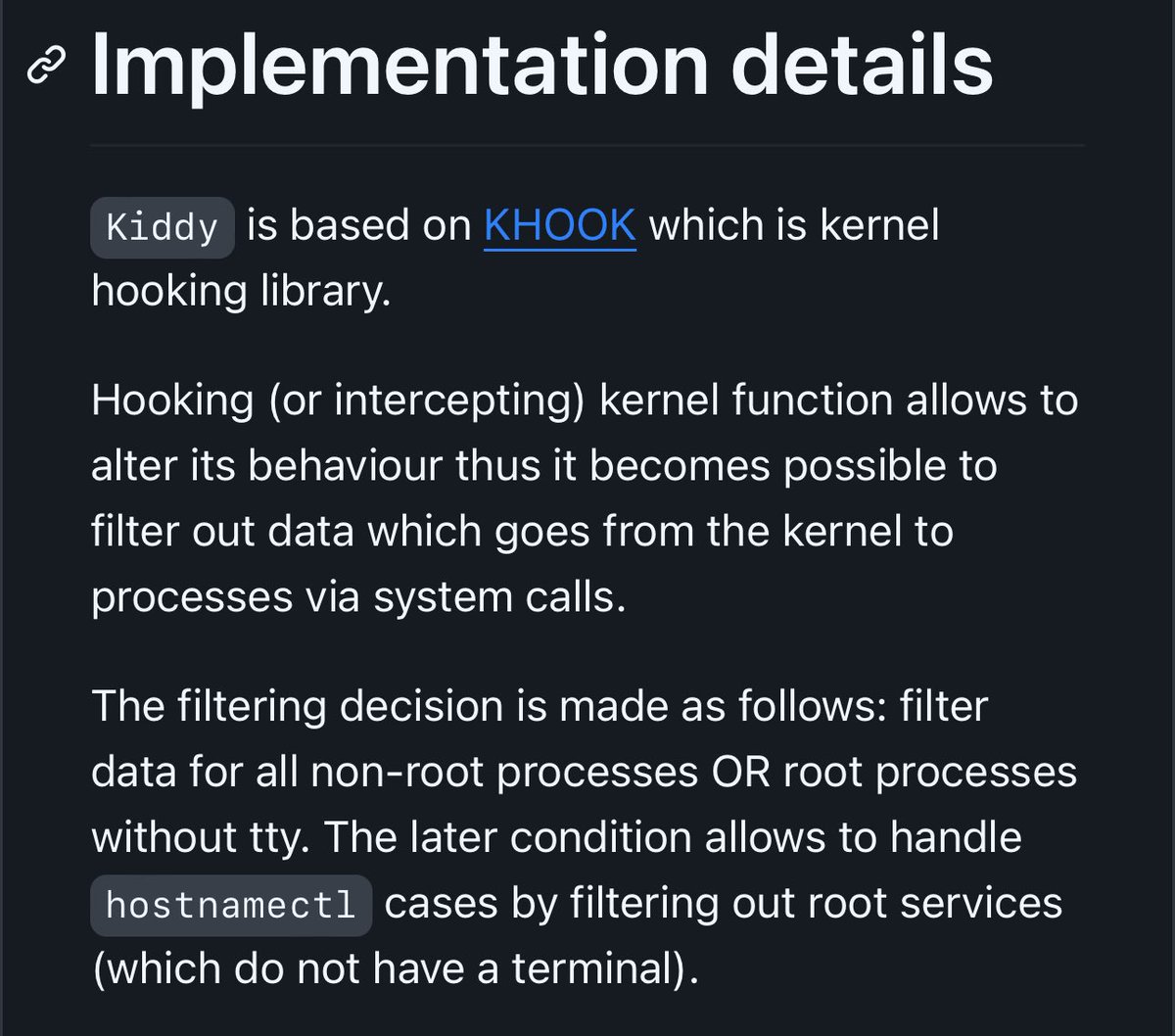
Kiddy - (linux) kernel identity spoofer github.com/milabs/kiddy Kiddy module performs runtime Linux kernel modification so its futher identification will give irrelevant result. Such modification serves the purpose of defeating kernel exploitation attempts as most of kernel…
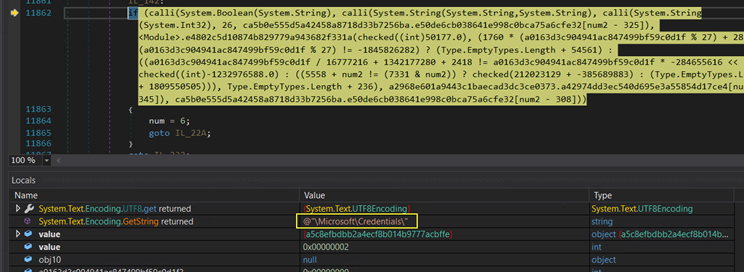
Bugs from the 90s… we all know gets() should never be used. It even says so in the Linux man page. The compiler (gcc for this example) lets you. It does give you a warning though. But scanf* and %s is exactly the same unbounded buffer overflow. But no compiler warning.
Malware Hiding in PDFs : What You Need to Know : mcafee.com/blogs/other-bl…

