sean
@seanmw
UnpacMe | OALABS | Security Researcher
You might like
Let the unpacking begin!! Looking forward to working on some cool @unpacme features for 2025!! 👾🚀🚀🚀

We've uploaded our stream from Oct 24 where we continued analyzing the SORVEPOTEL infection chain, including shellcode, Maverick.Agent.StageTwo, Maverick Agent, and a PowerShells WhatsApp worm. Big shout out to @dodo_sec, @washi_dev and @unpacme for helping with this stream.

The CFP for RE//verse 2026 is open, but not for long! Submissions close November 14th. Share your best RE and security research with us here: sessionize.com/reverse-2026

We at @emproofsecurity open-sourced a free firmware reverse engineering workshop for self-study. Topics: ELF analysis, cracking, malware triage, embedded-Linux, bare-metal, crypto-key extraction, anti-analysis. Docker setup and solutions included. github.com/emproof-com/wo…
We’ve seen a spike in submissions this morning, which may cause some analysis delays. We’re working to resolve the backlog.
Check out our latest blog post on modeling complex control flow with function-level basic block analysis in Binary Ninja 5.1. From DSPs to Brain***k, this update makes it easier to develop plugins for tricky architectures. binary.ninja/2025/08/12/fun…



Using the UnpacMe byte-search IDA plugin we found some Scavenger related malware dating back to October 2024. At the time the malware was dubbed ExoTickler. Analysis follows...
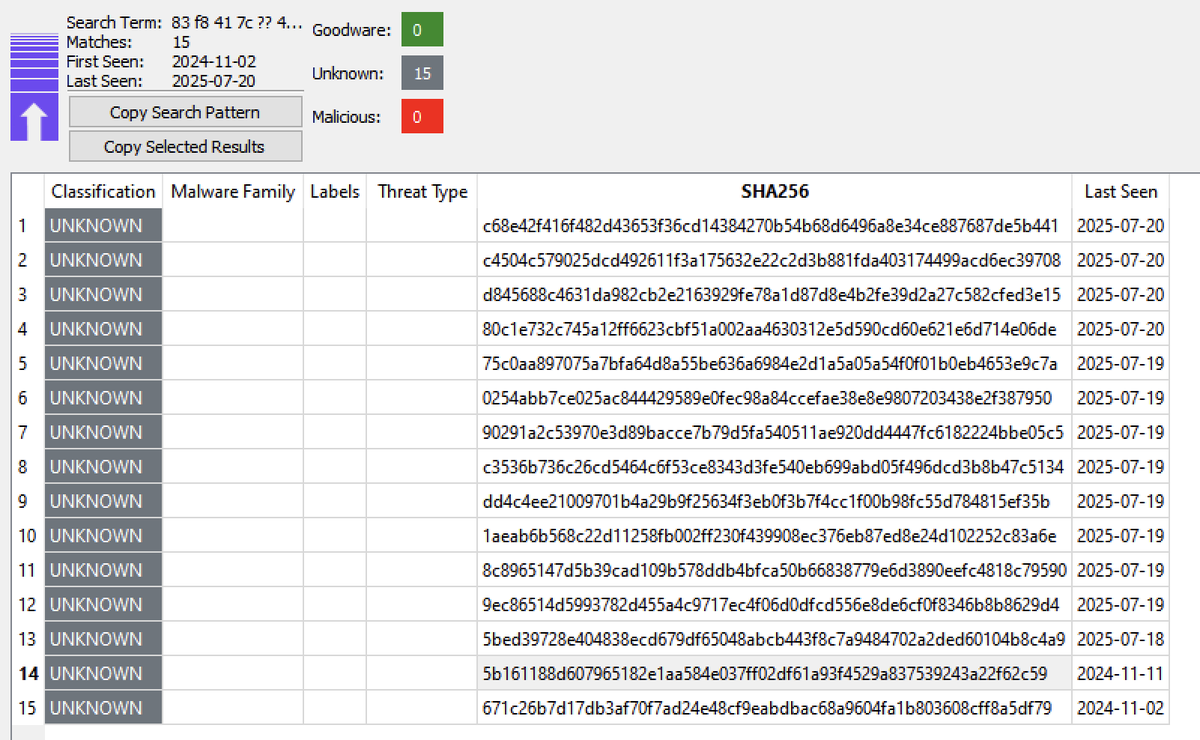
Hey all! As promised, here's the in-depth analysis @JershMagersh from @InvokeReversing and I did of the malware strain that's been spreading through NPM in the last few days following a successful phish. We present to you: Scavenger. c-b.io/2025-07-20+-+I…
We've uploaded our Time Travel Debugging in Binary Ninja stream with Xusheng Li from @vector35 where we unpacked malware and analyzed anti-analysis capabilities with TTD traces. Enjoy!

