Welcome to Secure Code , We are a team of cybersecurity professionals who are passionate and Skilled to improve and implement cybersecurity practices in Uganda 🇺🇬 and Africa. Please follow us for more Information.

How to identify cyber risks? 📌Unusual Emails or messages 📌Suspicious links 📌Request for sensitive information 📌Outdated software 📌Unsecure websites 📌Too good to be true offers #Cybersecurityawareness

What Is Cybersecurity? Cybersecurity is the ongoing effort to protect individuals, organizations and governments from digital attacks by protecting networked systems and data from unauthorized use or harm.
Au sure you system is securely developed . Or you are waiting to be hacked?😂😂 Contact us for all kinds of vulnerability testing and assessments. #cybersecurity


𝐓𝐡𝐞 𝐈𝐦𝐩𝐨𝐫𝐭𝐚𝐧𝐜𝐞 𝐨𝐟 𝐃𝐞𝐟𝐞𝐧𝐬𝐞 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐢𝐧 𝐭𝐡𝐞 𝐌𝐨𝐝𝐞𝐫𝐧 𝐖𝐨𝐫𝐥𝐝 (𝐔𝐩𝐝𝐚𝐭𝐞𝐝 𝐈𝐧𝐟𝐨𝐫𝐦𝐚𝐭𝐢𝐨𝐧)

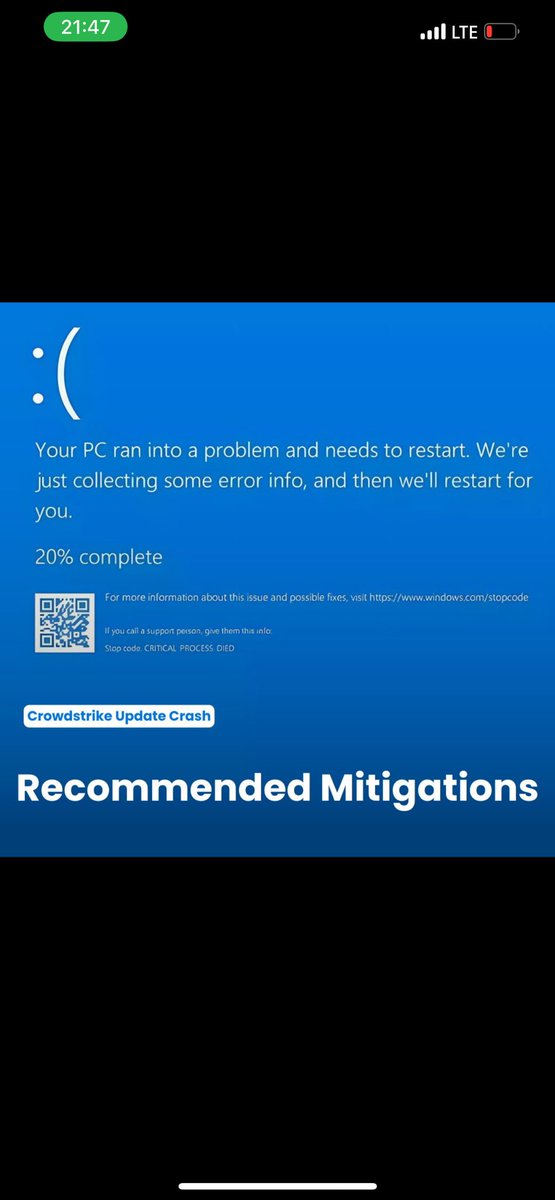
The crowdstrike incident, is a stuck reminder that Never keep all your eggs in one basket!
Hit our inbox for the services on the flyer . Secure your systems with us.

Have you heard about PHYSICAL CYBER CONTROLS? These are security measures that use physical devices to protect digital information. Like locks, surveillance cameras, and access cards. They safeguard data by controlling who can access the hardware that stores or processes it.
Enhance your email security with these essential strategies! From strong passwords to encryption, learn how to safeguard your digital communications at our Email Security Training. Don't miss out! #EmailSecurity #CyberSecurityTraining
CYBERSECURITY TERMS - MALWARE - Malicious Software - BRUTE FORCE - Gaining unauthorised access by guessing passwords. - ENCRYPTION - The process of protecting data by converting it into a secure format. - HONEYPOT - A system set up as a decoy to attract and detect hackers.
CATFISHING This is when a hacker leverages fake social media profiles to attack you. He fabricates a false online identity for the purposes of deception, fraud or exploitation. Be careful of who you connect with online and stay safe. #cybersecurityawareness
📧 Secure Code Technologies' Email Security training can strengthen your defenses against cyber assaults! Learn how to identify phishing scams, protect critical information, and keep your email free of unwanted attacks. Dm us Now !!#EmailSecurity #CybersecurityTraining
Elevate your cybersecurity game with Secure Code Technologies' comprehensive training! From email security to hardware protection, we've got you covered. Don't leave your company's assets vulnerable—Dm to train with us today! #CyberSecurityAwareness #SecureCodeTech

4 CYBERSECURITY TIPS TO PROTECT YOU WHEN USING PUBLIC WIFI Public Wifis and hotspots are not secure. 1. Do not conduct online banking on a public wifi. 2. Ensure that you are connected to secure websites. 3. Use VPN when connected to a public wifi. 4. Use firewalls.
United States 트렌드
- 1. D’Angelo 323K posts
- 2. Charlie 606K posts
- 3. Erika Kirk 56.2K posts
- 4. Young Republicans 20.1K posts
- 5. Politico 190K posts
- 6. #PortfolioDay 19.6K posts
- 7. Pentagon 111K posts
- 8. Presidential Medal of Freedom 80.4K posts
- 9. Jason Kelce 6,394 posts
- 10. #AriZZona N/A
- 11. Big 12 N/A
- 12. Brown Sugar 23.1K posts
- 13. Drew Struzan 33.2K posts
- 14. Scream 5 N/A
- 15. George Strait 4,582 posts
- 16. David Bell N/A
- 17. Burl Ives N/A
- 18. Angie Stone 38.7K posts
- 19. Venables 4,130 posts
- 20. VPNs 1,770 posts
Something went wrong.
Something went wrong.