Rust-based firmware is inherently secure by design. What could possibly go wrong?

when the bug only triggers once in a thousand executions

Apple today announced changes to increase attack surface apple.com/newsroom/2024/…

pretty sure nearly all the success of LLMs at vuln id is due to the benchmark datasets of past vulns. i gave gpt3.5 the vulnerable code from the GHOST writeup by @qualys and it gave the correct result, similar to the report . wow! then i renamed one of the variables "cool_guy"


My personal GPT for offensive security, SecGPT. Been working on it for a while now. I use it like i have a peer in a chair next to me, asking questions to learn and bounce ideas off of. Enjoy: chat.openai.com/g/g-HTsfg2w2z-…
To facilitate reverse-engineering of large programs, vulnerability research and root-cause analysis on iOS, Android, and other major platforms, @myr463 and @Hexabeast released Frinet, a tool combining Frida with an enhanced version of Tenet. synacktiv.com/publications/f…
New write-up on an Intel Ice Lake CPU vulnerability, we can effectively corrupt the RoB with redundant prefixes! 🔥 An updated microcode is available today for all affected products, cloud providers should patch ASAP. lock.cmpxchg8b.com/reptar.html
New Project Zero blogpost by Mark Brand - first mobile device ships with MTE (and how to enable it). "MTE on a production handset for the first time is a big step forward... there's real potential to use this technology to make 0-day harder". googleprojectzero.blogspot.com/2023/11/first-…
the fuzzer development process

I'm excited to announce a new decompilation control flow structuring algorithm, SAILR, which is the first to precisely revert compiler optimizations in decompilation. Find out how in our USENIX 2024 paper: zionbasque.com/files/publicat…. Code, info, and links in the 🧵

United States Trends
- 1. Good Sunday 65.1K posts
- 2. Klay 28.2K posts
- 3. #sundayvibes 5,200 posts
- 4. McLaren 120K posts
- 5. Blessed Sunday 17.7K posts
- 6. #sundaymotivation 3,455 posts
- 7. #FelizCumpleañosNico 4,366 posts
- 8. Beirut 3,668 posts
- 9. #FG3Dライブ 110K posts
- 10. Ja Morant 13.1K posts
- 11. For the Lord 30.6K posts
- 12. Lando 143K posts
- 13. #FelizCumpleañosPresidente 3,820 posts
- 14. Tottenham 47.4K posts
- 15. King of the Universe 2,108 posts
- 16. Piastri 86.3K posts
- 17. South Asia 40.6K posts
- 18. Christ the King 10.7K posts
- 19. Rubio 99.7K posts
- 20. Arsenal 176K posts
Something went wrong.
Something went wrong.