May be getting time to refresh why threat actor names exist and why they are important. They're not for marketing. silascutler.com/2021/01/14/Kil…
Contract is signed! No confidentiality, AMD has leadership that's capable of acting. Let's make this training run happen, we work in public on our Discord.
UnpacMe 8.7.2 - AI Script Analysis, Hunting, and Decompilation Updates 🚀 blog.unpac.me/2025/06/05/ai-…
YARA-X is now stable! virustotal.github.io/yara-x/blog/ya…
virustotal.github.io
YARA-X is stable!
We’re thrilled to announce the release of YARA-X 1.0.0, marking the end of the beta phase and the beginning of a new era for YARA users.
🔥 TitanHide has been updated to support the latest VMProtect 3.9.4 changes! The service name is now used as the device name as well, so the check for \\.\TitanHide will fail if you name the service differently 🧠

For half of the "encrypted" strings this stealc sample checks that the decrypted value is correct??? 🤣🤣

Over the past year I have been working on Python bindings (icicle-python) in stealth-mode. You can try it out today! The reversing community desperately needs alternatives to unicorn. Icicile is based on Ghidra's semantics and improvements there come essentially for free!

My emulator now supports icicle-emu as emulation backend. It serves as an alternative to the unicorn engine. The project is written in rust and looks very promising: github.com/icicle-emu/ici… However, first tests seem to show that unicorn is still faster. github.com/momo5502/emula…
New YARA hunting for decompiled scripts with UNPACME... Lazy malware devs exposed 👀
☕ ThreatLabz has discovered a new sophisticated malware threat that we have named CoffeeLoader. The malware is a loader that implements numerous stealthy techniques to evade antivirus and EDRs via call stack spoofing, sleep obfuscation, and Windows fibers. The malware is also…

UPX -> PyInstaller -> PS -> Xworm Full triage with UNPACME 🚀
UNPACME 8.7.0 Malicious Python analysis, AI safety, binary signature hunting, and much more! blog.unpac.me/2025/02/05/unp…
United States Trends
- 1. LINGORM HER AND HERS FANCON 49K posts
- 2. #BUNCHITA 1,427 posts
- 3. Tulane 4,395 posts
- 4. Frankenstein 80.1K posts
- 5. #SmackDown 46.8K posts
- 6. Giulia 15.1K posts
- 7. taylor york 8,421 posts
- 8. Supreme Court 182K posts
- 9. Aaron Gordon 4,524 posts
- 10. #TheLastDriveIn 3,993 posts
- 11. #River 4,545 posts
- 12. Russ 14.1K posts
- 13. #TheFutureIsTeal N/A
- 14. Justice Jackson 5,864 posts
- 15. Connor Bedard 3,118 posts
- 16. Gozyuger 1,879 posts
- 17. Podz 3,141 posts
- 18. Tatis 2,166 posts
- 19. Scott Frost N/A
- 20. Pluribus 30.9K posts
You might like
-
 herrcore
herrcore
@herrcore -
 UNPACME
UNPACME
@unpacme -
 Karsten Hahn
Karsten Hahn
@struppigel -
 Duncan Ogilvie 🍍
Duncan Ogilvie 🍍
@mrexodia -
 Silas Cutler (p1nk)
Silas Cutler (p1nk)
@silascutler -
 REhints
REhints
@REhints -
 Chuong Dong
Chuong Dong
@cPeterr -
 Myrtus
Myrtus
@Myrtus0x0 -
 ANY.RUN
ANY.RUN
@anyrun_app -
 0verfl0w
0verfl0w
@0verfl0w_ -
 MalShare
MalShare
@mal_share -
 Paul Melson
Paul Melson
@pmelson -
 James
James
@James_inthe_box -
 Ramin Nafisi
Ramin Nafisi
@MalwareRE -
 cybercdh
cybercdh
@cybercdh
Something went wrong.
Something went wrong.