manuel valdez⛩️
@saur1n
learning, breaking🔁 | bug bounty hunter in my free time at @intigriti
You might like
I'm going to explain how I found two OS command injection vulnerabilities a few days ago. The vulnerabilities were quite easy to exploit once the injection points were identified.
Bug Bounty Tip: Don't compare your day-to-day with someone else's wins. Behind every $10K bug post are dozens of duplicates, N/As, and dead ends. Stay consistent; that's what really counts.
Just scored a reward @intigriti, check my profile: app.intigriti.com/profile/saurinn Bug: Semi-Blind SSRF :) #HackWithIntigriti
To new comers, Everything you need to learn about bug bounty is available online for free. Stay curious.
These ones caught me off guard😳. Really cool initiative for starters and also a lot of invites too @Hacker0x01

I just found my first SSRF on @Hacker0x01 The client had a pretty decent defenses against this kind of vulnerability but once again I was able to bypass it setting a redirect to their internal network. #bugbountytip #TogetherWeHitHarder

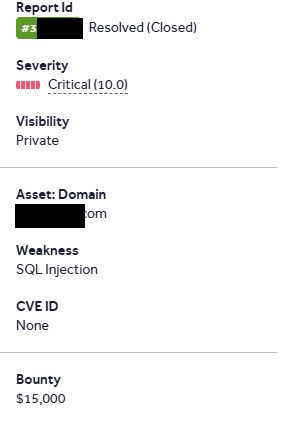
The pleasure was mine watching the master at SQLi at work :)
We earned a $15,000 bounty on @Hacker0x01 with @saur1n! His persistence on the target paid off, uncovering SQLi leads on a major social network. The exploit was straightforward once the query structure leaked due to verbose errors, revealing the injection point by commenting.…
🤌🏻
We've added a drop-down menu to list all the requests sent inside each Replay session, inspired by @ngalongc 🙌 Click "History" and use the search bar inside to quickly find important requests. Part of Caido v0.52.0 → caido.io/blog/2025-09-2…
I CALLED IT!
Gotta love bypasses!

Just scored a reward @intigriti, check my profile: app.intigriti.com/profile/saurinn Bug: Another full read SSRF leading to exfil. of AWS EC2 temp. keys :) Sent the report yesterday, today was triaged and rewarded 🚀 #HackWithIntigriti
Just scored a reward @intigriti, check my profile: app.intigriti.com/profile/saurinn Bug: Another full read SSRF leading to exfil. of AWS EC2 temp. keys :) Sent the report yesterday, today was triaged and rewarded 🚀 #HackWithIntigriti
Asking basic nmap stuff back in 2018, if I only would've been consistent enough...
So no -T4 and mtu < 1500 the question is what would be an efficient value of mtu to bypass *most* of firewalls/IDS/* -without sacrificing so much time-
😳
United States Trends
- 1. Cowboys 46.1K posts
- 2. James Franklin 44.3K posts
- 3. Drake Maye 14.3K posts
- 4. Pickens 14.5K posts
- 5. Penn State 60.7K posts
- 6. Jets 104K posts
- 7. Steelers 51.1K posts
- 8. Panthers 44.6K posts
- 9. Rico Dowdle 3,866 posts
- 10. Colts 45.2K posts
- 11. Diggs 7,574 posts
- 12. #Browns 3,189 posts
- 13. Saints 53.5K posts
- 14. Justin Fields 22.2K posts
- 15. Cooper Rush 2,994 posts
- 16. Gabriel 53K posts
- 17. Eberflus 2,437 posts
- 18. #RavensFlock 2,519 posts
- 19. Huntley 3,153 posts
- 20. Olave 4,118 posts
Something went wrong.
Something went wrong.