Aaron S
@ragingplatypi
Mobile security, pen tester, and sarcasm supplier (he/him)
You might like
Crowdstrike Analysis: It was a NULL pointer from the memory unsafe C++ language. Since I am a professional C++ programmer, let me decode this stack trace dump for you.

In early 2022, Mandiant detected & responded to an incident where #APT29 successfully phished a European diplomatic entity & ultimately abused the Windows Credential Roaming feature. Read the blog post for more on this research.👇 mndt.info/3FZp7Pk
Did you know that if you go to this link on @YouTube youtube.com/getAccountSwit… you download a file with your users settings? This is being abused by a #Stealer written in Golang, which allows the hijacking of YouTube channels and has apparently not yet been identified (?)🤔


Place your bets
PNG Steganography Hides Backdoor : Malware authors rely on LSB encoding to hide malicious payload in the PNG pixel data, more specifically in LSB of each color channel (Red, Green, Blue, and Alpha). decoded.avast.io/martinchlumeck…


The recording of the webcast I gave yesterday on pentesting AWS is up. If you want to see how lateral movement in the cloud can look check it out: youtube.com/watch?v=fg_hey…

youtube.com
YouTube
Securing AWS Discover Cloud Vulnerabilities via Pentesting Techniques...
HTTP Request Smuggler now has a probe for desync flaws caused by broken header removal operations, like this Akamai exploit. PS you can find the lengthy rambling editions of most of my tweets at @albinowax@infosec.exchange github.com/PortSwigger/ht… medium.com/@jacopotediosi…
What happens when an old satellite is no longer in use but can still broadcast? Some researchers earlier this year found a way to breathe new life into one's "graveyard orbit." (Via @WIRED) trib.al/4QHlIMs
arstechnica.com
Researchers used a decommissioned satellite to broadcast hacker TV
What happens when an old satellite is no longer in use but can still broadcast?
Massive thanks to @IAmMandatory for making XSS Hunter Express, and for making it so easy to set up and use 🤘 github.com/mandatoryprogr…
Microsoft has just released a patch for ZIP MOTW vulnerability assigned as CVE-2022-41091. I am happy to be able to finally drop my bug analysis write-up! 🔥🪲 Enjoy and happy patching! breakdev.org/zip-motw-bug-a…
Welcome to the new AD Mindmap upgrade ! v2022_11 will be dark only (this is too painful to maintain two versions). Thx again to : @Vikingfr and @Sant0rryu for their help 👍 Full quality and zoomable version here : orange-cyberdefense.github.io/ocd-mindmaps/i… Overview :

I found a vulnerability that allowed me to unlock any @Google Pixel phone without knowing the passcode. This may be my most impactful bug so far. Google fixed the issue in the November 5, 2022 security patch. Update your devices! bugs.xdavidhu.me/google/2022/11…
Fortinet Threat Research Blog | Threat Predictions for 2023: New Attack Surfaces and Threats Emerge as Cybercrime Expands stpmvt.com/3t8aGR6
The lastest @MsftSecIntel Defense report is out! Find more details about the recent threats we observed! 🤓 👇#ransomware #threatintelligence #microsoft #infosec #nationstate microsoft.com/en-us/security…


Demonstrating a tool I built a year ago because I was sure zipExec would be used in a large campaign sooner or later (feels good to be right tbh :D). Unpacking the #bumblebee sample mentioned below with zipExec_unpack Find it on Github: github.com/f0wl/zipExec_u…

#bumblebee samples using ZIPExec for evasion 2d10e35ba9ba3cba78d59a276708efae a67536d6f5ac9795ee10c3f47264da8e github.com/elastic/protec… github.com/Tylous/ZipExec


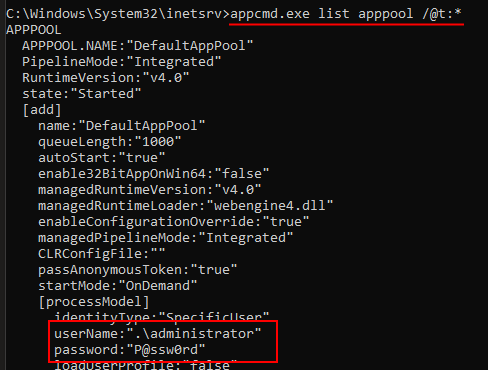
Do you detect IIS Application Pool credential dumping by looking for "/text:*"? Time to update your rules with undocumented /show, /(at)t, and /(at)text.
As attackers rely heavily on C2 communications for various stages of their campaigns, blocking these connections can disrupt or mitigate attacks. Learn how Microsoft Defender for Endpoint's network protection blocks connections to C2 infrastructure: microsoft.com/en-us/security…
Everyone uses the same recon playbook assets.sentinelone.com/sentinellabs22…

United States Trends
- 1. #AEWDynamite 36.2K posts
- 2. Epstein 1.39M posts
- 3. #Survivor49 3,284 posts
- 4. #AEWBloodAndGuts 4,703 posts
- 5. Hobbs 28.3K posts
- 6. #SistasOnBET 2,058 posts
- 7. Skye Blue 3,667 posts
- 8. Paul Reed 1,889 posts
- 9. Knicks 33.9K posts
- 10. Mark Briscoe N/A
- 11. Steph 20.4K posts
- 12. Draymond 8,125 posts
- 13. Hannah Hidalgo 3,992 posts
- 14. Claudio 24.3K posts
- 15. Paul Skenes 19.2K posts
- 16. Darby 3,963 posts
- 17. #TheChallenge41 1,135 posts
- 18. Mikey 59.5K posts
- 19. Cy Young 25.7K posts
- 20. Raising Arizona N/A
Something went wrong.
Something went wrong.